Best ProjectDiscovery Alternative: Attaxion
ProjectDiscovery has built a name for itself as the organization behind popular open-source tools such as the vulnerability scanner Nuclei, the passive subdomain enumeration tool Subfinder, the port scanner Naabu, and others.
But ProjectDiscovery also offers a platform that brings all these tools together to help with attack surface management and vulnerability management. They call it the ProjectDiscovery Cloud Platform.
In this article, we compare it with another platform built using a very similar idea, but a different set of tools – Attaxion. We’ll be evaluating both as platforms that enable vulnerability management and external attack surface management in an organization to see if Attaxion is a worthy ProjectDiscovery alternative for these tasks. We’ll start with pricing.
 PART 1
PART 1
Pricing
Free trial
Instead of a free trial, ProjectDiscovery offers a free tier. It only works with the domain that matches your business email you used to sign up, limiting discovery to 10 new domains a month, and scans for vulnerabilities on a monthly basis. There are also other limitations. It’s suitable for a quick taste of Nuclei-in-the-cloud, but it’s not enough for a real external attack surface management program.
Attaxion doesn’t have a free plan, but offers a 30-day free trial that has all features, but is limited to monitoring 60 assets and only one vulnerability scan of the entire external attack surface.
ProjectDiscovery pricing and plans
As of July 2025, ProjectDiscovery’s public pricing page shows only two tiers: Free ($0) and Enterprise (custom quote). Everything in between has disappeared from the site.
But until mid-2025, ProjectDiscovery used to offer another option called Growth, priced at $3,500/year for up to 100 assets (and in 2023, it was called Pro and cost $2,500 for up to 1,000 assets). It had some limitations compared to the Enterprise plan, and, well, doesn’t exist anymore. We’re mentioning it here because its price can probably still give some ballpark estimation for the current costs of the platform.
Attaxion pricing and plans
Just like ProjectDiscovery, Attaxion is priced per asset. However, unlike ProjectDiscovery, Attaxion keeps its pricing public and offers all features on every tier – the only variable is the asset count. The most affordable option allows you to discover, scan, and continuously monitor up to 40 assets for $129/month (or $1,290/year, as yearly plans come with a discount). If you want to track more assets, you can either choose a plan with a higher asset count or request a quote.
Both Attaxion and ProjectDiscovery mean the same thing by billable assets – they ask you to pay for active domains, subdomains, and IP addresses that were found to belong to your infrastructure.
How they compare
Since ProjectDiscovery has hidden its pricing, it’s hard to tell how the two tools compare now. But if we go a little back in time and consider the discontinued Growth plan ($3,500/year for 100 assets) that ProjectDiscovery had just recently, then we can say that it was just a little bit more expensive than Attaxion’s Plus plan ($3,490/year for 120 assets).
The main difference, perhaps, is that ProjectDiscovery doesn’t offer monthly plans, at least not publicly, while with Attaxion, you can choose between monthly and yearly (yearly is cheaper, of course). Also, Attaxion has a cheaper plan for smaller organizations.
 PART 2
PART 2
Asset Discovery and Inventory
Asset discovery with ProjectDiscovery
ProjectDiscovery uses its own free tools – Subfinder, Cloudlist, and Naabu – to discover and enumerate an organization’s assets.
Subfinder is a passive subdomain enumeration tool that uses a variety of cyber reconnaissance techniques to find subdomains belonging to a domain. It’s worth noting that Subfinder relies on various third-party APIs to help with that. For both the free standalone version of Subfinder and the ProjectDiscovery Cloud, you’ll need to provide the API keys yourself if you want to improve Subfinder’s capabilities, which means you’ll need to pay for them separately.
