External Attack Surface Management (EASM) platforms and attackers employ similar reconnaissance techniques for scanning an organization’s external infrastructure. These techniques reveal attack vectors and paths that adversaries can use to infiltrate an organization’s network.
Since the Mitre ATT&CK framework is based on real-world observations and modeling of the attacker’s behavior, using EASM tools at some of its stages makes perfect sense.
This blog post explores the possibilities of integrating EASM tools into the Mitre ATT&CK framework.
How to Use EASM Tools and the Mitre ATT&CK Matrix for Enterprise Together
Mitre ATT&CK framework offers several matrices of different tactics and techniques for different situations. The ATT&CK matrix for Enterprise is, perhaps, the most widely known and used one.
An EASM platform enables security professionals to apply the Mitre ATT&CK Enterprise matrix effectively, helping discover and emulate many potential attack vectors. Mainly, EASM tools can help with the first two Enterprise ATT&CK tactics: Reconnaissance and Initial Access.
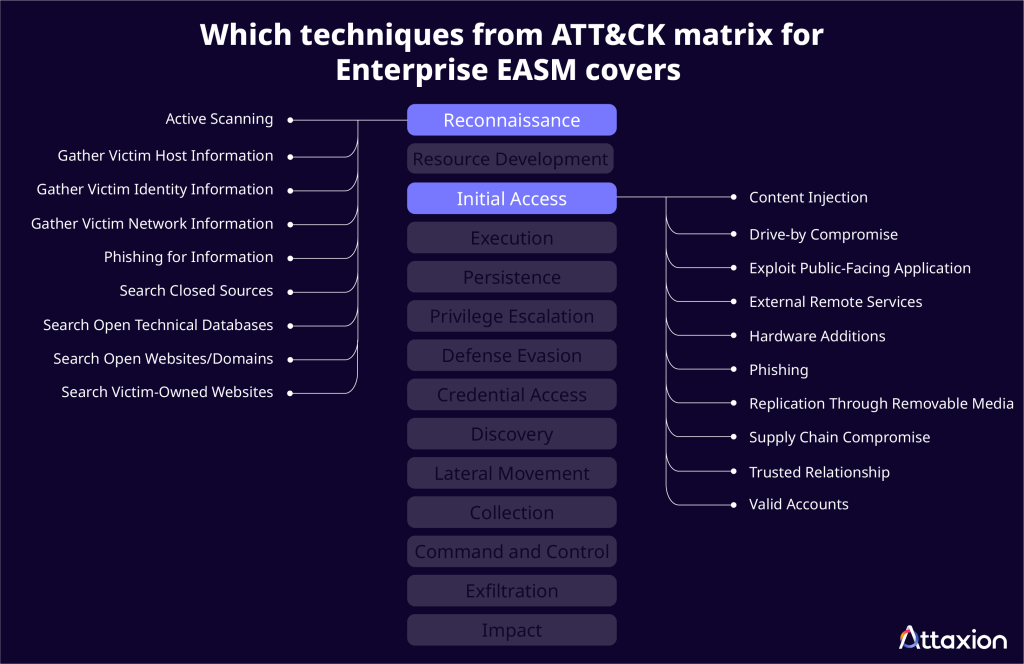
Using EASM for the Reconnaissance Stage
First of all, by using external attack surface management tools, cybersecurity teams can gather information about the organization’s infrastructure from the adversary’s point of view.
Unlike most other security tools that are installed on the infrastructure and look at it from inside and out, EASM tools use an outside-in approach – similar to that of a potential attacker.
These tools offer various techniques including:
- port scanning,
- web application scanning,
- digital footprint analysis,
- asset enumeration, and more.
Through port scanning, EASM identifies open ports that attackers could potentially use.
Meanwhile, web application scanning detects software vulnerabilities and misconfigurations adversaries might exploit for unauthorized access or denial-of-service attacks.
Enumeration maps out domains and subdomains associated with the target organization. Adversaries can try taking over subdomains and then leveraging that to gain further access into the organization’s network.
In combination these techniques provide a clearer scope of the attack surface.
As you can see, EASM capabilities match plenty of reconnaissance techniques listed in Mitre ATT&CK for Enterprise:
- Active scanning (scanning IP blocks, vulnerability scanning, wordlist scanning),
- Gathering information about the victim host (about software and client configurations)
- Gathering victim network information
- Search open websites and domains
- Search victim-owned websites.
