Best Beagle Security Alternative for Vulnerability Management: Attaxion
Beagle Security is a vulnerability scanning and automated penetration testing platform designed to help organizations identify security flaws in their web applications and APIs. Beagle focuses heavily on DevSecOps and integrating into the software development lifecycle. However, it can also be a solution for traditional vulnerability management as well.
Attaxion is a Beagle Security alternative for teams that have a lower security budget and want complete and continuous attack surface coverage instead of focusing on manually added targets and running scans once in a while.
In this article, we compare Beagle Security and Attaxion in terms of pricing and their capabilities in vulnerability management, including asset discovery, vulnerability scanning, prioritization, remediation, and continuous monitoring. We’ll also cover their integrations and reporting capabilities.
Quick Summary
| Feature | Attaxion | Beagle Security |
| Pricing | $1,290/year for 40 assets and continuous testing | $3,588/year for 15 tests/month |
| Asset discovery with 9+ types of assets | ✅ | ❌ (limited subdomain discovery) |
| Continuous vulnerability scanning | ✅ | ❌ (only scheduled or triggered scans) |
| Vulnerability prioritization with EPSS and CISA KEV | ✅ | ❌ |
 PART 1
PART 1
Pricing
| Beagle Security vs. Attaxion: Pricing | ||
| Attaxion | Beagle Security | |
| Pricing | USD $129/month for continuous testing of up to 40 assets with complete functionality | USD $119/month for the Essential plan with 2 tests of a single target and limited functions; USD $359/month for the Advanced plan and 15 tests of a single target per month |
| Assets covered at the starting price | 40 (all types) | 1 target and its subdomains |
| Free trial | ✅ (30 days) | ✅ (10 days) |
| Trial limitations | Up to 60 assets, 1 scan | Advanced plan, 1 scan |
Beagle Security Pricing
Beagle Security is priced per test. A test is, well, a test – a complete automated security test for one target. But on different tiers, the targets and the depth of tests may vary.
Beagle has fully transparent pricing and offers three paid plans:
- Essential,
- Advanced,
- Enterprise,
and a very limited free plan.
The Essential plan is priced at $119/month and offers two tests per month. As it often happens, it’s there basically to show what you’re paying for when going for the Advanced plan, as Essential lacks API testing, asset discovery, compliance reports, and some other useful features, as well as a bunch of integrations including the ones with CI/CD tools. Also, two tests per month aren’t likely enough for most vulnerability management purposes.
The Advanced plan has all the aforementioned features that are not available on Essential and offers 15 tests per month, as well as the option to run four concurrent tests, which comes in really handy if you have multiple targets. It also allows you to add your branding to reports. This tier costs $359/month – and we’ll be focusing primarily on it, as it shows what Beagle can really offer. Unlike Essential, Advanced is suitable for vulnerability management (at least to some extent). You can always expand the plan by adding more tests ($30/month each), more concurrencies ($15/month each), more users ($5/month each), and white-labelled reports (at a fixed cost of $49/month).
The Enterprise plan is there for those who need enterprise-grade features such as SSO, a dedicated customer success manager, priority support, etc. Among the features of this plan that stand out are internal web app tests (aka Cosmog), and API discovery in Kubernetes – we’ll get back to both a little later. Also, only the Enterprise plan allows you to pause and restart tests. The number of tests on this plan depends on what you agree on with sales.
Finally, the free plan is there mostly as a fallback mechanism – there’s one very limited test per month, no scheduling, no authenticated testing, and no integrations whatsoever.
Beagle offers a 10-day free trial of the Advanced plan, but with only one test included. After the trial is over, you get downgraded to the free plan.
Attaxion Pricing
Unlike Beagle, Attaxion runs continuous testing and is priced per asset. It has four different pricing plans:
- Starter, $129/month for up to 40 assets,
- Plus, $349/month for up to 120 assets,
- Business, $949/month for up to 360 assets,
- Enterprise, if you need to scan more assets than what the Business plan has to offer.
Essentially, plans differ only in terms of the number of assets scanned. All plans have all the integrations, asset discovery, the ability to switch between passive and active scanning, and more. To Enterprise users, Attaxion offers an isolated environment with dedicated resources and the option to pay via wire transfers, while the rest of the plans are only payable with a credit card. Attaxion also offers to develop integrations or features on demand on Business and Enterprise plans.
