Free Open Source Attack Surface Management: Is It Enough?
Upon looking at another costly tool, have you ever asked yourself a question like “Can we just use free open-source cybersecurity tools instead of this expensive stuff?”
If you did, you’re not alone. Software is often expensive, and cybersecurity budgets are always very limited. Fortunately, you can find a lot of open-source security applications — from vulnerability scanners to reconnaissance tools and from endpoint antiviruses to SIEM platforms.
Some open-source security tools, such as Kali Linux or Wireshark, are so good that they basically have no alternatives. However, in many areas, commercial solutions still dominate the market – and apparently, for a reason.
In this article, we’ll go through a list of popular open source or free attack surface management tools and discuss their pros and cons. We’ll also try to answer the questions about whether individual open-source tools or some combination of them is enough to cover your external attack surface management (EASM) needs or if the price of paid EASM tools is actually justified.
Table of Contents
 INTRO
INTRO
What Does EASM Consist Of
For an introduction to external attack surface management, we suggest that you read our EASM guide. Here, we’ll quickly outline the steps of the EASM process so that we can match open-source tools with them.
The external attack surface management process consists of four stages:
1. Network mapping and asset discovery
The first stage is understanding what assets your organization has. So, an EASM platform should be able to perform cyber reconnaissance and discover external assets (by doing subdomain enumeration, network mapping, port scanning, etc).
There’s a bunch of open-source tools for this, including widely used Nmap and Sublist3r, for example.
Many EASM solutions also scan websites for technology that is used to build them and 3rd party tools like analytics or A/B testing platforms that are connected to them. The famous and previously open-source platform called Wappalyzer used for this went private, but there’s still a fork of the original Wappalyzer repository which you can access for free.
2. Vulnerability scanning
After discovering the assets, all of them should be scanned for vulnerabilities.
To do that, you’ll need a vulnerability scanner. Again, there are plenty of open-source security tools for vulnerability scanning like OpenVAS, Nuclei, ZAP by Checkmarx, and more.
In fact, many commercial EASM and DAST tools rely on open-source scanners or some combination of open-source and commercial scanners.
3. Vulnerability prioritization and remediation
Just detecting vulnerabilities isn’t enough to enable external attack surface management; a good EASM tool should also help security practitioners prioritize and remediate or mitigate the risks. Essentially, this is vulnerability management.
This is where open-source ASM solutions typically fall short, because most of them are made for offensive security purposes. Mostly, they are used for penetration testing and bug bounty hunting and are not meant for continuous usage. However, there are some exceptions like Faraday which were designed specifically for this purpose. The open-source, community edition of the tool is quite limited and can’t handle automatic ticket-creation, but at least it exists.
4. Continuous monitoring
Finally, EASM solutions should offer continuous monitoring, which basically boils down to running reconnaissance and vulnerability scans again and again and notifying the user about new assets and issues, as well as generating reports.
That is, perhaps, the most problematic part. From the first three points, you might’ve noticed that it’s mostly individual tools that are capable of covering individual tasks, but none of them covers them all.
To enable continuous monitoring, you need some glue that brings them together. After the cyber reconnaissance stage, all newly detected assets should also be scanned for vulnerabilities, and all the vulnerability data should go into a single source of truth so that you can then use it to send notifications.
Tools like Faraday can handle notifications, but the open-source community edition doesn’t offer reporting capabilities.
 SOLUTION 1
SOLUTION 1
Open-Source Attack Surface Management Tools
1. OWASP Amass: Open-source cyber reconnaissance
| OWASP Amass | |
| Type | Network mapping and external asset discovery tool |
| GUI | ❌ |
| Installation | Source, Binary, Docker |
| Last updated | 2023 (v 4.2.0) |
| Pros | Well-known Easy to use Flexible & configurable |
| Cons | Doesn’t include vulnerability scanning, prioritization, etc Requires API keys for paid APIs to produce better results |
OWASP Amass is one of the most well-known reconnaissance and network mapping tools that a lot of other security tools rely on.
