Best Detectify Alternative: Attaxion
Quick Summary
| Feature | Attaxion | Detectify |
| Pricing | Starting from $1,290/year for 40 assets | Starting from ~$4,130/year for 25 assets |
| Dependency graphs for digital assets | ✅ | ❌ |
| Non-intrusive vulnerability scanning | ✅ | ❌ |
| Intelligent vulnerability prioritization with EPSS and CISA KEV | ✅ | ❌ |
Introducing Detectify and Attaxion
Detectify is a cybersecurity firm that offers three main products — an external attack surface management (EASM) platform called Surface Monitoring, a dynamic application security testing (DAST) suite called Application Scanning, and API Scanning. The first focuses on asset discovery, vulnerability scanning, prioritization, and remediation, while the second provides deeper scans for assets identified as web applications. API Scanning is self-explanatory.
At Attaxion, we consider Detectify one of our main competitors. Attaxion is a Detectify alternative – it’s also a SaaS cybersecurity platform that covers the entire EASM process, but it provides more diverse reconnaissance techniques (and a higher asset coverage as a result), more advanced prioritization, and the unique ability to monitor network traffic without deploying any agents.
Both tools help security professionals stay ahead of the attackers and protect their organization’s external attack surface. They have a lot in common, but there are some differences that set them apart. Here, we discuss how the two platforms compare and which one you should choose.
 PART 1
PART 1
Pricing
For bigger enterprises, both Detectify and Attaxion provide pricing on demand based on your specific needs and the number of assets that you have. However, both also offer plans that you can purchase without talking to sales, using just a credit card. Detectify has one such plan, while Attaxion offers three different plans on its pricing page.
| Detectify vs Attaxion: Pricing | ||
| Attaxion | Detectify Surface Monitoring | |
| Monthly pricing | from USD $129/month | from USD ~$465/month (405 EUR/month) |
| Yearly pricing | from USD $1,290 | from USD ~$4,130 (3,624 EUR) |
| Assets covered | 40 (domains, subdomains, and IP addresses) | 25 (domains and subdomains) |
| Free trial | ✅ (30 days) | ✅ (14 days) |
Detectify provides pricing in euros, while Attaxion is priced in US dollars. To compare, in the table above, we show the pricing in USD for both platforms (with the conversion rate for 10.09.2025).
Both Attaxion and Detectify are on the more accessible side of the spectrum when it comes to EASM platforms pricing and other Detectify competitors. Other EASM tools like Censys ASM or Cycognito would cost you much more.
When billed annually, Detectify’s Surface Monitoring ($~4,130/year) is more than three times more expensive than Attaxion’s Starter plan ($1,290/year). When billed monthly, the same plan for Detectify starts to become even more expensive (~$465 vs $129/month for Attaxion’s Starter plan). That makes Attaxion a more affordable Detectify alternative.
For this price, Detectify’s Surface Monitroing supports discovery, vulnerability prioritization, remediation, and continuous monitoring of up to 25 assets. When we say “assets,” in Detectify’s case it means domains and subdomains.
Attaxion’s most basic plan offers a higher number of covered assets – up to 40. But Attaxion doesn’t only count subdomains — IP addresses also contribute to the billable asset count. So, it’s worth noting that this number would deplete faster, but again, Attaxion is more than three times more affordable.
Both platforms offer a free trial: Detectify gives you 14 days, Attaxion offers 30.
Attaxion runs web application scanning by default if it discovers a web app, but Detectify wants you to buy Application Scanning (starting at ~$102 or EUR 90 per month) to do deeper scans.
Overall, Attaxion is a cheaper Detectify alternative, no matter whether you choose to go with a monthly or yearly plan. However, both tools are relatively inexpensive when it comes to the typical cost of advanced security software.
 PART 2
PART 2
Asset Coverage
Like every platform that supports EASM, the first thing both Detectify and Attaxion do is discovering the organization’s assets – known, unknown, and forgotten. For the user, the process looks more or less the same in both cases.