To understand pricing per asset, we need to define what an asset is. Attaxion bills users for domains, subdomains, IP addresses, SSL certificates, exposed email addresses, cloud instances, and CIDRs. To give you a ballpark estimate, one small SaaS that we tested had 25 assets, the other – 12. You can also use Attaxion’s free tool – Cyber Asset Finder – to estimate how many assets you have.
Attaxion doesn’t have a free plan, but it offers a 30-day free trial with all features and a limit of 60 assets. You can always contact sales if you need an extended trial or if you’re looking to scan more assets.
How They Compare
While Beagle’s Advanced plan is not really expensive at the start, the costs start to increase rapidly if you try to properly integrate Beagle into the software development lifecycle and scan every target on a regular basis.
Attaxion doesn’t offer CI/CD integrations, but its Starter plan is three times cheaper while offering no limitations on the number of tests – it just continuously monitors your entire external attack surface. Overall, both tools are priced very competitively, and we haven’t seen a single review on the Internet that complained about their pricing.
 PART 2
PART 2
Asset Discovery
Asset Discovery with Beagle Security
Like pretty much every other DAST tool, the setup process for Beagle Security starts with adding targets – the URLs of the web apps or APIs you want to scan. Then, you’ll need to verify the ownership of the target, for example, by adding a DNS record or uploading an empty file with a unique name to the root folder.
After the target is verified, Beagle Security can find associated assets – a feature that it offers on the Advanced and Enterprise plans. In their terms, asset discovery means that Beagle automatically detects subdomains linked to the target you’ve added.
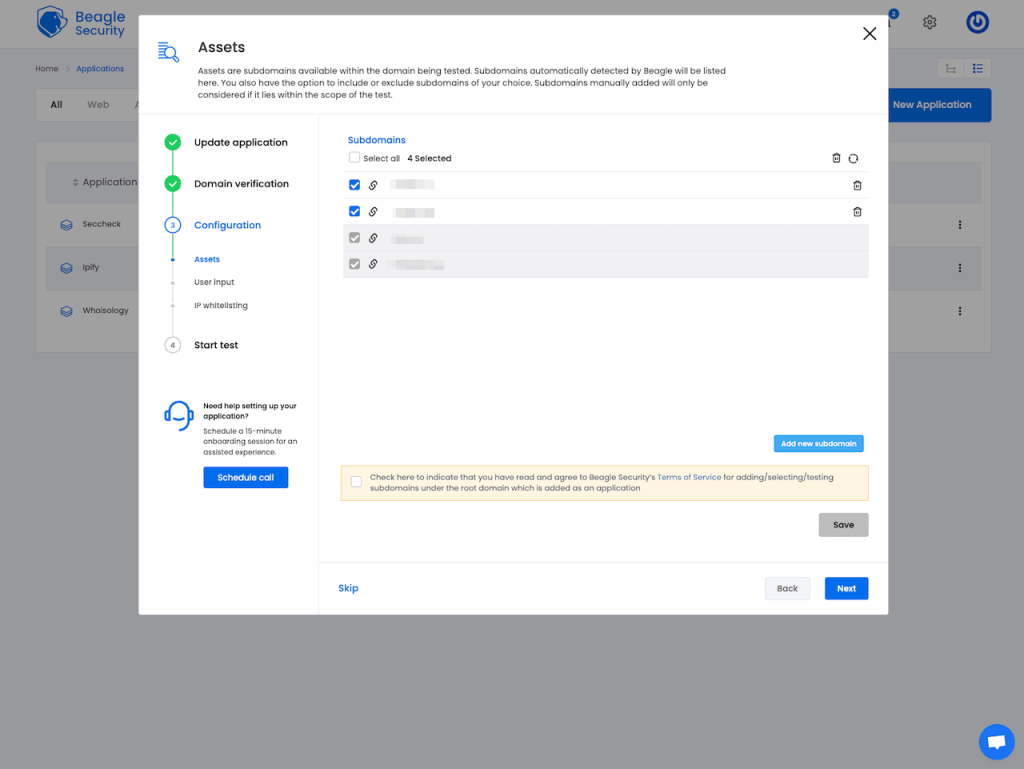
The good part is that the discovery process only takes a moment. But, in our experience, the number of subdomains it comes up with is quite low. For one of our test web applications, Beagle Security found just one subdomain, whereas Attaxion discovered four. For another, it was three for Beagle versus 13 for Attaxion.