It doesn’t offer a graphical user interface, only accepts a few commands, and its main function is external asset discovery using the `enum` command. What sets it apart is how deeply configurable it is. Amass allows connecting dozens of different APIs (some free, some paid) which can provide additional data to enhance its reconnaissance capabilities.
It does a decent job at discovering assets even without APIs, but begins to shine when it can get additional input from the APIs.
But Amass is just that – a reconnaissance and enumeration tool, which doesn’t go beyond this role. It neither has a vulnerability scanner nor offers a vulnerability management platform. So, it could only cover the first stage of the EASM process, leaving the rest to some other tools.
 SOLUTION 2
SOLUTION 2
2. EasyEASM: Command line-based asset discovery tool + notifications
| EasyEASM | |
| Type | Reconnaissance and external asset discovery |
| GUI | ❌ |
| Installation | Source |
| Last updated | 2023 (v 1.0.6) |
| Pros | Relatively easy to use Combines multiple reconnaissance tools |
| Cons | Seems somewhat abandoned (Nuclei integration pull request waiting approval for half a year) Currently doesn’t include vulnerability scanning, prioritization, etc |
EasyEASM has EASM in its name, which, logically, makes you think that it is an EASM platform. However, in reality, it’s again a reconnaissance solution which actually employs Amass as one of its main components.
Essentially, EasyEASM is a bunch of scripts that connect several reconnaissance tools – Amass, alterx, dnsx, and Subfind3r. On top of that, it offers Slack and Discord webhooks to enable notifications to these messengers about all the newly discovered assets.
For something with only a command line interface (CLI) and no GUI, EasyEASM is incredibly easy to use. Is it an external attack surface management platform though? No, because it’s missing at least two steps of the EASM process – vulnerability discovery and prioritization/remediation.
It can do a great job at finding assets for you, but you’ll need to code a connection with a vulnerability scanner and a vulnerability management system to actually make it into an EASM platform.
 SOLUTION 3
SOLUTION 3
3. Archery: Open-source application security orchestration
| Archery | |
| Type | Application security orchestration and correlation platform (ASOC) |
| GUI | ✅ |
| Installation | Source, Docker |
| Last updated | 10.2024 (v2.0.6 + hotfixes) |
| Pros | A lot of connectors to different dynamic and static scanners Connectors for most popular CI/CD platforms Jira ticketing system Combining dynamic and static application scanning |
| Cons | Very basic GUI Somewhat complicated setup Lack of notifications and reporting No asset discovery capabilities or connectors |
Archery doesn’t pretend to be an EASM platform, but it has some similarities. It is an application security orchestration and correlation platform (ASOC), and its main goal is enabling DevSecOps.
Archery integrates with web app vulnerability scanners like ZAP or OpenVAS and with continuous integration & deployment (CI/CD) platforms like Jenkins to enable dynamic and static application security scanning.
Unlike many other open-source cybersecurity solutions, Archery has a graphical user interface, which offers some dashboards and graphs. It even has an ability to create Jira tickets for individual vulnerabilities.
For application security purposes, Archery looks really interesting, but it’s not an EASM solution. It lacks reconnaissance capabilities and doesn’t offer to connect asset discovery tools like Amass. It doesn’t offer much when it comes to notifications and reporting either.
Also, Archery is only suited for development environments. The documentation section for running it in production is blank as of the time of writing this article.
 SOLUTION 4
SOLUTION 4
4. reNgine: A GUI-based ASM without vulnerability management
| reNgine | |
| Type | ASM |
| GUI | Yes |
| Installation | Docker |
| Last updated | 10.2024 |
| Pros | Combines various reconnaissance and asset discovery components Continuous monitoring for new assets with notifications |
| Cons | Limited vulnerability management capabilities |
reNgine is quite close to being a full-fledged EASM solution. It combines a bunch of asset discovery tools with open-source intelligence not only about an organization’s digital footprint but also about its employees, which can be helpful for social engineering prevention.
