External Attack Surface Management (EASM): The Complete Starter Guide
What Is External Attack Surface Management?
External attack surface management (EASM) is the process of continuous discovery, validation, prioritization, and remediation of exploitable vulnerabilities in an organization’s Internet-facing systems.
Cybersecurity tools used for this process are referred to as EASM solutions or platforms.
Table of Contents
 PART 1
PART 1
What Is an External Attack Surface?
An organization’s external attack surface is the sum of its digital assets accessible via the Internet and the attack vectors associated with them. It includes known, unknown, and forgotten assets and their vulnerabilities.
Over time, this surface keeps growing due to digital transformation, increased interconnectivity, and cloud migration. Gartner has identified attack surface expansion as the number 1 trend leaders must address.
One of the main tasks for cybersecurity teams is attack surface reduction – identifying and mitigating security risks.
What Contributes to Your External Attack Surface?
Examples of sources of weaknesses that make up an external attack surface include:
Misconfigurations in websites and web applications
Among other known techniques, threat actors can exploit site and application vulnerabilities through input validation, SQL injection, or XSS to gain unauthorized access to systems or compromise user data.
Third-party services
Businesses rely on third-party software-as-a-service (SaaS) providers for an increasing number of tasks – web analytics, client relations management, customer support, and more. These providers often need to connect to your infrastructure, adding new subdomains and thus contributing to your organization’s external attack surface in the process.
According to the State of Information Security Report 2024, 79% of businesses have been impacted due to an cybersecurity incident caused by a third-party provider or a supply chain partner.
Cloud storage
With 67% of enterprise infrastructure being based in the cloud and more and more workloads migrating there, the role of cloud storage becomes more and more critical for organizations of all sizes. As a result, the associated risks become more prominent – according to the NSA, attackers exploiting misconfigured cloud storage is the number one problem when it comes to cloud security.
As the demand for cloud storage continues to grow, so do the size and frequency of data breaches. In 2024 alone, Cisco, Fortinet, AT&T, JP Morgan Chase, Dropbox, Trello, and Bank of America alongside many smaller organizations experienced data breaches.
Unsecured open ports
Network ports that are left open to receive incoming communications may become security risks, as attackers often exploit open ports to access related systems and files.
For instance, RDP ports can be used for credential stuffing attacks or delivering ransomware payloads, while SSH port can leak SSH keys and SMTP port is often used for man-in-the-middle attacks.
Shadow IT
Shadow IT — the technological resources that somebody in an organization uses without the IT department’s knowledge or approval — is another prominent contributor to the organization’s digital attack surface.
Shadow IT assets are prone to misconfigurations, insecure data storage, and weak access controls.
To address the increasing amount of external cyber threats, cybersecurity teams employ external attack surface management solutions which can identify misconfigurations in web apps and cloud storage, discover shadow IT assets, find unsecured open ports, and highlight security weaknesses in third-party services.
Use Attaxion – the EASM platform that can discover more assets than any other – to get a bird’s eye view of your external attack surface, prioritize patching vulnerabilities, and plan remediation.
Or take a 60-second guided tour to see how EASM platforms work:
 PART 2
PART 2
How Does External Attack Surface Management Work?
EASM is a cyclical process that starts with attack surface discovery, followed by vulnerability prioritization, remediation, and continuous monitoring. These phases utilize a combination of automated and manual operations described in greater detail below.
Step #1: Attack Surface Discovery
The first step in the EASM process – just like in NIST or CIS cybersecurity frameworks – is discovering and cataloging everything that contributes to the organization’s external attack surface.
Attack surface discovery consists of three main processes:
- external asset enumeration,
- asset validation,
- vulnerability detection.
External asset enumeration
The first step in EASM is to catalog all Internet-facing assets, which may include:
- IP addresses
- CIDR blocks
- Domain names
- Subdomains
- SSL certificates
In this phase, EASM solutions require several root assets belonging to your organization as a starting point and use modern reconnaissance techniques similar to known attacker methods to survey the organization’s external infrastructure and find more public-facing assets.
External attack surface management techniques include:
- Subdomain enumeration
- Port scanning
- Network mapping
- SSL Lookup
- And more
In addition to that, some external attack surface management tools like Attaxion perform port scanning to find and catalog open ports and can also find exposed email addresses.
