Best Acunetix Alternative: Comparison With Attaxion
Acunetix by Invicti is a widely known tool that is a little hard to classify. Is it a dynamic application security testing tool (DAST)? Yes. Does it have some features that are more typical for interactive application security testing (IAST) platforms? Yes, it does. Does it also tackle asset discovery in addition to testing each individual application like a full-fledged external attack surface management (EASM) solution would? Yes, it does.
That’s why some organizations use this hybrid between DAST and IAST as an EASM tool as well, just with a bigger focus on application security.
Attaxion is an exposure management platform that offers EASM as one of it’s core capabilities. But you can also use it as a DAST solution, because the functionality is pretty similar. In this article, we want to compare the two tools and see if Attaxion is a good alternative to Acunetix (and Invicti, which is not only the name of the company that owns Acunetix but also the name of their enterprise solution which is actually quite similar to Acunetix).
Quick Summary
| Feature | Attaxion | Acunetix |
| Pricing | Starting from $1,290/year for 40 assets | Starting from ~$5,400/year for 5 assets |
| Discovery and dependency graphs for digital assets | ✅ | ❌ |
| Non-intrusive vulnerability scanning | ✅ | ❌ |
| Intelligent vulnerability prioritization with EPSS and CISA KEV | ✅ | ❌ |
 INTRO
INTRO
EASM vs DAST: What is the difference?
Acunetix is a DAST tool with some additional features, while Attaxion is an EASM platform. Can they really be compared? Well, yes.
The general idea behind DAST and EASM is more or less the same – assume an attacker’s perspective and discover as many real security vulnerabilities or misconfigurations as possible. The difference between traditional DAST and traditional EASM is in the approach to this task.
| DAST | EASM | |
| Asset discovery | ❌(or basic functionality) | ✅ |
| Vulnerability detection and prioritization | ✅(intrusive) | ✅(almost non-intrusive) |
| Vulnerability remediation | ✅ | ✅ |
| Continuous monitoring | ✅(only for new vulnerabilities) | ✅(for new vulnerabilities and new assets) |
EASM focuses on discovering your organization’s external attack surface – all of its assets, including the ones you may not have known about or forgotten, together with their vulnerabilities.
DAST’s focus is more on vulnerability scanning – traditional DAST tools do not try to find assets, only scanning those that you’ve provided. However, DAST platforms approach scanning differently than traditional EASM security tools, focusing on more intrusive, payload-based scanning. This can accidentally knock the target that it’s scanning offline, but is also more fact-based and in some cases digs deeper than traditional EASM tools.
The thing is, Acunetix is not a traditional DAST tool, and Attaxion isn’t your average EASM. So, they have more in common than one might expect. Even though formally they belong to different categories, the team at Invicti doesn’t shy away from saying that their security tool can handle EASM. Which makes Attaxion and Acunetix perfectly comparable.
 PART 1
PART 1
Pricing
Acunetix pricing
The brand “Acunetix by Invicti” was created in 2017, when two main players in the DAST market – Acunetix Ltd. and Netsparker Ltd. merged together. After the merger, Netsparker became Invicti and is considered a more advanced solution. Acunetix became Acunetix by Invicti and took the role of a more affordable option.
Even though Acunetix has a pricing page, there are no official numbers there, and the only way to know how much Acunetix is going to cost for your organization is to reach out to sales and get a quote. The only thing you can find on the official page is that Acunetix is priced by website – the more websites it’s going to scan for you, the more you’re going to pay. A website in this context is something that lives either on a domain or a subdomain.
However, there is unofficial information on the Internet that can give you an idea about Acunetix’s pricing. For example, TrustRadius lists five different yearly pricing plans for Acunetix, ranging from $4,500 for up to 5 websites to $26,600 for 36-50 websites. On Amazon Marketplace, Acunetix is listed for $7,000 for up to 5 websites and $15,960 for an MSSP license. We suspect that the pricing on Amazon Marketplace is more recent.