On top of that, it offers vulnerability scanning and continuous monitoring functions. It’s also connected to a GPT that can spit out vulnerability descriptions with remediation suggestions.
With a user-friendly GUI, reNgine makes it easy for teams to run cyber reconnaissance processes like subdomain enumeration, port scanning, and service identification.
What reNgine lacks in terms of EASM features is proper vulnerability management and remediation capabilities.
 SOLUTION 5
SOLUTION 5
5. reconFTW: Command line-based open-source ASM without vulnerability prioritization capabilities
| reconFTW | |
| Type | ASM |
| GUI | ❌ |
| Installation | Source, Docker, Terraform + Ansible |
| Last updated | 9.2024 |
| Pros | Huge selection of open-source recon tools and scanners Integrations with Slack, Discord, and Telegram |
| Cons | No GUI No vulnerability management No Jira integration Complicated setup |
reconFTW positions itself as an attack surface management tool for offensive security purposes – and is quite close to actually being a real ASM. It combines dozens of other open-source reconnaissance and asset discovery tools (think Nmap, Subfinder, and the like) with various targeted vulnerability scanners (think Nuclei, ffuf for fuzzing, katana, etc).
This combination allows for repeated discovery and mapping of external assets, followed by scanning them for vulnerabilities. As a cherry on top, reconFTW supports notifications across email and popular messengers. This combo is quite useful for red teams, but can be helpful for blue teams as well.
However, reconFTW is still primarily focused on the mapping and detection phases. It doesn’t include a vulnerability management or prioritization system, requiring users to export findings to other platforms. For better reconnaissance, just like Amass, it requires API keys from various APIs, some of which are commercial.
Also, reconFTW only has a command line interface – there’s no GUI. And it might take a while to set it up.
 SOLUTION 6
SOLUTION 6
6. Faraday Community Edition: a free tier of a commercial vulnerability management platform
| Faraday | |
| Type | Vulnerability Management Platform |
| GUI | Yes |
| Scanners | No (Integrations with ZAP, Nuclei, Nessus, Metasploit, etc.) |
| Installation | Docker, Binary, Source |
| Last updated | 11.2024 (v5.8.0) |
| Pros | Actively supported Nice GUI |
| Cons | No vulnerability prioritization in the free, community edition More of a connector for 3rd party tools than a self-sufficient tool |
Faraday is a vulnerability management tool designed to work with a range of popular scanners like ZAP, Nuclei, and Tenable Nessus (note that this one is proprietary and commercial).
There are several versions of Farday, and for the purpose of this article we’re looking at the free Faraday Community Edition. Its primary purpose is to centralize and manage vulnerability data, enabling users to prioritize findings and track remediation progress.
Faraday offers a nice GUI that makes it accessible and easy to work with. It can send notifications, so it partially covers the continuous monitoring stage as well.
But having multiple tiers should tell you right away that the free tier is limited. That is indeed the case: Faraday Community Edition doesn’t offer vulnerability prioritization or reporting, which is only available on paid tiers starting from the Personal plan.
Also, Faraday is completely missing the asset discovery and mapping stage – it expects you to provide a list of assets that it’s going to use as targets. For full EASM capabilities, security teams would need to combine it with reconnaissance tools like Amass or EasyEASM and vulnerability scanners. The connectors with the latter are in place, but you’ll need to develop integrations with the former yourself.
Only then you’ll be able to configure automated workflows to update the platform with new assets and vulnerabilities. Basically, Faraday could be a graphical user interface on top of an asset discovery and vulnerability scanning toolstack that you’ll need to engineer yourself.
 SOLUTION 7
SOLUTION 7
7. Qualys Community Edition: A free ASM for 3 external assets
| Qualys Community Edition | |
| Type | Vulnerability Management Platform |
| GUI | ✅ |
| Installation | Cloud |
| Last updated | ? |
| Pros | Well-known and supported by a big name User-friendly GUI Covers everything from asset discovery to continuous monitoring |
| Cons | Severely limited asset count |
Qualys Community Edition is a free (but not open-source) version of Qualys’ well-known vulnerability management platform. It is cloud-based, which makes it almost unique among other free attack surface management-related solutions, simplifying setup and removing the need for additional infrastructure.
