Best Intruder.io Alternative for Vulnerability Management: Attaxion EASM
Intruder.io is a cloud-based vulnerability scanner and vulnerability management tool that’s been around for almost a decade. Intruder helps organizations protect their attack surface and comply with regulations such as PCI.
Attaxion is a modern alternative to Intruder.io that also supports vulnerability management, but in addition, it helps proactively protect the organization’s external attack surface. It can discover and scan assets that the organization’s IT department wasn’t previously even aware of – something that Intruder.io can’t do.
Both Attaxion and Intruder have their own strengths and weaknesses. Let’s take a look at how these two platforms compare.
Since both solutions can be your go-to tools for vulnerability management, we’ll assess them as from this perspective, going through 5 stages of vulnerability management:
- asset discovery and inventory
- vulnerability scanning
- vulnerability prioritization and risk analysis
- vulnerability prioritization and mitigation
- continuous monitoring.
But we’ll start with pricing.
 PART 1
PART 1
Pricing
Free trial
Both Attaxion and Intruder offer a free trial, so that you can get a taste of the platform’s capabilities. Attaxion offers a 30-day trial with all features included and without any limitations. Intruder’s trial is 14-days long and is limited to its medium tier called Pro with licenses for up to 5 targets or web applications.
In both cases, free trials are available to everyone on demand – you don’t need to contact sales to start using Attaxion or Intruder.io.
Intruder.io pricing and plans
When it comes to paid plans, Intruder’s pricing depends on two main factors: which of the 3 tiers you choose and how many web apps or targets you want to cover.
The most basic tier in Intruder is called Essential – it’s very limited and doesn’t have any integrations or the ability to run automated scans. This tier is not very well suited for doing vulnerability management properly, as it’s limited to 1 scheduled scan per month. Basically, it’s an on-demand scanner. So, we won’t be considering it for the purposes of this article.
The next is Pro tier, which has most of the features Intruder has in its sleeve. It offers everything in Essential + internal scanning, unlimited scheduled scans, integrations, and automated scans. Also, Pro plan relies on a different vulnerability scanner, which we’ll discuss more in-depth later.
Finally, there’s Custom tier that has everything in Pro plus daily scans, so-called rapid response scans, and more. If you want to use invoices rather than pay with a card, that’s the only option.
Intruder’s Essential and Pro plans are self-serve and have transparent pricing. Intruder.io is priced by target: you choose how many web apps and how many infrastructure targets (websites/hostnames/IPs/endpoints) you want Intruder to cover – and it calculates the pricing for you.
Pro-tier pricing starts at ~$296 USD (277 EUR)/month for 1 web app or ~$180 USD (169 EUR)/month) for 1 infrastructure target. If billed yearly, it’s a little cheaper: ~$2,840 USD (2,656 EUR)/year for 1 web application and $2,164 USD (2,023 EUR)/year for 1 infrastructure target). Custom plan’s pricing is not available publicly.
Attaxion Pricing
Attaxion offers all it has right away – there’s only one tier, and it has all the functionalities available. That includes an advanced proprietary scanner, automated scans, integrations, and more.
Attaxion is priced by asset. The pricing starts at $349/month for up to 120 assets, which include domains, subdomains, IPs, open ports, cloud infrastructure instances, CIDRs, and more. Here’s some details on assets and asset types in Attaxion.
If paid yearly, Attaxion also gets cheaper – down to $3,490 a year for the same number of assets.
As the number of assets increases, so does the price.
How They Compare
Due to significant differences in pricing models, it’s hard to compare prices. However, market analysis suggests that both tools are on the less expensive side of the spectrum.
Intruder usually ends up being somewhat more expensive than Attaxion, if you try to cover the whole infrastructure.
For example, with 3 web applications and no infrastructure targets Intruder will cost you ~$360 USD (338 EUR) / month, while Attaxion’s starting price for 120 assets will be $349/month. So, overall, Attaxion is likely going to be a cheaper alternative to Intruder.io.
Now, let’s jump to how well they perform as vulnerability management tools.
| Intruder.io vs Attaxion: Pricing | ||
| Attaxion | Intruder | |
| Pricing monthly | Starts at USD $349/month | Starts at USD ~ $180/month (169 EUR/month) for 1 infrastructure target or USD ~$296/month (277 EUR/month) for 1 web application |
| Pricing yearly | Starts at $3,490/year for up to 120 assets | Starts at USD ~ $2,164/year (2023 EUR/year) for 1 infrastructure target or USD ~$2,840/year (2,656 EUR/year) for 1 web application |
| Assets covered at the starting price | 120 (all types) | 1 |
| Free trial | ✅ (30 days) | ✅ (14 days) |
| What happens after the trial ends | Account is still accessible, but the platform runs no scans or updates | Account is still accessible, but the platform runs no scans or updates |
 PART 2
PART 2
Asset Discovery and Inventory
Asset discovery and inventory is the first step of the vulnerability management process. And this is, perhaps, where Intruder.io and Attaxion differ the most. For Attaxion, asset discovery is its core specialization, while Intruder doesn’t offer to discover assets at all.
