For IT and SaaS
Identify all external assets and address security gaps in hosted applications and IT environments.
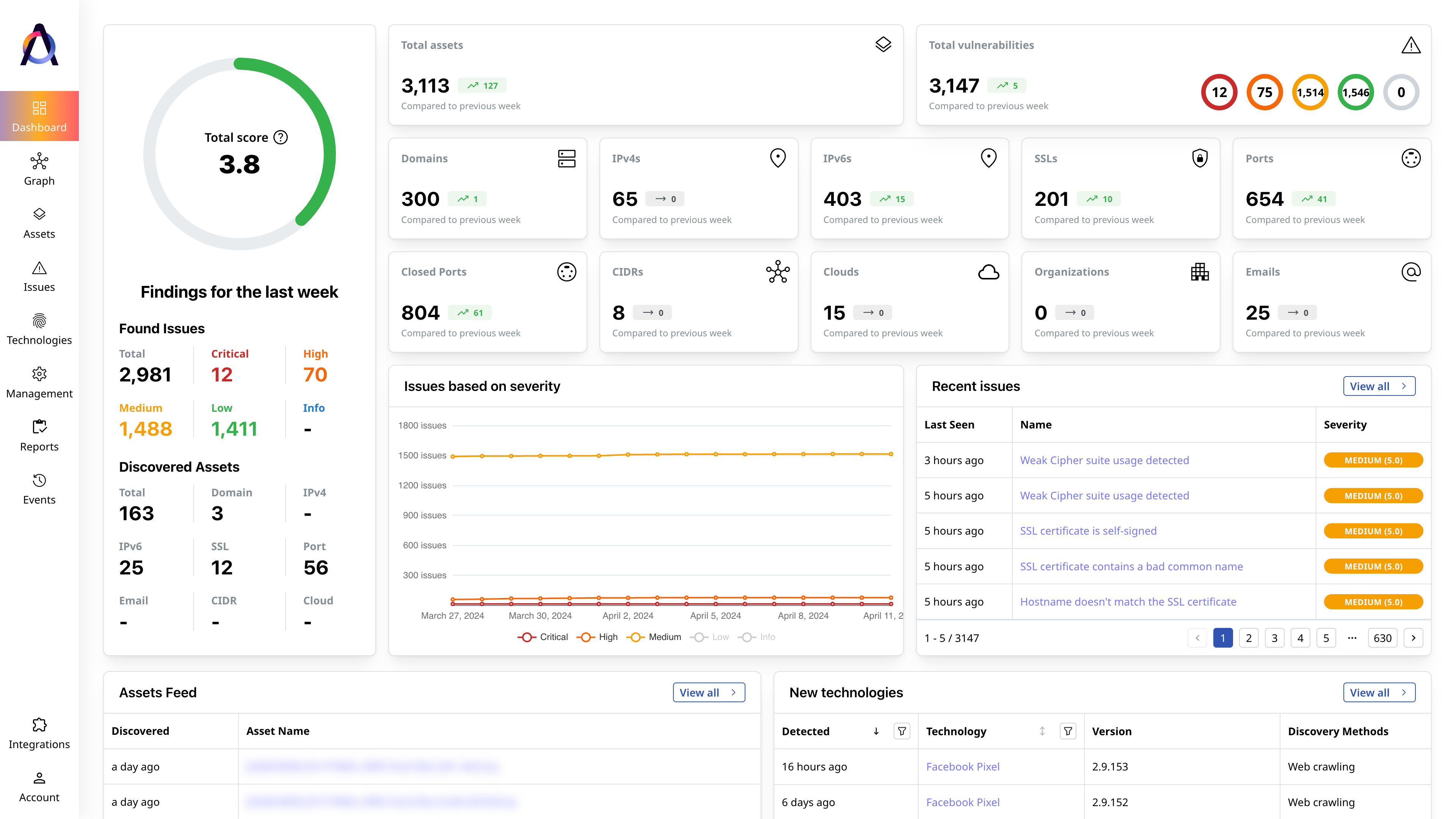
Detect all exposed assets, including cloud-hosted shadow IT
