New cybersecurity abbreviations appear faster than professionals manage to memorize them. So, when people see yet another abbreviation, confusion is a very normal emotion: What is this new thing and how is it different from another thing that we’ve had before?
In this article, we look at two particular abbreviations that are often confused: ASM and VM – attack surface management and vulnerability management. Both seem to be about roughly the same proactive approach: finding vulnerabilities is an organization’s assets, prioritizing and remediating them. But there are some important differences which justify the existence of ASM, and people saying that it’s just “the newfangled VM” are not exactly correct.
We’ll start with a quick answer in the form of a table, and then proceed to discuss the differences in more detail.
| Vulnerability Management (VM) | Attack Surface Management (ASM) | |
| Scope | Known assets | Known and unknown assets |
| Primary approach | Inside-out | Outside-in |
| Attack surface | External and internal | External and internal |
| Process | ||
| Asset discovery | ❌ | ✅ |
| Vulnerability scanning | ✅ | ✅ |
| Vulnerability prioritization | ✅ | ✅ |
| Vulnerability remediation | ✅ | ✅ |
| Monitoring | Cyclical | Continuous |
| Security issues covered | ||
| Unpatched software vulnerabilities | ✅ | ✅ |
| Software and network misconfigurations | ✅ | ✅ |
| Information disclosure | ✅ | ✅ |
| Encryption weaknesses | ✅ | ✅ |
| Shadow IT | ❌ | ✅ |
| Ad-hoc implementations | ❌ | ✅ |
| Exposed or unsecured databases and APIs | ❌ | ✅ |
| Brand and reputation risks | ❌ | ✅ |
Table of Contents
- What is Vulnerability Management
- What is Attack Surface Management (and How Is It Different from Vulnerability Management)
- What is the Difference Between Attack Surface Management and Vulnerability Management
- The Key Differences in ASM and VM Tools
- How Can Attaxion Help with ASM and VM
What is Vulnerability Management
Vulnerability management (VM) is the continuous process of identifying, prioritizing, remediating, and monitoring vulnerabilities.
It helps security teams deal with vulnerabilities before attackers can find and exploit them. VM is a relatively old concept by cybersecurity standards, having been created in 1999 by Foundstone (which was acquired by McAfee in 2004).
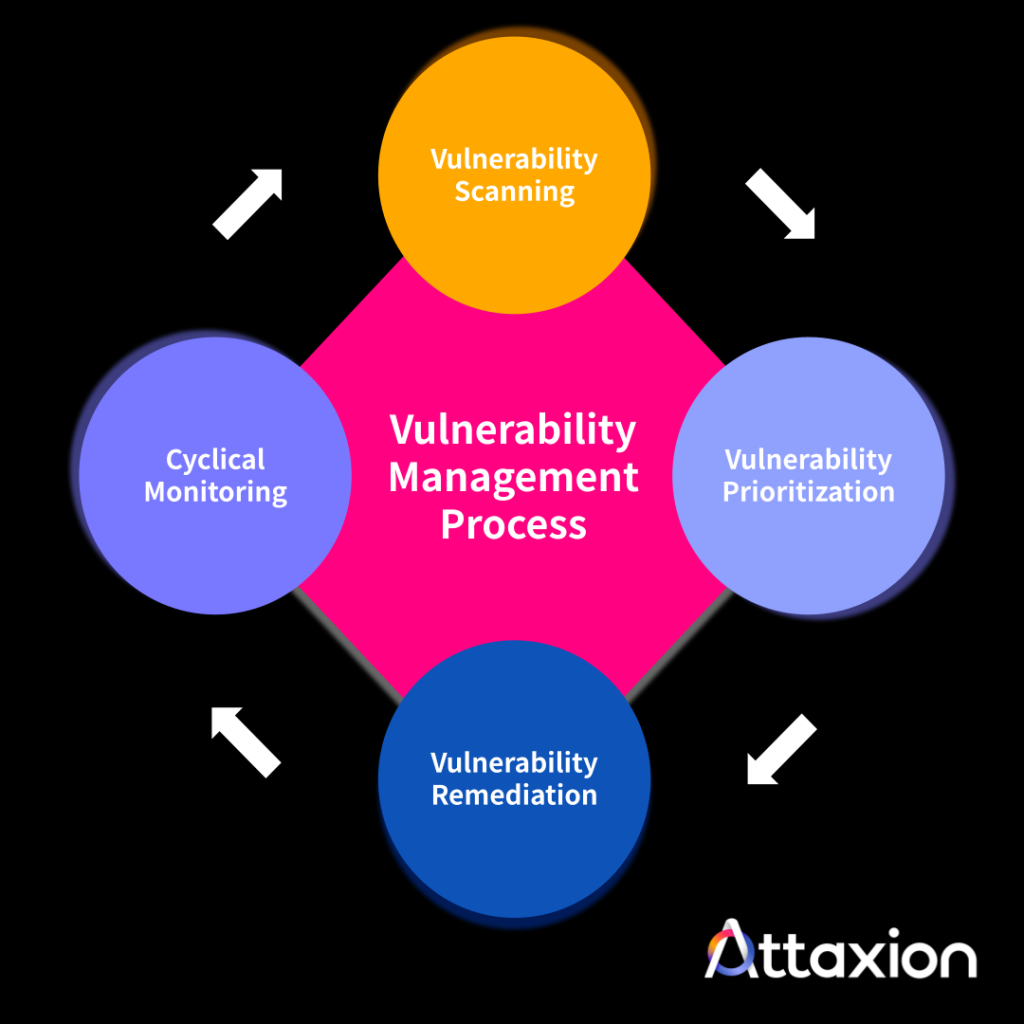
We have a beginner’s guide to vulnerability management if you want to learn more about VM. Here, for comparison purposes, we’ll look at its scope – assets and issues that it tackles – and the structure of the process.