Asset validation
After building a complete asset inventory, the next step is validating the assets to ensure they are attributable to a target organization. That is done through rule-based heuristics, ML algorithm usage, and other contextualization techniques.
Asset validation helps build an accurate external asset inventory with as few false positives as possible.
Vulnerability detection
The last step of attack surface discovery is vulnerability detection, where the EASM platform scans all attributable assets to search for issues, misconfigurations, and other potential vulnerabilities.
Domain names, for example, are scanned to check if their DNS records are configured correctly. IP addresses and linked connected servers, meanwhile, are checked for suboptimal cipher suites, among other weaknesses.
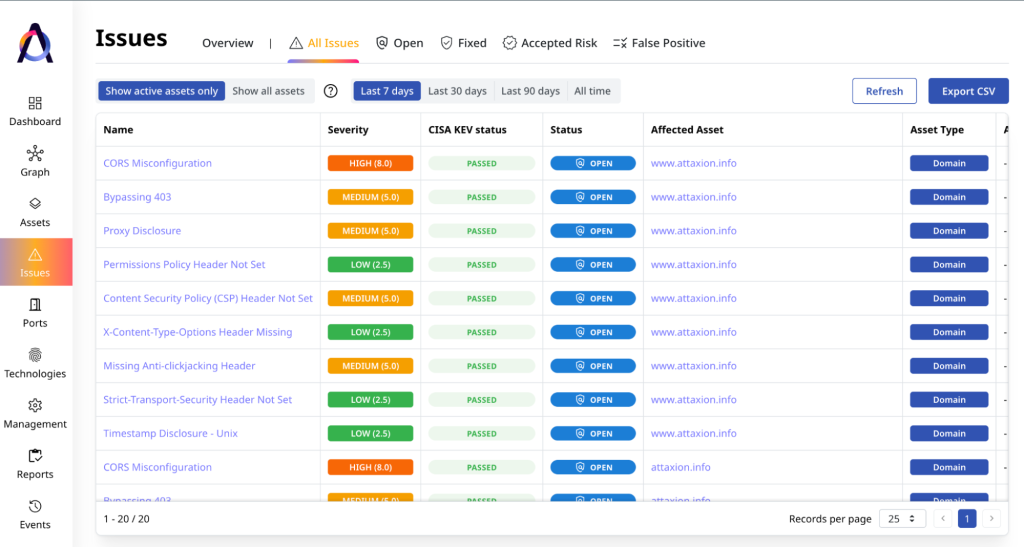
All assets are tested for new and emerging CVEs.
EASM platforms rely on collecting data about new vulnerabilities from various sources – from CERT (Computer Emergency Response Team) portals of various organizations to crowdsourced directories.
By discovering and cataloging the vulnerable assets and their vulnerabilities EASM platforms provide cybersecurity teams with a complete overview of the organization’s external attack surface.
Step #2: Vulnerability Prioritization
Not all vulnerabilities pose the same level of risk. As such, accurate prioritization through risk scoring is a must to address the most critical issues first. That way, teams can efficiently focus their efforts on the bugs that matter most.
Vulnerability scoring can be done automatically based on the following criteria:
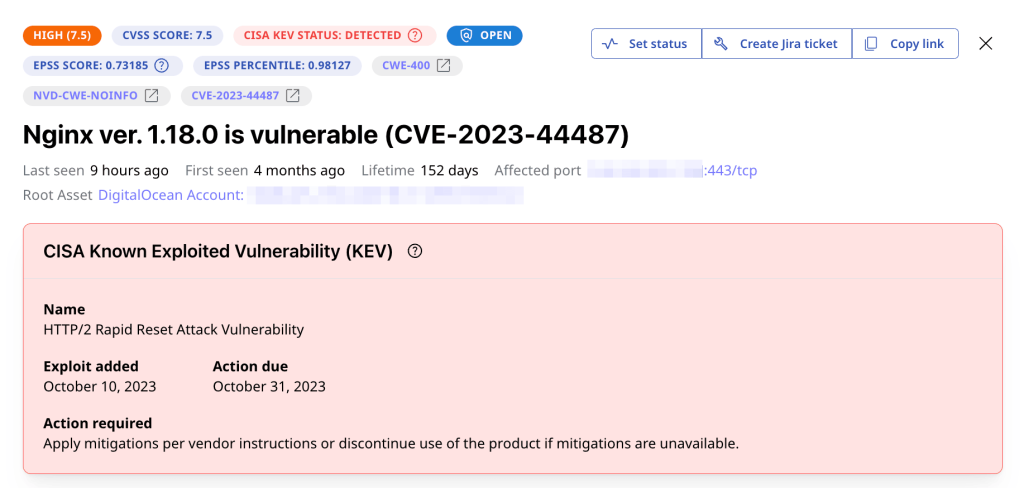
- Severity. The importance of each affected asset and the amount of damage the vulnerability can cause. This is usually measured using CVSS (Common Vulnerability Scoring System) score on a scale from 0 to 10, where 10 is the CVSS score of the most critical vulnerabilities.
