Manage Your Threat Exposure
Protect your exposed assets from emerging threats and exploitable security issues.
Detect exposed assets
Uncover Internet-facing assets at risk using modern discovery methods and reconnaissance techniques.
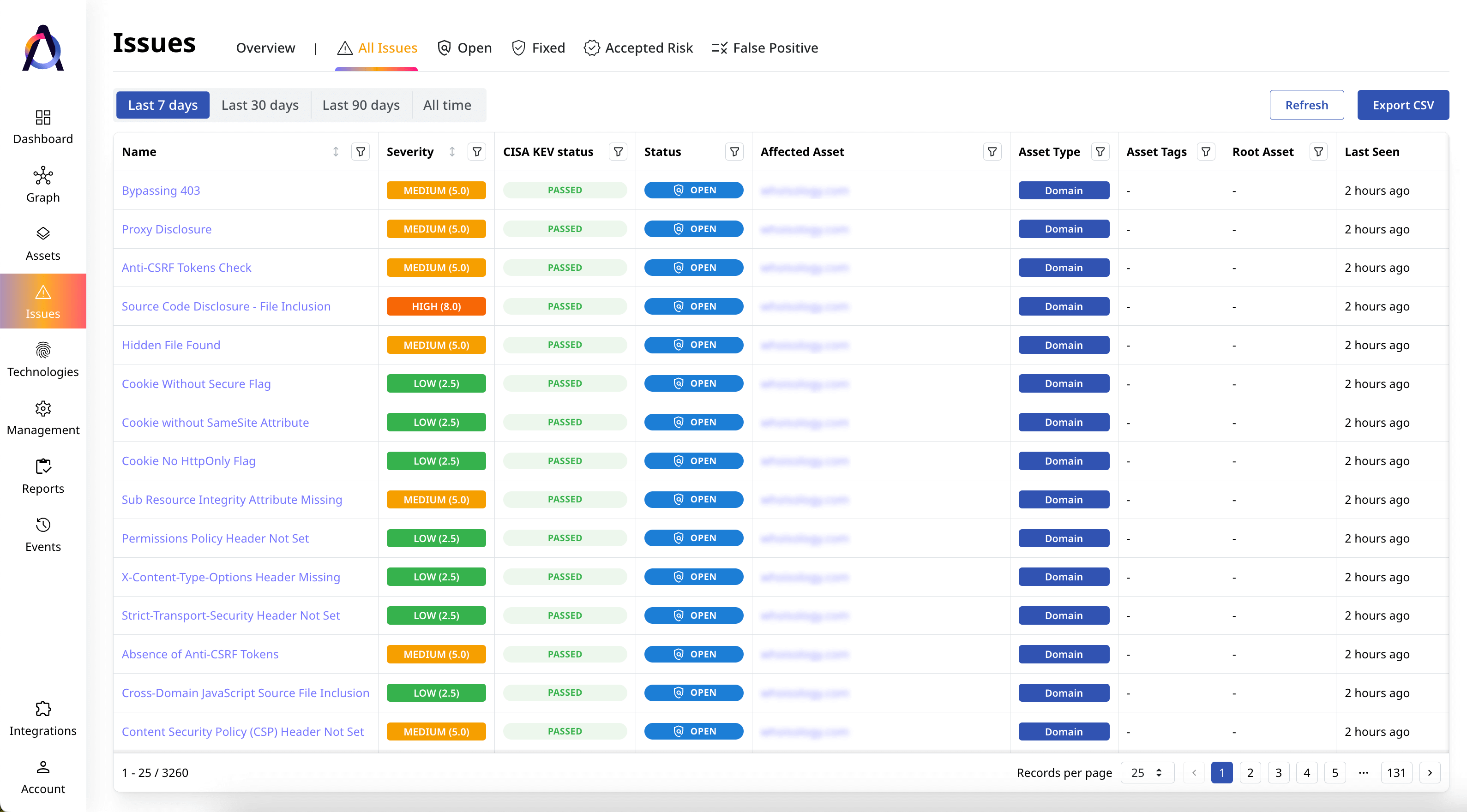
