Best Censys ASM Alternative
Censys.io is best known for Censys Search – a search engine for internet-facing assets with a database that Censys keeps constantly updating. But they also offer other products, including Censys Internet Map, a threat hunting module, and Censys Attack Surface Management (ASM) – a cloud-based solution that allows organizations to discover assets and vulnerabilities that together form their attack surface.
Censys ASM also helps security teams prioritize issues and their remediation, as well as continuously scans for new assets and vulnerabilities, keeping track of changes in the external attack surface.
Attaxion is another solution with a very similar approach. It fully supports External Attack Surface Management (EASM), which makes it a Censys ASM alternative. Let’s compare the two and find out what their stronger sides are.
Quick Summary
| Feature | Attaxion | Censys ASM |
| Pricing | Starting from $1,290/year for 40 assets | Starting from ~$60,000/year |
| Discovery and dependency graphs for digital assets | ✅ | ❌ |
| Quick root asset ownership verification | ✅ | ❌ (verified by the Censys team) |
| Intelligent vulnerability prioritization with EPSS and CISA KEV | ✅ | ❌ |
Important Note & Methodology
Censys.io’s solution (that was previously called Exposure Management) has ASM in its title, which suggests that it’s an attack surface management platform. In this case, it should be capable of scanning the organization’s entire attack surface, including both internal and external assets. However, it’s not the case – just like Attaxion, Censys ASM focuses on internet-facing assets, which effectively makes it an EASM.
Another argument in favor of this position is that ASM solutions rely on the inside-out approach, requiring deployment. EASM tools use an outside-in approach and do not require deployment – and that’s exactly how both Censys ASM and Attaxion work.
ASM solutions often incorporate digital risk protection, but it’s not the case with Censys ASM.
| Censys ASM | Attaxion | |
| Approach | Outside-in | Outside-in |
| Assets covered | External | External |
That yet again proves that Censys ASM is in fact a EASM solution. So, it makes sense to evaluate it with the EASM methodology in mind. To learn more about the methodology, check out our EASM guide.
 PART 1
PART 1
Pricing
When it comes to pricing, Attaxion and Censys have completely different approaches.
| Censys ASM vs Attaxion: Pricing | ||
| Attaxion | Censys ASM | |
| Monthly pricing | From USD $129/month | Not publicly available |
| Yearly pricing | From USD $1,290 | Not publicly available |
| Free trial | ✅ (30 days) | ❌ |
| Assets covered | 40 | Not publicly available |
Attaxion allows anybody who’s interested to sign up and start a free trial. Unlike Attaxion or even Censys’s own Internet Map, Censys Attack Surface Management doesn’t offer a public free trial, and to start using it you need to talk to their representatives.
Currently, Attaxion offers four different plans on it’s pricing page – three that you can pay for by credit card and an enterprise plan for larger attack surfaces. The functionality doesn’t differ between plans. Meanwhile, Censys has 3 different tiers – Core, Advanced, and Enterprise – with a different set of features available on different plans.
Censys doesn’t have publicly available pricing, so it’s hard to compare it with Attaxion from a cost standpoint. We could only rely on information that we could gather from 3rd party sources. Back in 2024, on a British government website, Censys Attack Surface Management was listed at £46,000 per year (roughly $60,000 at that time ). On Amazon, Censys ASM was available at $93,000 per year. Currently, Censys ASM is not listed on any of these websites, but these numbers are enough to get a ballpark estimate.
Attaxion is a much more affordable solution, starting at $1,290/year for 40 assets. That’s roughly 50 times cheaper. We don’t know how many assets are included in Censys’s price, but at least the starting price for Attaxion is much lower.
Overall, when it comes to pricing, Attaxion looks like a clear winner, with publicly available pricing, open free trial, and a much lower starting price.
 PART 2
PART 2
Asset Discovery
The first stage of the EASM process is asset discovery.
Both Attaxion and Censys discover assets in roughly the same way. First, you need to provide some assets belonging to your organization – Censys calls them seeds, while in Attaxion they are known as root assets.