| Intruder.io vs Attaxion: Asset Discovery | ||
| Attaxion | Intruder | |
| Automatic asset discovery | ✅ | ❌ |
| Types of assets discovered | 10+: Domains Subdomains IPv4 addresses IPv6 addresses Organizations Open ports Email addresses Clouds CIDRs SSL Certificates | 2 (for manually added assets): PortsSSL Certificates |
| Asset coverage | ✅Highest | ❌Not applicable |
| Reconnaissance techniques | 11+ automatic methods | None |
| Dependency graph | ✅ | ❌ |
Intruder.io Doesn’t Have Asset Discovery
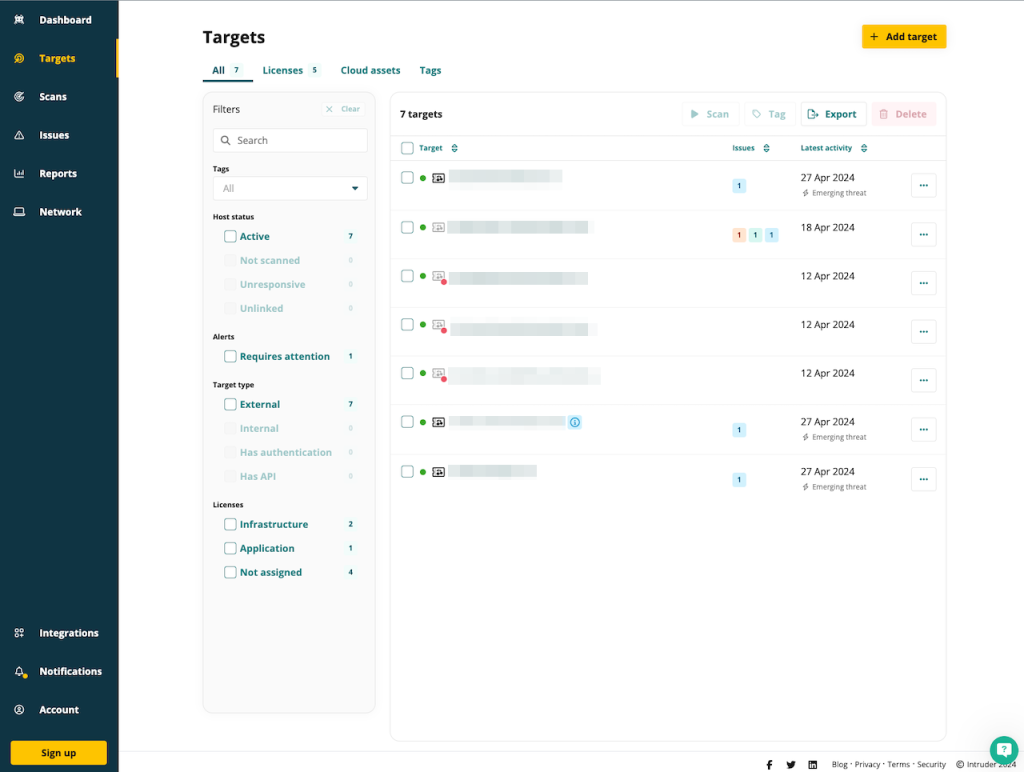
Using Intruder begins with adding targets. The platform completely relies on you knowing about all the assets that you want to scan, and meticulously adding them to Intruder’s interface as targets or web applications.
Once you’ve added an asset, Intruder.io will be able to scan it for vulnerabilities, as well as find open ports and related SSL certificates. But it doesn’t provide subdomain enumeration functionality, for example. You need to add subdomains manually, one by one.
That means that Intruder.io can only protect assets that the organization’s IT department is aware of. It’s worth noting that those could be both internal and external assets – Intruder can help with endpoints as well.
The assets are organized under the “Targets” section. Intruder offers to sort them by status and target type, as well as select to view only those that require your attention. You can also add tags and notes to assets for convenience.