- Exploitability. The ease at which attackers can exploit the vulnerability. This is measured using EPSS (Exploit Prediction Scoring System) score that’s calculated based on exploit availability and complexity, asset exposure, and other parameters. EPSS has a scale from 0 to 1 where 1 is the highest likelihood of exploitation.
- Relevance. The likelihood that the organization would be targeted by malicious actors known for exploiting certain vulnerabilities.
Intelligent EASM platforms consider all these factors while allowing for customization.
Step #3: Vulnerability Remediation
At this point, security teams devise remediation plans to address high-priority vulnerabilities and implement these with the EASM platform’s help. EASM platforms usually have integrations with bug tracking or project management systems such as Atlassian Jira to help team leaders quickly assign, track, and close tasks related to vulnerability remediation to speed up attack surface reduction.
EASM tools like Attaxion allow you to create tickets populated with all necessary vulnerability details in one click.
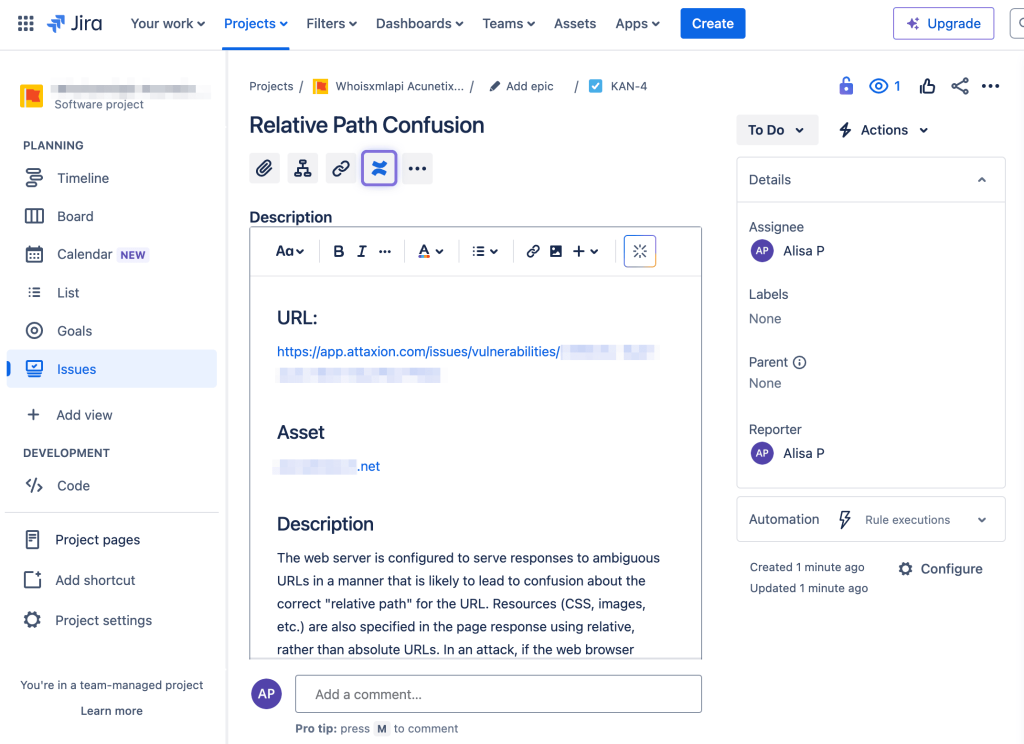
With organizations often requiring days to resolve a security issue, automated remediation workflows are crucial in reducing the MTTR (mean time to resolution).