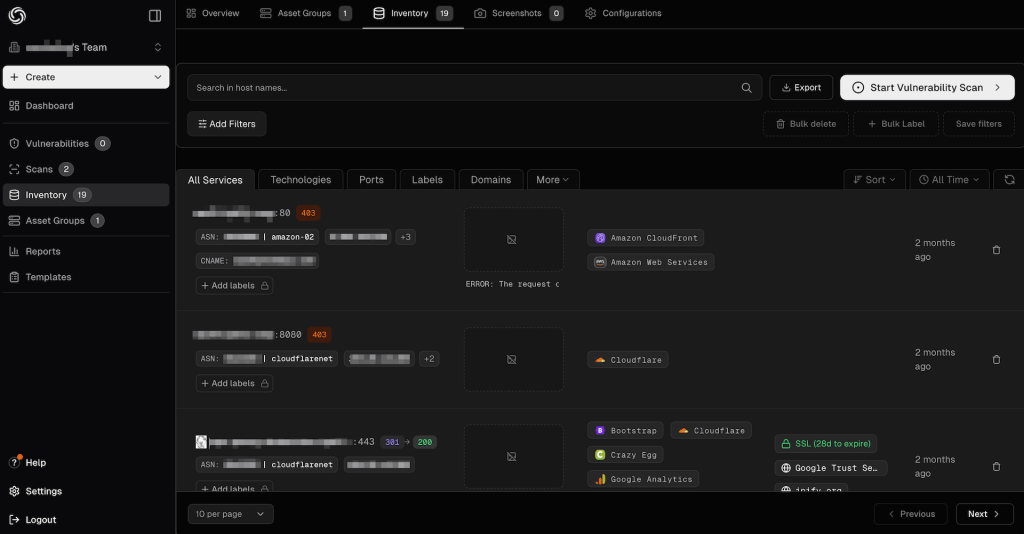
An interesting feature that ProjectDiscovery has is an integration with the Crunchbase API to discover an organization’s subsidiaries, so that it automatically proceeds to discover their assets and add them to the organization’s attack surface.
The public cloud integration tool Cloudlist allows users to pull lists of assets from public cloud accounts such as Google Cloud Platform (GCP), Amazon Web Services (AWS), and Microsoft Azure, as well as Cloudflare, Digital Ocean, and some others. You’ll need to connect ProjectDiscovery Cloud to your public cloud accounts to enumerate hostnames and IP addresses that you have there.
The port-scanning tool Naabu reveals open ports and together with a web-crawling tool called httpx they discover associated web services, allowing ProjectDiscovery Cloud to build a list of third-party technologies associated with each asset.
All of that happens under the hood – the user only needs to provide some seed assets (and the API keys for Subfinder, but that’s optional), and then ProjectDiscovery Cloud will pivot off them and discover the rest.
Asset discovery with Attaxion
Attaxion employs a very similar approach, even though the tools under the hood are different.
It also uses a wide variety of cyber reconnaissance techniques to identify associated assets such as domains, subdomains, IPv4 and IPv6 addresses, and open ports. Attaxion’s discovery tools also employ a number of APIs, but all API keys are built-in, so it doesn’t require you to pay third parties to discover every asset in your external attack surface.
Like ProjectDiscovery, Attaxion integrates with public cloud services such as AWS, GCP, Azure, and DigitalOcean to pull lists of assets from those accounts. And similarly, it also has a port scanner combined with a web crawler to identify open ports and build a list of technologies.
What Attaxion does differently is that it offers a visual representation of how the assets are connected to each other, creating a graph that can show potential attack paths. The graph allows users to quickly understand which assets are vulnerable, which are not, and which are associated with your infrastructure but are beyond your control.