A curious feature that Beagle offers only on the Enterprise plan is API discovery – if you connect it to a Kubernetes cluster, it can attempt to automatically find APIs.
Asset Discovery with Attaxion
Attaxion’s primary focus is attack surface mapping. So, even though the process starts just like with Beagle Security – by manually adding and verifying root assets – Attaxion does a very different kind of job afterward.
Instead of quick and basic subdomain enumeration, Attaxion employs more than a dozen cyber reconnaissance techniques to find all kinds of external assets that are connected to the ones you’ve provided. And it does so not once, but continuously. Those assets could be domains and subdomains, IP addresses, CIDRs, open ports, and even exposed email addresses. Attaxion catalogs all the assets, providing you with a complete external asset inventory, and maps assets to each other. It creates a graph, showing you the connections between assets and the theoretical attack paths a threat actor may take.
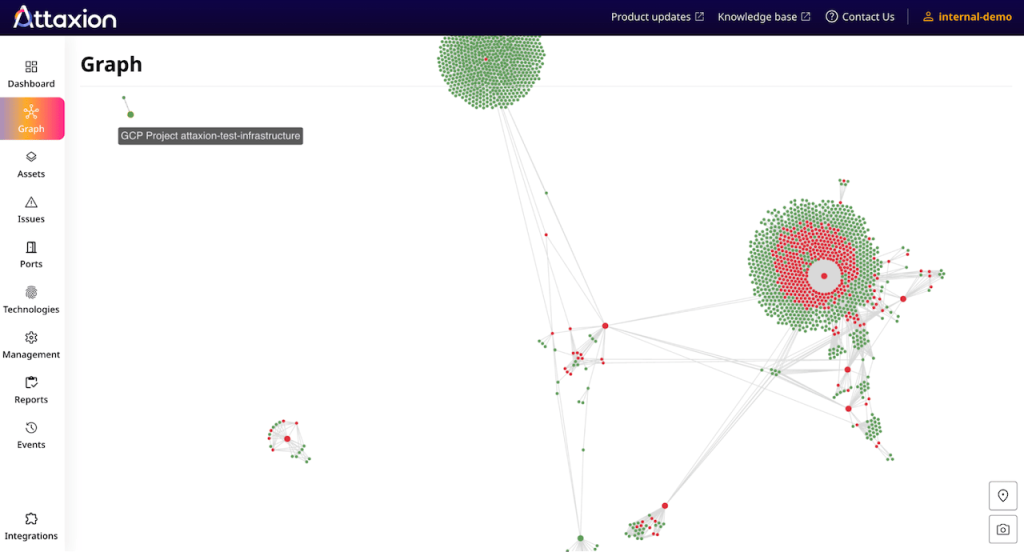
If WHOIS or DNS data suggests that a domain (not a subdomain) is connected to one of your domains, Attaxion will add it to the list of root asset candidates. For each of those, you can either verify ownership to begin further discovery of assets connected to it or mark them as false positives so that Attaxion doesn’t look at them in the future.
Attaxion also has integrations with popular public cloud providers such as AWS, Google Cloud, Microsoft Azure, and Digital Ocean, which, if set up, allows it to sync the list of assets with the public cloud account.
We’ve already discussed above how many more subdomains Attaxion could find for the same test apps.
How They Compare
When it comes to asset discovery, Attaxion is the clear winner.
Beagle Security’s Advanced plan includes basic subdomain enumeration. Attaxion goes much further—uncovering a wider range of assets, including significantly more subdomains and even related domains.
With Beagle, you have to add assets manually, which risks missing vulnerable apps belonging to your attack surface that you accidentally forgot or weren’t aware of. Attaxion finds domains and subdomains tied to your organization—even the ones you didn’t know existed. And it does all of this at one-third of the price.