Attaxion pricing
Unlike Acunetix, Attaxion has a publicly available pricing – not only the page, but the actual official numbers. Attaxion is priced by asset (which is not only websites, but also IP addresses, cloud instances, and more). The more assets you have in your external attack surface, the higher the price.
Attaxion is a more budget friendly solution, starting at $1,290 per year for 40 assets (that’s likely more than 5 subdomains, even though it’s hard to compare the pricing directly). The most expensive publicly available plan costs $9,490 per year for 360 assets. If you have more – you’ll need to talk to sales.
Attaxion also offers a 30-day free trial that you can start right away.
How they compare
Acunetix is not the most expensive cybersecurity tool on the market. At $7,000 per year, it’s a fraction of what, for example, Palo Alto Cortex Xpanse will cost. However, it’s still several times more expensive than Attaxion, which even on a Starter plan gives you more tracked assets.
 PART 2
PART 2
Asset Discovery
Asset Discovery with Acunetix
Unlike other DAST tools like Intruder.io, Acunetix by Invicti can discover assets that belong to your external attack surface. Like EASM tools, it needs some initial targets – usually domains or IP addresses – and then it can discover other assets that are related to it. It does not accept IP ranges (CIDRs) or cloud instances as root assets.
As a DAST, Acunetix cares mostly about web apps, so the assets that you’ll see in the asset list would be domains and subdomains. However, there are complaints on G2 about Acunetix generating false positives – finding web apps that don’t belong to your organization.
What makes Acunetix stand out is that it uses AI at this stage – not for discovery per se, but for prioritizing websites before they are thoroughly scanned for vulnerabilities. This feature is based on getting a technology fingerprint for each website. As a result, in the list of websites you’ll see that some are more likely to have high-severity vulnerabilities than others and Acunetix will suggest prioritizing them even before you run the first scan.
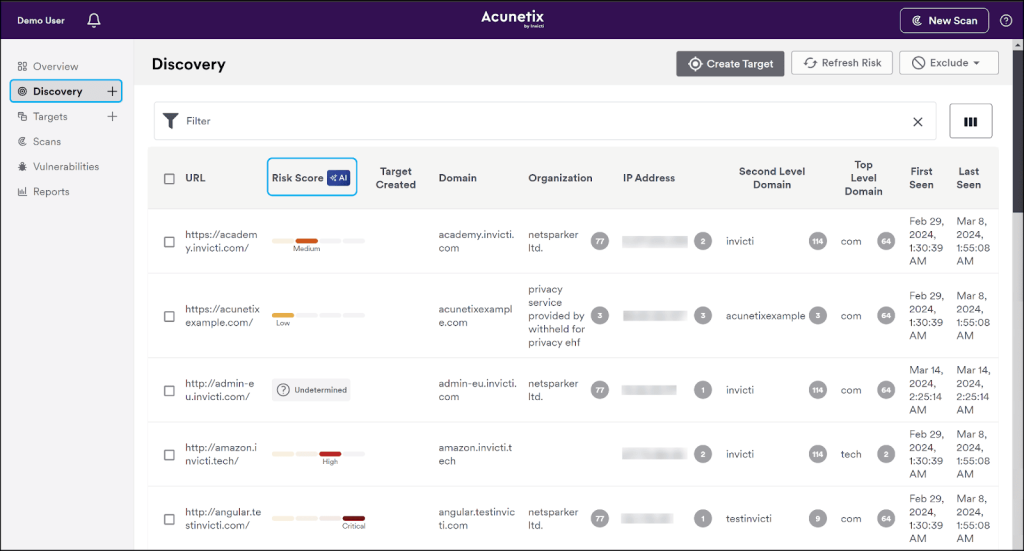
This is an interesting feature, but it doesn’t take into account any business context – whether an asset is important or not. Also, it’s a predictive feature, so it operates with probabilities rather than hard data.
Asset Discovery with Attaxion
Attaxion is a full-fledged external attack surface management solution, which means that discovering assets is one of its main functions. In Attaxion’s particular case, it’s also one of the main selling points, as Attaxion relies on multiple different reconnaissance techniques coupled with open source and closed source intelligence to find more assets than other EASM tools.