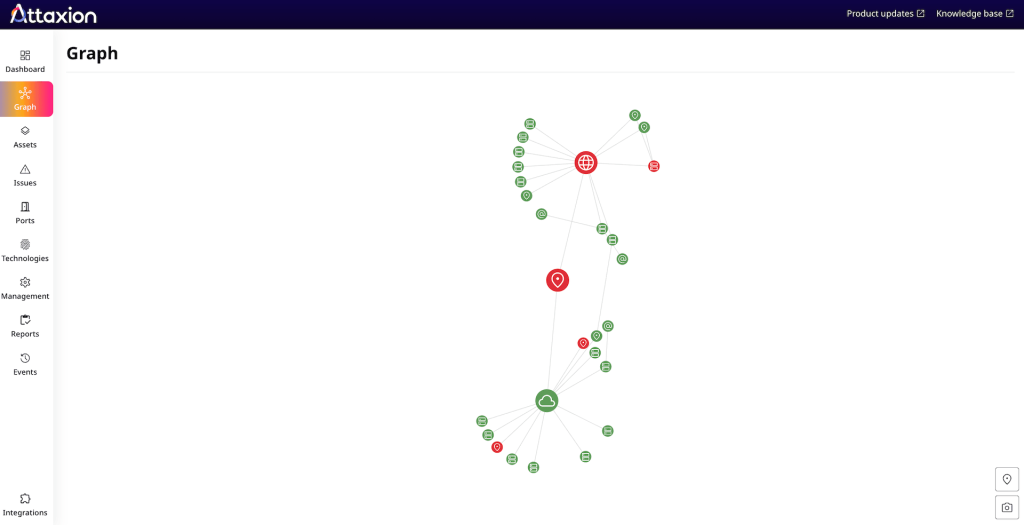
Attaxion also builds two more graphs for assets: a discovery graph and a dependency graph. The first shows how the asset was discovered (essentially, outlining the attack path to it), and the second visualizes which other assets depend on the one in question.
How they compare
Both ProjectDiscovery and Attaxion do a great job when it comes to asset discovery. In our test infrastructure, Attaxion discovered one more subdomain and a few more IP addresses, but both tools did better than an average external attack surface management platform. It’s also worth noting that both tools are very fast – you can get value out of them in about an hour after you begin using them.
ProjectDiscovery’s stronger side is a user-friendly asset inventory with plenty of information. Attaxion compensates for that with a slightly better discovery capabilities and the graphs. Also, while both tools theoretically allow you to export the lists of assets, we kept running into errors in ProjectDiscovery, while it worked without any problems in Attaxion.
 PART 3
PART 3
Vulnerability Scanning
Vulnerability scanning with ProjectDiscovery
ProjectDiscovery relies on its own vulnerability scanner called Nuclei to detect and validate the existence of vulnerabilities in systems. Nuclei is different from many other scanners for a variety of reasons: it’s open-source, it’s template-based rather than version-based, and the templates to detect and validate issues mostly come from the community.
ProjectDiscovery emphasizes that Nuclei is supposed to significantly reduce false positives, as – theoretically – template-based scanning allows you to reproduce the attacker’s steps and verify if the vulnerability is really there and can be exploited.
Nuclei is well-known in the cybersecurity community and used by other platforms as well (for example, by Intruder.io).
On the Enterprise plan, ProjectDiscovery scans continuously (while on the free plan, you get a limited monthly scan).
It supports authenticated scanning, and some of the Nuclei templates require authentication to work properly. ProjectDiscovery’s platform is also capable of internal network scanning, which requires setting up ingress tunnels using yet another of their free tools – TunnelX.
Vulnerability scanning with Attaxion
Attaxion relies on a different set of tools to detect vulnerabilities, primarily on a different renowned open-source scanner – OWASP ZAP by Checkmarx. ZAP is considered by its creators to be a penetration testing tool.
In addition to ZAP, it relies on port scanners, various DNS utilities, and web crawlers to identify misconfigurations, missing HTTP headers, and other issues.
Attaxion runs vulnerability scans continuously (roughly daily) on each asset it discovers with a generally low false positive rate.