First, you need to manually add root assets, which are domain names that your company owns. Detectify offers to do this in a variety of ways: manually, by using a Connector to a cloud service, by adding a zonefile, or performing a DNS transfer.
With Attaxion, you can also use cloud server connectors to pull asset lists from services like AWS, GCP, Microsoft Azure, or DigitalOcean. You can also manually add TXT DNS records to the domains you control to verify them or add a text file to the root catalog. Finally, Attaxion can automatically verify the domain that you had in your email which you used to create an account to speed things up.
After that, the EASM platforms perform cyber reconnaissance and find other assets linked to the root assets.
Attaxion offers more than 11 different methods of asset discovery, including WHOIS and DNS lookups, cloud platform scans, brute forcing, web crawling, and more. It’s capable of finding a very diverse spectrum of assets – not only domains, subdomains, and IP addresses, but also CIDRs (Classless Inter-Domain Routing), exposed email addresses, SSL certificates, and more. Of course, it also performs port scanning.
In comparison, Detectify offers 5 methods for automatic asset discovery – scraping, brute-forcing (recently updated with an improved wordlist), DNS zone transfer, SSL monitoring, and application scanning (essentially, fuzzing). In addition to that, subdomains can be added manually – either by direct import, or through integrations with Cloudflare and AWS Route53, or through Google Analytics. The types of assets that Detectify can discover are subdomains, IP addresses, and cloud instances.
| Detectify vs Attaxion: Asset Coverage | ||
| Attaxion | Detectify | |
| Types of assets discovered | Domains Subdomains IP addresses Organizations Email addresses Clouds CIDRs SSL Certificates | Domains Subdomains IP addresses Clouds |
| Ports Discovery | ✅ | ✅ |
| Asset coverage | Highest | High |
| Reconnaissance techniques | 11+ automatic methods | 5 automatic methods |
| Dependency graph | ✅ | ✅ |
When used on the same infrastructure, Attaxion usually discovers many more internet-facing assets than Detectify. Even when it comes to assets of the same type, Attaxion is usually ahead thanks to the advanced cyber recon methods it uses for asset discovery.
One other point which makes Attaxion stand out is it builds a graph of your entire attack surface, showing you how your assets are interconnected, also highlighting vulnerable assets on the graph.
Both Detectify and Attaxion can build dependency graphs for individual assets that show how a certain asset was discovered. These graphs help with understanding of potential attack paths.
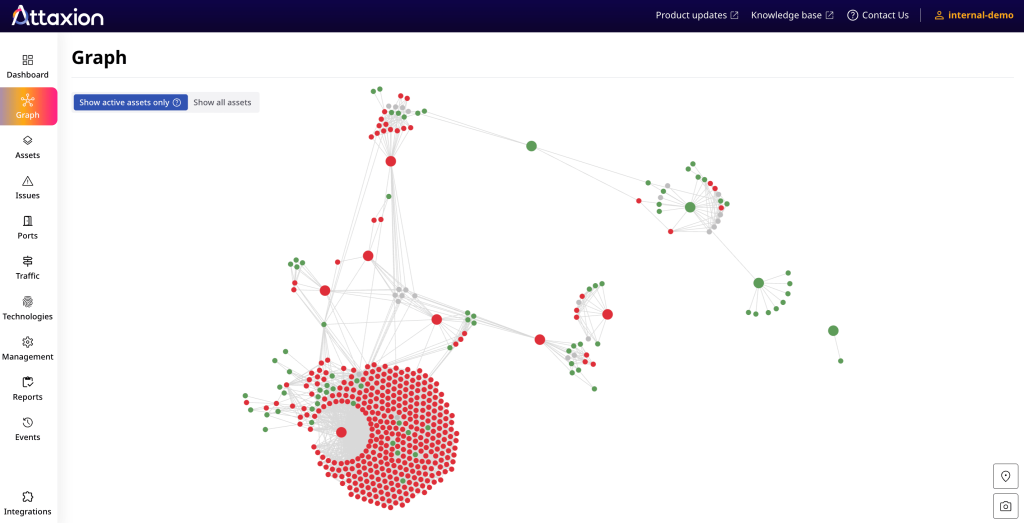
Overall, Attaxion has a broader asset coverage than Detectify, offering to find more different types of assets and using advanced cyber reconnaissance techniques to discover more assets than Detectify.