The Scope of Vulnerability Management
Asset Scope
Vulnerability management requires an existing asset inventory – somebody has to create it before the process can start.
The asset inventory may include both internal assets (endpoints such as computers or smartphones, internal networks, and more) and external assets (websites, external APIs, public cloud environments).
Issues Scope
VM relies on running vulnerability scanners across all the assets in the inventory, identifying a variety of issues. Here are some examples of the issues that a vulnerability scan can identify:
- Unpatched software vulnerabilities. Security flaws in vulnerable assets such as operating systems, applications, and web apps that need updates or patches.
- Software misconfigurations. Weak security settings in servers, databases, cloud environments, or network devices that could be exploited.
- Information disclosure. Incorrectly configured systems that, as a result, can disclose private information publicly.
- Encryption weaknesses. Improper or outdated encryption methods that can make sensitive data vulnerable to interception or unauthorized access.
How The Process of Vulnerability Management Looks Like
As a process, vulnerability management has a relatively straightforward structure that can be distilled into 4 steps:
- Vulnerability scanning. Using an existing asset catalog, an organization’s security team runs a vulnerability scanner across all the assets to identify potential security vulnerabilities.
- Vulnerability prioritization. The team then proceeds to prioritize the detected vulnerabilities based on the asset business criticality, the vulnerability severity, exploitability, relevance, and other parameters. Often, there’s some criticality score calculated based on all of these parameters, and the most critical vulnerabilities should be dealt with first. There are different cyber risk prioritization models, we discuss some of them in our guide to vulnerability prioritization.
- Vulnerability remediation. The team creates tasks for IT engineers to remediate vulnerabilities according to the defined priorities by patching the outdated software or reconfiguring it. They also report on the work they’ve done – in some cases only to internal stakeholders, but more and more countries’ compliance standards require public vulnerability reporting. Sometimes, reporting is considered a step of its own.
- Vulnerability monitoring. The cybersecurity team proceeds with monitoring for vulnerabilities, essentially restarting the entire process. It’s cyclical, which means there’s an agreed frequency at which the team performs the process.
Vulnerability Management vs Vulnerability Scanning
Some people confuse vulnerability management and vulnerability scanning. But after reading the previous part, you can clearly see they are not synonyms. Scanning is just a part of the vulnerability management process, essentially its first step.
Scanning does not include such essential steps as prioritization and remediation, it only finds issues. That’s why scanning can be used by both offensive and defensive security teams – red teams use it to find vulnerabilities they’d exploit. VM, however, is an exclusively blue team process.
What is Attack Surface Management (and How Is It Different from Vulnerability Management)
Attack surface management (ASM) is the process of continuous discovery, validation, prioritization, and remediation of exploitable vulnerabilities in an organization’s systems.
It’s a relatively new concept, with the term “attack surface management” having been coined only in 2019.

For a more comprehensive overview, we recommend that you take a look at our external attack surface management guide where we discuss ASM in more detail. Here, we’ll again focus on the scope of assets and issues and the process to pinpoint where exactly ASM is different from VM.
The Scope of Attack Surface Management
Asset Scope
Attack surface management begins with identifying the organization’s assets, which means, creating the asset inventory is a part of the ASM process. That’s, perhaps, the most important difference between ASM and VM: VM requires an asset inventory, ASM generates it.
