Attack surface mapping is the process of identifying and cataloging an organization’s physical and digital assets, along with the attack vectors associated with them.
Cataloging here means going beyond creating an inventory of assets—it involves uncovering connections between the assets and pinpointing the potential ways an attacker could interact with these assets (i.e., attack vectors).
In other words, attack surface mapping involves discovering all assets, mapping asset-to-asset connections, and scanning the assets for vulnerabilities.
Table of Contents
- Why Is Attack Surface Mapping Important?
- Types of Attack Surfaces
- Techniques and Tools for Attack Surface Mapping
- How to Map Your Attack Surface
- Best Practices for Attack Surface Mapping
- Key Takeaways
- FAQs
Why Is Attack Surface Mapping Important?
As an initial part of the larger external attack surface management (EASM) process, attack surface mapping provides the foundational catalog needed to make EASM work. Its most significant benefit is improved visibility into all potential entry points for cyberattacks, including assets that may have otherwise been overlooked.
Moreover, attack surface mapping goes beyond identifying potential attack vectors. It also helps organizations understand the relationship between different assets and, therefore, the process can reveal potential attack paths—the “digital roads” attackers can take to infiltrate a target system.
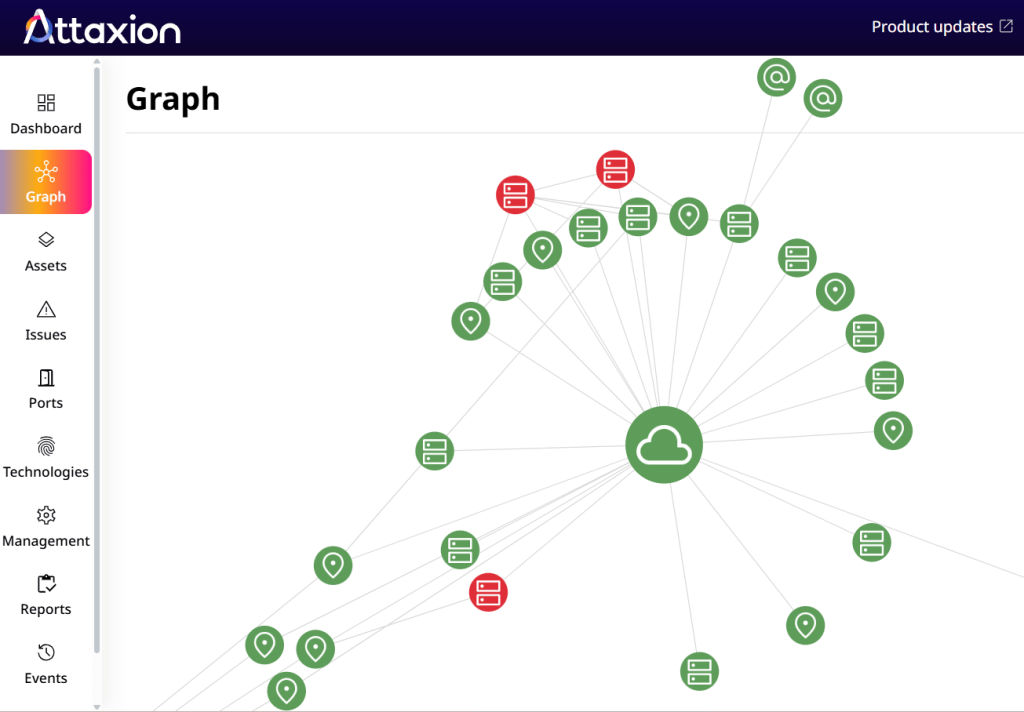
What Are the Types of Attack Surfaces?
Most organizations deal with several types of attack surfaces all at once—digital, physical, and social engineering.
The digital attack surface includes all potential entry points within an organization’s information systems that attackers can use to gain access to data. It encompasses digital assets like websites, databases, applications, operating systems, and cloud assets and their misconfigurations, vulnerabilities, and other security issues. These attack vectors can be accessed remotely, increasing the likelihood of exploitation of vulnerabilities in an organization’s digital attack surface.
