Assess Mergers & Acquisitions Security Risks
Get a complete inventory of the target’s external infrastructure for M&A due diligence, evaluate, prioritize, and remediate inherited risks.
What our clients say
Get Complete Visibility During Due Diligence
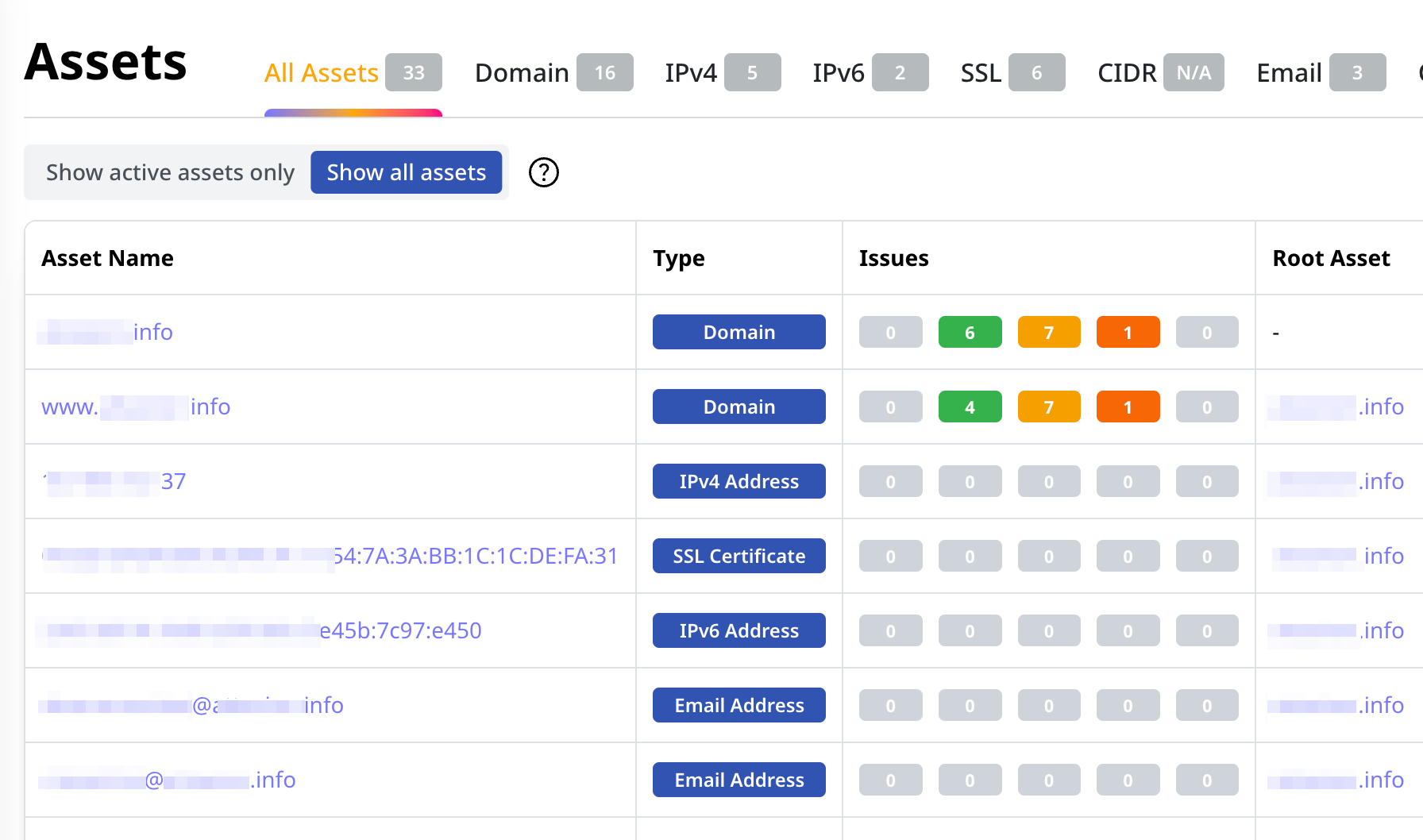
Attaxion quickly provides you with a comprehensive inventory of all the target’s web-facing assets, uncovering shadow IT and forgotten infrastructure.