Attaxion also needs some targets or root assets to start discovering assets and mapping your external attack surface. It will also discover so-called “root asset candidates” that may belong to your organization – you can either add them as legit root assets or discard them as false positives. For them, Attaxion also offers probabilities.
Since Attaxion is an EASM, it cares about more than just websites. So, on its list of assets you’ll find different types of assets, from IP addresses and CIDRs to cloud instances and even public email addresses.
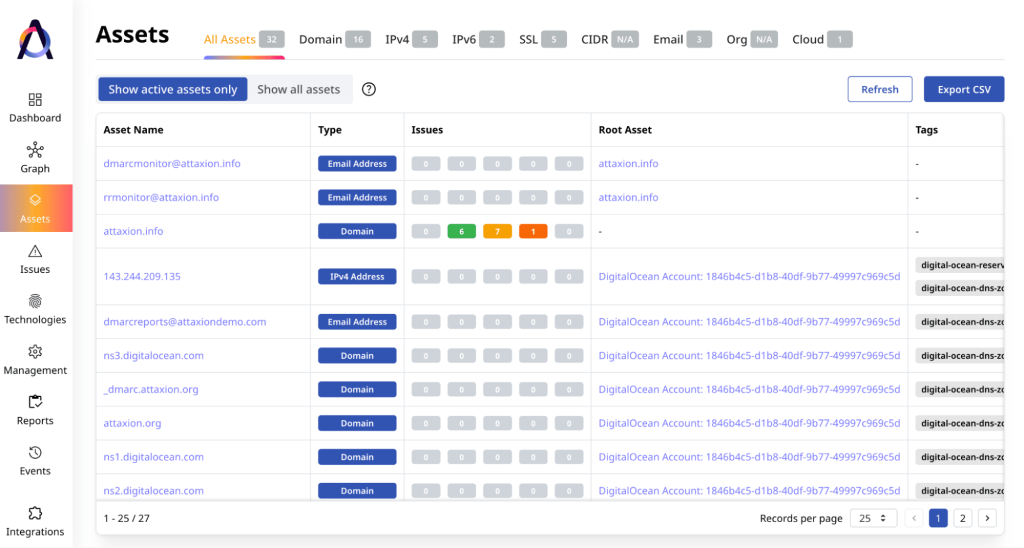
Attaxion also offers a dependency graph that can show you how your assets are connected with each other.
How They Compare
Attaxion beats Acunetix when it comes to the number of discovered assets of all kinds, including domains and subdomains, which isn’t a surprise, given how important asset discovery is for EASM and how most DAST tools don’t have any asset discovery at all.
 PART 3
PART 3
Vulnerability Scanning
Vulnerability Scanning with Acunetix
Acunetix employs its own vulnerability scanner that is quite different from those normally seen in EASM tools. This scanner is very active, relying on payloads that don’t just do handshakes on certain ports, but really try to exploit the vulnerabilities.
As a result, on the one hand, Acunetix provides you with reliable data on the vulnerabilities that you have with a low false positive rate. It also offers probability ratings ranging from 80% to 95% that a vulnerability is indeed there.
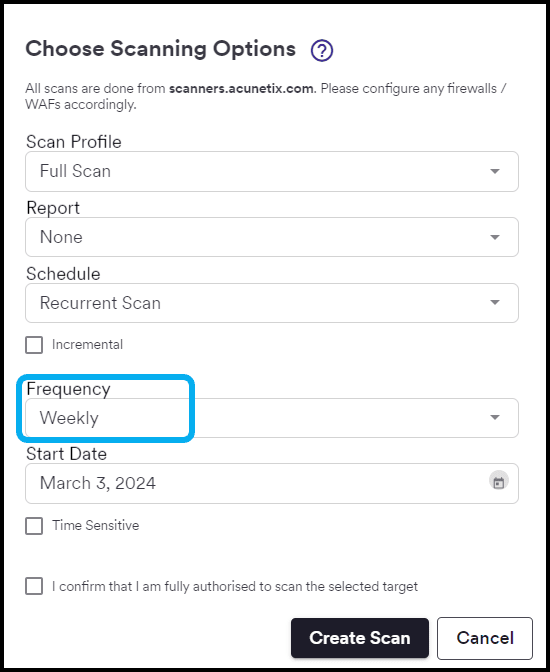
On the other hand, Acunetix is intrusive – almost on the same level as a real pentest. It means that it can slow a web app down, possibly significantly. The team behind Acunetix is obviously aware of this, that’s why it allows you to schedule application scanning so that it does not impact your web apps during peak usage times.