 PART 3
PART 3
Vulnerability Scanning
Vulnerability Scanning with Beagle Security
Beagle security relies on a proprietary vulnerability scanner, positioning itself as an alternative to popular tools such as OWASP ZAP by Checkmarx and Burp Suite. A scan takes time – from two hours up to three days, if the application is really big. In our experience, Beagle took about an hour to scan a static website with a few pages and about two hours to scan a relatively small SaaS application. If something goes wrong during a scan (say, app authentication failed), the scan never concludes, but you’ll get an email notification from support that something went wrong.
Beagle is capable of detecting some technology that a web application uses, including a CMS, but to improve results, you can manually indicate which programming languages, frameworks, and databases your applications use during the setup.

Beagle offers authenticated scanning and even business logic recording – you can record important user flows in your application for Beagle to replicate and test. It offers multiple authentication mechanisms and is even capable of bypassing CAPTCHA (or rather, it can try, but doesn’t promise that it’ll succeed every time).
A curious feature that the platform has is the Beagle Security Cosmog module, which allows users to scan internal web applications and APIs. That one is likely geared towards enterprises, as smaller companies usually don’t have web applications that face their internal network (and because Cosmog is only available on the Enterprise plan).
Vulnerability Scanning with Attaxion
For web application vulnerability scanning, Attaxion relies on the aforementioned open-source scanner OWASP ZAP. As some G2 users mention, ZAP is capable of discovering some issues that Beagle Security misses.
On top of that, Attaxion scans open ports and builds a technology inventory based on the received answers. It highlights the vulnerable technologies and the assets they are used on, as well as when they stopped being supported.
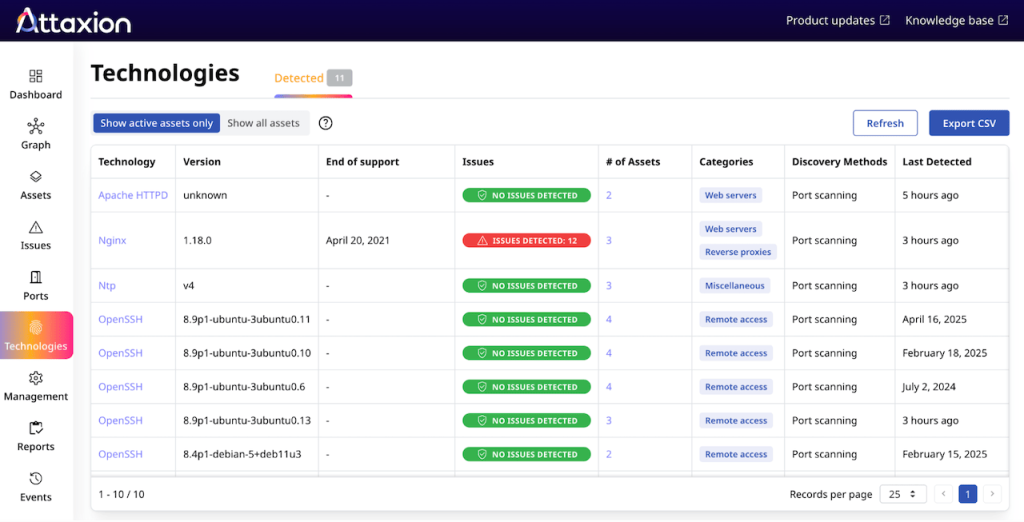
It also runs network scans. The databases Attaxion uses are up to date with MITRE’s CVE and CWE databases (while Beagle focuses primarily on CWEs).
The scans are completely automated, they run continuously, without any need to initiate or schedule them. The user can also choose between passive and active scanning. The passive mode, while stealthy, is mostly about asset discovery rather than vulnerability scanning.
How They Compare
Both tools have their significant advantages.
Beagle Security proves itself as a capable gray-box scanner: its stronger sides are authenticated scanning with various authentication mechanisms and even CAPTCHA bypass.
Attaxion – as a platform that fully supports external attack surface management – can discover a broader scope of issues, but doesn’t have authenticated scans.