Step #4: Continuous Attack Surface Monitoring
Even as organizations eliminate attack vectors, new ones get added over the course of business operations, especially those involving digital transformation, cloud migration, and mergers and acquisitions (M&As).
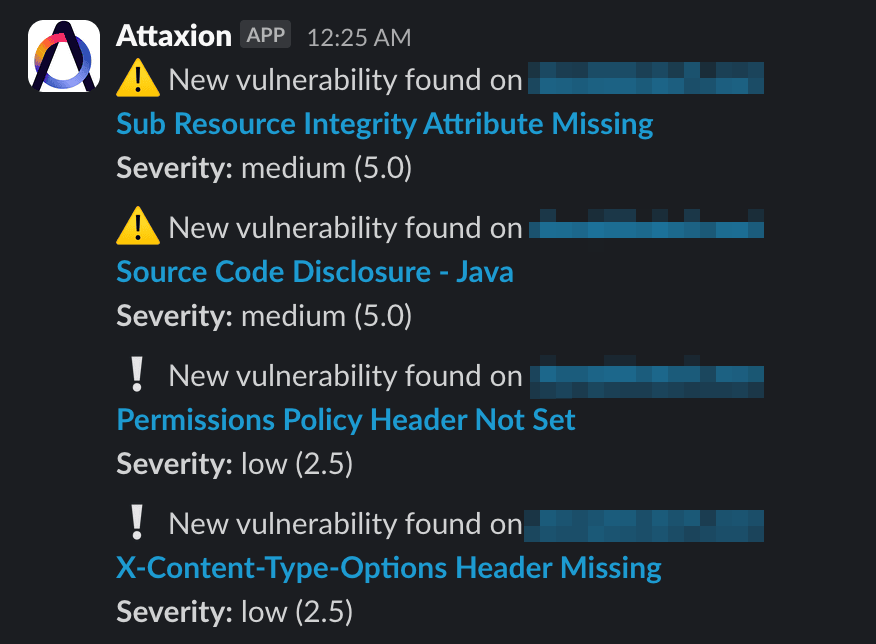
As such, continuous visibility across the organization’s real-time external attack surface is necessary. EASM platforms usually do that by continually discovering, validating, and scanning new assets for existing and emerging vulnerabilities.
They are capable of promptly notifying security teams of the new findings via email or using integrations with instant messaging systems like Slack.
 PART 3
PART 3
The Benefits of External Attack Surface Management
External attack surface management platforms offer a number of benefits to cybersecurity teams:
- Outside-in perspective. EASM tools look at the organization’s infrastructure the same way a potential attacker does.
- Complete external asset inventory. What makes EASM platforms unique in the cybersecurity tools market is that they allow you to automatically create a continuously updated inventory of the organization’s external assets. Relying on an EASM platform for this task saves a lot of time and effort in comparison with doing it manually. And thanks to EASM platform’s capability of discovering unknown assets, it provides a more complete picture than what can be achieved manually.
- Holistic overview of the organization’s external attack surface. Since, in addition to discovering known and unknown assets, EASM platforms scan them for vulnerabilities, they provide you with a comprehensive picture of your organization’s external attack surface.
- Faster investigation and response. Due to the continuous nature of the scanning that EASM platforms perform, they help find new issues quickly, which helps proactively patch the most critical vulnerabilities before attackers attempt to exploit them.
 PART 4
PART 4
External Attack Surface Management Use Cases
As a process, external attack surface management helps organizations strengthen their security posture and is beneficial on its own. In addition to that, EASM platforms help enable other cybersecurity processes and tasks.
✅ Asset inventory management
Asset inventory management is the process of identifying and cataloging all of an organization’s IT assets.
EASM platforms completely cover the external asset discovery and validation, providing IT teams with an always up-to-date list of the organization’s internet-facing assets.
Relying on EASM platforms for this task instead of doing it manually saves cybersecurity teams plenty of time while also improving the quality of the result, as EASM platforms can discover unknown and forgotten assets.
✅ Risk-based vulnerability management (RBVM)
Also known as vulnerability risk management (VRM), risk-based vulnerability management takes into account the business context of an asset in addition to vulnerability severity, exploitability, and relevance. The higher the business criticality of an asset, the more severe the impact of potential security incidents, and the higher the priority given to the associated cyber risks.