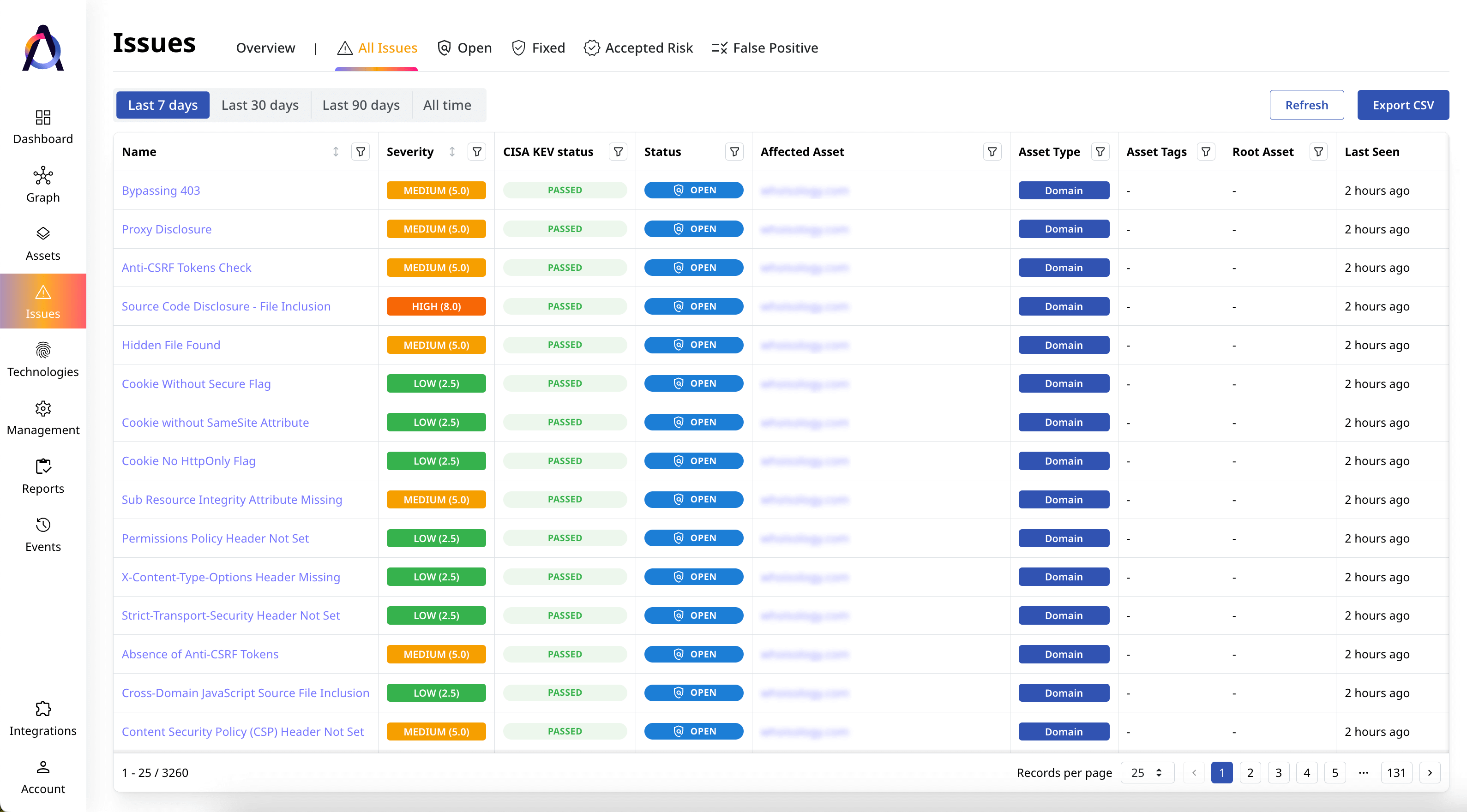
Find and catalog all known and unknown assets and their technologies across your Internet-facing applications and systems.