 PART 4
PART 4
Vulnerability Prioritization and Remediation
Prioritization and Remediation with Beagle Security
The main criterion that Beagle Security uses for prioritization is vulnerability severity – critical, high, medium, low, or info.
That’s it for prioritization. Since Beagle is primarily focused on application security, it mostly looks at CWEs. Perhaps, that is why it doesn’t offer additional, CVE-specific data such as the EPSS score (the likelihood of the vulnerability being exploited) or the CISA KEV catalog (information about whether it’s known to be exploited in the wild).
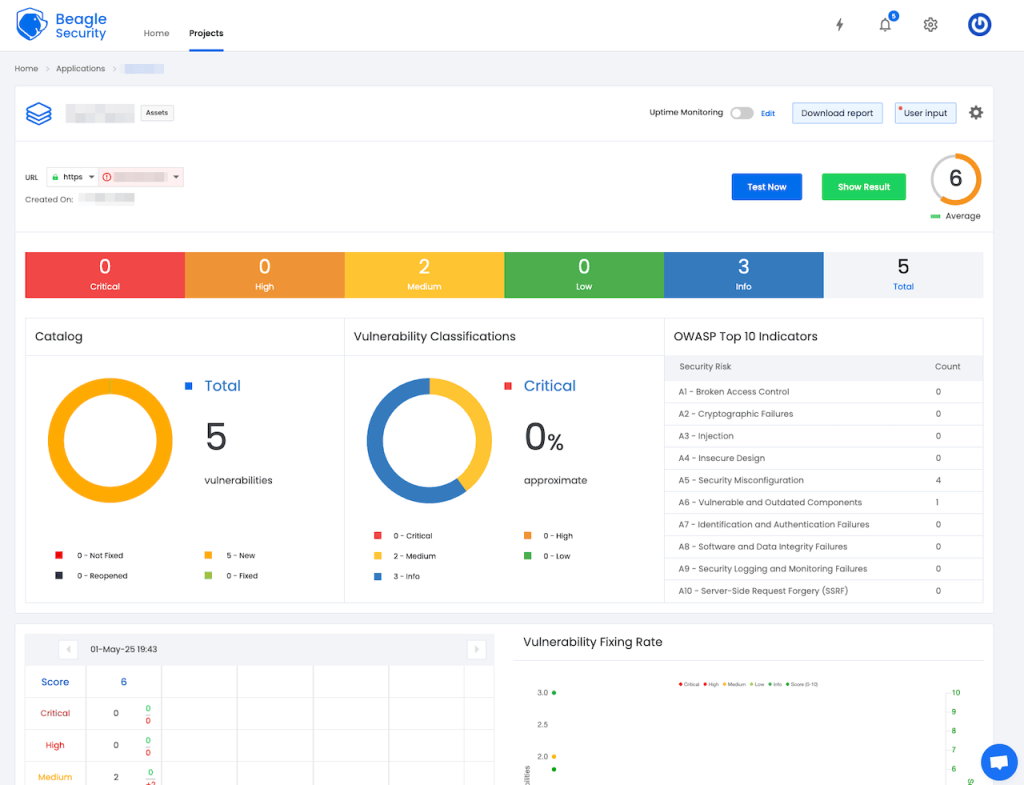
Beagle Security has an interesting idea for presenting the vulnerabilities it discovers. Instead of offering a full list of issues that can be sorted by name, CWE number, or severity, Beagle organizes the list of vulnerabilities by report – OWASP, OWASP Top 10, or CWE Top 25. Another nice feature is adding a line of tags to each issue showing which lists it belongs to and which compliance requirements it violates.