Learn more:
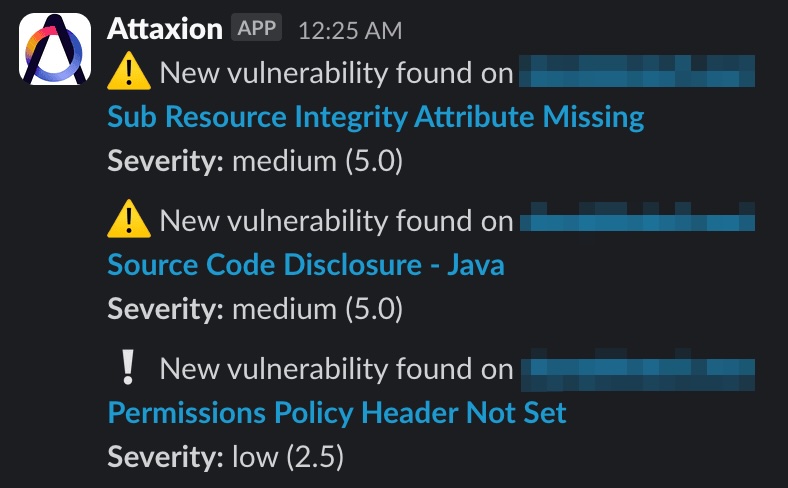
Evaluate Inherited Risk
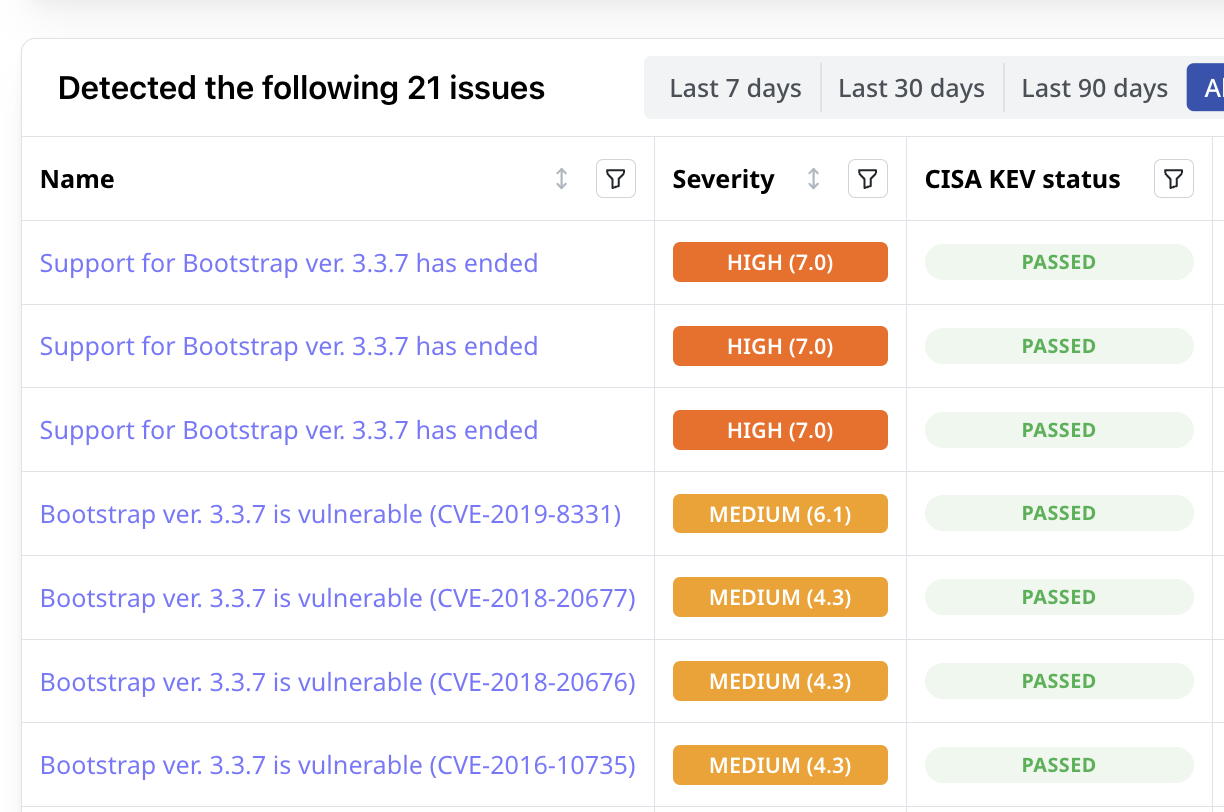
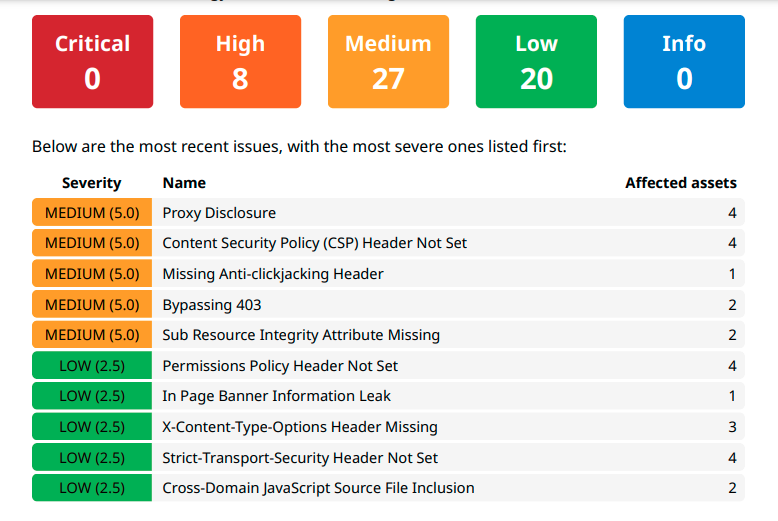
Scan the entire external attack surface of the target company for vulnerabilities and misconfigurations, identifying risks, software dependencies, and third-party connections that you are going to inherit with the merger.
Learn more:
Understand the Impact on the Deal Valuation
Learn about potential exposures, data leaks, compliance gaps, and other cybersecurity issues that can affect deal value.
Easily communicate them to stakeholders with Attaxion’s dashboards and reports.
Remediate Smarter
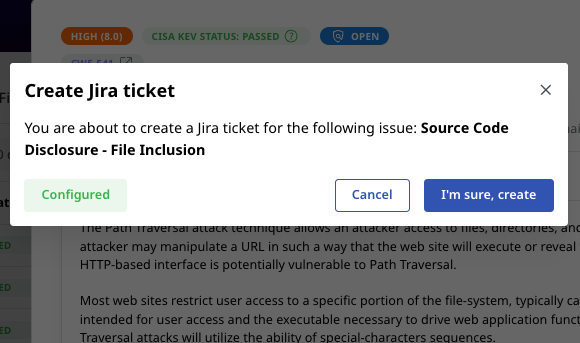
Prioritize cybersecurity issues based on exploitability and the actual impact they might have. Speed up remediation efforts with 1-click support ticket creation.
Learn more:
Manage Risks for the Combined Entity
Attaxion continuously notifies you about emerging risks throughout the merger process with the communication channel of your choice.
Learn more:
Start Using Attaxion for M&A Due Diligence
Get started in a few clicks and get the first results in 2 hours. Attaxion is easy to navigate and provides a complete image of your organization’s external attack surface, including third-party technology.
Why Choose Attaxion for M&A Risk Assessment?
-
Highest Asset Coverage
Attaxion can discover more external assets than other solutions, ensuring comprehensive visibility into the target’s external attack surface and reducing inherited risk.
-
Pricing for Any Budget
Whether the acquisition target is a small startup or a large enterprise, Attaxion has the right pricing plan for you that scales together with the company.
-
Start Right Away
Attaxion doesn’t require deployment or integration development – you can start in mere minutes and get a full overview of the external infrastructure of the target company in a couple of days.
Frequently Asked Questions
Featured Resources

10 Critical Attack Surface Metrics to Track
With recent regulatory changes pushing cybersecurity to the boardroom, effective attack surface monitoring and visualization techniques are more cruci[...]

Detecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the reason can be a security weaknes[...]

NIS 2 Compliance: From Asset Discovery to Risk Management
No entity across industries and regions is safe from cyber attacks. The European Union (EU) Agency for Cybersecurity (ENISA) annual Threat Landscape R[...]