The physical attack surface is more restricted. It involves physical intrusion, theft, tampering, and unauthorized access to facilities, hardware, servers, data centers, Internet of Things (IoT) devices, workstations, mobile devices, and other tangible assets.
Lastly, there’s the human element, which we call the social engineering attack surface. This type of attack surface covers human vulnerabilities that can be exploited through manipulation—phishing, impersonation, and pretexting are some of the most common tactics that come to mind.
Techniques and Tools for Attack Surface Mapping
Since an attack surface comprises very different assets and issues, it’s impossible to use just one cyber reconnaissance technique to discover all of them. As a result, attack surface mapping requires a blend of techniques that mostly run automatically:
- Subdomain enumeration: This technique aims to discover all subdomains associated with a target domain so that exposed staging environments and other services are immediately detected. It can be performed directly by querying DNS servers to find subdomains (i.e., active subdomain scanning) or by analyzing historical DNS data and certificate transparency logs (i.e., passive subdomain scanning).
- DNS enumeration: Attack surface mapping requires the use of tools that can gather the DNS records associated with a domain (e.g., A, AAAA, CNAME, MX, NS, TXT). DNS enumeration tools typically query DNS servers to retrieve these records. Reverse DNS lookups then help discover other assets associated with these records (such as other domains using the same mail server, for example).
- WHOIS discovery: This technique identifies a domain’s ownership and registration details, which are useful for discovering other assets owned by the same organization.
- Web crawling and content discovery: This involves exploring websites by following links and submitting various HTTP requests to comprehensively map the website’s structure and discover all accessible pages, directories, files, and associated content. That helps reveal technologies used across the organization’s websites and potentially find more associated domains.
- ASN and IP space mapping: Identifying the ASNs and IP ranges associated with the organization helps security teams understand the organization’s network infrastructure.
- Technology fingerprinting. This attack surface mapping technique gives security teams insights into the organization’s tech stack, including content management systems (CMS), web frameworks, server software, programming languages, and other related software. Technology fingerprinting also extends to an organization’s cloud environment, helping identify cloud services and assets.
- SSL certificate analysis: This technique examines SSL certificate details, such as expiration dates, certificate authority (CA) validation, and certificate chains, to detect security vulnerabilities and misconfigurations.
- Vulnerability scanning: This technique compares the asset’s software versions and configurations against known vulnerability databases to detect potential vulnerabilities. Vulnerability scanners also check for common misconfigurations, such as weak passwords and default credentials.
- Port scanning: Port scanning determines which ports are open and what services are running on them by sending network packets.
How to Map Your Attack Surface
Mapping your attack surface can be described as a four step-process, which we break down below.
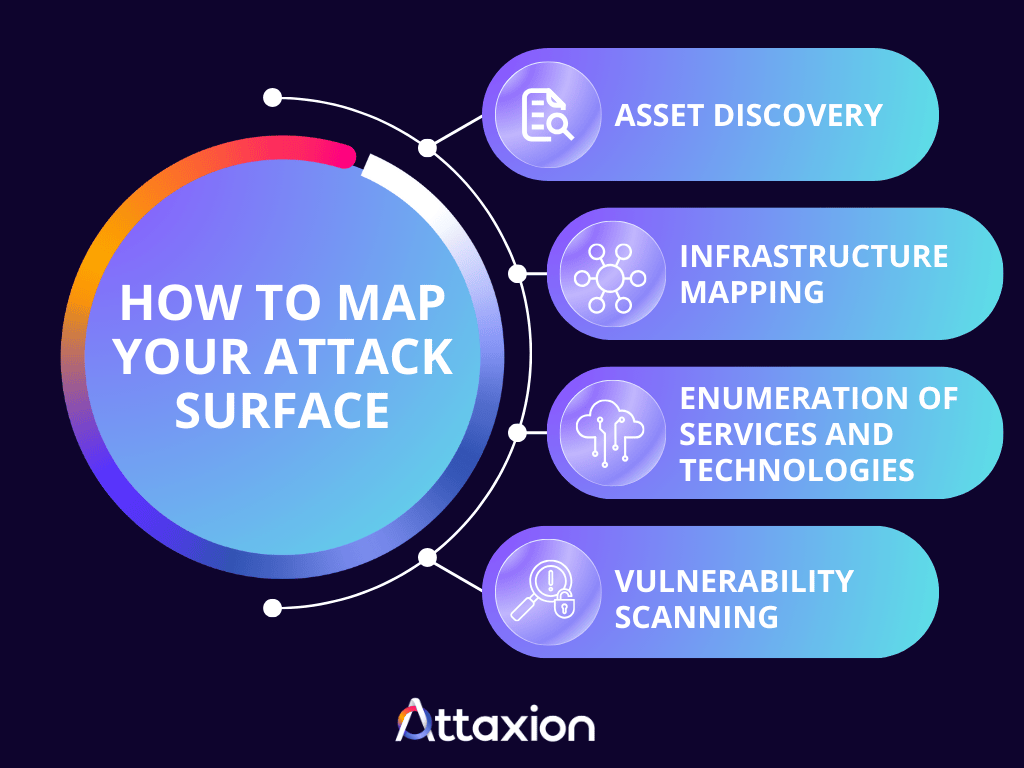
1. Asset Discovery
Asset discovery involves identifying all Internet-facing assets, specifically those that contribute to an organization’s attack surface. This step essentially tells organizations what are the possible attack targets.