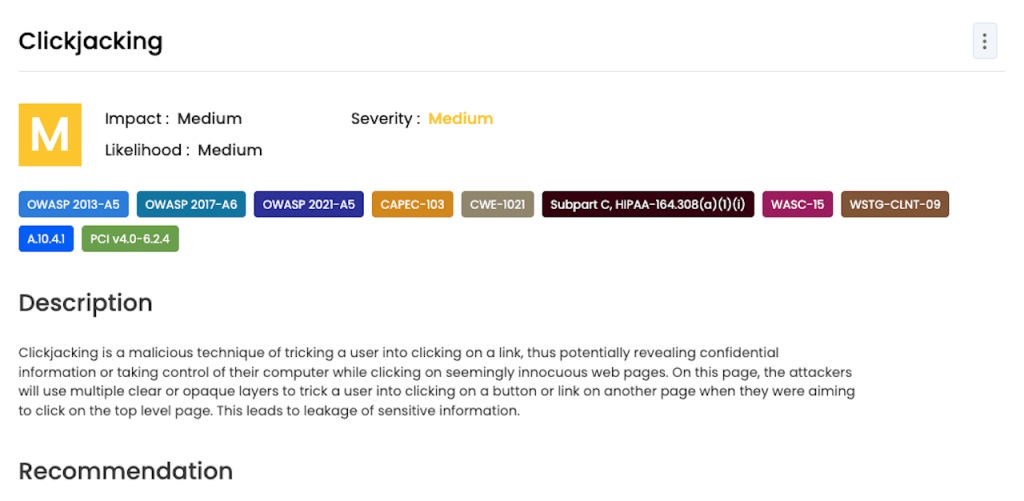
Beagle uses AI to offer detailed and tailored recommendations to address security issues.
For remediation, Beagle Security offers integrations with popular project management and bug tracking tools such as Atlassian Jira, Asana, Azure Boards, and Trello, as well as lesser-known ones such as Bugasura.io. What these integrations provide is 1-click support ticket creation. Beagle also has webhooks and an integration with Zapier for roughly the same purpose.
Finally, Beagle offers official-looking testing reports, as well as compliance reports for HIPAA, PCI DSS, and GDPR (the latter on the Advanced plan and above). For $49/month, you can make the reports look as if they were generated not by Beagle Security, but by your MSSP.
Prioritization and Remediation with Attaxion
Attaxion offers more prioritization context and flexibility, as, in addition to severity, it also provides CVE details, EPSS score, and CISA KEV data (only for CVE vulnerabilities though, as this data simply doesn’t exist for non-CVE issues). So, with Attaxion, you know which issues have a higher risk of being exploited and are actually exploited in the wild.
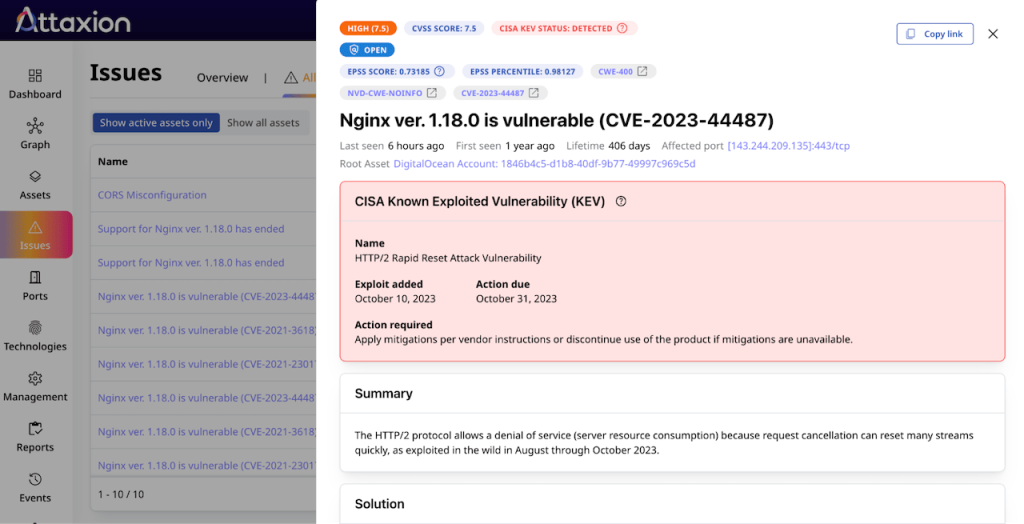
The platform lists the issues in a more traditional way – as a list of everything that you can then sort or filter by severity, CISA KEV status, affected asset, etc. Each issue is marked as open by default, but you can mark it as fixed, accepted risk, or false positive.
Attaxion can generate only one kind of report for every asset. But you can also download CSV files with lists of assets, filtered lists of issues, technologies, etc.