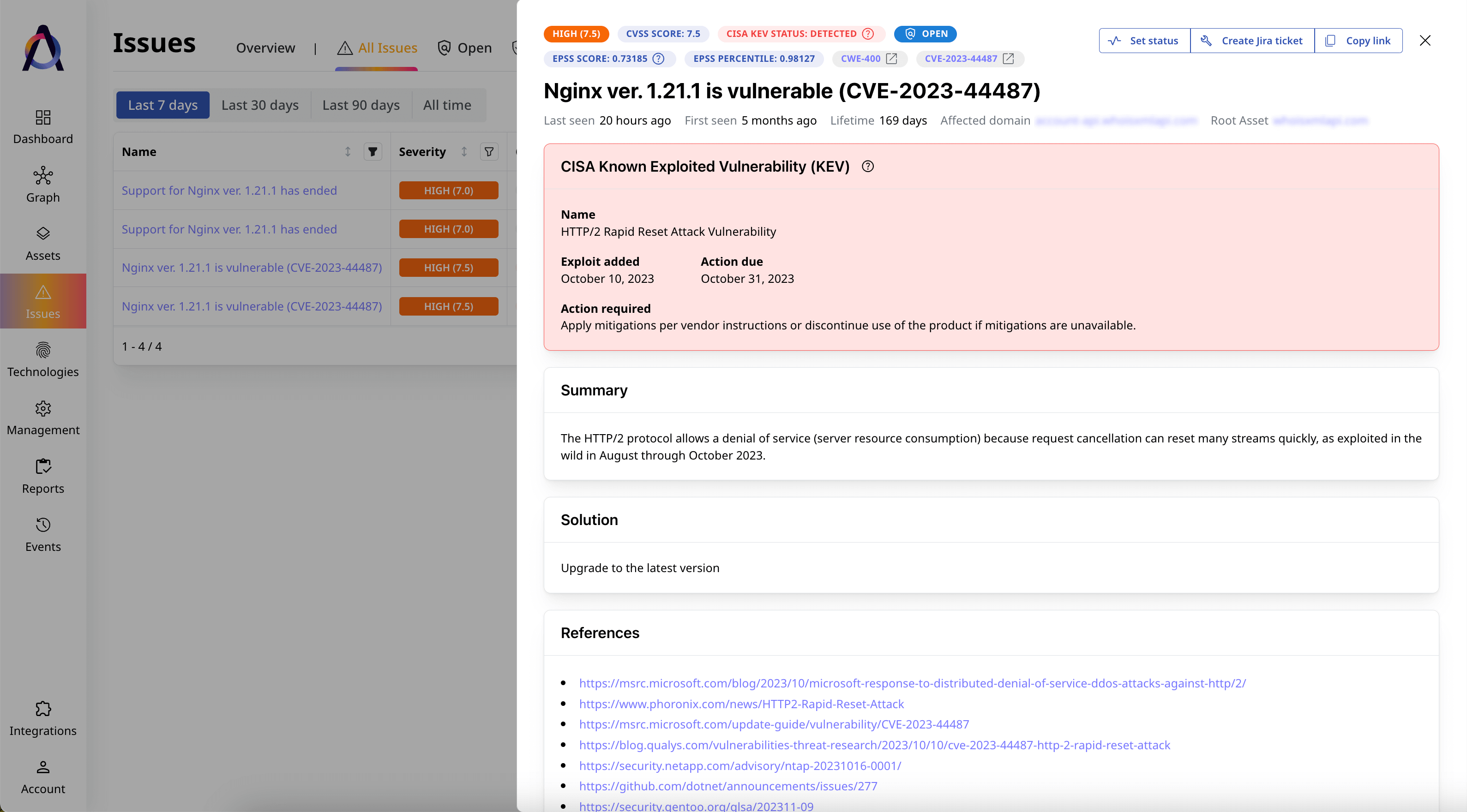
Uncover issues and vulnerabilities
Identify all security gaps exposing your public-facing assets to threats.
Address cyber risks continuously
Plan, assign, and monitor remediation tasks to reduce exposure to threats.