Attaxion Offers Broad Asset Coverage
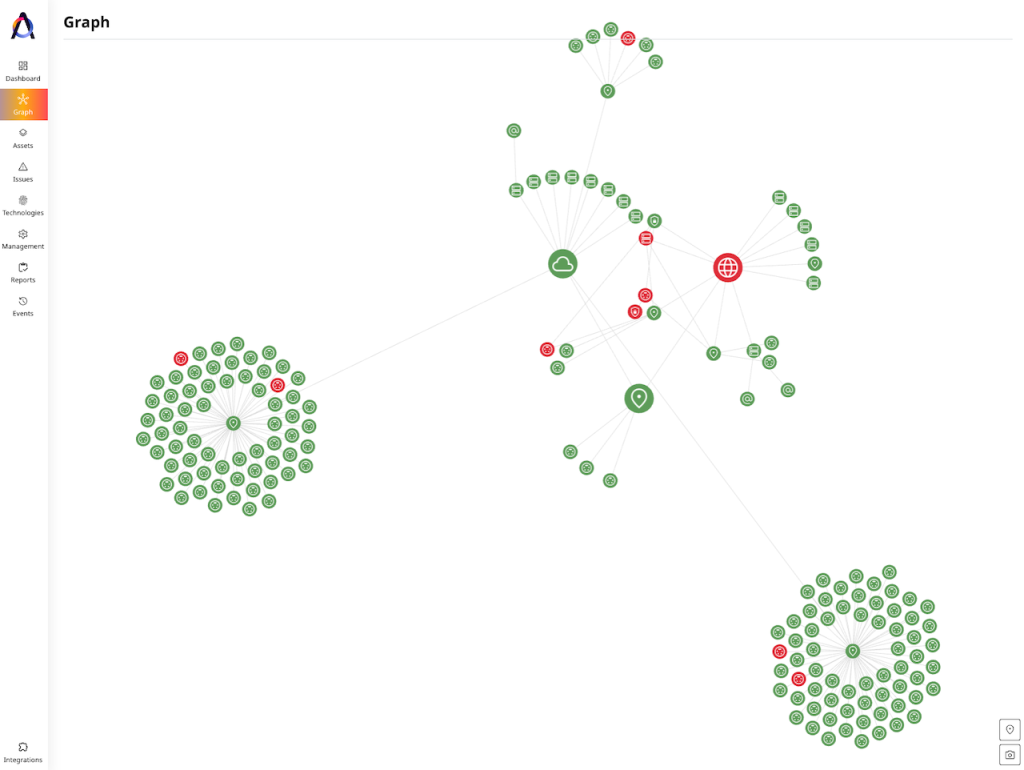
Attaxion’s approach is very different from how Intruder.io works. You can add a number of root assets to Attaxion (domains, IP addresses, cloud accounts), and then it will discover related assets automatically.
Attaxion’s set of reconnaissance techniques allows it to find associated subdomains, IP addresses, open and closed ports, SSL certificates, and so on. It can even find exposed email addresses associated with the root asset.
So, unlike Intruder, Attaxion can help you protect not only the assets you are aware of and added to the interface, but also assets you didn’t even know existed.
Attaxion’s asset discovery capabilities are among the best on the market. In addition to finding new assets, Attaxion can show how they are connected, drawing a dependency graph that can give an idea about potential attack paths adversaries can use. Intruder doesn’t show connections between assets.
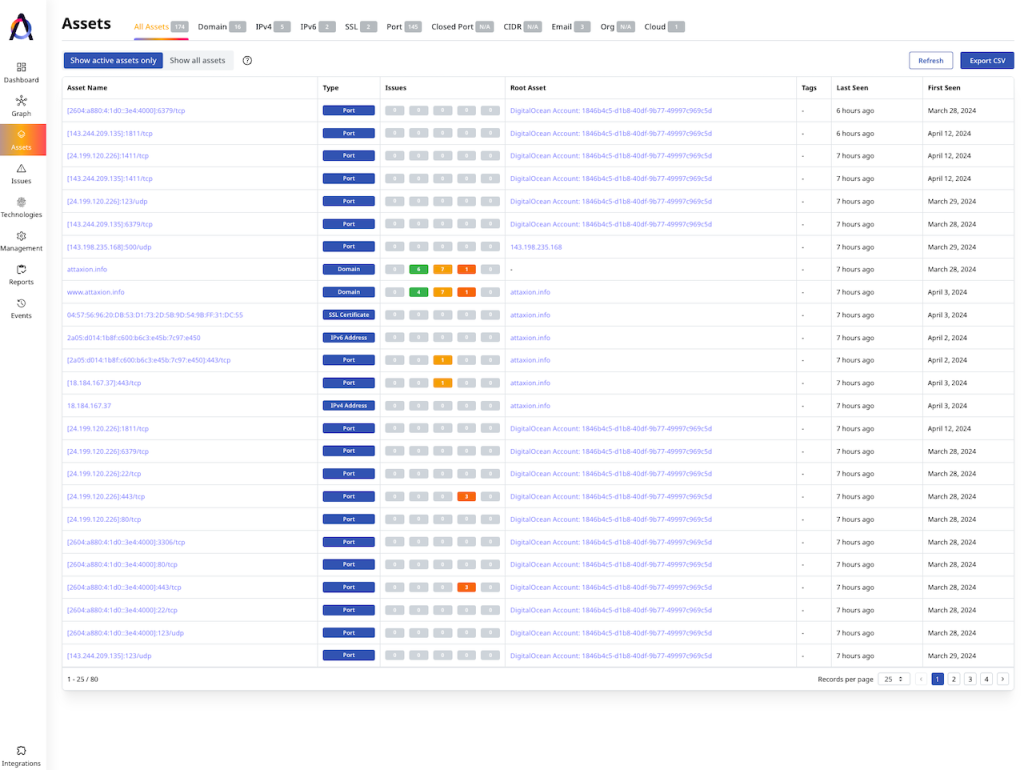
When it comes to inventory, Attaxion provides you with a complete list of assets (both added and discovered), giving you a full overview of the organization’s external attack surface.
For each asset, you can see its type, how many issues of different severity it has, when it was last seen, and so on. Attaxion allows you to filter the list of assets by each of these parameters, as well as add tags.
With Attaxion, you can also switch between scan types: it offers stealthy passive scanning in addition to the more advanced active scanning.