Then, both platforms employ reconnaissance techniques to scan for other assets connected to the ones you provided.
| Censys ASM vs Attaxion: Asset Discovery | ||
| Attaxion | Censys ASM | |
| Types of assets discovered | Domains Subdomains IP addresses Organizations Open ports Email addresses Clouds CIDRs SSL Certificates | Domains Subdomains IP addresses Clouds CIDRs ASNs Clouds SSL Certificates |
| Easy user interface | ✅ | ✅ |
| Asset coverage | Highest | High |
| Dependency graphs | ✅ | ❌ |
| Technology fingerprinting | ✅ | ✅ |
Asset Discovery with Censys ASM
Censys ASM relies on Censys Search to discover assets that are related to your organization.
To start the process, you need to provide the seed assets to Censys – and then talk to the team to verify ownership of these assets. That process can take some time, up to a month in some cases. This is usually a part of the onboarding process.
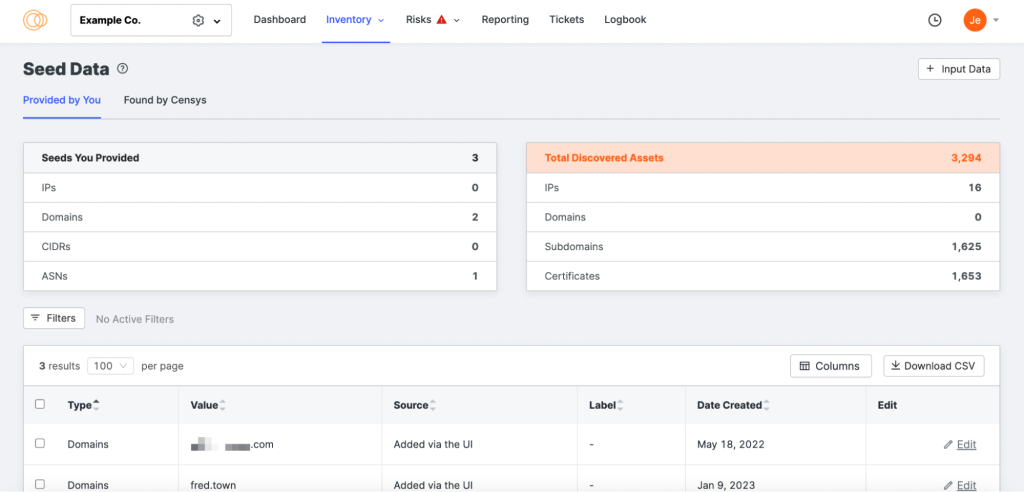
Then, Censys ASM will find some other potential seed assets and suggest that you either add or exclude them. Adding seed assets doesn’t require verification anymore and can be done in mere seconds.
After that, Censys ASM refers to Censys Search to discover related assets – domains and subdomains, IPv4 and IPv6 addresses, cloud buckets, CIDRs and ASNs, and SSL certificates – providing you with an asset inventory. It also builds a list of technologies used across assets.
Asset Discovery with Attaxion
Attaxion’s process of asset discovery consists of fewer stages and provides better results. You only need to add and verify a few root assets – and Attaxion will find the rest of the related assets for you.
Since it’s open to everybody, Attaxion requires root asset verification for security purposes (even though a domain that corresponds with the business email used for sign-up is verified automatically), but it’s a quick process that doesn’t require customer rep interactions and can be done in a few minutes.
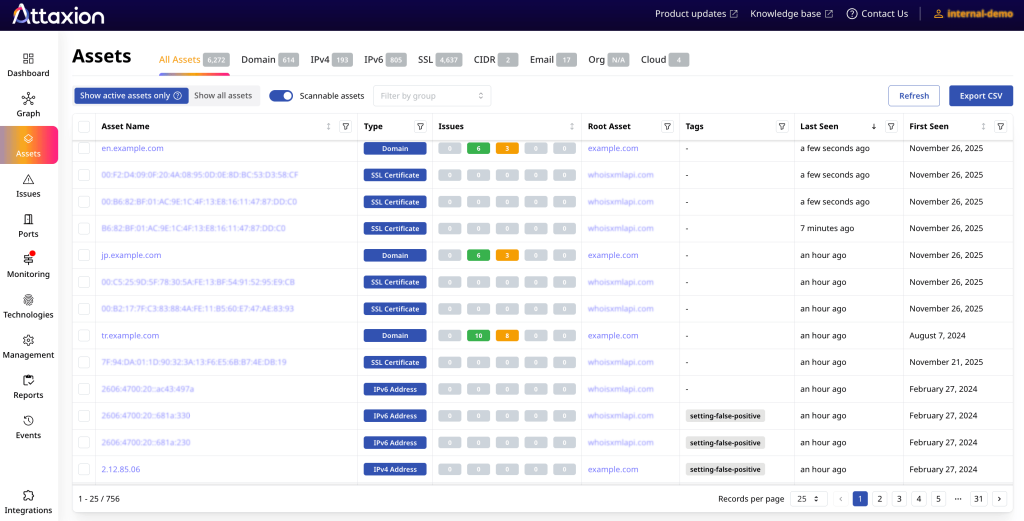
Attaxion can discover the same types of assets as Censys ASM, but it also has a unique functionality to find exposed email addresses.