Vulnerability Scanning with Attaxion
Attaxion relies on a much less intrusive scanner that doesn’t deliver payloads to test each vulnerability.
Theoretically, that increases the number of false positives that Attaxion should have. In reality, though, Attaxion boasts a relatively low false positive rate while not presenting any danger to systems working in a production environment except for a low chance of triggering an intrusion detection system (IDS).
Unlike Acunetix, Attaxion scans for vulnerabilities continuously and doesn’t offer scheduling.
How They Compare
Acunetix and Attaxion take a very different approach to vulnerability scanning. Acunetix is intrusive, yet accurate. Attaxion is almost non-intrusive and doesn’t threaten to bring down production, yet manages to still offer a relatively low false positive level.
 PART 4
PART 4
Vulnerability Prioritization and Remediation
Vulnerability Prioritization and Remediation with Acunetix
When it comes to cyber risk prioritization, Acunetix offers very straightforward and minimalistic functionality. It even looks as if the team at Invicti designed Acunetix to be more of a red team tool rather than something a blue team would use, because it has integrations with Metasploit and other penetration testing software.
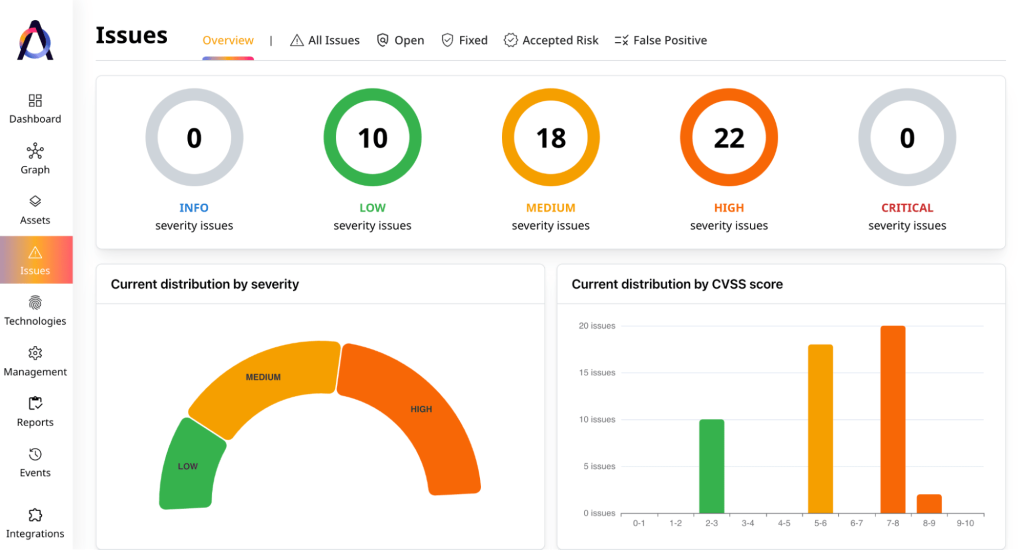
Acunetix has five different predefined severity levels – Critical, High, Medium, Low, and Info – and each vulnerability gets assigned one of these five depending on its CVSS score.
In addition to that, Acunetix offers a bunch of filters that can be applied to the list of vulnerabilities – first seen, last seen, vulnerability type, business criticality, status, etc.