How They Compare
To sum it up, when it comes to asset discovery, Intruder just skips this part altogether, while Attaxion offers a set of advanced techniques for discovering known and unknown assets and mapping the whole external attack surface of the organization. That’s why Attaxion is a full-fledged external attack surface management platform, while Intruder is a vulnerability scanner.
As for asset inventory, the tools are more or less equal – provided that you took time to add all the assets to Intruder. Overall, for asset discovery Attaxion is more than just an Intruder.io alternative, it’s on a completely different level.
 PART 3
PART 3
Vulnerability Detection
After the assets have been discovered, vulnerability management platforms rely on vulnerability scanners to find vulnerabilities, and then filter out false positives.
| Intruder.io vs Attaxion: Vulnerability Detection | ||
| Attaxion | Intruder.io | |
| Scanner | Attaxion (proprietary) | OpenVAS (Essential) Tenable (Pro) Tenable + Nuclei (Custom) |
| Scanning | Continuous | Scheduled Triggered Emerging Threat scans (Pro) Rapid Response scans (Custom) |
| Easy user interface | ✅ | ✅ |
| Dependency graphs | ✅ | ❌ |
| Technology fingerprinting | ✅ | ❌ |
Intruder’s Vulnerability Detection Capabilities
Depending on the plan that you choose, Intruder offers different vulnerability scanners:
- On Essential, you get OpenVAS – an open-source full-fledged vulnerability scanner, developed by Greenbone.
- On Pro, instead of OpenVAS, Intruder.io offers to scan your infrastructure with Tenable Nessus, theoretically a more advanced vulnerability scanner.
- On Custom plans, Intruder combines Tenable Nessus with Nuclei – another open-source scanner.
Intruder.io offers to run scans on a regular basis – weekly, monthly, or quarterly (with daily scans available on custom plan). You can also initiate a scan manually.
In addition to that, on Pro plan Intruder.io offers to run so-called Emerging Threat scans – automatically initiating scans when new vulnerabilities are added to its database.
On Custom plan, it adds so-called Rapid Response scans – scanning for threats that are actively exploited in the wild at the moment.
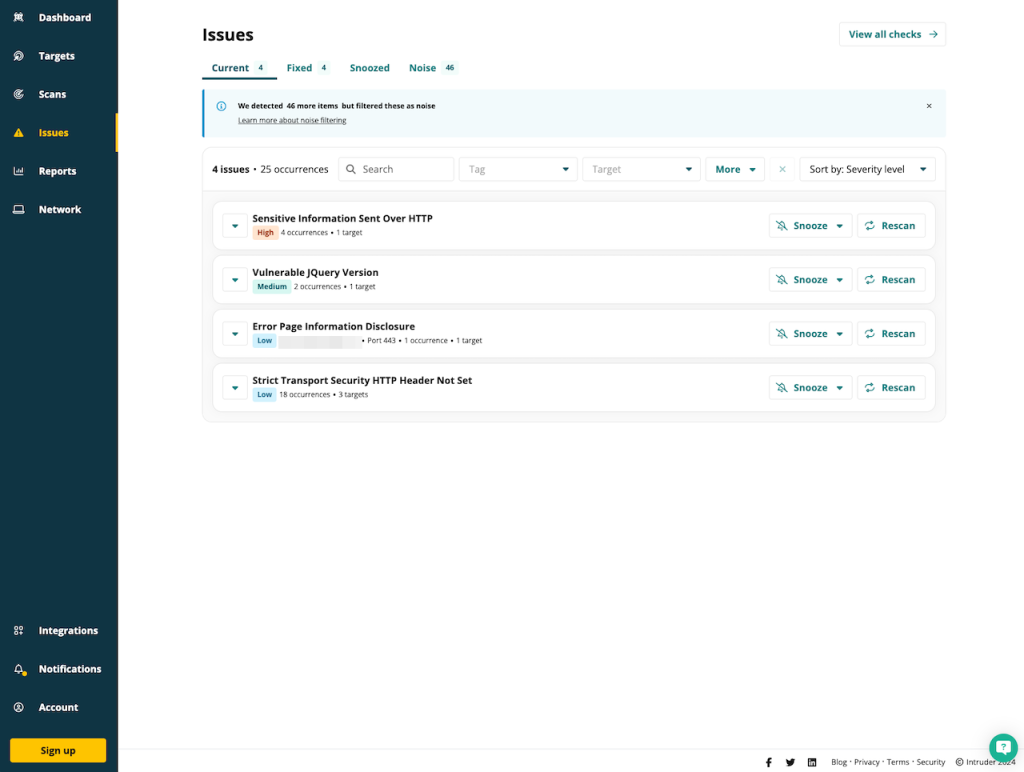
Some issues Intruder filters out as noise. According to Intruder’s documentation, these are the issues that they “deem informational rather than actionable.” You can still get access to the list of “noisy” issues as well, if you want to.
Attaxion’s Vulnerability Detection Capabilities
Attaxion uses its own proprietary scanner to scan for vulnerabilities in the assets that it discovers (and those that you add manually as root assets as well).
The databases Attaxion uses are up to date with Mitre’s CVE and CWE databases.
