The Exploit Prediction Scoring System (EPSS) is a vulnerability scoring system designed to predict the likelihood that a vulnerability may be exploited in the wild.
It was created by the Forum of Incident Response and Security Teams (FIRST), an organization in charge of maintaining several vulnerability scoring protocols, to help organizations better prioritize their vulnerability remediation efforts.
EPSS assigns a probability score of 0 to 1 to each vulnerability. The higher the score, the greater the probability that a vulnerability will be exploited.
Aside from EPSS, FIRST also currently maintains CVSS. It’s worth noting that the two scoring systems are different—EPSS focuses on the likelihood of exploitation, while CVSS considers the vulnerability severity and associated attack vectors. However, CVSS base scores are among the parameters that influence EPSS scores. To learn more about their differences, read our blog post on EPSS vs. CVSS.
Table of Contents
- Why Is EPSS Important?
- How Does EPSS Work?
- What Is the Difference between the EPSS Score and the EPSS Percentile?
- Where to Get The EPSS Scores for CVE Vulnerabilities?
- What Are the Limitations of EPSS?
Why Is EPSS Important?
For years, network defenders had relied on vulnerability scoring systems that focus on severity (primarily CVSS) to rank vulnerabilities and prioritize remediation efforts. Although these scoring systems reflect important vulnerability characteristics such as the impact of exploitation and how easy it is to exploit it, they don’t evaluate current threats. They don’t consider which issues are actually exploited or will be exploited in the nearest future. To address this limitation, FIRST developed the EPSS model to help organizations prioritize vulnerabilities, remediate them more effectively, and thus improve the overall security posture.
The original EPSS model was published in 2019, with scores released publicly for the first time in 2021. Major updates were released in February 2022, March 2023, and March 2025. FIRST continues to improve the model to provide near-real-time assessments of all publicly disclosed vulnerabilities.
EPSS helps organizations prioritize which software vulnerabilities to address first by assigning a score to them based on their possibility of exploitation. It helps answer the question “How likely is it that attackers would exploit a specific vulnerability in the next 30 days?”
Integrating EPSS into vulnerability management allows security teams to focus patching efforts on vulnerabilities that threat actors are most likely to exploit, rather than basing these efforts on vulnerability severity scores alone.
Why does this matter? Some critical vulnerabilities with very high severity ratings may be difficult to exploit and therefore not as urgent as others with medium or even low severity, which may prove easier to use as an attack entry point (or may already have existing exploits).
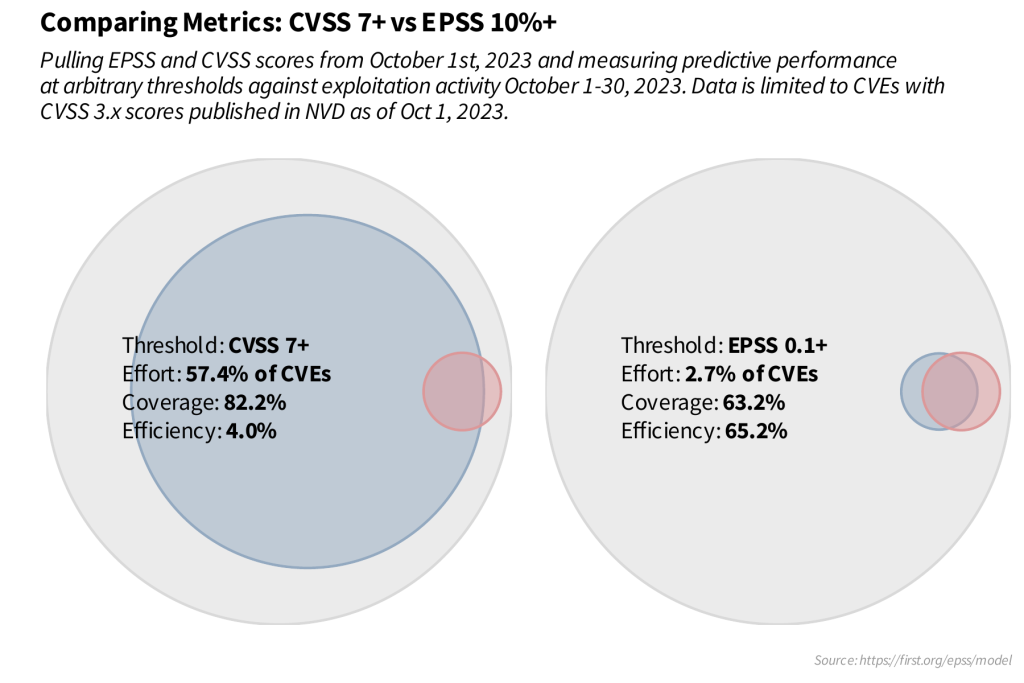
Remediation strategies based on exploitability allow cybersecurity professionals to optimize and allocate security resources more efficiently in comparison to the common security strategy that relies on severity alone.