 PART 3
PART 3
Vulnerability Detection and Prioritization
One of EASM’s main functions is analyzing all detected assets for security weaknesses and offering to prioritize them. Of course, both Detectify and Attaxion offer that functionality – and provide a rather similar approach to it.
Both platforms use proprietary vulnerability scanners to compose a list of vulnerabilities in the organization’s assets that can be sorted by severity (CVSS), asset, date first seen, date last seen, etc. Both platforms offer some additional information on each vulnerability, such as some details about it, remediation suggestions, and more. Both allow you to add tags for vulnerabilities to create taxonomies and both offer to mark security issues as fixed, accepted risk, or false positives to manage them more effectively.
Both Attaxion and Detectify also offer a list of technologies and SaaS tools that the EASM scans discovered on the organization’s assets.
| Detectify vs Attaxion: Vulnerability Detection and Prioritization | ||
| Attaxion | Detectify | |
| Tags | ✅ | ✅ |
| Proprietary vulnerability research | ❌ | ✅ (hacker community) |
| Advanced prioritization | ✅ (EPSS, CISA KEV catalog data) | ✅ |
| Marking as false positive / accepted risk | ✅ (plus proactive false positive filtering) | ✅ |
| Technology fingerprinting | ✅ | ✅ |
| Export reports | ✅ (CSV) | ❌ |
| Visual diagrams | ✅ | ❌ |
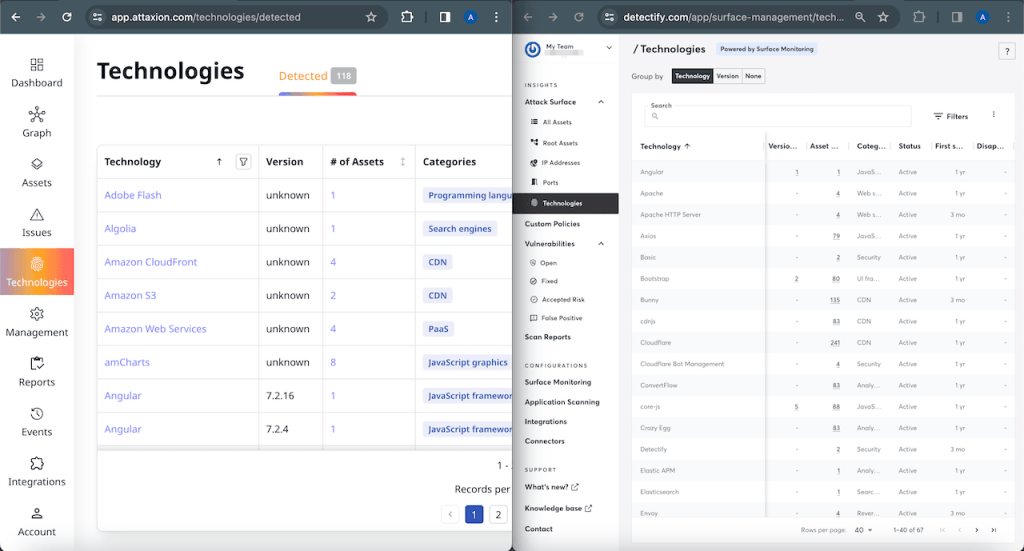
There are some noticeable differences though.
Unlike Attaxion, Detectify states that they are relying on an ethical hacker community to provide information on vulnerabilities even before they get added to CVE and CWE lists. That’s a useful feature, as earlier discovery and remediation of vulnerabilities helps lower the risk of cyber attacks. Detectify also uses payload-based vulnerability scanning, which means that it provides higher certainty that vulnerabilities really exists at the cost of vulnerability scanning being more intrusive. Attaxion doesn’t always use payload-based scanning, even though for some vulnerabilities (like SQL injection, for example), it runs validation using payloads.