Attaxion’s approach to scanning is also different from Intruder’s. Instead of offering daily or manual scans, Attaxion relies on continuous scanning. It constantly keeps going through the organization’s assets, trying to discover new ones and scanning the already discovered ones for vulnerabilities.
In addition to a list of vulnerabilities, Attaxion also builds a list of technologies such as SaaS platforms or frameworks associated with the asset. In the list, Attaxion highlights vulnerable technologies.
Technology fingerprinting allows you to quickly sort assets by technology, helping with prioritization and remediation. Intruder detects a much narrower list of technologies and doesn’t offer a centralized database for it.
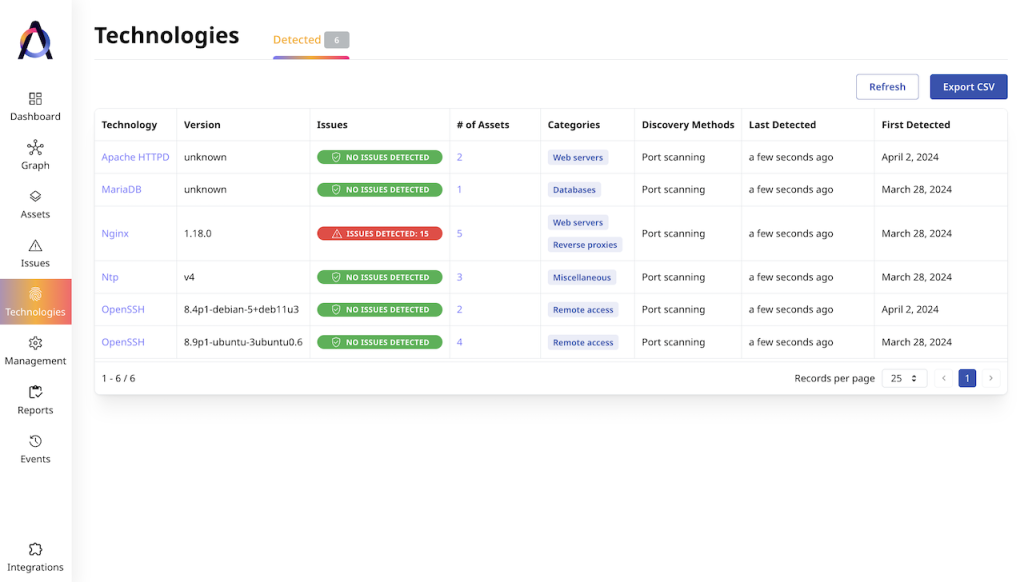
Other than that, Attaxion’s capabilities in vulnerability scanning are similar to those of Intruder: it provides a dashboard with distribution of issues by severity, and a list of issues with descriptions, dates, related assets, and remediation suggestions.
Both Intruder and Attaxion link to sources with more information about vulnerabilities.
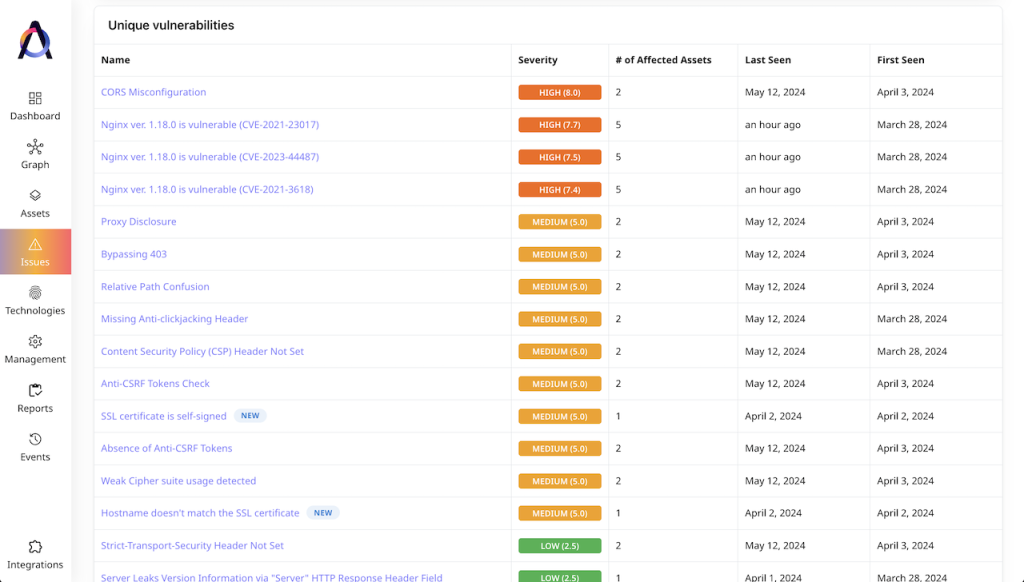
How They Compare
When it comes to vulnerability detection, Intruder’s strong side is the ability to run Emerging Threat and Rapid Response scans. Intruder also does a great job providing reports about the results of the scans, but we’ll talk about it in more detail later.
Attaxion’s strong sides are continuous scanning and technology fingerprinting. When it comes to the performance of the scanners, in our test, Attaxion was able to find more vulnerabilities than the Pro version of Intruder.