EASM platforms help discover external assets and their respective vulnerabilities, while offering flexible automated scoring systems. Relying on an EASM platform allows cybersecurity teams to introduce risk-based vulnerability management in the organization, improving its security posture by prioritizing the highest risks first.
✅ Cloud security posture management (CSPM):
CSPM consists of discovering incorrect or weak cloud asset configurations and identifying cloud policy violations and potential compliance risks.
EASM platforms like Attaxion have cloud connectors with popular cloud platforms such as AWS, GCP, Microsoft Azure, and Digital Ocean to help cybersecurity teams inventory their cloud infrastructure and identify and score related risks.
✅ Third-party risk management (TPRM)
TPRM is the process of identifying, assessing, and mitigating risks associated with using third-party vendors or service providers. Third-party risks are on the rise: according to Hyperproof, in 2024, 62% of organizations reported experiencing a supply chain disruption related to cybersecurity, 13% more than the previous year.
EASM platforms like Attaxion create a third-party technology inventory for each website or web application in your organization’s attack surface and find misconfigurations and other vulnerabilities in the discovered third-party software. They also help identify connections with third-party websites and potential exposures, helping enable TPRM in your organization.
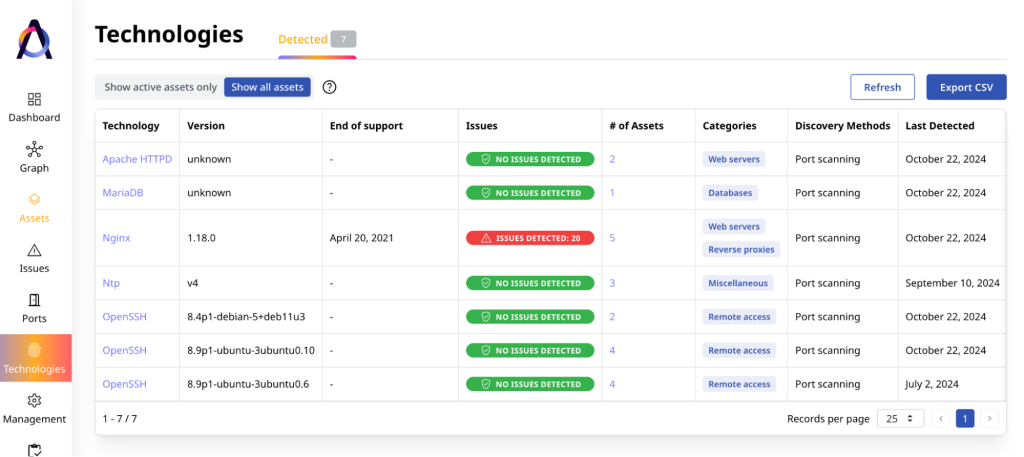
✅ Network segmentation
Some EASM platforms like Attaxion provide discovery and dependency graphs for the organization’s assets, showing potential attack paths and attack vectors. These graphs serve as a great tool for planning network segmentation to better contain the spread of a successful attack.
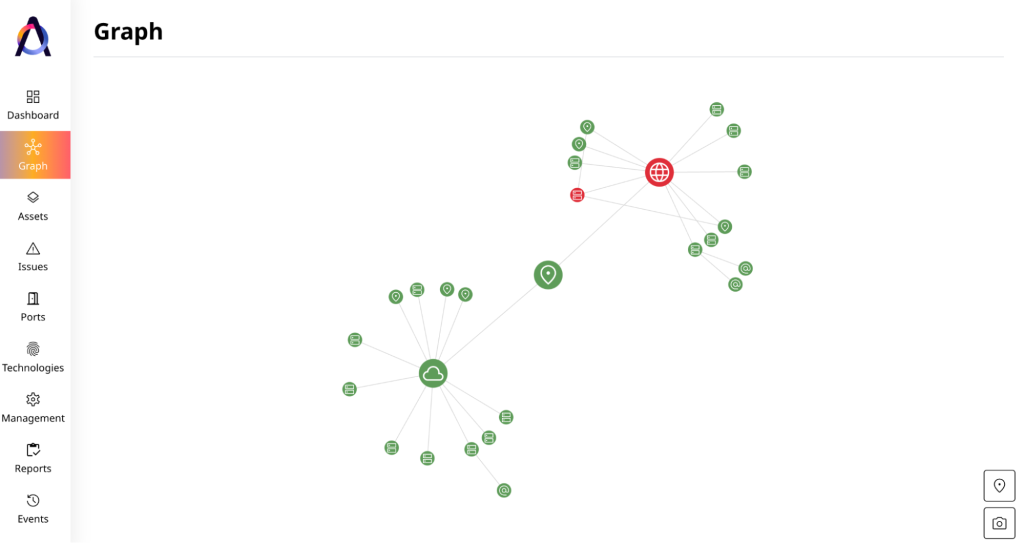
✅ M&A due diligence
Information technology due diligence of an acquisition target includes discovering and enumerating its known and unknown internet-facing assets and assessing their risk levels to determine potential threats and next steps in due diligence.