Unlike Detectify, Attaxion provides more rich data for vulnerability prioritization. For every CVE, it pulls EPSS score as well as data from CISA KEV catalog. Attaxion also integrates with the European Vulnerability Database (EUVD) to provide rich vulnerability context.
In our experience, Attaxion was able to find more vulnerabilities than Detectify, despite not having a dedicated team of ethical hackers to source the vulnerabilities from. Detectify prides itself on low false positive count – and that seemed to be true during our tests, but the platform suffers from false negatives.
Attaxion provides a graphical presentation of the distribution of vulnerabilities by severity, as well as how it’s been changing during the latest period, which can help with reporting and getting a quick idea of the organization’s security status. In addition to that, Attaxion offers to export information on security vulnerabilities in a CSV report.
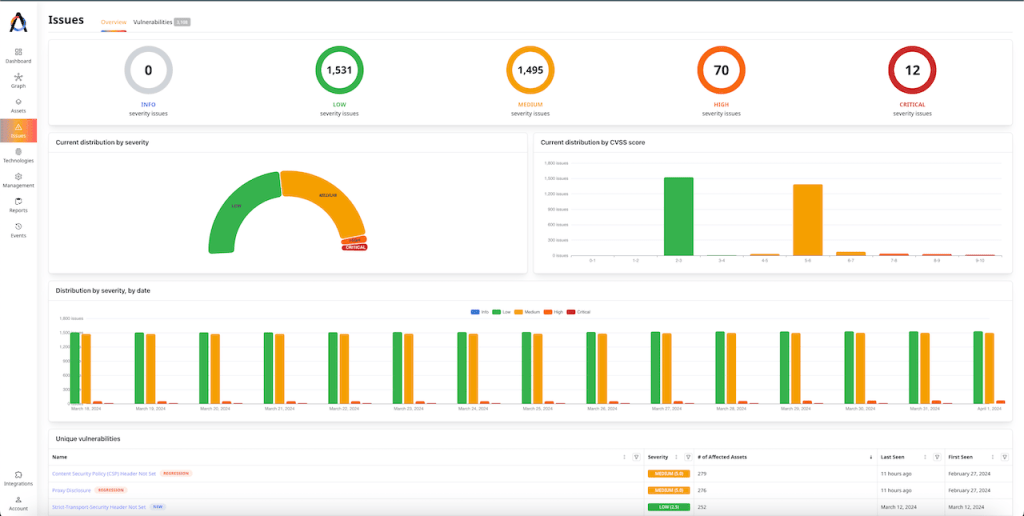
Overall, when it comes to vulnerability management, Detectify and Attaxion offer very similar functionality. Detectify has an advantage of being able to detect some vulnerabilities that were not assigned a CVE or CWE number, but Attaxion is better at visualizing the state of the attack surface, providing more data for prioritization, and offering to export reports to use them in other tools.
 PART 4
PART 4
Remediation
For each discovered vulnerability, Both Detectify and Attaxion provide remediation techniques. Here, the tools have more or less the same to offer for each vulnerability – a description, the list of vulnerable assets, and some remediation suggestions.
In some cases, both Detectify and Attaxion show exact code snippets where the vulnerability was found, thus speeding up remediation efforts.