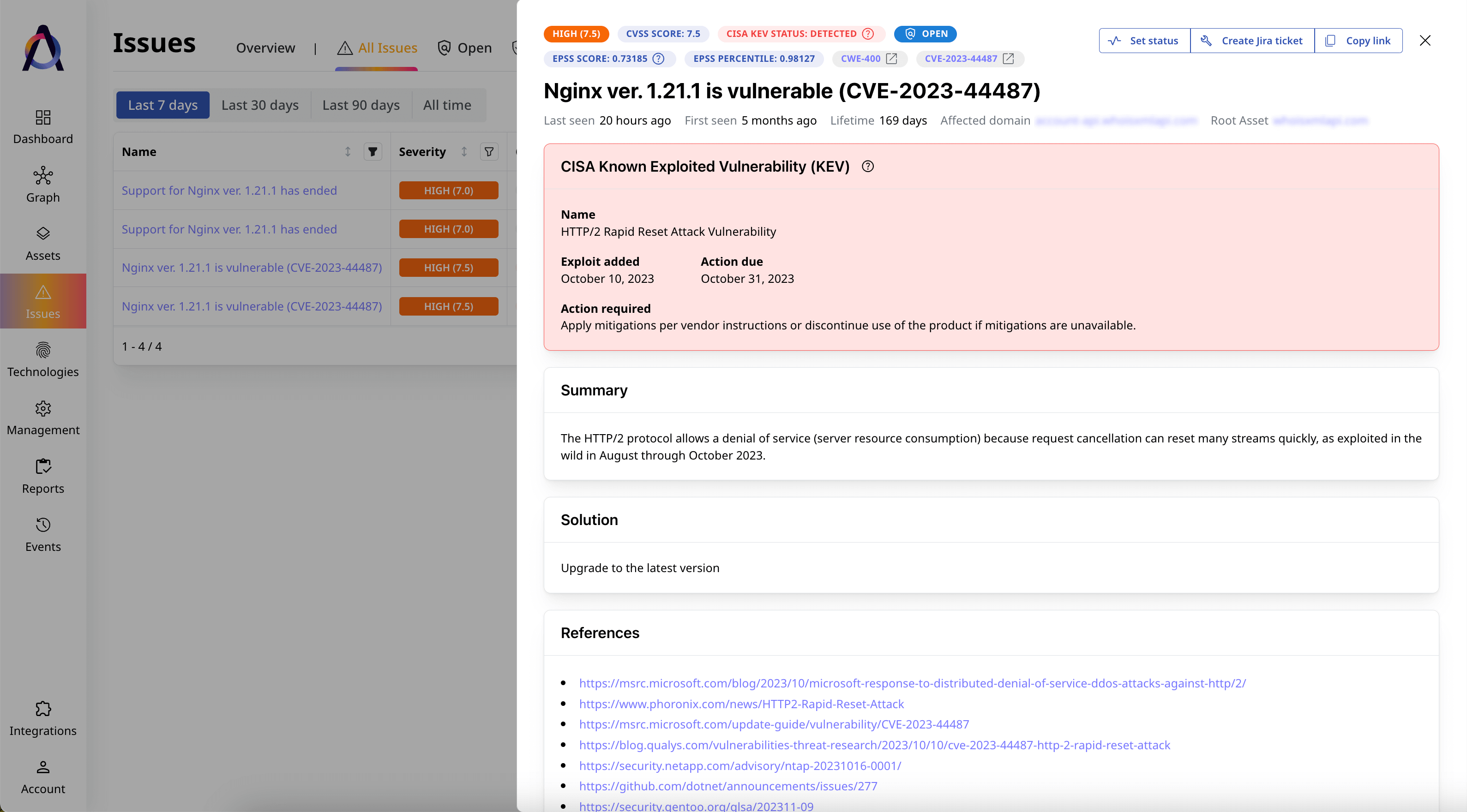
Uncover and prioritize security issues
Prioritize vulnerabilities based on their severity and potential impact on application development and performance.
Track and tackle emerging risks
Continuously find new assets and address emerging security issues in your public-facing IT environment.
-
Complete Inventory
Access dedicated catalogs of your Internet-facing assets and their issues.
-
Cloud Provider Integration
Monitor known and unknown cloud assets across popular cloud providers.
-
Detailed Reporting
Review your overall security posture and drill down on each issue.
What security experts say
Featured Resources

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

CWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like CWE, CVE, and CVSS. These term[...]

How to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sensitive information, or disrupt[...]