Using this functionality, users can narrow down all the security issues discovered in their attack surface to a relatively small group.
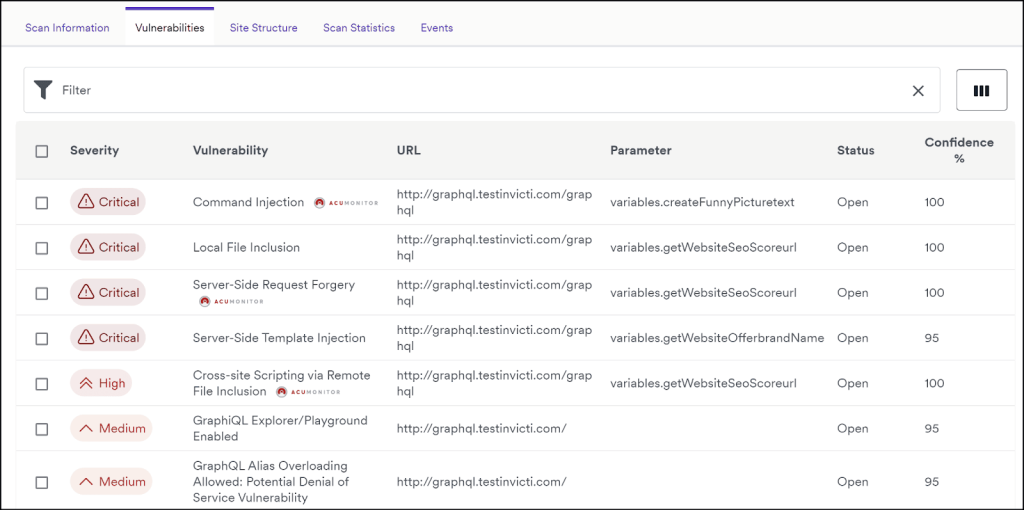
Acunetix has a long list of integrations with project management and bug tracking tools such as Jira, Redmine, FogBugz, ServiceNow and some others. Using these integrations, you can export vulnerability information as bug reports to those bug trackers.
Vulnerability Prioritization and Remediation with Attaxion
Attaxion offers a very similar functionality, but with some additional data that can help with prioritization. It also has severity and CVSS score as main prioritization criteria, as well as the option to filter by vulnerability type, asset, status, and more.
However, it adds data from two more sources that might matter even more than CVSS. Firstly, for each CWE there is data from the CISA KEV catalog about whether a vulnerability is known to be actively exploited in the wild – or not.
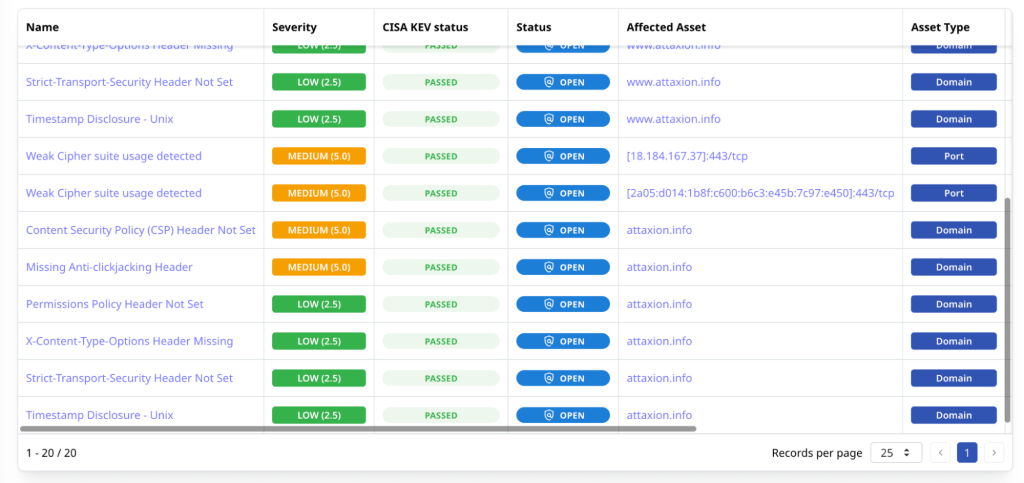
Secondly, for CVEs Attaxion also offers another score – EPSS, that relies on AI and different parameters of the vulnerability to calculate the chance of its exploitability. Finally, Attaxion pulls data from the EUVD database as well – for redundancy and to ensure better context.