And in addition to having cloud connectors with AWS, Azure, and GCP, Attaxion also offers to connect with Digital Ocean, which Censys ASM doesn’t have.
How They Compare
Censys ASM and Attaxion use the same approach when it comes to asset discovery.
However, Attaxion can find more types of assets, including publicly exposed emails. Overall, in our test, Attaxion managed to find almost three times more assets than Censys with the same seed (or root asset) input.
Also, Attaxion offers much quicker turnaround time: you only need a few minutes to add the first root asset – and the scanning will start immediately.
We can conclude that when it comes to asset discovery, Attaxion is superior to Censys ASM.
 PART 3
PART 3
Vulnerability Detection and Prioritization
External assets and their vulnerabilities comprise the organization’s external attack surface. So, the next step of the EASM process is to scan all the assets for vulnerabilities.
| Censys ASM vs Attaxion: Vulnerability Detection & Prioritization | ||
| Attaxion | Censys ASM | |
| Scanner | Attaxion (proprietary) + OWASP ZAP | Censys (proprietary) + Censys Search |
| Scanning | Continuous | Continuous (automated seed scanning only for Enterprise customers) |
| Dashboard | ✅ | ✅ |
| Vulnerability scoring | CVSS, EPSS, CISA KEV | Severity(can be manually adjusted) |
| Mark as false positive or accepted risk | ✅ | ✅ (only accepted risk) |
| Manual rescan trigger | ❌ | ? |
Vulnerability Detection & Prioritization With Censys ASM
Censys doesn’t disclose the scanner that Censys ASM uses for vulnerability scanning.
The results of the scan are presented on the tab called Risk Instances. Censys ASM offers quick filters to be able to sort by asset type, environment, risk type, severity, etc.
Censys has an interesting approach to issue severity. By default, there are four severity levels: low, medium, high, and critical. Censys automatically assigns the severity to each risk but allows the user to adjust the severity if they think it’s different from what Censys has assigned.
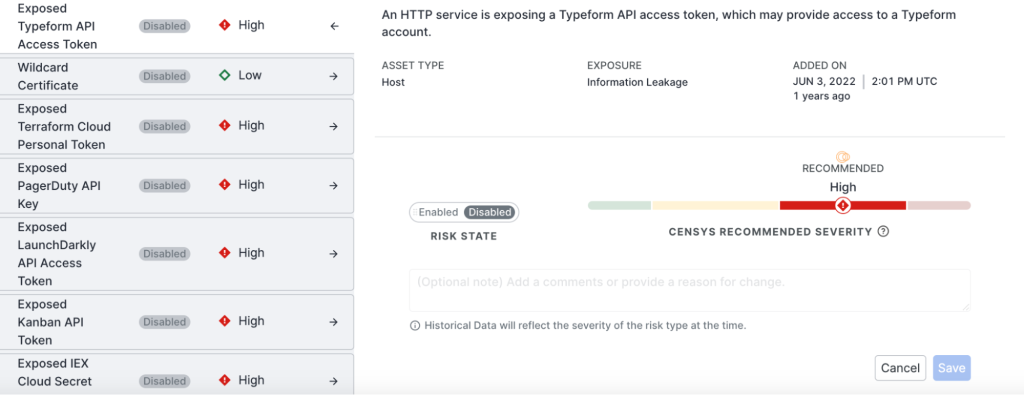
Risks can have different statuses such as new, active, accepted, and closed.
For each risk, Censys provides a short snippet with remediation recommendations.
Vulnerability Detection with Attaxion
Attaxion relies on a proprietary scanner to scan assets for vulnerabilities and does it continuously. The scanner is up to date with NIST’s and Mitre’s CVE and CWE databases.