Websites and web applications are the most common external-facing assets, and they are included in asset discovery. However, they have components that may not be immediately visible but nonetheless externally exposed, such as:
- Domains
- Subdomains
- IP addresses
- SSL certificates
- Open ports
The asset discovery process should also identify cloud assets like buckets and compute instances if the organization uses cloud systems. Email addresses can also be considered an external digital asset type since they are visible to outsiders and can be exploited in impersonation and phishing campaigns. The main goal of this step is to identify forgotten or unknown assets that have not been on the security team’s radar.
2. Infrastructure Mapping
The next step is to document network architecture, dependencies, and third-party integrations to gain a clear picture of the system layout. This is called infrastructure mapping, which essentially maps asset-to-asset connections.
3. Enumeration of Services and Technologies
Now that you have visibility over the organization’s digital assets and how they are connected, you would need to identify open ports, running services, software versions, and exposed endpoints. It helps security teams understand how attackers can potentially gain access and make the next step—vulnerability scanning—more targeted and effective.
4. Vulnerability Scanning
Since there is already a list of services and technologies (along with their software versions), security teams can focus vulnerability scans on specific components and even perform version-specific vulnerability detection.
For instance, they can perform a targeted scan on a web server running on, say, open port 80 that was found while enumerating the organization’s services and technologies. While opening port 80 is common, the vulnerability scan revealed that the web server is running Apache HTTP Server version 2.4.41 (the latest as of the time of writing is version 2.4.63). This means that the organization’s web server is outdated and has unmitigated Apache server vulnerabilities.
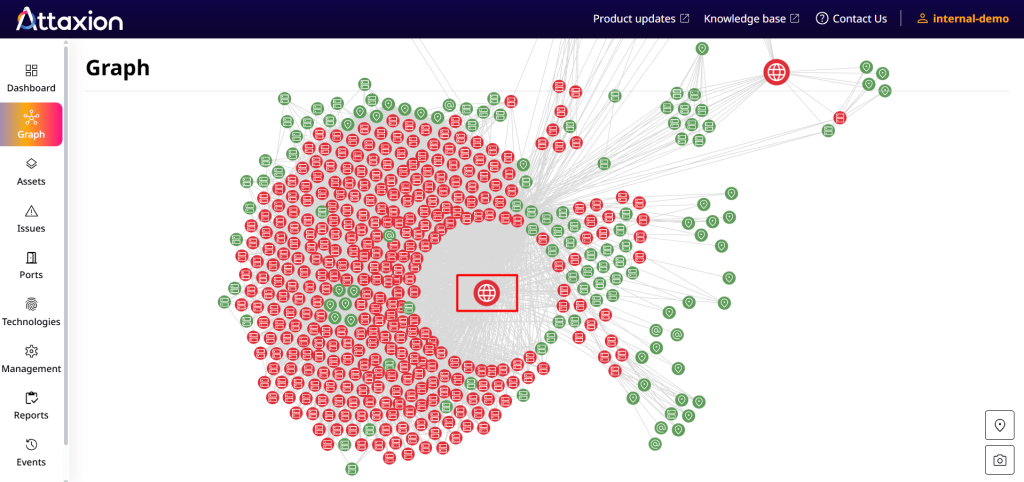
Take a look at the website inside the red box in the attack surface graph below. All of the vulnerable assets (colored red) connected to it, both directly and indirectly, represent potential attack vectors. This helps organizations understand where an attacker can start their infiltration efforts and enables security teams to map out possible attack paths.