Formally, ASM also covers both internal and external assets – there are even separate sub-processes, internal attack surface management (IASM) and external (EASM). But many cybersecurity practitioners confuse ASM with EASM – the process that covers only external assets. This is perhaps because internet-facing assets are more exposed and more likely to become a target for cyber threats, since the actors behind those threats don’t need network access to try exploiting vulnerabilities in external assets.
Issue Scope
ASM’s scope of covered issues is broader than that of VM, but it includes everything from VM’s scope – security vulnerabilities, misconfigurations, information disclosure, and encryption weaknesses. However, in addition to that, ASM can discover assets and analyze connections between them, which allows it to help with other issues, such as:
- Shadow IT
- Ad-hoc implementations
- Exposed or unsecured databases and APIs
- Brand and reputation risks
How The Process of Attack Surface Management Looks Like
ASM can also be broken down into several steps, usually it’s the following 5:
- Asset discovery. The ASM process starts with building an asset inventory – using cyber reconnaissance techniques to look for the organization’s assets and map them to each other. There’s a manual part called asset validation, where the cybersecurity team validates if the discovered assets are really a part of the organization’s digital footprint and not some false positives.
- Vulnerability scanning. Then, ASM tools automatically scan all of the mapped and validated assets to identify misconfigurations, vulnerabilities, exposures, and other potential risks. Sometimes, the first two steps are considered to be one – attack surface discovery.
- Risk prioritization. Just like in the case with VM, the security team then prioritizes the discovered issues based on their potential impact, which is calculated using various parameters, from scores such as CVSS (severity) or EPSS (exploitability) to exploit availability in the wild (CISA KEV). The team also defines more critical assets, with asset criticality also impacting prioritization.
- Risk remediation. Again, just like in the case of VM, the issues are then tackled by engineers in accordance with priorities. In ASM, reporting is also considered a part of remediation efforts.
- Continuous monitoring. The ASM process is continuous, with automated tools always looking for previously undiscovered assets and their respective issues.
According to Gartner, attack surface management actually consists of three areas:
- External attack surface management (EASM). That’s the main part, and it covers everything listed above when applied to external, i.e. internet-facing assets. EASM assumes an outside-in perspective, which means it looks at your organization’s infrastructure the same way a potential attacker does and finds potential attack vectors the same way a threat actor would.
- Cyber asset attack surface management (CAASM). This is the complementary part that looks on the organization’s infrastructure from the inside. This allows CAASM to discover internal assets and their vulnerabilities, but at the same time, requires a tight integration with the rest of your IT stack so that a CAASM tool knows where to look for assets. A primary source of information for CAASM systems usually is EASM platforms.
- Digital risk protection services (DRPS). This is an extension (sometimes partially integrated into EASM tools) that covers external cybersecurity risks such as data leaks or brand impersonation.
What is the Difference Between Attack Surface Management and Vulnerability Management
As you can see, ASM and VM are very similar, with one major difference: VM does not include asset discovery, while ASM does. That means that VM only handles known security risks, ASM handles both known and unknown risks, as it also can find assets belonging to the organization that the IT team wasn’t aware of.
That also means that ASM looks at the organization’s digital attack surface primarily using an outside-in approach, similar to how a potential attacker would do it – discovering and mapping the organization’s vulnerable assets. VM, on the other hand, primarily relies on the inside-out approach, looking from the standpoint of somebody who works in the organization and knows the assets that it has.
Also, ASM is continuous and VM is cyclical, which means that ASM provides near real-time visibility into your attack surface while VM runs periodic scans.
Is VM Enough or Do I Need ASM?
With the seemingly small difference, one can assume that it doesn’t really matter which process you choose to follow. But in fact, the difference is significant. Let’s discuss some of the problems and use cases that ASM covers and VM doesn’t.
- Shadow IT. With its heavy focus on the cyber attack surface discovery, ASM can find assets an organization’s IT team wasn’t aware of – these are called shadow IT assets. They can range from a new technology a team decided to use on a server to an entire forgotten test infrastructure. These assets can also be vulnerable and become targets of external threats, so they also require attention, but they’re out of scope for VM, as they are not known to the IT team, and VM can only work with known risks.
- Ad-hoc implementations. As companies get bigger and departments become more independent, they tend to create their own infrastructure, sometimes ad-hoc, without proper security controls and any involvement from the IT department. This infrastructure is often not immediately accounted for, so it won’t end up in asset inventory used for VM and might result in additional security gaps. ASM, however, can discover this infrastructure through connections to other organization’s assets and add it to the asset inventory so that it falls under proper control of the IT department.
- Brand and reputation risks. ASM includes looking outside the organization’s network to find potential typosquatting domains, websites trying to mimic the organization’s own websites, rogue social media accounts, and more.