Adding EPSS and KEV to CVSS allows organizations to introduce risk-based vulnerability management that is more modern and effective than the traditional severity-based approach. It allows you to find really critical vulnerabilities – not only from the severity perspective, but also from the perspective of the exploitation likelihood.
Attaxion has a native integration with Atlassian Jira, allowing users to create support tickets in one click, speeding up remediation efforts.
How They Compare
Acunetix offers relatively basic functions for prioritizing vulnerabilities, mostly letting cybersecurity teams rely on their own judgment and applying the right filters. On the brighter side, it has a wide selection of integrations with various project management tools and bug trackers for remediation purposes.
Attaxion goes two steps further than Acunetix in prioritization, adding EPSS and CISA KEV data to help prioritize issues more effectively. It’s only integrated with Jira, but the team behind Attaxion is open to developing new integrations if the customers need them.
 PART 5
PART 5
Continuous Monitoring
Continuous Monitoring with Acunetix
As we’ve said before, Acunetix is very flexible when it comes to scan scheduling and allows you to set the frequency for scans (daily, weekly, or something else), their maximum duration, and more.
It has a special status for vulnerabilities that were supposed to be remediated, but were rediscovered.
Acunetix also allows you to send notifications about vulnerabilities and other events and generate reports for different purposes.
When it comes to email notifications, Acunetix also shows quite some flexibility. It allows you to set up notifications for specific events like running a new scan or discovering outdated technology. It also allows you to specify websites or groups of websites you want to receive these particular notifications for and send them to specific user groups.
In addition to that, Acunetix can send SMS notifications. You can also integrate it with Slack.
Reporting is another strong side of Acunetix by Invicti. It offers several different types of reports for regulatory compliance purposes or just to understand your organization’s security posture. You can choose to generate reports manually or automatically.
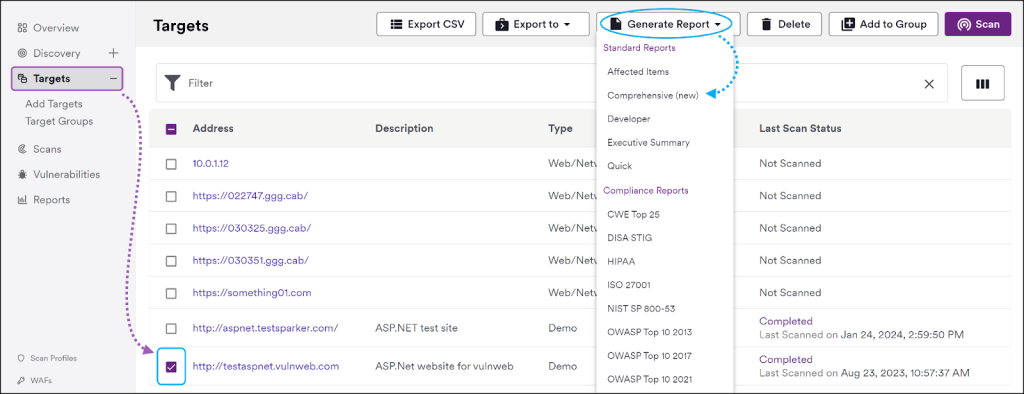
Continuous Monitoring with Attaxion
Attaxion’s stronger side when it comes to continuous monitoring is that it’s really continuous – the scans are not daily, but almost real-time. That means that you can get notifications about new vulnerabilities faster.
