The overwhelming number of vulnerabilities organizations face—and attackers can exploit—makes it impractical and even impossible to address all of them at once. An effective approach to vulnerability management requires some level of prioritization, which is traditionally represented by the Common Vulnerability Scoring System (CVSS)—a standard for assessing the severity of security vulnerabilities based on their technical characteristics.
However, the Forum of Incident Response and Security Teams (FIRST), the organization maintaining several vulnerability scoring protocols including CVSS, introduced a new vulnerability scoring system called the Exploit Prediction Scoring System (EPSS) in 2021. The goal was to help network defenders prioritize vulnerabilities more efficiently.
This article explores the differences between CVSS and EPSS, their pros and cons, and which system is best for vulnerability prioritization.
Table of Contents
- CVSS: Prioritizing by Severity
- Factors Affecting the CVSS Score
- EPSS: Prioritizing by Likelihood of Exploitation
- Factors That Influence EPSS Scores
- CVSS vs. EPSS: Detailed Comparison
- CVSS vs EPSS: Which One Should You Use?
- How Attaxion Can Help
CVSS: Prioritizing by Severity
CVSS is a quantitative measure of a vulnerability’s technical severity, which is based on two key factors: the consequences of vulnerability exploitation and the ease with which attackers can carry it out. CVSS assigns vulnerabilities a numerical score ranging from 0 to 10, with 10 being the most severe. This score can be translated into a qualitative representation—low, medium, high, and critical.
| CVSS Score | Rating |
| 0 | Info |
| 0.1-3.9 | Low |
| 4.0-6.9 | Medium |
| 7.0-8.9 | High |
| 9.0-10 | Critical |
Vulnerabilities that lead to arbitrary code execution are often assigned the highest severity rating because attackers can run malicious code on the target system, potentially leading to full control of that system.
The first version of CVSS was created in 2005 by FIRST and the National Infrastructure Advisory Council (NIAC), although FIRST has taken on the role of custodian and maintains the official CVSS standard and its associated documentation. Since then, CVSS has evolved to address limitations and improve its accuracy. Below are the released versions:
- CVSS v2.0: This version was launched in 2007 and was widely adopted by vulnerability scanning tools and other solutions. However, it faced criticism primarily for its ambiguous guidelines that often led to inconsistent and inaccurate vulnerability assessments across different organizations.
- CVSS v3.0 and v3.1: CVSS v2.0 was overhauled in 2012, and work on CVSS v3.0 began, but it wasn’t until 2015 that the newer version was officially released. This version introduced several improvements, such as enhanced granularity for metrics, a clearer definition of “scope,” and better consideration of attacker privileges and user interaction. In mid-2019, v3.1 was released to provide a more detailed scoring guidance without any changes to the metrics or formula. CVSS v3.x is still widely adopted across many organizations.
- CVSS v4.0: The latest iteration was released in November 2023 in response to the growing complexity of modern systems and attack techniques. This version has new metrics and terminologies aimed at enhancing accuracy. It also made existing metrics more granular, improved user interaction classification, and expanded its scope to consider impacts on subsequent systems.
Factors Affecting the CVSS Score
CVSS v4.0 introduced a refined scoring system with four key metric groups that influence vulnerability assessments. The table below lists these groups and the metrics that belong to each of them.
Each published vulnerability that belongs to the Common Vulnerabilities and Exposures (CVE) database has a CVSS score. However, even for vulnerabilities without a CVE identifier, it’s possible to calculate their CVSS scores. To do so, users can use calculators like those created by the National Institute of Standards and Technology (NIST) and FIRST.
Despite being exhaustive in terms of the metrics its latest version considers, CVSS does not cover all security issues, since it only applies to publicly disclosed software vulnerabilities. Many issues—such as misconfigurations, zero-day vulnerabilities, and human-related security flaws—fall outside its scope. That pushes vulnerability management solutions to develop their own severity scoring systems or augment CVSS with additional factors to enable more efficient vulnerability prioritization.
EPSS: Prioritizing by Likelihood of Exploitation
EPSS is a predictive scoring system designed to estimate the probability that a vulnerability will be exploited within the next 30 days. Unlike traditional severity-based scoring systems, EPSS focuses on real-world exploitability, helping organizations prioritize vulnerabilities based on actual risk, rather than theoretical impact.