 PART 4
PART 4
Vulnerability Prioritization
After finding all vulnerabilities, the next task is to prioritize them. Here, platforms have very similar functionality.
| Intruder.io vs Attaxion: Vulnerability Prioritization | ||
| Attaxion | Intruder.io | |
| Dashboard | ✅ | ✅ |
| Vulnerability scoring | CVSS, severity | CVSS, severity |
| Mark as false positive or accepted risk | ✅ | ✅ |
| Manual rescan trigger | ❌ | ✅ |
Vulnerability Prioritization with Intruder.io
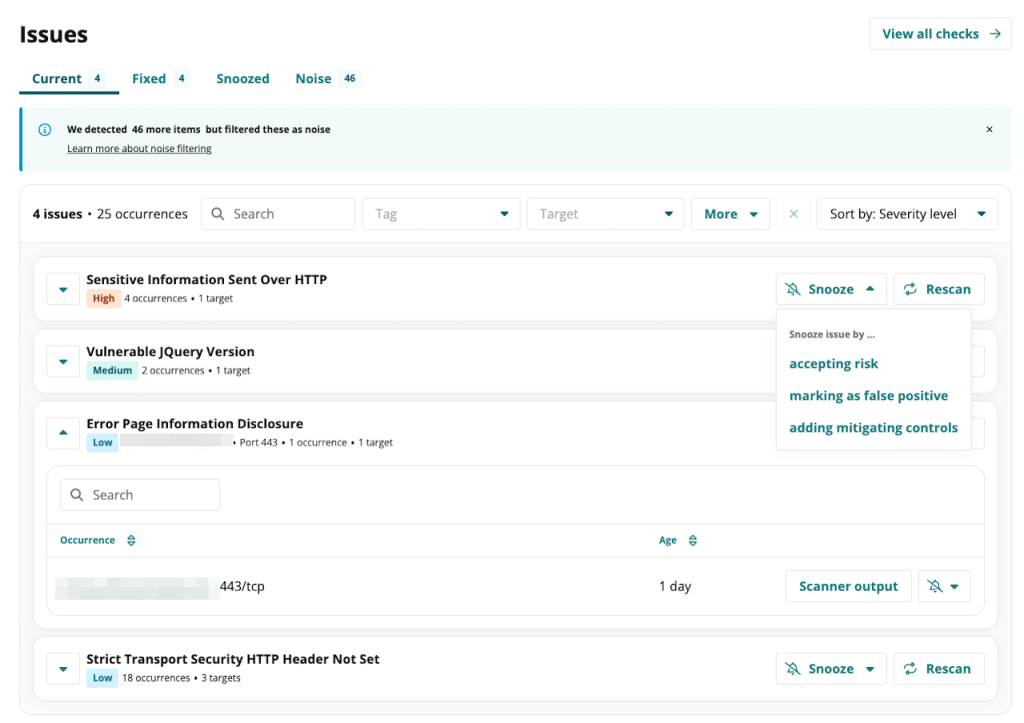
Intruder offers a neat dashboard, where for each issue it provides data such as the description of the issue, which assets does it plague and how long ago has it been found. It also provides remediation suggestions.
You can snooze the issue by marking it as an accepted risk, a false positive, or as something for which you’ve added mitigation controls. Also, you can manually trigger a rescan upon fixing the issue to ensure that it’s fixed.
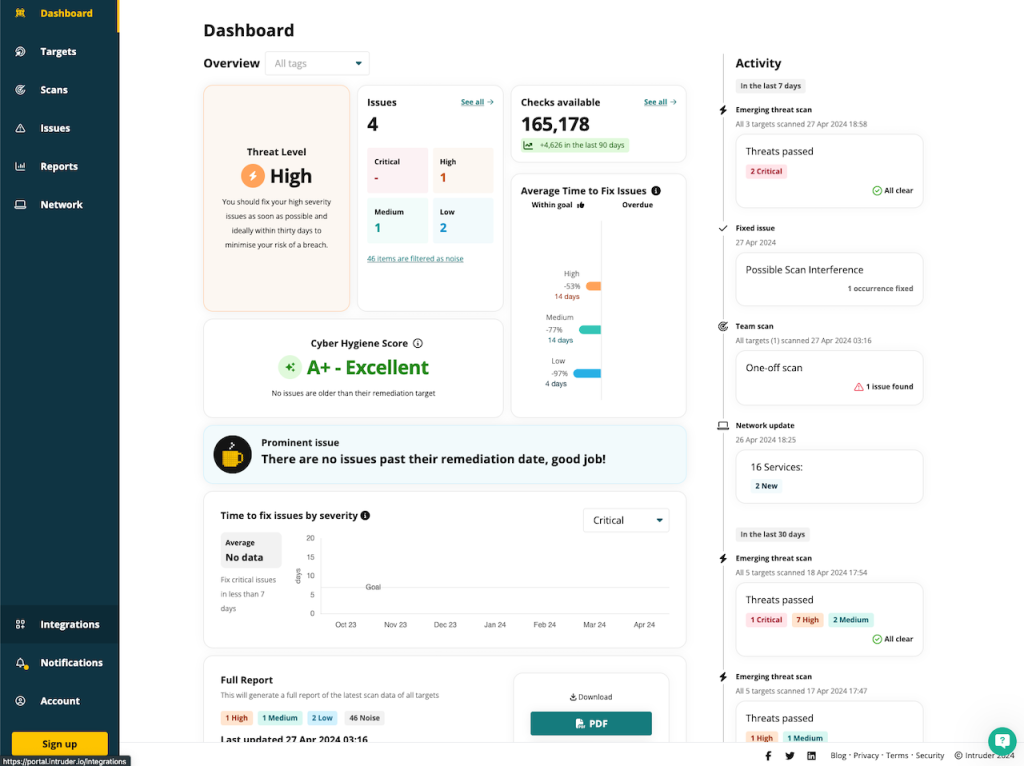
Vulnerability Prioritization with Attaxion
Attaxion is not very different from Intruder.io in this regard. It offers a list of all vulnerabilities that can be sorted by asset, by severity, CVSS score, or date when the issue was last or first seen.
