Cyber reconnaissance, sometimes referred to as “recon” for short, is the process of gathering as much intelligence as possible about a target system or network. Penetration testers and security researchers do it to uncover system vulnerabilities and other information like a target’s network infrastructure, employee contact details, and any other data that can serve as attack entry points.
Cyber reconnaissance aims to identify attack vectors or ways attackers can use to get into a target organization’s network. During reconnaissance, cybersecurity specialists—and possibly bad actors, too—use techniques, such as footprinting, scanning, enumeration, and social engineering.
Table of Contents
- What Are The Types of Reconnaissance?
- What Techniques Are Used to Perform Cyber Reconnaissance?
- What Types of Data Are Gathered during Cyber Reconnaissance?
- Why Is Cyber Reconnaissance Important?
- What Are the Use Cases of Cyber Reconnaissance?
- What Happens After Cyber Reconnaissance?
Cyber Reconnaissance: A Deep Dive
What Are The Types of Reconnaissance?
There are two types of reconnaissance—active and passive.
Active vs Passive Reconnaissance
The core difference between active and passive reconnaissance lies in the level of interaction with the target system. Active reconnaissance involves direct interaction, while passive reconnaissance operates at a distance, without directly engaging with the target.
What Is Active Reconnaissance?
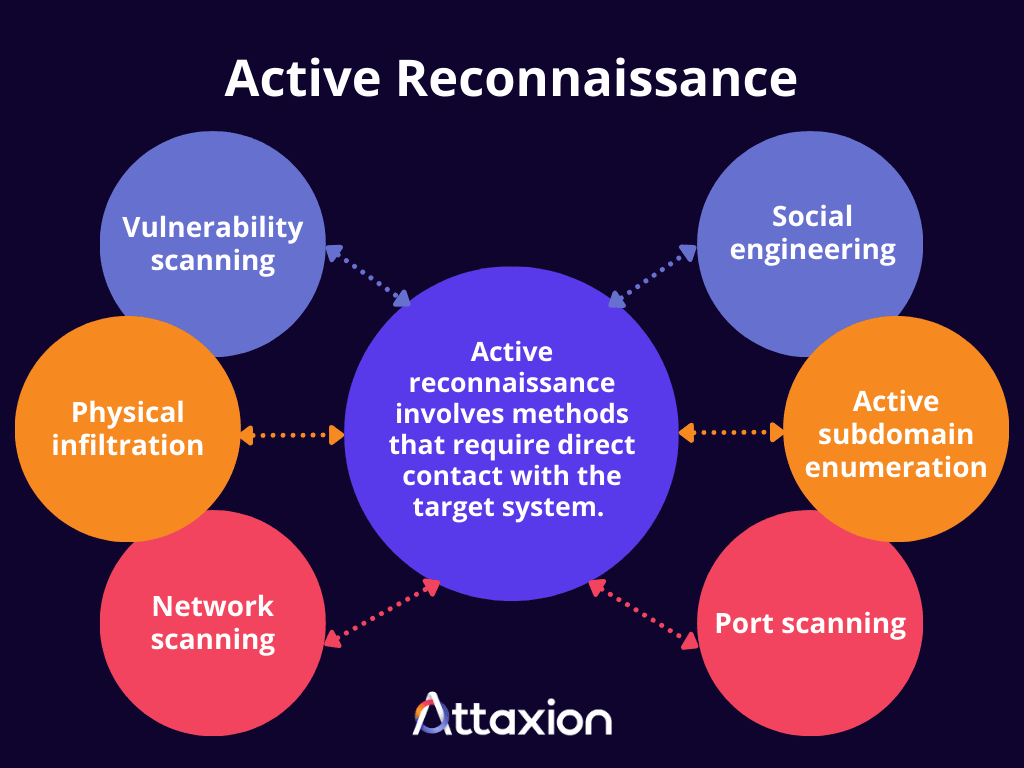
Active reconnaissance is the type of reconnaissance that covers methods requiring direct contact with the target to gather information. This is done by sending probes or specific requests designed to elicit responses that would then provide information about the target infrastructure configuration, open ports, active services, and vulnerabilities.
Active Reconnaissance Techniques
Several techniques fall under the umbrella of active reconnaissance, including the following:
- Active subdomain enumeration: This technique identifies the subdomains of a target domain by directly interacting with it through various methods, such as sending DNS queries to its name servers and analyzing the responses or using web crawlers to discover subdomains through links within the website. Active subdomain enumeration allows not only to find subdomains, but also understand if they are in use.
- Port scanning: Port scanning involves directly sending network packets to specific ports on a target system to actively probe for listening services, essentially knocking on the ports to see if any of them answer and what services they offer.
- Network scanning: This reconnaissance method involves sending packets to the target network to identify active devices (also known as hosts), along with details about those devices and their services.
- Physical infiltration: Threat actors or penetration testers can gain entry into a company’s office through deception, such as by disguising themselves as inspectors or tailgating (following an employee and pretending they also have access but forgot their badge).