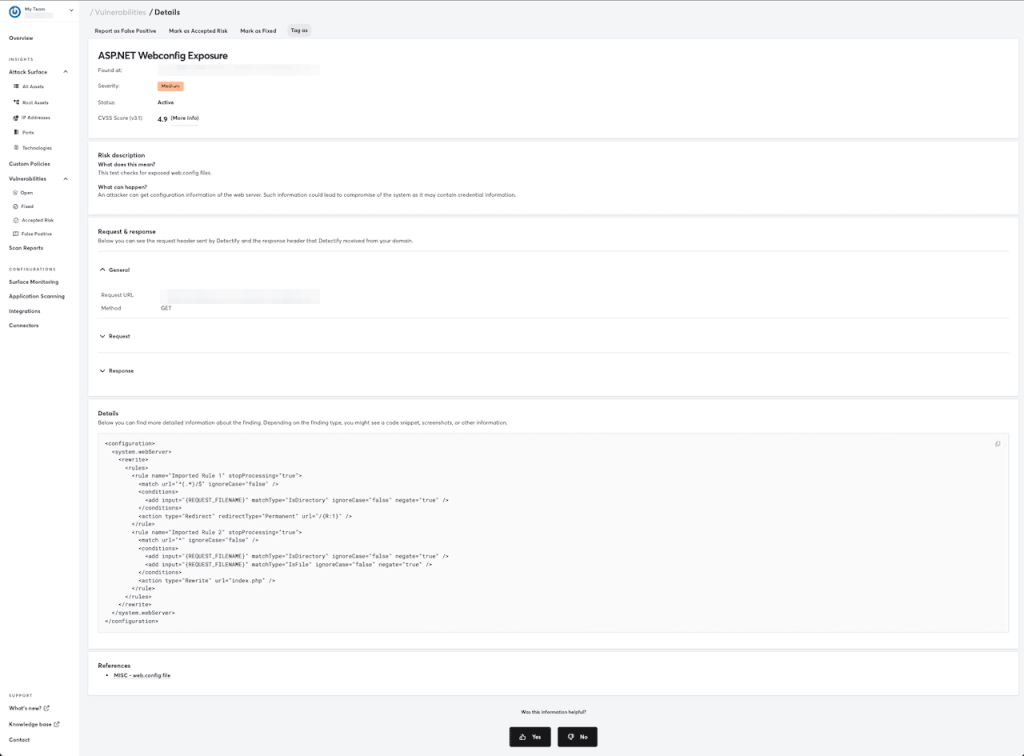
The key difference that Attaxion has is gathering information about the vulnerability and remediation techniques from multiple sources, which sometimes can make remediation suggestions more useful.
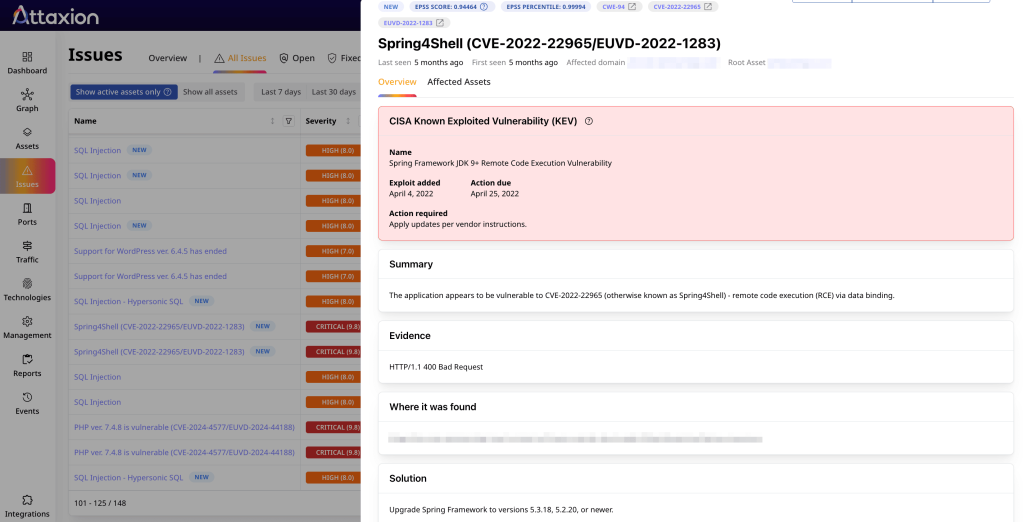
Both tools offer to create tickets in task management systems with all information for each vulnerability or send messages over corporate IM systems.
The difference here is in the supported integrations.
Attaxion offers two integrations with the most widely used tools – Jira and Slack. In one click, you can create a ticket in Jira with all relevant information about the vulnerability. Similarly, Attaxion offers to update you about newly discovered vulnerable assets via Slack.