Above the list, there’s a dashboard that shows the distribution of vulnerabilities by CVSS and severity, as well as a graph showing how this has been changing over time.
Attaxion similarly offers to mark issues as accepted risks, false positives, or fixed. There’s no option to manually trigger a scan though.
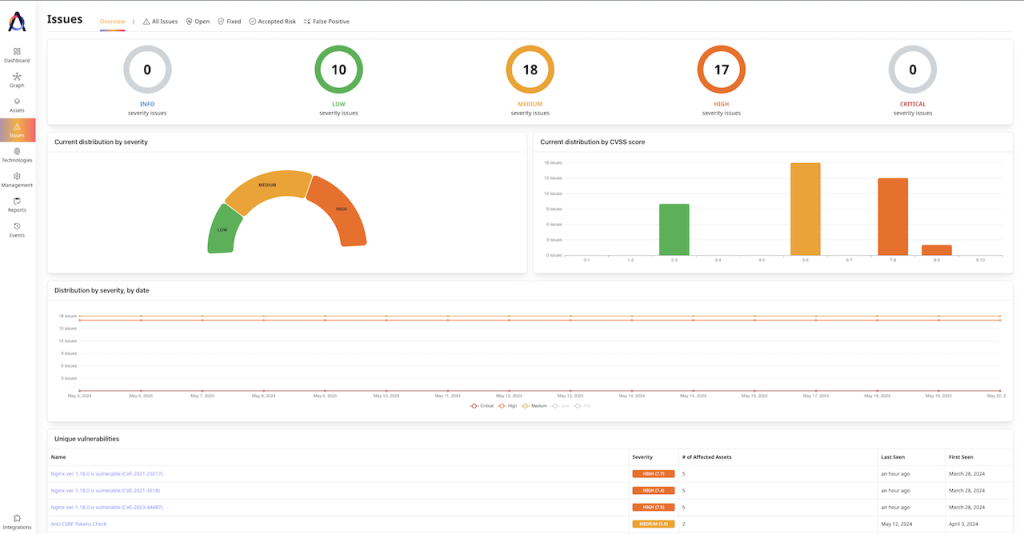
How They Compare
When it comes to prioritization, Intruder and Attaxion are almost equal. Both offer the necessary, neither provides fancy features such proprietary severity scores.
 PART 5
PART 5
Vulnerability Remediation
Vulnerability remediation in case of vulnerability management platforms usually boils down to providing suggestions and automating routine tasks such as creating tickets for support engineers. Attaxion and Intruder are similar in this regard.
| Intruder.io vs Attaxion: Vulnerability Remediation | ||
| Attaxion | Intruder | |
| Remediation suggestions | ✅ | ✅ |
| Integrations with ticketing software | Jira | Jira GitHub GitLab Azure DevOps Service Now |
| Remediation dashboard | ❌ | ✅ |
| API | ❌ | ✅ |
Remediation with Intruder
For each vulnerability, in addition to description, Intruder offers remediation suggestions, as well as scanner output.
Intruder offers a broad set of integrations that help simplify the remediation process. It can automatically create issues in Jira, GitHub, GitLab, Azure DevOps, and ServiceNow. It also offers an API to connect to other cybersecurity software. An integration with Zapier serves the same purpose.
Intruder offers very convenient dashboards that, among other things, show how the security team is handling vulnerability remediation. It provides metrics such as average time to fix issues (for different severities) and offers a graph to show how this changes over time.