EPSS was created by a group of cybersecurity experts at FIRST in 2020 and was publicly released in January 2021. It has since undergone multiple updates, with major revisions in February 2022 (version 2), March 2023 (version 3), and March 2025 (version 4). FIRST continues to maintain and improve EPSS, ensuring it remains a valuable tool for vulnerability management.
It’s worth noting that EPSS applies only to vulnerabilities with a CVE identifier, meaning that, like CVSS, it also does not cover security misconfigurations and other security issues that have not been publicly disclosed. You can manually calculate CVSS for non-disclosed issues if you know enough about them, but it’s impossible to get EPSS scores for them. EPSS is also more valuable in assessing vulnerabilities without evidence of active exploitation, as confirmed active exploitation (i.e., the presence of the vulnerability in the CISA Known Exploited Vulnerabilities (KEV) catalog) always takes precedence over EPSS scores.
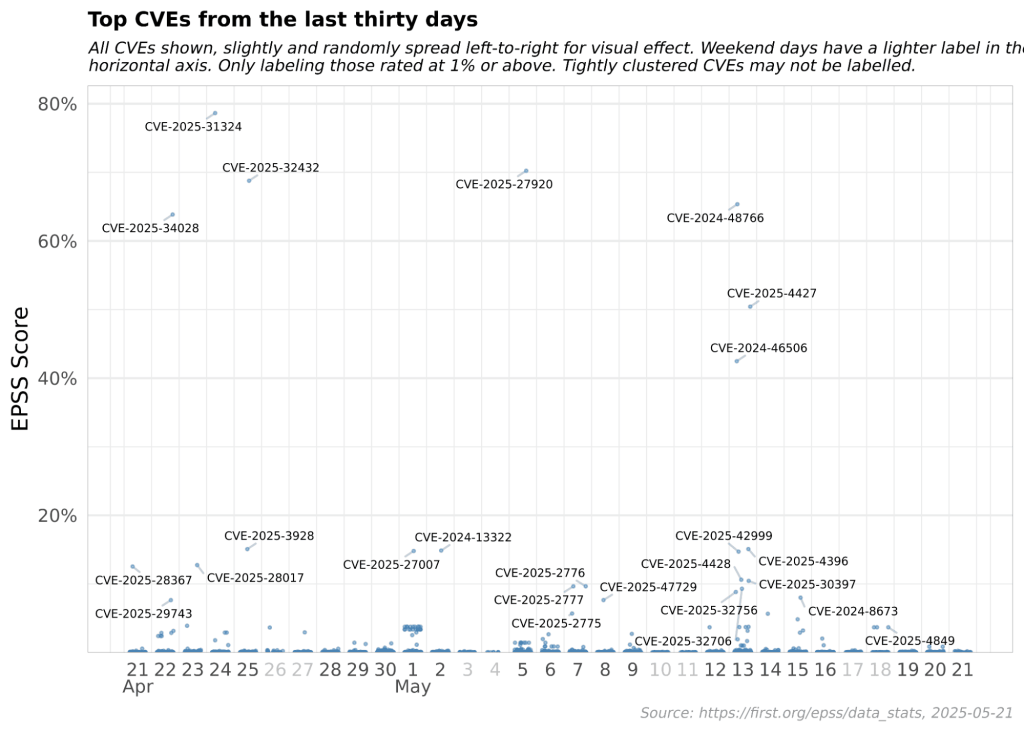
Another characteristic of EPSS is that it is dynamic. It is continuously updated based on new exploit data and emerging threats, and scores are refreshed daily so that organizations have the most up-to-date risk assessments. Here are the EPSS scores of the top CVEs from the last 30 days as of May 21, 2025, as published by FIRST:
Factors That Influence EPSS Scores
The EPSS model collects two types of data on a daily basis—vulnerability information and exploitation activity. These include the following data points:
- Vendor: The product and product provider affected by the vulnerability using the Common Platform Enumeration (CPE), obtained from the National Vulnerability Database (NVD).
- Age of the vulnerability: Number of days since the CVE was published in the MITRE CVE list.
- References: The MITRE CVE List and NVD provide various references with categorical labels (e.g., advisories, malware, exploit, patch).
- Normalized multiword expressions: This data is extracted from the description of the vulnerability in the MITRE CVE List.
- Common Weakness Enumeration (CWE): EPSS obtains the underlying security issue associated with the vulnerability from NVD.
- CVSS metrics: EPSS incorporates CVSS 3.x base vector metrics from NVD.