Attaxion lists all discovered issues under the “Issues” tab, offering a dashboard with distribution by severity there.
In addition to all the severity levels that Censys offers, Attaxion has one more – info, which is 0, aka unknown severity. Attaxion also shows CVSS scores for each risk, as well as EPSS (likelihood of exploitability) and CISA KEV (real-world exploitation) data. That allows for more granular prioritization.
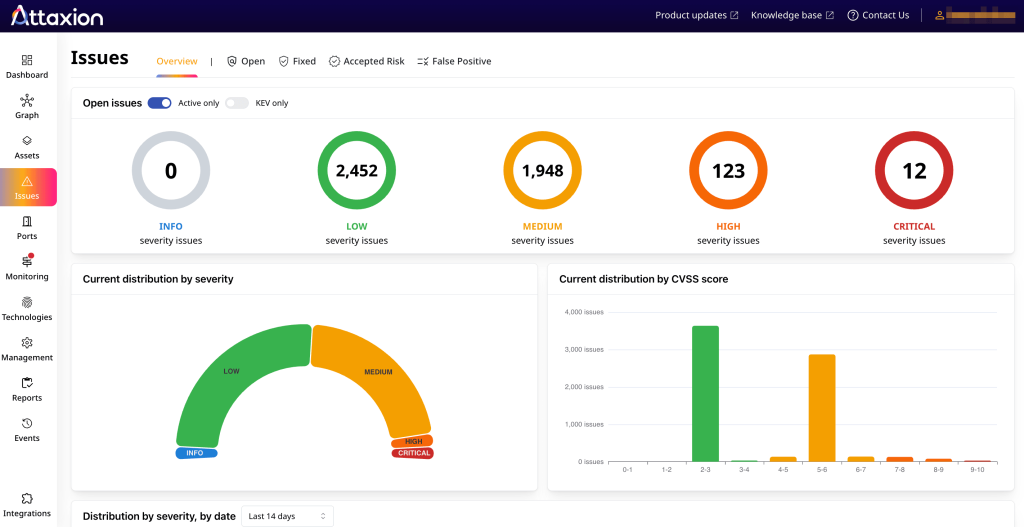
Attaxion lists unique vulnerabilities and the number of affected assets. Clicking on a certain vulnerability gives you details about what the vulnerability is, where it’s found, a link to the CWE or CVE page, some remediation suggestions, and links to the sources of information that Attaxion used to gather all the information.
How They Compare
When it comes to vulnerability detection, Censys ASM and Attaxion are very similar, with Attaxion having an edge in prioritization.
They have a slightly different approach to dashboards, but most importantly, different ideas of prioritization. Censys ASM offers to manually adjust risk severity, while Attaxion provides more context for prioritization, offering exploitability data on top of severity.
 PART 4
PART 4
Remediation
The next step after vulnerability detection and prioritization is remediation or at least mitigation of the issues. When it comes to EASM solutions, it usually boils down to providing some suggestions and partially automating the creation of tickets in support tracking software.
| Censys ASM vs Attaxion: Vulnerability Remediation | ||
| Attaxion | Censys ASM | |
| Remediation suggestions | ✅ | ✅ |
| Integrations with ticketing software | Jira | Jira ServiceNow |
| API | ✅ | ✅ |
Remediation With Censys ASM
As we already mentioned, Censys ASM provides short remediation suggestions for each vulnerability.
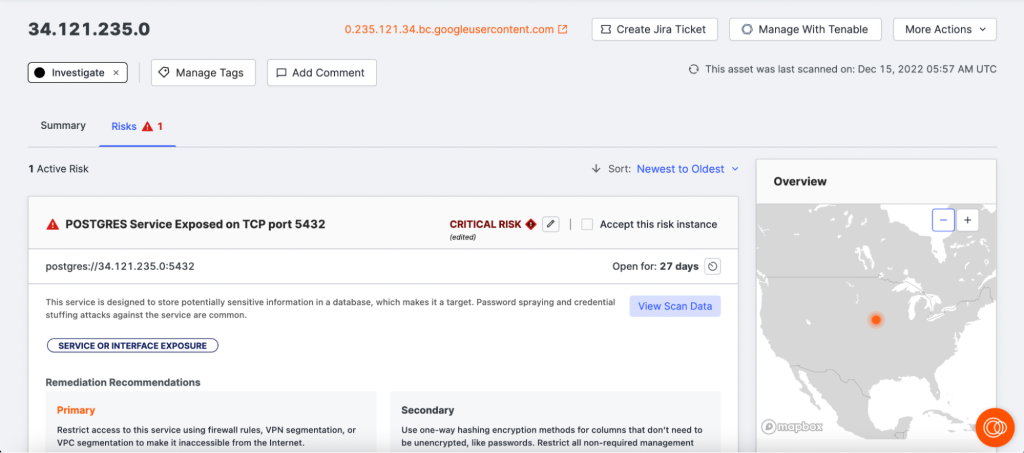
To speed up remediation or risk mitigation, it allows users to create support tickets with risk details in two project management tools – Atlassian Jira and ServiceNow. Censys ASM also offers an API if you want to connect it to something other than the two platforms listed above.