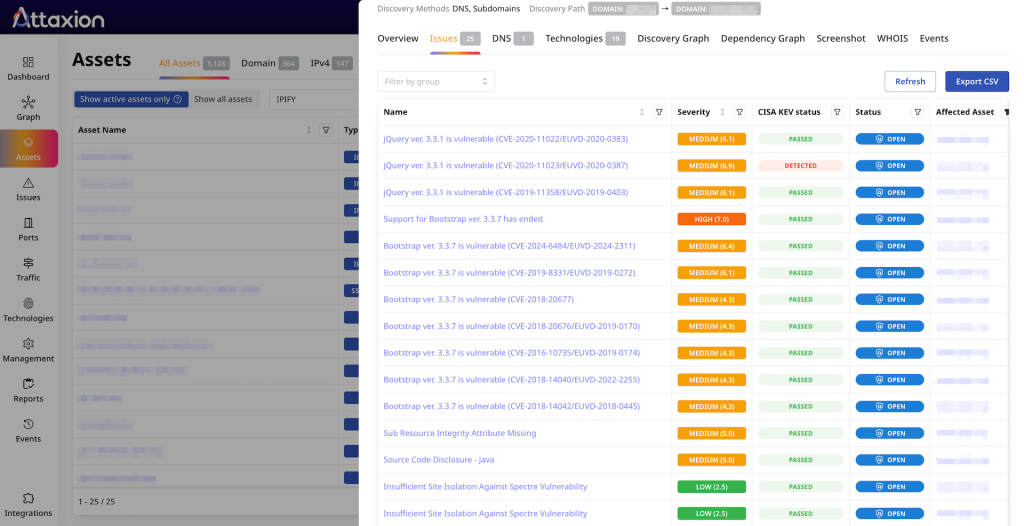
For each vulnerability, Attaxion pulls data from CVE (where applicable) and CWE databases, and recently, also added an integration with the EUVD – for both redundancy purposes and to ensure comprehensive vulnerability coverage.
How they compare
While on paper, Nuclei and ProjectDiscovery sound like a lot of things are done right, in some real situations it might not be the case. At least for our test domain, ProjectDiscovery found zero vulnerabilities, and we are quite certain there are many more than that.
While users complain that Nuclei generates a lot of false positives due to the varying quality of community-based scan templates, our experience is the opposite, but also not good – a lot of false negatives: vulnerabilities that exist and were not found by ProjectDiscovery.
Attaxion, on the other hand, found many vulnerabilities in the same test domain and its associated infrastructure.
 PART 5
PART 5
Vulnerability Prioritization and Remediation
Vulnerability prioritization and remediation with ProjectDiscovery
ProjectDiscovery could’ve used Steve Jobs’s legendary “there’s an app for that” to describe its features, but replacing “app” with “open-source tool.”
For example, they have an open-source CLI utility called cvemap to pull additional information about CVEs such as EPSS score to help users understand the likelihood of exploitation and CISA KEV data so that they can prioritize issues that are known to be actively exploited in the wild. It also shows if there’s a Nuclei template for this vulnerability.
For remediation, ProjectDiscovery offers integrations with Atlassian Jira, GitHub, GitLab, and Linear.
It supports one-click retest for vulnerabilities to highlight if something wasn’t fixed.
Vulnerability prioritization and remediation with Attaxion
For prioritization, Attaxion enables the user to make better-informed decisions, pulling a significant amount of data about the vulnerabilities.
In addition to severity levels (critical, high, medium, low, info), for each CVE it also pulls its CVSS score, advisories, and sources. On top of that, for CVE vulnerabilities, it adds EPSS and CISA KEV data to enrich context.
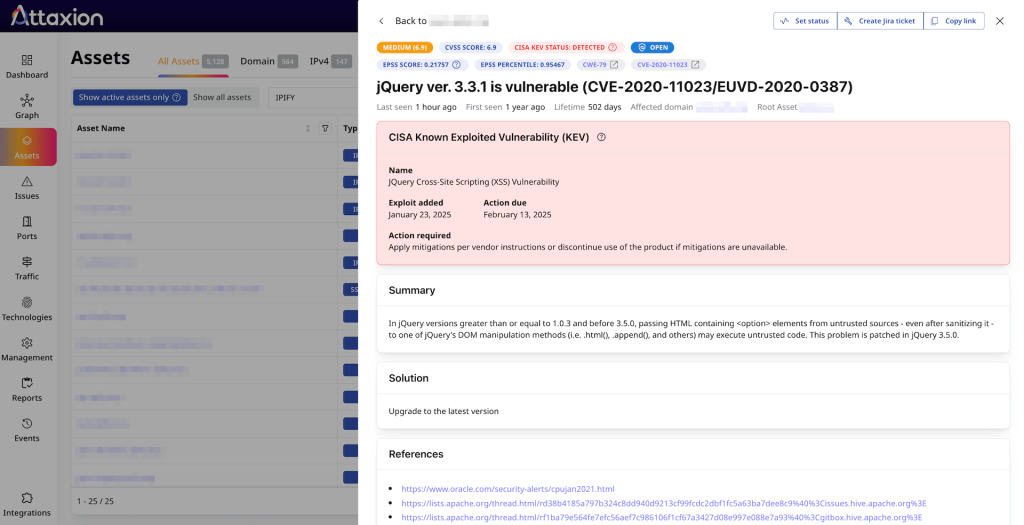
Attaxion enables security teams to create Jira tickets in one click, populating them with all necessary vulnerability details to help the responsible engineers with remediation.