- Merger and acquisition security risk assessment. Asset discovery plays an important role in M&A risk assessments, as it allows the acquiring company to get a complete overview of the acquisition target’s infrastructure and the risks the company is about to inherit. In fact, M&A risk assessment is one of the key EASM use cases. VM is not useful here, as it requires an asset inventory, which means it relies on trusting the acquisition target’s team to provide one. That doesn’t sound like due diligence.
Does ASM Include VM?
The short answer is yes. Vulnerability management can be considered a subset of attack surface management. If you follow the ASM process, you also have to manage vulnerabilities.
However, to cover the entire attack surface, you need a bunch of tools – EASM, CAASM, and DRPS, which often makes ASM expensive. To cut costs, smaller security teams sometimes choose a cybersecurity strategy where they combine EASM and VM as a less expensive alternative to the full ASM process.
EASM and VM together cover most of what ASM does, allowing organizations to maintain a solid security posture. EASM also partially includes VM, but only for external assets. So, the major important part not covered by this combination would be internal asset discovery – maintaining the internal asset inventory falls on the security team’s shoulders. But internal assets generally pose lower risk than external ones, so this tradeoff may be justified.
The Key Differences in ASM and VM Tools
Now that we’ve discussed the similarities and differences between EASM and VM as processes, let’s take a look at how the tools designed for these processes compare.
It’s not surprising that both types of tools can be described as “vulnerability scanning automation.” Even more to that, they often rely on the very same vulnerability scanners. Their interfaces often look similar, but, just like with the processes, there are some significant differences you’ll usually find between ASM and VM tools:
- Asset discovery. While ASM solutions rely heavily on cyber reconnaissance and discover the assets automatically, VM tools often don’t have any reconnaissance at all. However, lately, many vulnerability management tools started offering subdomain discovery. Some went even further, adding more cyber reconnaissance techniques and essentially becoming ASM tools.
- Integrations/connectors. With ASMs primarily outside-in approach, it doesn’t need many integrations to work. VM, on the hand, needs more integrations to get an inside-out perspective and to pull an asset inventory from somewhere. That’s why VM tools often have more integrations with other tools. But, with the rise of automation and orchestration, ASM vendors started paying more attention to integrations.
- Scan aggressiveness. ASM tools often mimic how an attacker would scan the infrastructure, trying not to interfere with normal work processes and avoid detection. That’s why they often rely on passive scanning. As VM is cyclical (so that you can schedule heavier scans on weekends, for example, to avoid interruptions), VM tools often offer a choice between passive and active scanning. However, there are some ASM tools that rely on payload-based scanning to reduce false positives.
- Notifications. As VM tools rely on their cyclical scanning, the types of notifications one can expect to receive from them is “the scan is completed, here’s what we’ve found.” ASM tools with their continuous monitoring usually send you more granular notifications, for example, notifying you about an issue of a certain severity that has been discovered.
As the ASM and VM processes evolve, they seem to converge, moving towards each other. So, the tools of each type also started to incorporate features that were previously more typical for the tools of the other type: VM platforms introducing at least some asset discovery and ASM platforms offering active scanning and more integrations. Some differences are still there, but as time passes, more and more tools become perfectly suitable for both processes.
So, if we try to compare modern VM and ASM tools, a comparison table could look like that:
| Modern VM Tools | Modern ASM Tools | |
| Asset discovery | basic | advanced |
| Integrations | many | some |
| Scan aggressiveness | configurable | configurable |
| Notifications | on scan completion | on discovering an issue |
Of course, all the tools are different. Some VM tools still don’t offer any asset discovery and some ASM tools still rely exclusively on passive scanning. So, when choosing a platform, you need to analyze a lot of details. We’ve prepared a guide to choosing the best EASM tool which includes some of the VM tools as they’re gradually moving towards ASM’s territory.
How Can Attaxion Help with ASM and VM
Attaxion is an external attack surface management platform with a heavy emphasis on attack surface discovery built to suit any cybersecurity budget. It helps cybersecurity teams discover known and unknown digital assets, organize and maintain an external asset inventory, find issues, prioritize them and simplify remediation of vulnerabilities with 1-click JIRA ticket creation. Attaxion is very effective in preventing potential threats and helping organizations maintain a strong security posture.
Getting started with Attaxion takes less than an hour and only requires adding a few root assets manually so that Attaxion’s cyber reconnaissance toolset may take care of the rest, building a comprehensive external asset inventory for you and continuously scanning for new assets and potential vulnerabilities.
Attaxion can handle the EASM part of the ASM process for you and help you manage vulnerabilities in your external-facing assets while saving you a lot of money. If you’re ready to give it a try, you can sign up for a 30-day free trial or book a demo with our specialists to have them answer the questions you might have.