- The CVE’s presence on prominent security lists: EPSS identifies whether a CVE is listed or discussed on the CISA KEV catalog, Google Project Zero advisories, or Trend Micro’s Zero Day Initiative (ZDI), as these often indicate active exploitation or high researcher interest.
- Publicly available exploit code: The model checks platforms like Exploit-DB, GitHub, and Metasploit for any exploit code related to the vulnerability.
- Offensive security tools and scanners: EPSS considers whether the vulnerability is integrated into popular offensive security tools and scanners like Intrigue, sn1per, jaeles, and nuclei.
The inclusion of exploitability data encourages security teams to look beyond a vulnerability’s technical impact (expressed as a severity rating) since it’s more strategic to prioritize vulnerabilities with a higher chance of exploitation, even though they might have lower severity ratings.
CVSS vs. EPSS: Detailed Comparison
Let’s compare CVSS and EPSS side by side to get a clearer picture.
| CVSS | EPSS | |
| What it measures | Vulnerability severity | Likelihood of exploitation |
| Intended use | Understand the potential impact of vulnerability exploitation | Estimate the real-world risk of vulnerability exploitation |
| Score range | 0-10 | 0-100% |
| Created by | FIRST CVSS division | FIRST EPSS division |
| Created in | 2005 | 2021 |
| Scores calculated | Manually, with a calculator | By a machine learning (ML) algorithm, probability-based |
| Scoring | Decentralized: CVE Numbering Authorities (CNAs) like NVD, EUVD, and vendors | Centralized: ML algorithm developed by First.org |
| Last updated in | 2023 (CVSS v4.0) | 2025 (EPSS v4) |
| Static/dynamic | Base score remains static, but Threat metrics and Environmental metrics are dynamic | Dynamic, calculated daily |
| Predictive | No, it can’t predict future exploits | Yes, it’s predictive |
| Pros | Standardized and universalComprehensive technical details of vulnerabilitiesServes as a foundation for risk assessment | Prioritizes vulnerabilities based on real-world riskDynamic and up-to-dateAbility to predict the likelihood of exploitation |
| Cons | Lacks real-world exploitability contextNeeds to be manually calculated for non-CVE vulnerabilitiesCan overwhelm security teams that focus remediation efforts on high-risk vulnerabilities | Limited to CVEsRequires continuous updates because scores change dailyDoes not measure the impact of an exploitation |
CVSS vs EPSS: Which One Should You Use?
Security teams had been using CVSS as the primary tool for vulnerability assessment for almost two decades. However, its limitations in taking into account real-world threats led to the development of EPSS to address the main missing piece in CVSS ratings: the likelihood of a vulnerability actually being exploited.
However, EPSS alone doesn’t provide a complete picture either, as it doesn’t fully account for the severity of the impact to an organization in case a vulnerability is exploited. While it considers the CVSS Base score, it doesn’t include other CVSS metrics that are more organization-specific.
Therefore, the optimal approach for effective vulnerability prioritization is to integrate both CVSS and EPSS scores, with the highest priority ideally assigned to vulnerabilities that exhibit both a high CVSS score (indicating a severe potential impact) and a high EPSS score (indicating a high probability of exploitation).
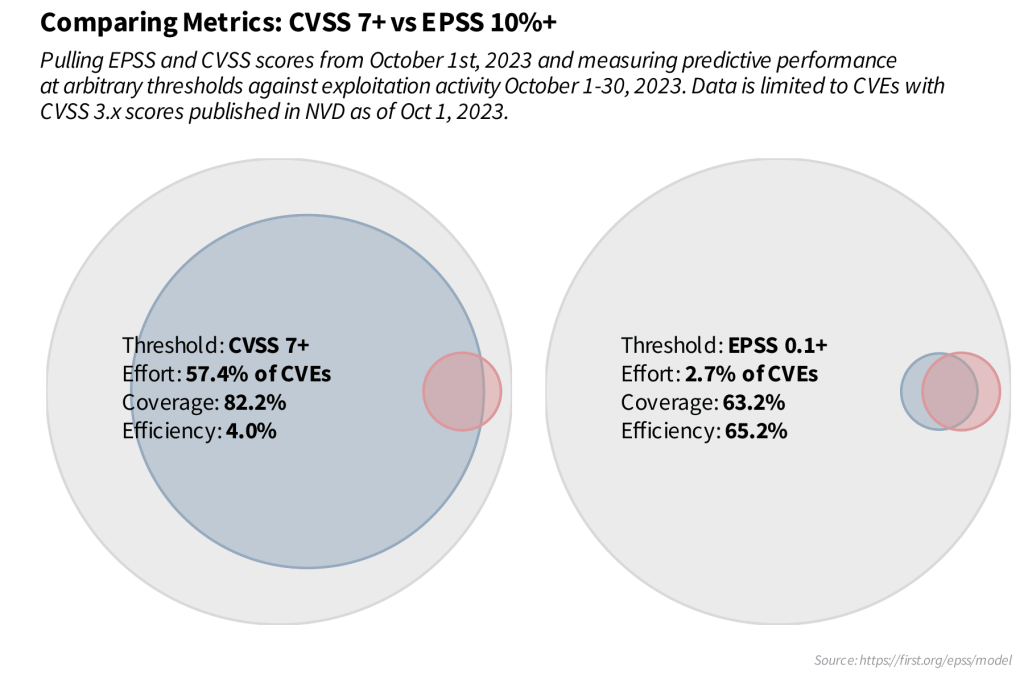
Beyond these scores, it’s also important to incorporate other threat intelligence sources, such as the CISA KEV catalog. After all, a vulnerability confirmed to be exploited in the wild warrants immediate attention regardless of its CVSS or EPSS score.