Of course, you can also just copy a link to the page dedicated to a certain vulnerability and send it over to somebody, but to view it, they will also need to have access to Attaxion to open it. Fortunately, Attaxion offers unlimited user seats.
Detectify also offers integrations, but they are set up a bit differently. While Attaxion offers native integrations, Detectify uses a 3rd party service called Workato to set up integrations and workflows with other apps. Currently, it supports Slack, Jira, Trello, Microsoft Teams, Splunk, OpsGenie.
| Detectify vs Attaxion: Vulnerability Detection and Prioritization | ||
| Attaxion | Detectify | |
| Integrations | Native: – Slack, – Jira | Via 3rd party service (Workato): – Slack, – Jira, – Trello, – Microsoft Teams, – Splunk, – OpsGenie |
| Code snippets / screenshots | ❌ | ✅ |
| Multi-source threat intelligence | ✅ | ❌ |
Overall, both tools provide mostly similar options when it comes to vulnerability remediation and mitigation, offering additional information and creating tickets / sharing information about vulnerabilities. Detectify offers a broader list of integrations than Attaxion.
 PART 5
PART 5
Continuous Monitoring
There is a number of major differences between Detectify and Attaxion when it comes to continuous monitoring of the external attack surface.
Let’s start with what they have in common: both tools continuously scan the attack surface for new assets, technologies, and vulnerabilities, regularly updating the respective lists.
Now, to the differences. Attaxion has more different monitoring capabilities. One major difference is Attaxion’s Agentless Traffic Monitoring feature. Unlike Detectify, Attaxion can monitor traffic to and from IP addresses in your infrastructure and detect if any of them are talking to external IPs that are known to be malicious. This is a unique feature that doesn’t require any setup or agent installation – it relies on global NetFlow data and a variety of threat intelligence feeds to do this.
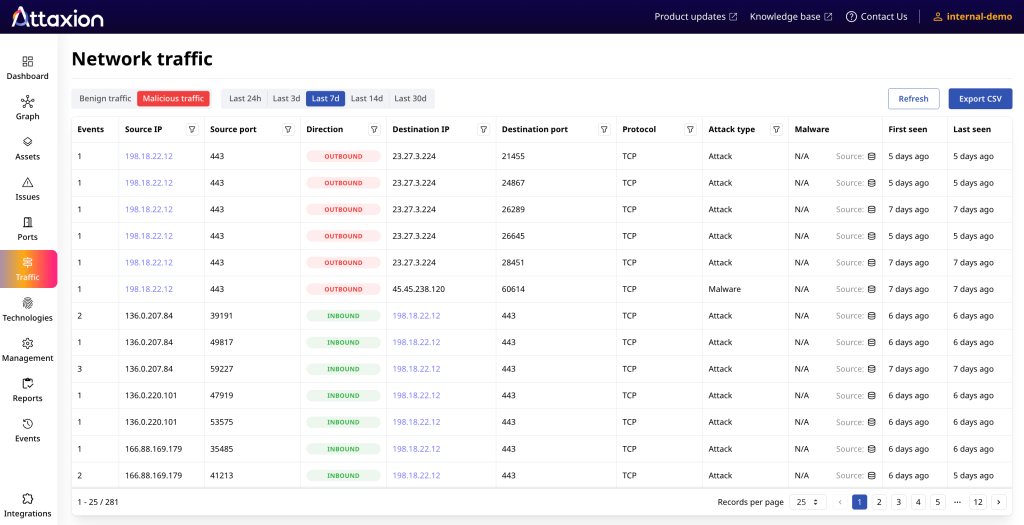
Attaxion also has another feature, called IoC Monitoring, which helps identify if any of your external infrastructure IPs are known to be associated with some malicious activity. Attaxion compares discovered IPs with indicators of compromise from connected threat intelligence feeds and highlights if there are any matches.
Finally, Attaxion supports brand monitoring — it gives you updates when typosquatting domains that mimic your brand are being registered.