For each vulnerability, the user can mark it as open, fixed, accepted risk, or false positive.
Attaxion also provides a REST API, allowing security teams to integrate its data and actions into their existing workflows or ticketing systems beyond the built-in options.
How they compare
- Attaxion runs continuous vulnerability scanning on each plan, while ProjectDiscovery does so only on its Enterprise plan.
- ProjectDiscovery has an integration with Teams and webhooks which Attaxion doesn’t. However, Attaxion offers custom development for its clients if they need more integrations.
 PART 5
PART 5
Continuous Monitoring
Continuous monitoring with ProjectDiscovery
ProjectDiscovery runs its discovery engine continuously. It keeps discovering internet-exposed and cloud assets and keeps your asset inventory up to date.
Similarly, on the Enterprise plan, it continuously scans everything for vulnerabilities and misconfigurations. On the free plan, you get only one monthly scan.
The platform automatically retests open vulnerabilities to track their current status – whether they have indeed been fixed or not.
To send notifications, ProjectDiscovery has integrations with Slack, MS Teams, and email, as well as webhooks. It allows you to create notification profiles and choose events and event parameters for each profile.
ProjectDiscovery also tracks your overall security score, remediation efficiency, and regression efficiency.
Continuous monitoring with Attaxion
When it comes to monitoring, Attaxion is very similar to ProjectDiscovery – it also runs the discovery engine continuously. It scans both new and previously known assets for vulnerabilities – both validating the existence of the known ones and detecting new ones.
Perhaps, the main difference is that Attaxion offers continuous scanning on all plans – from Starter to Enterprise.
For notifications, Attaxion integrates with email and Slack and allows users to customize the severity of vulnerabilities that trigger notifications individually for each channel. Attaxion will also send notifications if it has discovered new assets.

Attaxion keeps track of your overall security score and builds diagrams showing the number of issues by severity over time.
For each individual asset, Attaxion can also create reports, describing what the asset is and which vulnerabilities are associated with it, adding all the data necessary for remediation there.
How they compare
ProjectDiscovery and Attaxion are almost identical when it comes to continuous monitoring, with only two noticeable differences:
- Attaxion runs continuous vulnerability scanning on each plan, while ProjectDiscovery does so only on its Enterprise plan.
- ProjectDiscovery has an integration with Teams and webhooks which Attaxion doesn’t. However, Attaxion offers custom development for its clients if they need more integrations.
 PART 6
PART 6
Conclusion
ProjectDiscovery Cloud Platform and Attaxion have a lot in common – the platform architecture is very similar, and so is the pricing. Both excel at asset discovery, bringing together a variety of cyber reconnaissance techniques to discover a vast number of assets. Attaxion is a little better at that, at least for the seed we tested, and perhaps connecting APIs to Subfinder would nullify the difference.
Theoretically, ProjectDiscovery is a more functional tool, as it supports internal agentless network scanning, as well as authenticated scanning.
Yet, in practice, the situation is sometimes the opposite. Attaxion reliably finds vulnerabilities where – in our test – ProjectDiscovery missed them. Also, ProjectDiscovery seems to be ridden with minor bugs and glitches, with scans not starting when they should, exports not working, etc. – we’ve experienced this during the test and found that users on Reddit have faced those issues too.
Ready to try Attaxion? Start a 30-day free trial, or request a personal demo.