How Attaxion Can Help
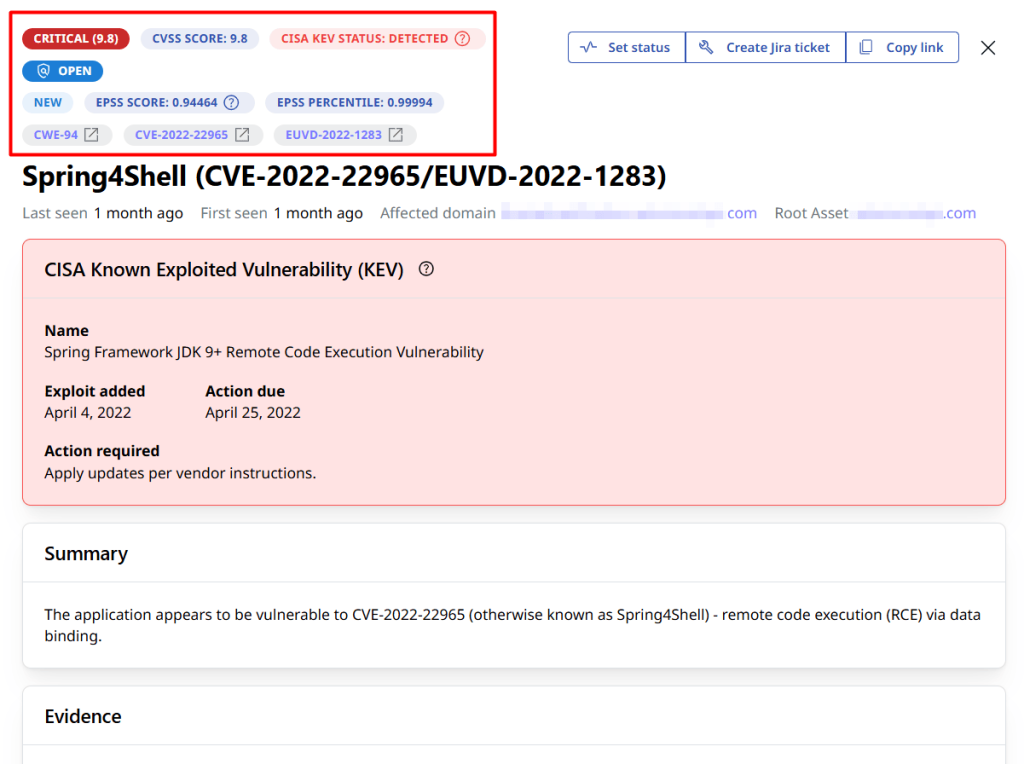
Attaxion is an agentless Exposure Management platform that offers all the metrics you need for vulnerability prioritization: CVSS, EPSS, and CISA KEV.
Attaxion also discovers all your external-facing assets automatically, providing visibility into previously unknown and vulnerable assets and allowing you to determine the business criticality of each vulnerable asset.
These combined data points—prioritization metrics and a complete asset catalog—serve as a strong foundation for a well-informed risk-based vulnerability management.
Ready to see how Attaxion can help you prioritize vulnerabilities using CVSS, EPSS, and CISA KEV? Schedule a demo now.