EASM platforms help quickly identify and inventory the acquisition target’s assets and do a comprehensive risk assessment.
✅ Regulatory compliance
Compliance with standards and regulations like GDPR, HIPAA, and PCI DSS requires organizations to protect sensitive data, patch vulnerabilities, and report cybersecurity incidents.
EASM platforms support compliance by identifying external-facing assets, assessing their configurations, and flagging non-compliance risks. By continuously monitoring an organization’s digital footprint, they help security teams prioritize issues and maintain compliance with relevant regulations and standards.
 PART 4
PART 4
EASM for Red and Blue Cybersecurity Teams
EASM for Red Teams
Red teaming is a cybersecurity exercise that relies on using tactics, techniques, and procedures (TTPs) simulating real-life attacks to help measure how well an organization can defend itself against cyber threats and malicious actors.
Red teams (the ones simulating the attacker) rely on cyber reconnaissance techniques to map the organization’s external-facing assets. They then use vulnerability scanners to identify weaknesses and discover potential attack vectors.
Usually, red teams use a mix of free and open-source tools for these purposes. However, they can save time and effort by relying on an EASM tool that does all the reconnaissance and vulnerability scanning for them automatically.
EASM for Blue Teams
In the same teaming exercise, the blue team is the one to defend the organization against the red team’s efforts. Their responsibility is reducing the attack surface — ensuring that all external-facing assets are secure and rid of misconfigurations, the network is properly segmented to contain threats, and new issues are addressed timely and effectively.
Using a good EASM platform is a must for blue teams, as it allows them to get a holistic view of the organization’s external infrastructure, discover all shadow IT assets, understand the risk that each asset poses, and prioritize issues based on their severity and exploitability.
Overall, EASM helps blue teams adopt a more proactive approach to cybersecurity.
 PART 5
PART 5
How Can Attaxion Help with External Attack Surface Management?
Attaxion is an EASM platform with the highest asset coverage and flexible pricing. It helps organizations of all sizes – from SMBs to large enterprises – to map out their entire external attack surfaces in real time, discovering known, unknown, and forgotten assets with very few false positives. It gives you a complete picture of the third-party technologies you’re using across your organization’s external infrastructure to enable TPRM.
Attaxion uses dynamic application scanning to find vulnerabilities and misconfigurations in the discovered assets, providing you with a holistic overview of your entire external attack surface. It offers CVSS and EPSS scores for all CVE issues, as well as CISA KEV data about vulnerabilities that are known to be exploited in the wild.
Continuous monitoring and notifications allow you to be on top of all newly discovered assets and vulnerabilities, effectively prioritizing them and remediating them before attackers can exploit them.
Ready to see Attaxion in action? Schedule a personal demo now or start a 30-day free trial.
Learn More
 PART 6
PART 6
Frequently Asked Questions
-
EASM vs ASM: What is the difference?
EASM is often confused with attack surface management (ASM). In fact, EASM is a part of the broader ASM process, which consists of three parts:
– EASM (external attack surface management);
– CAASM (cyber asset attack surface management);
– DRPS (digital risk protection services).Below are some of the differentiating factors between EASM and ASM.