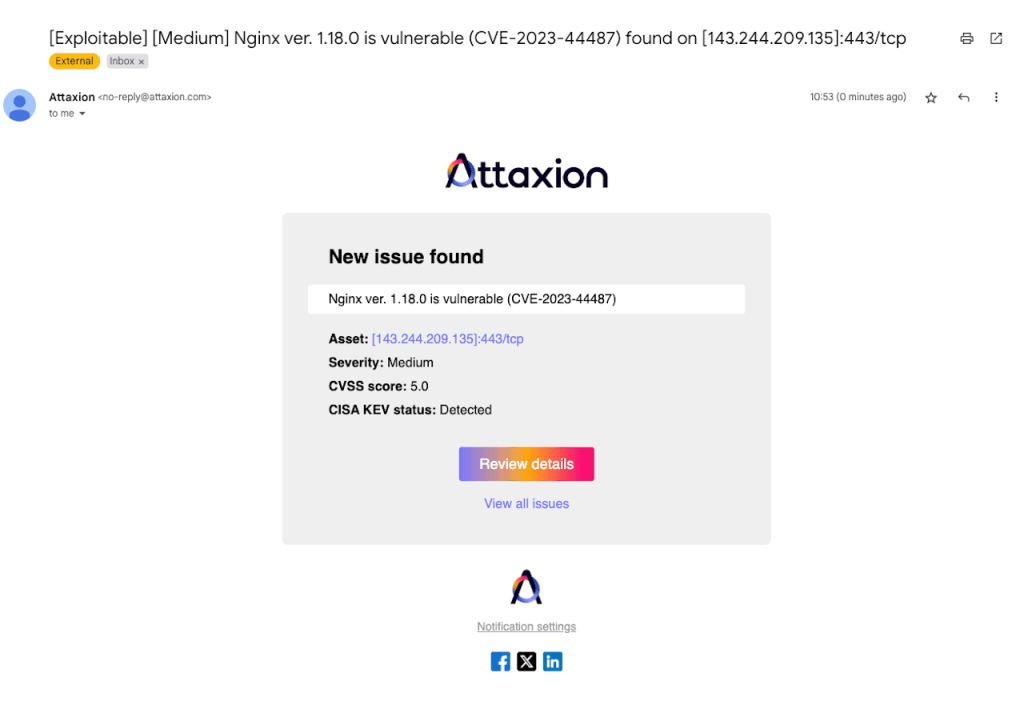
For notifications, Attaxion offers two main options – email and Slack. Both can be tweaked (independently) so that you only get notifications about issues starting from a certain severity level.
You can also export reports from Attaxion, be it for the assets in your external attack surface, for issues, or for technologies that it has detected in your tech stack. On top of that, Attaxion offers a REST API that allows you to connect Attaxion to other apps in your cybersecurity stack and get virtually any data from it into any workflow you want to build.
How They Compare
Acunetix has a strong focus on notifications and reports, outperforming most tools we’ve ever tested in this aspect. The only limitation that it has is that – like most other tools – it runs scans only daily or even less frequently.
Attaxion doesn’t have this drawback, offering continuous scans. On the other hand, it doesn’t have this broad functionality when it comes to notifications and reporting.
 PART 6
PART 6
Conclusion
Acunetix by Invicti is widely known in the industry for offering a unique combination that includes reasonable price, broad set of integrations, and great notifications and reporting capabilities. It is a great solution if your objective is automated pentesting of a specific website or several.
However, Attaxion makes for a stronger alternative to Acunetix if you’re interested in covering your entire attack surface. It offers a much broader asset coverage and an effective yet less intrusive vulnerability scanner at a lower price. Attaxion also provides more data for vulnerability prioritization.
Acunetix is effective at finding vulnerabilities, but Attaxion is a more versatile security platform that goes one step further, being effective at finding potentially vulnerable assets that belong to your organization and that you might not have even been aware of. If the objective is to continuously protect an organization from external threats, Attaxion is a better fit for that, making it one of the best Acunetix alternatives for the task.
Ready to try Attaxion? Start a 30-day free trial, or request a personal demo.