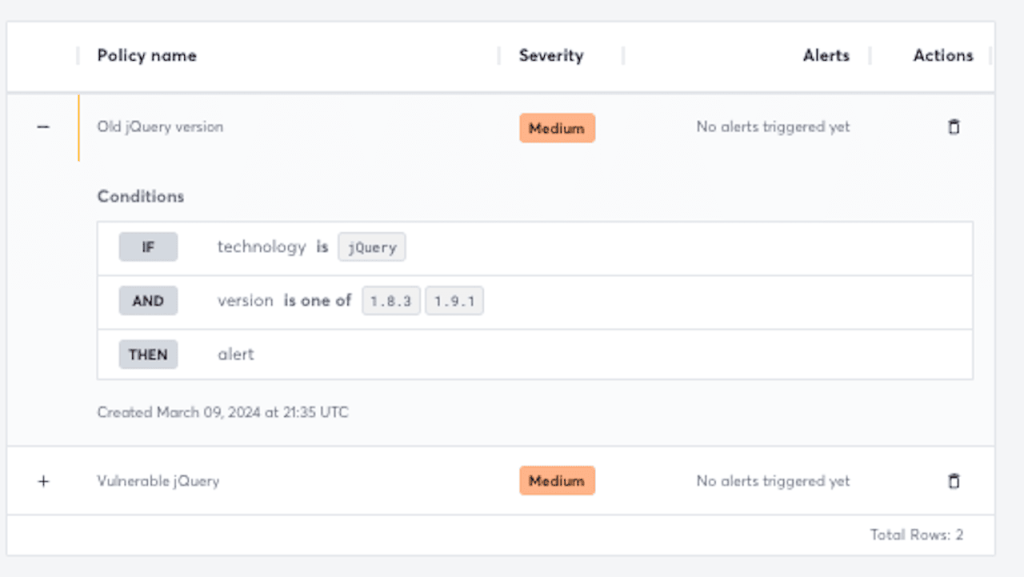
Detectify also has an ace up its sleeve though, and it’s connected with notifications and reporting. Attaxion can send updates over Slack or email about everything new that it discovers during asset monitoring. To avoid getting spammed, you can choose the minimum severity of the vulnerabilities you want to be notified about. With Detectify, you can set up so-called Custom Policies – which basically are more specific notifications. For example, you can set them up so that you get notified whenever a certain technology with certain versions is discovered on one of your organization’s assets.
That helps not to drown in notifications, however, to make Custom Policies truly useful, you’ll need to set up a lot of them.
| Detectify vs Attaxion: Continuous Monitoring | ||
| Attaxion | Detectify | |
| Continuous monitoring alerts | ✅ | ✅ |
| Agentless Traffic Monitoring | ✅ | ❌ |
| IoC Monitoring | ✅ | ❌ |
| Brand Monitoring | ✅ | ❌ |
| Custom policies | ❌ | ✅ |
| API | ✅ | ✅ |
Overall, both tools have their strong sides when it comes to continuous monitoring: Attaxion comes with more monitoring tools such as Agentless Traffic Monitoring, IoC Monitoring, and Brand Monitoring that help speed up threat hunting and incident response. Detectify has Custom Policies that help implement security controls.
 PART 6
PART 6
Conclusion
Both Detectify and Attaxion are solid choices if you’re looking for an External Attack Surface Management tool that won’t break your cybersecurity budget.
Attaxion is still better than Detectify when it comes to discovery. It offers broader asset coverage and is capable of finding more different types of assets. You can only protect the assets that you’re aware of, and with Attaxion, you’ll be aware of more assets than with Detectify, which makes it a great Detectify alternative. Attaxion is also more affordable than Detectify and has unique features like it’s Agentless Traffic Monitoring or IoC Monitoring.
On the other hand, Detectify has been on the market for a while, so it offers some advanced functionalities such as advanced payload-based vulnerability scanning and Custom Policies. However, it can discover and protect fewer assets, thus not completely covering your organization’s external attack surface, and sometimes suffers from false negatives when it comes to vulnerability detection.
This article was updated in January 2026 to incorporate changes in functionality and pricing of both Attaxion and Detectify.
Ready to try Attaxion? Start a 30-day free trial, or request a personal demo.