– Asset discovery scope. EASM focuses on external-facing assets accessible from outside an organization’s network, such as websites, web applications, and APIs. ASM, meanwhile, deals with both internal and external assets. Internal systems such as employee portals and physical access points like server rooms, employee entrances, and data centers can only be accessed from inside a network; they require a tool that works differently than EASM. So, ASM relies on CAASM for analysis of such assets, which, in turn, relies on pre-made asset lists and APIs to collect information.
– Perspective. EASM looks at a digital infrastructure from an external attackers’ perspective. By looking from the outside in, it aims to see how threat actors can exploit vulnerabilities and gain unauthorized access. Meanwhile, CAASM looks at the asset from the inside out, assuming the blue team’s perspective. Both EASM and CAASM are important parts of ASM, which considers potential risks from all sources, including insider threats, external attackers, and supply chain vulnerabilities.
– Implementation. EASM involves using specialized tools and platforms designed to scan and assess an organization’s external-facing resources. Thanks to the outside-in approach, EASM platforms are easy to set up, don’t require a lot of integrations, and are heavily automated. In contrast, ASM typically requires a combination of tools as well as processes like employee training to prevent social engineering attacks as part of managing one’s overall attack surface holistically. -
EASM vs Vulnerability Management
Vulnerability management is the process of continuous discovery, prioritization, and remediation of security vulnerabilities in an organization’s IT infrastructure and software. Vulnerability management platforms use passive and active vulnerability scanners to discover and validate issues in the organization’s assets.
External attack surface management might seem somewhat similar to vulnerability management, but there are a few important differences.
– Asset discovery. Vulnerability management considers vulnerabilities in a pre-defined list of the organization’s assets and doesn’t include asset discovery. Vulnerability management requires an asset inventory to start. EASM, on the other hand, does include asset discovery, which helps find and manage vulnerabilities in previously unknown or forgotten assets.
– Scope. Vulnerability management focuses on vulnerabilities in both internal and external assets, while EASM deals only with external assets.Overall, vulnerability management – scanning for, prioritizing, and remediation of vulnerabilities in the organization’s infrastructure – is considered to be a part of the attack surface management process.
-
EASM vs CAASM
Both external attack surface management and cyber asset attack surface management (CAASM) deal with managing an organization’s attack surface, and both are part of the overarching ASM process. However, EASM and CAASM differ in scope, data sources, and approach.
– Scope. EASM focuses solely on an organization’s external attack surface, encompassing all Internet-facing assets like websites, APIs, cloud resources, and exposed vulnerabilities. CAASM covers both internal and external assets, including servers, devices, applications, user accounts within a network, and their external components.
– Data sources. EASM relies on external data sources like Internet scans, vulnerability databases, and threat intelligence feeds to discover and analyze assets. CAASM leverages internal data sources, such as asset inventories, security tools, and endpoint management systems, to identify and assess assets. For additional context, CAASM may also rely on external data sources, including EASM platforms.
– Approach. EASM primarily focuses on attack vectors and vulnerabilities associated with external assets, prioritizing risks based on their potential impact. Meanwhile, CAASM provides a holistic view of the entire attack surface, considering relationships between internal and external assets, user behaviors, and potential insider threats.CAASM can be seen as an extension of EASM. EASM platforms are often used as the main source of asset data for CAASM, providing specialized insights into external threats and attack vectors.
-
EASM vs DRPS
EASM and digital risk protection services (DRPS) are both parts of the ASM process and play important roles in an organization’s cybersecurity processes, but the difference between them is significant.
EASM is a proactive approach to minimizing technical vulnerabilities in the external attack surface. It identifies and prioritizes weaknesses in Internet-facing assets like websites, APIs, and cloud resources to prevent exploitation.
Meanwhile, DRPS is a reactive approach that focuses on monitoring and mitigating reputational and brand risks stemming from digital data exposure. It proactively searches for sensitive information leakage and brand mentions across the Internet, including dark web forums and social media, to prevent or respond to data breaches and reputational damage.
EASM and DRPS complement each other. EASM actively minimizes vulnerabilities, while DRPS monitors for data breaches and branding-related threats arising from successful targeted attacks or even human error.
Some EASM platforms like Attaxion can discover exposed email addresses to reduce the risk of phishing attacks, which creates a slight overlap between these platforms and DRPS.
-
EASM vs DAST
Dynamic application security testing platforms are often very similar in functionality to EASM platforms. But there are two important differences between EASM and DAST.