- Vulnerability scanning: Active vulnerability scanning involves directly sending target systems probes and analyzing the responses to identify security issues. These probes are specifically designed to test for known vulnerabilities, misconfigurations, and other potential attack entry points. Interestingly—and counterintuitively—passive vulnerability scanning is also an active reconnaissance technique. While passive vulnerability scanners don’t send any unusual traffic to the target system, they often require some interaction with it—like sending normal requests to a website to analyze HTTP headers. These interactions fall under the definition of active reconnaissance that we’ve given above. If the passive vulnerability scanner is deployed on premises and only analyzes network traffic without any interactions with the target system, that behavior may be classified as passive reconnaissance (which we describe in more detail below).
- Social engineering: Attackers can manipulate individuals within an organization into divulging sensitive information that can be used to launch further attacks.
Active Reconnaissance Advantages and Disadvantages
Active reconnaissance techniques yield a substantial amount of highly specific and actionable intelligence. They identify active systems and services based on responses to requests—if the system is off or the service is not listening on a port, then there won’t be any response at all. Active reconnaissance provides a real-time snapshot of assets (and their services) that are currently online and functioning.
However, active reconnaissance also has notable disadvantages, including the significant risk of detection since actively sending probes to a target leaves a footprint that Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) are designed to identify and flag.
Moreover, methods like port scanning and vulnerability scanning have the potential to disrupt normal system operations since sending a high volume of unexpected packets can cause network congestion or services to crash. Finally, active reconnaissance methods can be time-consuming and resource-intensive—scanning large networks or complex infrastructures requires significant time, bandwidth, and computational resources.
What Is Passive Reconnaissance?
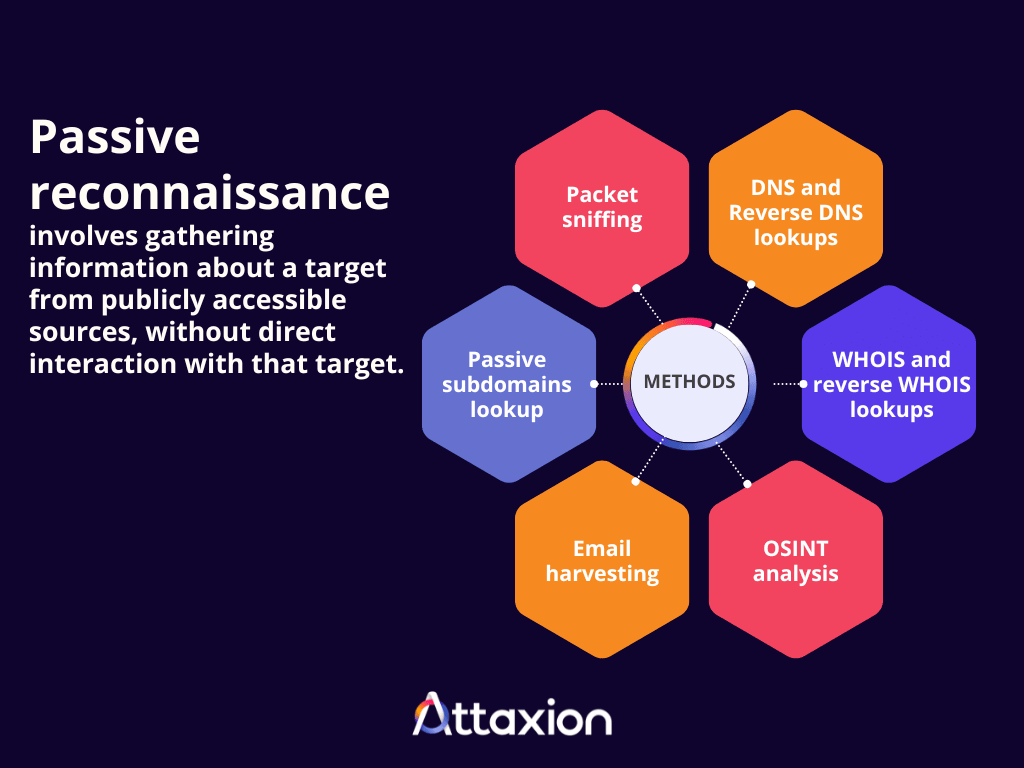
Passive reconnaissance is the subset of cyber reconnaissance that covers the methods which do not require direct interaction with the target. It involves gathering information about a target from publicly accessible sources, such as Open Source Intelligence (OSINT) and premium third-party intelligence sources.
Passive Reconnaissance Techniques
Here are a few examples of passive reconnaissance methods:
- Historical DNS and reverse DNS lookups: These lookups involve querying passive DNS repositories to uncover relationships between domain names and IP addresses. They avoid direct interaction with the target’s DNS servers and instead rely on past DNS resolutions.
- WHOIS and reverse WHOIS lookups: These techniques examine domain registration records to find out the name server, registrant email address, and other details. Or, based on those details, find other associated domains, also relying on WHOIS data.
- OSINT analysis: OSINT analysis involves scrutinizing search engine results, social media profiles, job boards, news articles, and other publicly available content for any details about the target organization.
