Blog
Trending Post
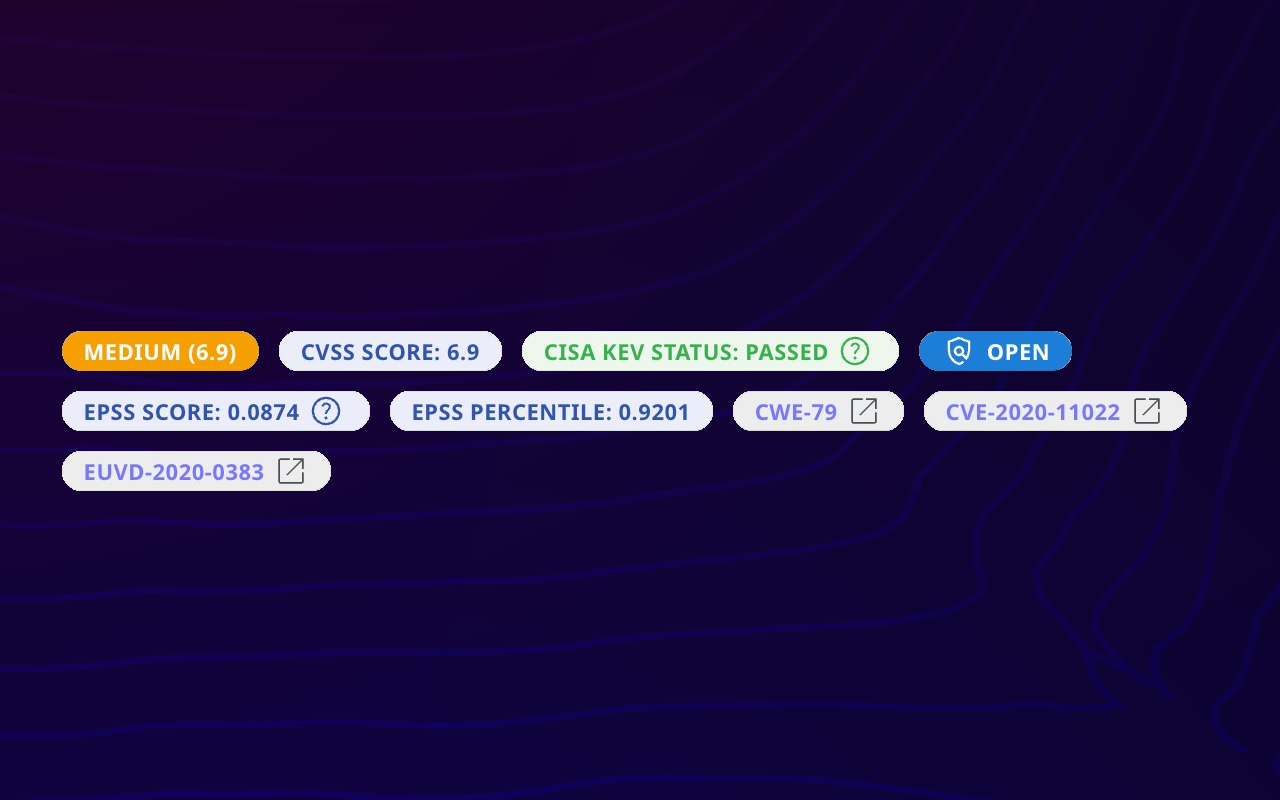
Attaxion Becomes the First EASM Platform to Integrate ENISA’s EU Vulnerability Database (EUVD)
DOVER, DE, UNITED STATES, May 21, 2025 — Attaxion, the external attack surface management (EASM) vendor with industry-leading asset coverage, announce[...]
-
 Learn more
Learn moreHow to Detect Exposed IP Addresses in Your Infrastructure
“What Internet-facing IP addresses do I have in my infrastructure?” This is a common question that security professional[...]
-
 Learn more
Learn moreUnderstanding Penetration Testing Scope
Your organization will likely need penetration testing at some point, whether for regulatory compliance or as part of a[...]
-
 Learn more
Learn moreSSRF vs. CSRF Vulnerabilities: Comparing Targets, Impact, and Mitigation Techniques
Server-side request forgery (SSRF) and cross-site request forgery (CSRF) are two types of attacks that allow attackers t[...]
-
 Learn more
Learn moreCVSS vs. EPSS: Which Vulnerability Scoring Do You Need?
The overwhelming number of vulnerabilities organizations face—and attackers can exploit—makes it impractical and even im[...]
-
 Learn more
Learn moreAttaxion Becomes the First EASM Platform to Integrate ENISA’s EU Vulnerability Database (EUVD)
DOVER, DE, UNITED STATES, May 21, 2025 — Attaxion, the external attack surface management (EASM) vendor with industry-le[...]
-
 Learn more
Learn moreAttack Surface Management vs Vulnerability Management: What’s the Difference?