How Does EPSS Work?
EPSS relies on collecting a variety of vulnerability data points and leverages machine learning (ML) to analyze them and generate a probability score.
What Is the EPSS Score?
An EPSS score is a numerical value ranging from 0 to 1 (or from 0% to 100%) that predicts the likelihood of a CVE being exploited in the next 30 days. A higher score means a greater risk and tells security practitioners which vulnerabilities require immediate attention.
All published CVEs have EPSS scores.
What Data Does EPSS Rely On?
The pieces of information the model gathers include the following:
- Software vendor affected by the vulnerability, according to the National Vulnerability Database (NVD)
- Number of days since the assigned Common Vulnerabilities and Exposures (CVE) number was published in the MITRE CVE list
- Categorized references from MITRE and NVD
- Normalized phrases from the vulnerability description
- Common Weakness Enumeration (CWE) numbers mapped to the vulnerability
- CVSS base score (the current version of EPSS relies on CVSS 3.x)
- Presence of the CVE on vulnerability tracking lists like the CISA KEV, Google Project Zero, and Trend Micro’s Zero Day Initiative (ZDI)
- Exploit codes published on code repositories like Exploit-DB, GitHub, MetaSploit
- Vulnerability’s presence in the lists of vulnerability scanning and assessment tools, such as Intrigue, Sn1per, Jaeles, and Nuclei
How the EPSS Score Is Calculated
The machine learning model is trained on a 14-month historical dataset to identify patterns and correlations between vulnerabilities and exploitation. With this data, it can predict the likelihood of exploitation of new vulnerabilities using a probability score. The performance of this model is evaluated through a look-back approach, using the last two months of the 14-month historical data (only 12 months of data out 14 are used for the training and the last 2 months worth of data help validate if the model was trained correctly).
The EPSS model is continuously updated, constantly obtaining vulnerability information and using it to produce daily estimates of the exploitation probability of each published CVE for the next 30 days.
It’s worth noting that the EPSS department of FIRST changes the model itself relatively frequently. For example, on March 17, 2025 a new model (aka EPSS version 4) was introduced, as, according to FIRST, the third version’s performance has degraded over time.
What Is the Difference between the EPSS Score and the EPSS Percentile?
EPSS score and percentile are two different ways to represent the likelihood that a vulnerability would be exploited. In the image below, for instance, CVE-2023-44487 has a score of 0.73185 and a percentile of 0.98127.
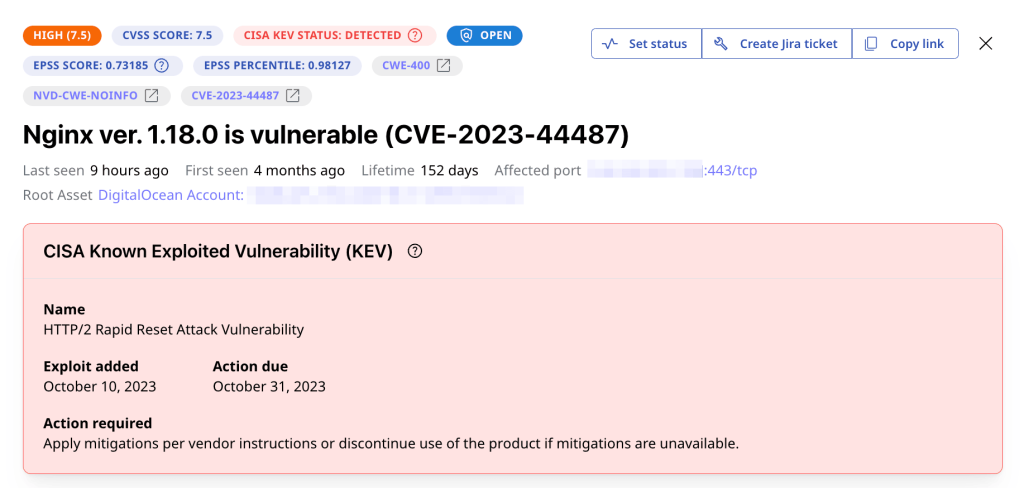
The EPSS score is the direct output of the EPSS model, ranging from 0 to 1 or from 0% to 100%. As previously mentioned, a higher score indicates a higher probability of exploitation. In the context of CVE-2023-44487, there is around a 73% probability that threat actors would exploit it during the next 30 days.