- Email harvesting: This method involves collecting publicly listed email addresses from websites or using sales intelligence platforms like Apollo to aggregate contact information.
- Passive subdomains lookup: Instead of sending DNS queries to a target to obtain its subdomains, passive subdomain lookup relies on publicly accessible sources, such as passive DNS databases that collect and store DNS records and the use of advanced search operators (site:*.targetdomain.com) to find subdomains indexed by search engines.
- Packet sniffing: This technique relies on the pre-existing circumstance of the reconnaissance team already having access to the system, allowing them to capture and log network traffic—essentially eavesdropping on the communication happening on the target network.
Passive Reconnaissance Advantages and Disadvantages
One of the biggest advantages of passive reconnaissance is its low risk of detection by the target organization’s security systems. Since they avoid direct contact, passive methods leave no footprint that could trigger alarms or alert the organization to the ongoing intelligence gathering.
Passive reconnaissance also poses no threat of disrupting the organization’s operations since it does not include active probing or exploitation. In addition to that, it does not require as many resources as active reconnaissance does, as it does not rely on brute force techniques and does not involve exploitation attempts that take a lot of time and compute resources..
However, passive reconnaissance also has certain drawbacks. One major limitation is that the data gathered can be noisy, inaccurate, or even irrelevant, increasing the risk of false positives, as passive reconnaissance doesn’t offer validation for the collected data. In addition, the collected information might be incomplete or outdated and may not reflect the current state of the target’s infrastructure.
Using Active and Passive Reconnaissance Together
While active and passive reconnaissance have a lot of differences, they are not mutually exclusive. A blended approach is ideal, yielding the most comprehensive and insightful results, especially since some active reconnaissance techniques are more intrusive than others.
A common strategy involves initiating the reconnaissance process with passive methods to get a baseline of the target. After that, more targeted active reconnaissance techniques can be used to validate the initial findings and gather more information.
What Types of Data Are Gathered during Cyber Reconnaissance?
The data points typically collected during cyber reconnaissance include network information (e.g., IP addresses, open ports and services, and network configurations), system details (e.g., OS, software versions, system names, usernames, and email addresses), security issues (e.g., misconfigurations and vulnerabilities), and organizational data (e.g., employee names and roles, and security policies).
In addition, reconnaissance can help gather information from social media profiles, company websites, and other public sources.
Why Is Cyber Reconnaissance Important?
Threat actors make calculated moves before launching full-blown attacks. They observe which areas in a target system can serve as entry points. In a way, they also perform their version of reconnaissance.
Therefore, making cyber reconnaissance a part of an organization’s cybersecurity strategy enables security teams to examine their systems through cyber attackers’ eyes. Security teams can use reconnaissance techniques to identify weaknesses in their systems before attackers do, enabling them to be proactive in their defenses and ASM strategies.
Understanding what attackers can potentially see in their systems also allows security teams to implement more effective security controls and mitigation strategies. As a result, organizations can develop a more robust security posture.
What Are the Use Cases of Cyber Reconnaissance?
Cyber reconnaissance is the usual first step in penetration testing, a simulated attack on an organization’s system. Aside from that, cyber reconnaissance can have a deeper and more strategic purpose. In particular, it helps organizations in these areas:
- Risk management: The process allows organizations to analyze which areas in their IT environments are most prone to cyber attacks.
- Attack surface management (ASM): Reconnaissance exposes threat vectors that make up an organization’s attack surface, allowing security teams to manage and reduce it.
- Vulnerability management: By performing techniques that test a system’s security, cyber reconnaissance helps organizations understand and mitigate the most vulnerable areas, improving its security posture.
Regulatory compliance: Since the process brings to light system vulnerabilities, entities can work toward securing their whole IT infrastructure and ultimately comply with industry standards and regulations.
What Happens After Cyber Reconnaissance?
Upon identifying security issues through reconnaissance techniques, security teams can prioritize and patch them to eliminate attack vectors and reduce their attack surface. Other reconnaissance findings may require teams to implement new security controls, such as firewalls, intrusion detection/prevention systems (IDSs/IPSs), data loss prevention (DLP) solutions, or endpoint security software.
Security professionals may also leverage reconnaissance results to inform security awareness training. For example, if the findings highlight potential social engineering tactics attackers use, then security teams can educate employees about these tactics to reduce the risk of successful attacks.
—
To get ahead of attackers, security teams must regularly put cyber reconnaissance into practice. Doing so enables them to protect their systems based on what the enemy may already be seeing.
Key Takeaways
- Cyber reconnaissance refers to the process of gathering information about a target system or network.
- It is an essential part of an organization’s proactive cyber defense strategy.
- The goal of reconnaissance is to find and eliminate potential attack vectors and vulnerabilities.
- Cyber reconnaissance techniques include footprinting, scanning, and enumeration.
- Security teams use tools like ASM platforms, network scanners, and vulnerability scanners to perform reconnaissance.
- Cyber reconnaissance use cases include risk management, ASM, vulnerability management, and regulatory compliance.
Attaxion uses modern reconnaissance methods to uncover hidden vulnerabilities and help expand your attack surface intelligence. Start your free trial now.