Remediation With Attaxion
Attaxion is not very different from Censys ASM when it comes to vulnerability remediation.
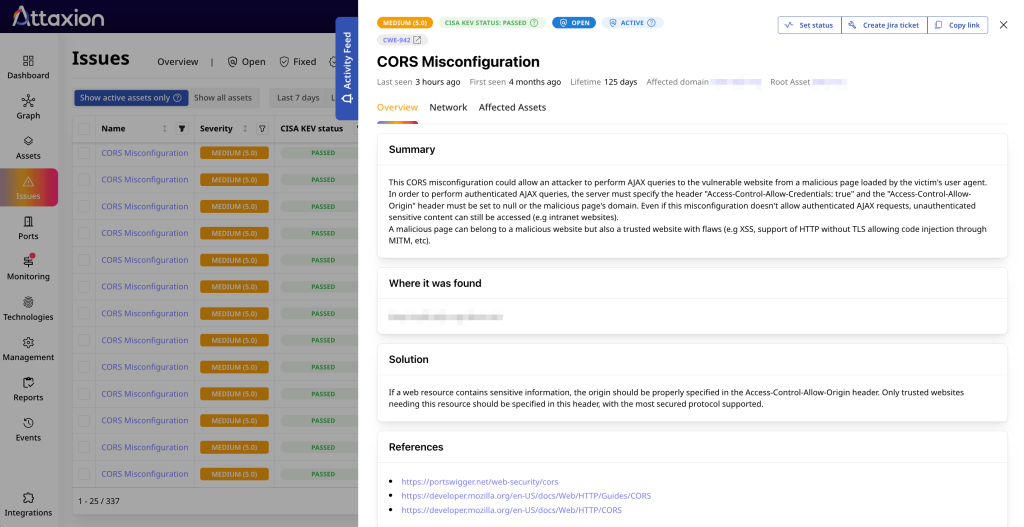
It pulls remediation suggestions from different sources, sometimes being more informative than Censys ASM. It has an integration with Jira for ticket creation. This is the only such integration at the moment, but Attaxion offers to develop integrations on demand if you need them. Also, teams that want to plug Attaxion into their existing tools or workflows can use its REST API to pull data into just about any system.
How They Compare
Censys ASM and Attaxion are very similar to each other when it comes to vulnerability remediation. Both offer recommendations and the ability to create support tickets.
Attaxion sometimes has more detailed suggestions, while Censys ASM has one more integration out of the box. However, both tools have an API if you need to build more integrations.
 PART 5
PART 5
Continuous Monitoring
The final step of the EASM process is continuous monitoring. Platforms keep looking for new digital assets and scan the entire external attack surface for vulnerabilities.
For the user, it often boils down to notifications about new scans, new assets, and new issues, but Attaxion has a couple of additional monitoring-related features.
| Censys ASM vs Attaxion: Continuous Monitoring | ||
| Attaxion | Censys ASM | |
| Continuous attack surface discovery | ✅ | ✅ |
| IoC monitoring | ✅ | ❌ |
| Agentless network traffic monitoring | ✅ | ❌ |
| Email notifications | ✅ | ✅ |
| Customizable notifications | ✅ (By risk severity) | ✅ (By risk severity) |
| Integrations with messaging software | Slack | Slack Microsoft Teams Cisco Webex Teams |
Continuous Monitoring with Censys ASM
Censys ASM keeps scanning the Internet for new assets that can be associated with your organization and new vulnerabilities.