For remediation purposes, Attaxion has an integration with Jira, which also allows one-click support ticket creation.
How They Compare
Attaxion has an important advantage when it comes to prioritization, thanks to EPSS and CISA KEV data that provide insight into exploitability. Beagle Security has a heavier focus on application security, with its OWASP Top 10 and CWE Top 25 lists.
Beagle leads when it comes to vulnerability reporting, with its official compliance reports and white-labeling abilities. It also has more integrations with ticketing tools, but the remediation capabilities are the same – both Attaxion and Beagle offer 1-click ticket creation.
 PART 5
PART 5
Continuous Monitoring
Continuous Monitoring with Beagle Security
Beagle Security by default doesn’t run any tests continuously. Since tests are its currency, it tries to give you control over how you spend them, allowing you to either trigger a test manually or schedule tests on a regular basis – from weekly to biannual. Tests can also be triggered by external events via integrations with CI/CD tools, for example.
With its heavy DevSecOps focus, the platform has as many as a dozen CI/CD integrations, including with popular tools like GitHub Actions, GitLab CI, Jenkins, and others. The primary purpose of these integrations is the ability to trigger tests from continuous integration pipelines, which, in turn, are triggered by merge requests or code commits.
On top of that, Beagle Security offers an API that you can use to connect it with other tools. All of that makes Beagle’s monitoring capabilities very flexible, but not really continuous. Rather, they are on-demand, triggered. And given that the DevOps methodology calls for deployment to production many times a day, you’ll quickly run out of paid tests if you try to stick to DevSecOps and implement Beagle Security into the release pipeline.
When it comes to notifications, Beagle again offers integrations with different platforms such as Slack, Discord, and Microsoft Teams to make sure you don’t miss a scan report.
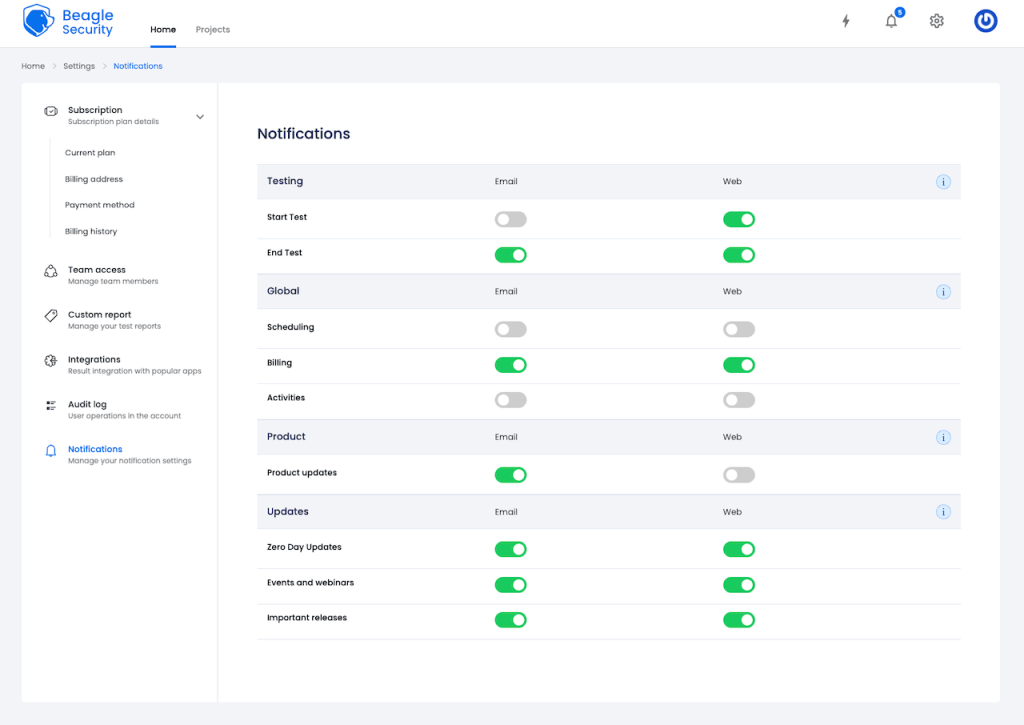
While notification settings appear extensive at first glance, they offer basic customization which boils down to choosing whether you want to receive notifications about starting tests and their completion.