-
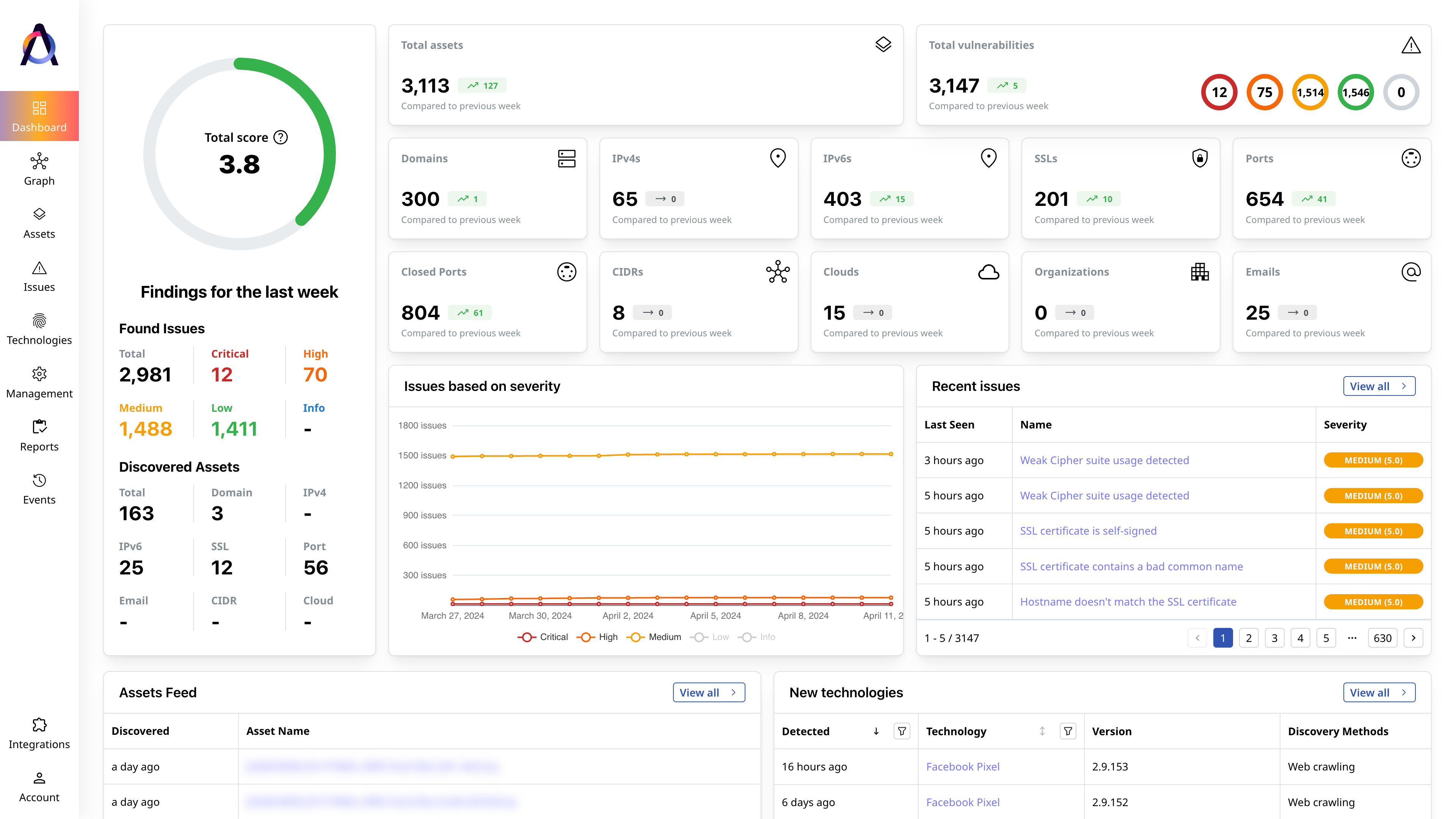
Complete Inventory
Access comprehensive catalogs of your exposed assets and their issues.
-
Third-Party Integrations
Unify remediation by integrating project management and ticketing tools.
-
Detailed Reporting
Know your overall threat exposure and drill down on each issue.
What security experts say
Featured Resources

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

CWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like CWE, CVE, and CVSS. These term[...]

How to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sensitive information, or disrupt[...]