New cybersecurity abbreviations appear faster than professionals manage to memorize them. So, when people see yet anothe[...]
-
 Learn more
Learn moreVulnerability Assessment: Methodology, Benefits, and Types
The sheer volume of potential attack vectors is staggering. In 2024 alone, 40,077 Common Vulnerabilities and Exposures ([...]
-
 Learn more
Learn moreCWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like[...]
-
 Learn more
Learn moreSubdomain Security: How Forgotten Assets Can Become Vulnerable Gateways for Attackers
“Out of sight, out of mind” is true even in cybersecurity. Assets that are not visible to the security team are often fo[...]
-
 Learn more
Learn moreNew EU Product Liability Directive: What Software Companies Need to Know
Software supply chain vulnerabilities are a multimillion-dollar problem, according to a study by Juniper Research, and i[...]
-
 Learn more
Learn moreSAST Vs. DAST Vs. EASM: Selecting the Right Tools for You
Modern cybersecurity is littered with too many acronyms that sometimes leave even seasoned professionals scratching thei[...]
-
 Learn more
Learn moreStaying Ahead of Domain Hijacking: The Critical Risks of Missed Domain Renewals
Two-thirds of security breaches can be attributed to human error, according to Verizon’s 2024 DBIR. Cyber attackers are[...]
-
 Learn more
Learn more10 Critical Attack Surface Metrics to Track
With recent regulatory changes pushing cybersecurity to the boardroom, effective attack surface monitoring and visualiza[...]
-
 Learn more
Learn moreTechnology Vulnerability Management Process with EASM
Technology Vulnerability Management Process with EASM Modern cybersecurity solutions allow you to partially automate vul[...]
-
 Learn more
Learn moreHow BOD 23-01 Can Enhance Federal Network Asset Visibility and Vulnerability Detection
It’s no secret that governments are prime cyber attack targets the world over. And why not? They hold very sensitive inf[...]
-
 Learn more
Learn moreThe New SEC Rules and What They Mean for CISOs
The onslaught of cyber attacks in the past years has prompted government agencies to take the lead in improving cybersec[...]
-
 Learn more
Learn moreWhat Does the Threat Landscape Look Like According to the 2024 Verizon DBIR?
When we know what threats we’re up against, we can prepare better. For this reason, reports like Verizon’s annual Data B[...]
-
 Learn more
Learn moreDetecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the re[...]
-
 Learn more
Learn moreThe Importance of Asset Attribution to External Attack Surface Management
The prevalence of cyber attacks has become a harsh reality. A study shows that 69% of organizations have fallen victim t[...]
-
 Learn more
Learn moreNIS 2 Compliance: From Asset Discovery to Risk Management
No entity across industries and regions is safe from cyber attacks. The European Union (EU) Agency for Cybersecurity (EN[...]
-
 Learn more
Learn moreUsing EASM Together With the Mitre ATT&CK Framework
External Attack Surface Management (EASM) platforms and attackers employ similar reconnaissance techniques for sca[...]
-
 Learn more
Learn moreSecuring ISO 27001 Compliance: Attack Surface and Risk Management Essentials
Building customer trust takes a lot of hard work, and a single security incident can jeopardize it all. In fact, IBM[...]
-
 Learn more
Learn moreOWASP Top 10 Vulnerabilities Detection through EASM
Threat actors strategically capitalize on their knowledge of existing vulnerabilities to target susceptible victims. The[...]
-
 Learn more
Learn moreOvercoming the Top SOC Challenges with EASM
A day in the life of a security operations center (SOC) analyst likely involves sifting through mountains of data and al[...]
-
 Learn more
Learn moreYour Digital Supply Chain Is Expanding Your Attack Surface
As organizations increasingly rely on third-party vendors and suppliers for their day-to-day operations, their digital e[...]
-
 Learn more
Learn moreScaling Up? 4 Critical Questions to Manage Your Expanding Attack Surface
Standing still is not an option for organizations that want to succeed. Companies must constantly strive for growth by e[...]
-
 Learn more
Learn moreActive and Passive Vulnerability Scanning: What Is the Difference?
Vulnerability scanning is an integral part of attack surface analysis, helping security teams identify security issues,[...]
-
 Learn more
Learn moreTypes of Web Application Attacks
Web applications are a prime cyber attack target because they often contain sensitive data, such as customer information[...]
-
 Learn more
Learn more4 Common Network Vulnerabilities
Although threat actors aim to take advantage of the latest vulnerabilities, there are also recurring weak aspects of net[...]
-
 Learn more
Learn morePenetration Testing versus Vulnerability Scanning: How Do They Differ?
Penetration testing or pentesting for short and vulnerability scanning are critical processes that help organizations id[...]
-
 Learn more
Learn moreHow to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sens[...]
-
 Learn more
Learn moreHow Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is th[...]