Continuous Monitoring with Attaxion
Unlike Beagle, Attaxion keeps scanning the organization’s attack surface continuously. It has a completely different workflow: while Beagle focuses on the targets you’ve provided or subdomains it once found, Attaxion keeps looking for assets and regularly scans everything that it finds for security issues.
Attaxion isn’t made for DevSecOps, so it doesn’t have integrations with CI/CD tools, but that fact doesn’t change much, as, thanks to continuous attack surface discovery, Attaxion will find and scan everything you’ve deployed roughly within a day. With Beagle, it’s likely going to take more time, unless you pay for daily tests of all your targets.
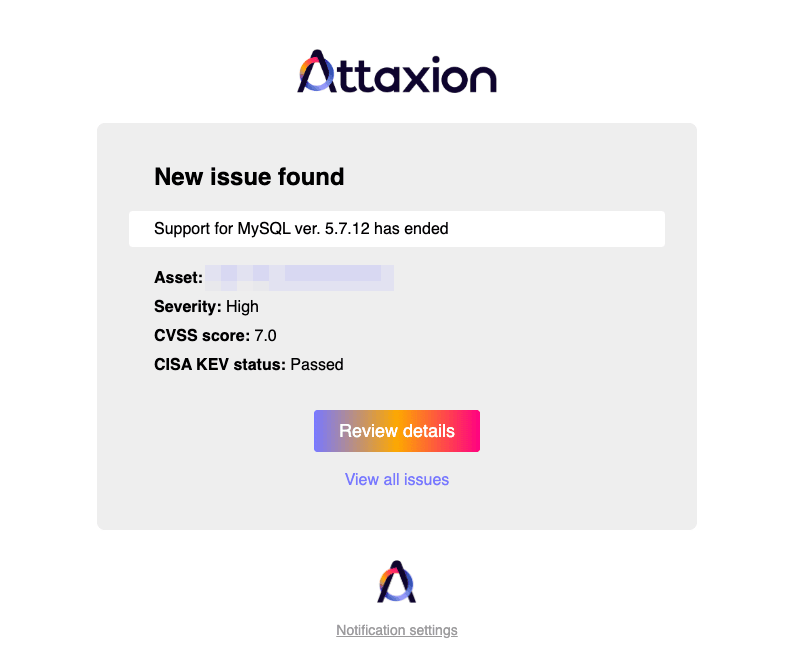
Attaxion also offers email notifications and has an integration with Slack. Currently, there are no Teams or Discord integrations, but the team offers to develop integrations (these or any other) on demand.
Attaxion’s REST API lets you feed its findings into other tools or dashboards, so you can adapt the data to your team’s existing workflows.
How They Compare
Beagle has useful integrations for continuous delivery, but if you set up tests to run on every deployment, you’ll quickly run out of tests – you’ll need to be careful with that. Otherwise, Beagle can schedule scans, but no more frequently than weekly. Attaxion scans your entire external attack surface continuously (roughly daily) out of the box, which gives you an almost real-time picture. Beagle is more integration-rich, though both tools have an API that allows you to build the missing integrations.
 PART 6
PART 6
Conclusion
Beagle Security is a great choice for automated penetration testing – it’s quite thorough, it offers authenticated scanning with various authentication methods and business logic recording, it can scan APIs and generate nice reports. Last but not least, it has useful integrations with CI/CD tools to enable DevSecOps. It’s also not very expensive, if you don’t run tests too often, and is useful for both red and blue teams.
But when it comes to continuous monitoring and control over the entire external attack surface, Attaxion is far ahead of Beagle. It doesn’t impose limits on the number of scans, instead scanning continuously and updating you immediately once it finds an issue. Its asset discovery capabilities far surpass what Beagle has to offer, it has better prioritization, and it’s roughly three times less expensive.
It doesn’t have that many integrations, API/GraphQL scanning capabilities, and many bells and whistles, but as a vulnerability management tool, Attaxion is a more capable and more affordable Beagle Security alternative.
Ready to try Attaxion? Start a 30-day free trial, or request a personal demo.