Remediation with Attaxion
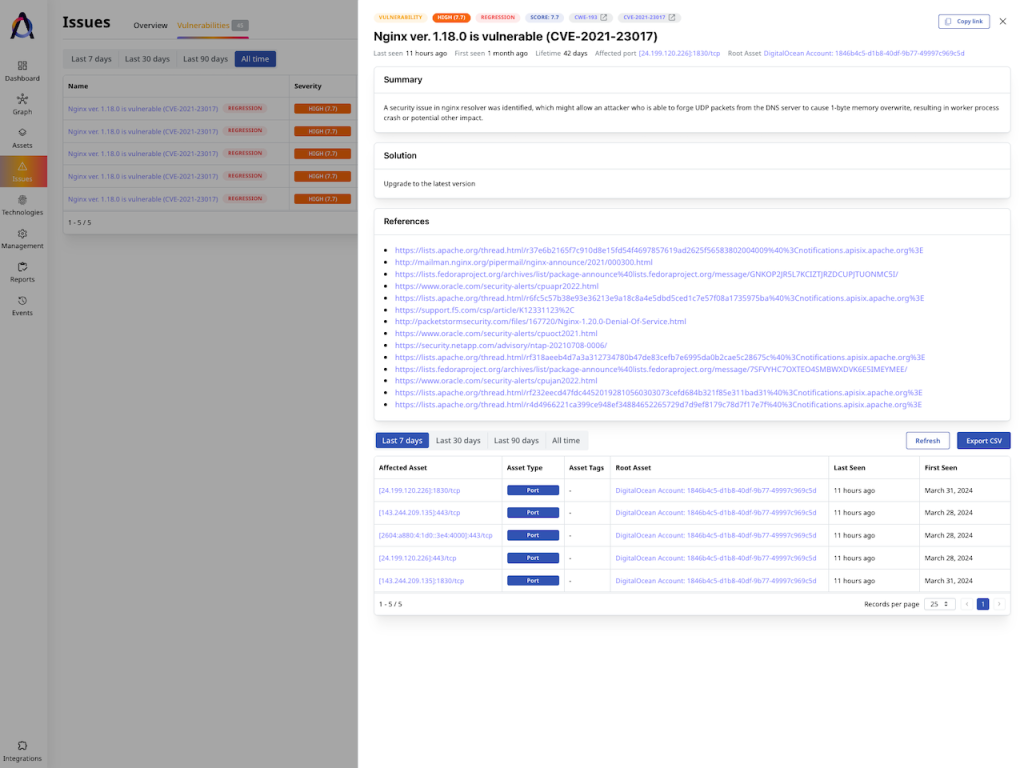
Attaxion also provides vulnerability description, evidence, and remediation suggestions from different sources, sometimes offering more detailed advice than Intruder.
When it comes to integrations relevant for the remediation stage, Attaxion has an integration with Jira that can create tickets pre-populated with vulnerability data. There aren’t any other integrations with ticketing software currently available, but you can reach out to Attaxion support and discuss the integrations you require with them.
How They Compare
Overall, when it comes to remediation, both platforms offer the two main things: advice and the ability to create tickets in bug trackers. Both Attaxion and Intruder refer to multiple sources for remediation suggestions.
However, Intruder has a broader set of integrations and an API.
 PART 6
PART 6
Continuous Monitoring
We’ve described most of the features related to continuous monitoring in Asset Discovery and Inventory and Vulnerability Detection sections. Basically, both tools just keep using them continuously.
| Intruder.io vs Attaxion: Continuous Monitoring | ||
| Attaxion | Intruder | |
| Continuous attack surface discovery | ✅ | ❌ |
| Email notifications | ✅ | ✅ |
| Customizable notifications | ❌ | ✅ |
| Integrations with messaging software | Slack | SlackMicrosoft Teams |
| Remediation dashboard | ❌ | ✅ |
| API | ❌ | ✅ |
Continuous Monitoring with Intruder.io
Intruder.io offers regular vulnerability scans and emerging threat scans (as well as rapid response scans on the Custom plan).
You can set up notifications for certain events that happen during scans.
Intruder offers very flexible email notifications, where you can choose to be notified about targets being affected or not affected by emerging threats, about completion of manual scans, and of the overall network status.
It also has integrations with Slack and Teams to send notifications via these messengers.
Continuous Monitoring with Attaxion
As mentioned earlier, Attaxion continuously keeps scanning the organization’s attack surface. Unlike Intruder, it can discover new assets – and run vulnerability scans against them.
Basically, Attaxion automates continuous monitoring of the whole external attack surface, while with Intruder, you’ll need to manually add new assets as they appear in the organization’s network.
Attaxion also offers email notifications and has an integration with Slack.
How They Compare
Attaxion can continuously monitor the changing external attack surface, while Intruder.io keeps track only of the assets that you’ve added manually.
On the other hand, Intruder is more flexible when it comes to notifications, thanks to the broader set of integrations and extensively customizable email alerts.
 PART 7
PART 7
Conclusion
Intruder.io is a solid vulnerability scanner with a very user-friendly interface. Its strong sides are its dashboards, reports, and notifications, as well as a broad set of integrations. However, Intruder.io completely ignores the discovery step of the vulnerability management process and doesn’t offer subdomain enumeration.
Attaxion, on the other hand, has unique reconnaissance capabilities that allow it to discover and scan previously unknown external assets more effectively than the other tools on the market. It covers all 5 steps of the vulnerability management process, protecting the organization’s external attack surface on a completely different level. However, being an EASM platform, Attaxion doesn’t help with scanning internal assets.
In most cases, Attaxion is also less expensive than Intruder, saving some of the precious cybersecurity budget for other necessary tools.
Ready to try Attaxion EASM? Start a 30-day free trial, or request a personal demo.