Qualys Community Edition covers the entire spectrum of ASM tasks – it discovers assets and adds them to an asset inventory, scans them for vulnerabilities, offers reports and notifications.
While the Community Edition allows organizations to experience some of the functionality of Qualys’ paid solutions, it comes with limitations, such as a cap on the number of assets – the free version allows you to scan 3 external assets and 16 internal assets.
For very small organizations of 1-3 people with very little online presence, Qualys Community Edition could be a sensible option that provides good security at no cost. However, those looking for a full-scale EASM platform will need to pay for a commercial Qualys license.
 FREE VS COMMERCIAL ASM
FREE VS COMMERCIAL ASM
Comparison With Commercial EASM Solutions
So, we just did a quick overview of open-source tools that are somewhat related to attack surface management or vulnerability management. What if we try comparing it with a relatively inexpensive paid solution that supports EASM – Attaxion? (By the way, if you’re looking to compare commercial platforms against each other, we have a guide to best external attack surface management platforms as well)
Like most other commercial solutions, Attaxion doesn’t require installation – it’s a cloud platform and it works right out of the box (if the ‘box’ metaphor is even applicable to SaaS).
It combines multiple cyberrecon techniques to discover external assets. While apps like Amass require you to connect additional paid APIs to enhance reconnaissance capabilities, Attaxion has access to some of these APIs under the hood and doesn’t require additional payments or additional configuration.
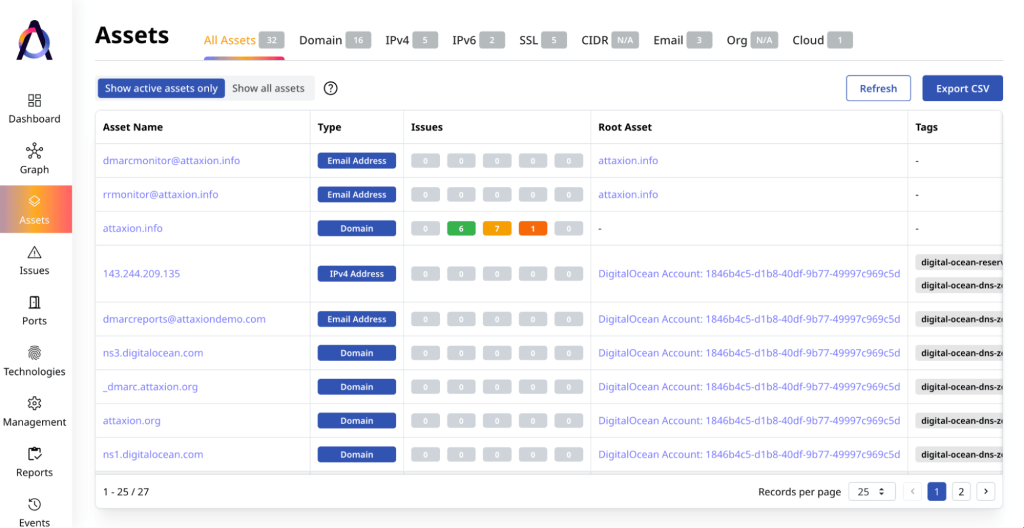
Attaxion automatically passes newly discovered assets as targets for vulnerability scanning and continuously runs both reconnaissance and vulnerability scans, making sure that you have a complete picture of your entire external attack surface at every moment.
That is one of the key differences between open-source ASM and commercial EASM platforms – the latter don’t need to be manually fed with new targets discovered by network scans, port scans, and other cyberrecon techniques.