EASM’s primary focus is asset discovery, while DAST platforms either often don’t have asset discovery at all or limit themselves to basic subdomain enumeration capabilities.
DAST scanning is usually payload-based and quite intrusive. A DAST scan in a production environment might cause some disturbances and downtime. EASM platforms are usually less intrusive, which allows them to continuously scan the organization’s attack surface without causing any outages. However, some EASM platforms actually use DAST scanners to find issues in discovered assets after mapping the attack surface.
Overall, an EASM platform is a better choice than a DAST scanner in situations where you need visibility into all external assets that you have instead of focusing on a select few.
-
EASM vs BAS
Breach and Attack Simulation (BAS) is another cybersecurity approach or technology that might seem to be somewhat similar to EASM. According to Gartner, BAS tools allow enterprises to continually and consistently simulate the full attack cycle (including insider threats, lateral movement and data exfiltration) against enterprise infrastructure.
However, one of the differences between BAS and EASM is that BAS tools do not conduct asset discovery and do not offer to prioritize vulnerabilities. On the other hand, EASM tools cannot simulate lateral movement and do not actually exploit vulnerabilities.
EASM is usually considered as a step that enables BAS: EASM automatically identifies assets and scans them for vulnerabilities, while BAS executes real-life exploits against discovered weaknesses.
-
What kinds of organizations could benefit from EASM?
Unlike many other cybersecurity tools that require a certain level of maturity and are usually used by enterprises, EASM can be beneficial for organizations of all sizes.
Smaller organizations can use EASM as their main, and perhaps one and only solution, to enable vulnerability management and asset discovery. EASM could be a value-packed alternative to DAST solutions, as, in addition to covering the web apps, it also provides a comprehensive picture of the remaining attack surface.
Bigger organizations usually use EASM as a starting point for the ASM process, to create asset inventories and vulnerability lists that can be fed to other cybersecurity systems.
If your organization has a digital footprint that is not negligible, it can benefit from EASM.
Government Agencies
The government sector is heavily targeted by sophisticated threat actors. That highlights the importance of reducing each entity’s external attack surface through deeper visibility and insights that supplement existing foreign, military, and global threat intelligence sources.By uncovering and remediating vulnerabilities in mission-critical external assets, government agencies and departments can:
– Manage their nation’s threat exposure
– Fight against APTs
– Comply with federal security frameworks and regulationsFinancial Organizations
With scattered and multiple digital touchpoints, financial institutions often have a sizable external attack surface to cover. Gaining complete and up-to-date visibility over all Internet-facing assets through EASM enables them to:– Protect sensitive financial client data
– Prevent financially motivated cyber attacks
– Comply with cybersecurity laws applicable to their industryAside from banks and investment companies, cyber insurance companies can also make accurate and well-informed underwriting decisions with EASM’s help.
Online Marketplaces
E-commerce companies, API marketplaces, and other online retail platforms need help to provide customers with a safe environment as such entities increasingly rely on cloud-based systems, API integrations, and other external-facing technologies.Online businesses need to proactively identify and protect known, unknown, and new assets. EASM helps them accomplish that by providing complete attack surface visibility that enables them to:
– Secure customer payment information
– Protect their brand reputation
– Reduce cloud-based risks
– Comply with e-commerce and data privacy lawsIT and Software Companies
Security gaps seem inevitable, especially for companies that develop new applications and software. The key is to detect blind spots before attackers can. EASM allows AppSec and ProdSec teams to see their external IT and cloud assets in one place with as little noise and few false positives as possible, enabling them to:– Quickly detect security gaps like asset misconfigurations and unsecured applications
– Customize risk scoring so they can focus on the most critical and relevant risks first
– Remediate vulnerabilities seamlesslyHealthcare Organizations
Healthcare organizations increasingly rely on connected IT systems and the cloud, which exposes them to several risks, including patient data breaches, ransomware attacks, and denial-of-service attacks. EASM can help these organizations efficiently manage risks by:– Providing a complete and real-time catalog of all external-facing assets comprising their large digital operations and cloud environments
– Allowing limited security personnel to view, rank, and remediate vulnerabilities in one place
– Continuously detecting new assets and vulnerabilities that could expose electronic protected health information (ePHI) to ransomware and other attacks.