To notify you about them, Censys ASM offers either email notifications or integrations with messengers such as Slack, Microsoft Teams, and Cisco Webex Teams. You can choose the severity level of risks that you want to get notifications about.

In addition to that, Censys ASM has integrations with Microsoft Sentinel (a SIEM tool) for better event tracking, with Qualys VMDR and Tenable VM for vulnerability management, and with Splunk Cloud & Enterprise if you’re using it for data analysis.
Continuous Monitoring with Attaxion
Attaxion also continuously finds new assets and vulnerabilities, using the same broad spectrum of cyber reconnaissance techniques.
In addition to that, Attaxion has a feature called IoC Monitoring that tells you if an IP address in your infrastructure is known to be associated with malicious activity.
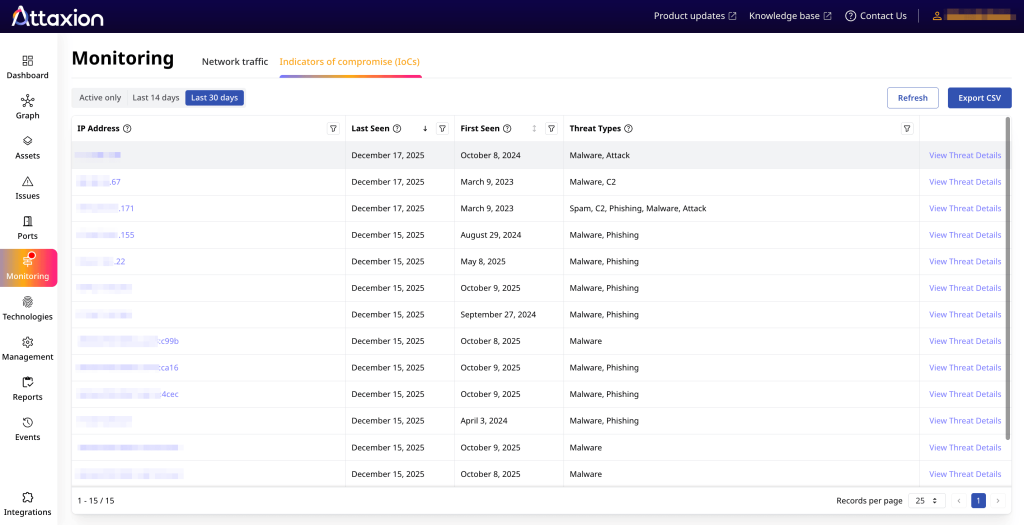
Another Attaxion’s unique monitoring feature is Agentless Network Monitoring. Using NetFlow data, it tells you which external IPs do your infrastructure IP addresses communicate with, and on which ports.
For notifications, it relies on either email or a Slack integration. Similarly to Censys ASM, you can choose the minimum risk severity you want to receive notifications about.
Attaxion doesn’t have other integrations at the moment, but offers to develop them on demand, or you can rely on the REST API that it has.
How They Compare
Both Censys ASM and Attaxion continuously scan for new assets and vulnerabilities and both offer email and messenger notifications. Censys ASM has more messenger integrations and slightly more customizable notifications, while Attaxion keeps an eye on your network traffic and integrates threat intelligence feeds to show if your infrastructure’s IPs are also used for malicious purposes.
 PART 6
PART 6
Conclusion
Attaxion and Censys ASM are two external attack surface management tools with similar functionalities.
Censys ASM’s stronger side is its broader set of integrations and some additional flexibility when it comes to vulnerability prioritization. Censys also offers to create more different kinds of reports.
Attaxion, on the other hand, excels at asset discovery and vulnerability scanning – the two main stages of the EASM process. It also provides more context for risk prioritization, as well as unique monitoring features for network traffic and IP reputation. As a result, it gives you a much more complete picture of the organization’s external attack surface, with more assets, more vulnerabilities, and more complete context. As a platform for EASM, Attaxion is a stronger Censys alternative.
It also offers a unique graph view showing connections between assets and outlining possible attack paths. The rest of its functionality is quite similar to what Censys has.
The key differentiator is pricing: Attaxion’s starting price is about 50 times lower than that of Censys ASM. This makes Attaxion a much more attractive tool for security teams that are concerned about their budgets but do not want to compromise on quality.
Ready to try Attaxion? Start a 30-day free trial, or request a personal demo.