On the other hand, an EPSS percentile refers to a vulnerability’s position compared with all other vulnerabilities in the dataset. It also ranges from 0 to 1. A higher percentile means the vulnerability has a higher probability of exploitation compared with a larger portion of other vulnerabilities. Therefore, CVE-2023-44487 is more likely to be exploited than 98% of all the CVEs.
Where to Get The EPSS Scores for CVE Vulnerabilities?
The EPSS model described above calculates the EPSS score. Unlike CVSS scores that are constant (within the given version of CVSS), EPSS scores for CVE vulnerabilities are recalculated daily. So, users that want to incorporate EPSS into their vulnerability management or attack surface management workflows need to update EPSS scores of the vulnerabilities on a daily basis.
There are four main ways to get EPSS score of certain vulnerabilities:
- Download the daily CSV file with all the CVEs and their corresponding EPSS scores manually from from FIRST’s data and statistics page
- Query a REST API maintained by FIRST
- Use an EPSS calculator (the one we link to is just an example, there are other)
- Using external attack surface management (EASM) platforms like Attaxion with a built-in EPSS scoring mechanism. Attaxion downloads the daily file on its own and automatically provides EPSS scores for each CVE vulnerability it discovers.
What Are the Limitations of EPSS?
While EPSS is valuable in implementing a risk-based vulnerability management approach, it has limitations that have to be considered when integrating EPSS within a broader security strategy.
For one, EPSS scores are only applicable to vulnerabilities with CVE identifiers, so unknown or unreported vulnerabilities (including zero-day vulnerabilities) that haven’t been cataloged with a CVE identifier are not covered. Similarly, other security weaknesses, such as some misconfigurations and software bugs, will not have an associated EPSS score. Therefore, using EPSS alone creates a visibility gap for critical security issues that haven’t been formally analyzed in the CVE framework.
Another limitation of EPSS is that since the system uses ML algorithms, its accuracy and reliability in predicting the exploitability likelihood of potential threats depend heavily on the quality of data the ML algorithm is trained on and on the algorithm itself. Like any ML system, EPSS can be susceptible to biases or inaccuracies present in its training data. As noted above, even FIRST itself admits to EPSS models’ performance decaying over time.
EPSS should be part of a larger strategy, as organizations benefit more when they use EPSS along with CVSS and other vulnerability prioritization methods. The CISA KEV catalog, for example, informs security professionals if the vulnerability has already been successfully exploited in the wild. Combining EPSS, CVSS, and CISA KEV allows organizations to implement risk-based vulnerability management more effectively.
Key Takeaways
- EPSS is a vulnerability scoring system that predicts the probability that a vulnerability will be exploited.
- It assigns each vulnerability a probability score ranging from 0 to 1 and a percentile score.
- It helps organizations prioritize vulnerability remediation efforts.
- The EPSS score indicates the likelihood of exploitation, while the percentile measures exploitability relative to other vulnerabilities.
- One of its limitations is that EPSS only covers vulnerabilities with CVE identifiers.
- It is most effective when used as a part of a comprehensive security strategy, together with other vulnerability metrics.
Obtain EPSS scores for all vulnerabilities in your external attack surface. Kick off your 30-day free trial with Attaxion today.