Attaxion offers a flexible toolkit for vulnerability prioritization and remediation, providing CVSS and exploit prediction (EPSS) scores alongside with CISA KEV data about exploitability in the wild for each CVE. It has integrations with Atlassian Jira and Slack to enable automatic support ticket creation and notifications. That’s what most open-source solutions also lack: since most of them are aimed at red teams and penetration testing, barely any of them have a Jira integration.
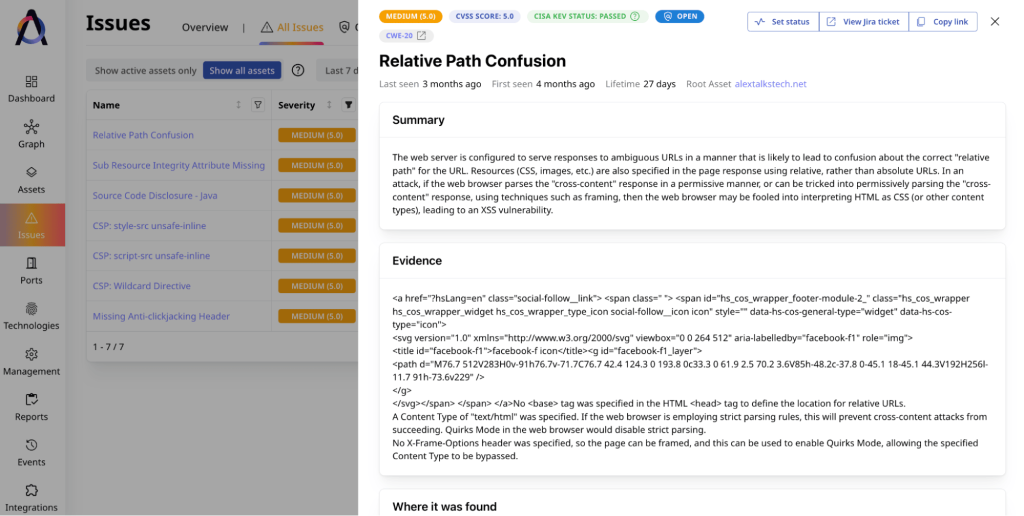
Finally, commercial solutions like Attaxion have support teams that answer your questions and help you solve problems.
Overall, Attaxion offers a broader range of features and covers all steps of the EASM process, which open-source tools can’t do.
 CHOOSING THE BEST
CHOOSING THE BEST
Conclusion: Are Open-Source EASM Tools Enough?
In this article, we’ve briefly evaluated 7 popular free cybersecurity ASM solutions that have thousands of stars on GutHub. We’ve mentioned many more single-purpose open-source tools like vulnerability scanners, network mappers, and more. So, are they enough to fully cover the EASM process?
Individually, only Qualys Community Edition covers the entire EASM process, but only for 3 external assets. Some tools like Amass or EasyEASM do a great job at the reconnaissance stage, but lack everything else. Others, like Faraday, act like a glue between different open-source tools, but also fall short when it comes to vulnerability prioritization and remediation assistance.
Theoretically, it’s possible to combine a bunch of those open-source ASM-related components together to create something like a Frankenstein’s monster of an EASM. But you’ll need to do it yourself, connecting the tools and making sure they work together. Also, you’ll need infrastructure to deploy them to.
So, we can conclude that open-source ASM apps can be pretty helpful mostly for bug-bounty hunters and penetration testers, who don’t need continuous monitoring or vulnerability prioritization/remediation. If all they need is cyberreconnaissance and/or vulnerability scanning, free open-source tools may be enough.
However, for security teams that need continuous coverage of their entire internet-facing infrastructure, commercial tools like Attaxion can be a better and easier choice. They work out of the box, they cover all stages of the EASM process, including asset discovery, vulnerability scanning, prioritization, remediation, and continuous monitoring.
Finally, with open-source tools, you’re on your own and rely on the community for help, while commercial solutions have customer support teams that can help you if you run into some blocker.
Ready to see Attaxion in action? Start a 30-day trial now.