Best Practices for Attack Surface Mapping
Having outlined the basic steps of attack surface mapping, it’s important to acknowledge that these activities can be optimized by integrating best practices.
- Prioritize critical assets: Some assets contain or lead to sensitive information, such as databases containing customer financial records and public-facing login pages. Prioritizing these assets in attack surface mapping ensures that all attack paths leading to them are immediately discovered and that remediation resources are allocated effectively.
- Maintain an up-to-date inventory of assets: Asset discovery should not be a one-time activity since digital resources are constantly being added and decommissioned throughout the course of day-to-day operations. The list of assets you have today would not be the same a month from now. Automating asset discovery can significantly help ensure that your asset catalog is updated.
- Use your attack surface map to create a threat model: While attack surface mapping is an integral part of EASM, the insights gained from the process can also be used to create a threat model—a structured approach that anticipates potential threats that may impact the organization. Frameworks like MITRE ATT&CK can be used to map out threat actor tactics and techniques.
- Minimize the attack surface: Attack surface mapping often reveals that your attack surface is getting bigger, which means that the likelihood of an asset and its vulnerabilities getting overlooked—and exploited—becomes higher. One way to avoid this is to continuously minimize the attack surface by disabling unnecessary services, closing unused ports, and regularly updating software.
- Automate attack surface mapping: ASM tools can automate the process by combining asset discovery techniques with vulnerability scanning. They can also handle large and complex attack surfaces and eliminate the need for manual asset inventory, which is often incomplete and prone to errors.
Key Takeaways
- Attack surface mapping is the process of identifying and cataloging an organization’s physical and digital assets and their associated attack vectors.
- It is a part of the larger EASM process that helps uncover forgotten assets, hidden connections, and unknown security issues, strengthening the organization’s security posture.
- It involves four fundamental steps—asset discovery, infrastructure mapping, enumeration of services and technologies, and vulnerability scanning.
- The process can be optimized through automation and by prioritizing critical assets, maintaining an up-to-date asset catalog, creating a threat model, and disabling unnecessary services and open ports.
- ASM tools allow security teams to automate the entire attack surface mapping, from asset discovery to vulnerability scanning.
FAQs
What are the challenges in attack surface mapping?
The biggest challenge in attack surface mapping is the complexity of modern networks, which often involve multi-cloud and hybrid environments. Not to mention IoT devices and shadow IT assets that drastically expand the attack surface and make digital infrastructures more tangled.
Adding to the challenge is the dynamic nature of these environments—an organization’s attack surface can quickly change and expand, adding new security risks despite the best efforts of the security team.
How often should attack surface mapping be done?
As a part of continuous attack surface monitoring, attack surface mapping is an ongoing process. However, in addition to that, it’s considered a best practice to perform full attack surface mapping annually, with highly dynamic environments going for more frequent mappings (e.g., semi-annually or quarterly). This annual mapping is somewhat of a deep dive with the goal of obtaining a more up-to-date snapshot of the attack surface on top of fully automated continuous monitoring.
Can attack surface mapping be automated?
Attack surface mapping can be automated, and due to the continuously growing attack surfaces, automation has actually become non-negotiable. While some manual aspects remain (especially in highly specialized or physical security areas), the majority of the process can be streamlined with the right tools, such as quality external attack surface management platforms.
How do you prioritize assets during mapping?
Prioritizing assets during attack surface mapping entails asking questions like:
- What assets are essential for your organization’s core operations?
- What assets contain personally identifiable information (PII), protected health information (PHI), trade secrets, intellectual property, and other sensitive data?
- What assets, if compromised, would have the most significant financial or reputational impact?
- What assets are subject to regulatory requirements (e.g., HIPAA, PCI DSS, GDPR)?