It enables organizations to disrupt an attacker’s planning phase. Thus, it helps prevent further stages of an attack from materializing.
Using EASM Tools for the Initial Access Stage
EASM tools are also instrumental at the initial access stage. They identify vulnerabilities that could become entry points for attackers into the infrastructure. EASM discovers improperly configured web servers and unsecured ports. Additionally, it identifies services that are unnecessarily exposed to the internet.
These capabilities correlate with the Exploit Public-Facing Application technique from Mitre ATT&CK Enterprise matrix.
Overall, using an EASM platform, cybersecurity teams can partially automate the first two tactics from the Mitre ATT&CK Matrix for Enterprise. It makes implementing the ATT&CK framework easier.
EASM Tools and the Mitre ATT&CK Matrix for Cloud
Mitre ATT&CK framework has special matrices developed specifically for the external attack surface. They include the Cloud Matrix as well as matrices for Office 365, Azure AD, Google Workspace, SaaS, IaaS.
These matrices follow a similar principle, but are designed for the assets you are aware of. However, the reality of cloud infrastructure often presents a different scenario. In modern companies, cybersecurity specialists rarely know about all the SaaS services, subdomains, open ports, and other external assets within their network.
This is where EASM tools like Attaxion can provide the missing information. EASM helps map all external assets within an organization’s infrastructure and identify vulnerabilities in these assets.
The cybersecurity team can apply the tactics and techniques from the Mitre ATT&CK Matrix for Cloud to this external assets map. It will help to further anticipate and mitigate adversary actions.
For instance, EASM tools can identify vulnerabilities in a public-facing application within the network. Cybersecurity teams can then trace connections among the assets to evaluate potential risks, such as by examining asset-to-asset dependencies.
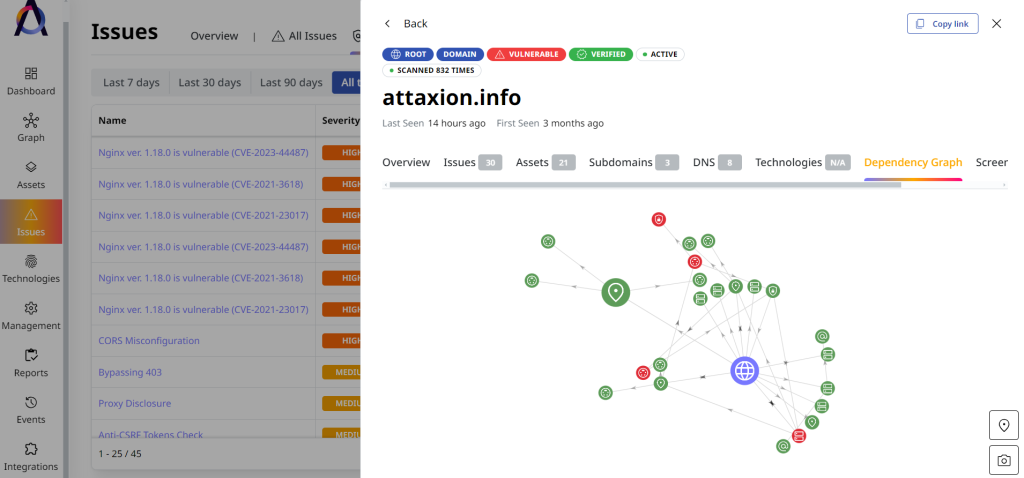
They may check other Mitre ATT&CK techniques that adversaries could use on their network before or after an incident and, of course, illuminate these potential entry points for attackers.
Armed with this information, cybersecurity teams can implement a vulnerability risk management approach. This allows them to efficiently protect the organization, even with limited resources. This proactive approach is crucial for maintaining robust security in dynamic cloud environments.
Conclusion
New vulnerabilities and cyber threats appear continuously. Mitre ATT&CK framework allows organizations to address them efficiently by adopting an adversary mindset.
Using an EASM platform can simplify applying the ATT&CK framework, helping automate emulating some of the techniques from the ATT&CK matrices.
Find out how Attaxion can bring your EASM activities to a higher level with superior asset coverage and deep context. Schedule a customized demo.

