PLATFORM CAPABILITIES
PLATFORM CAPABILITIES
Risk Remediation
Effectively tackle your critical security issues and minimize risk exposure.
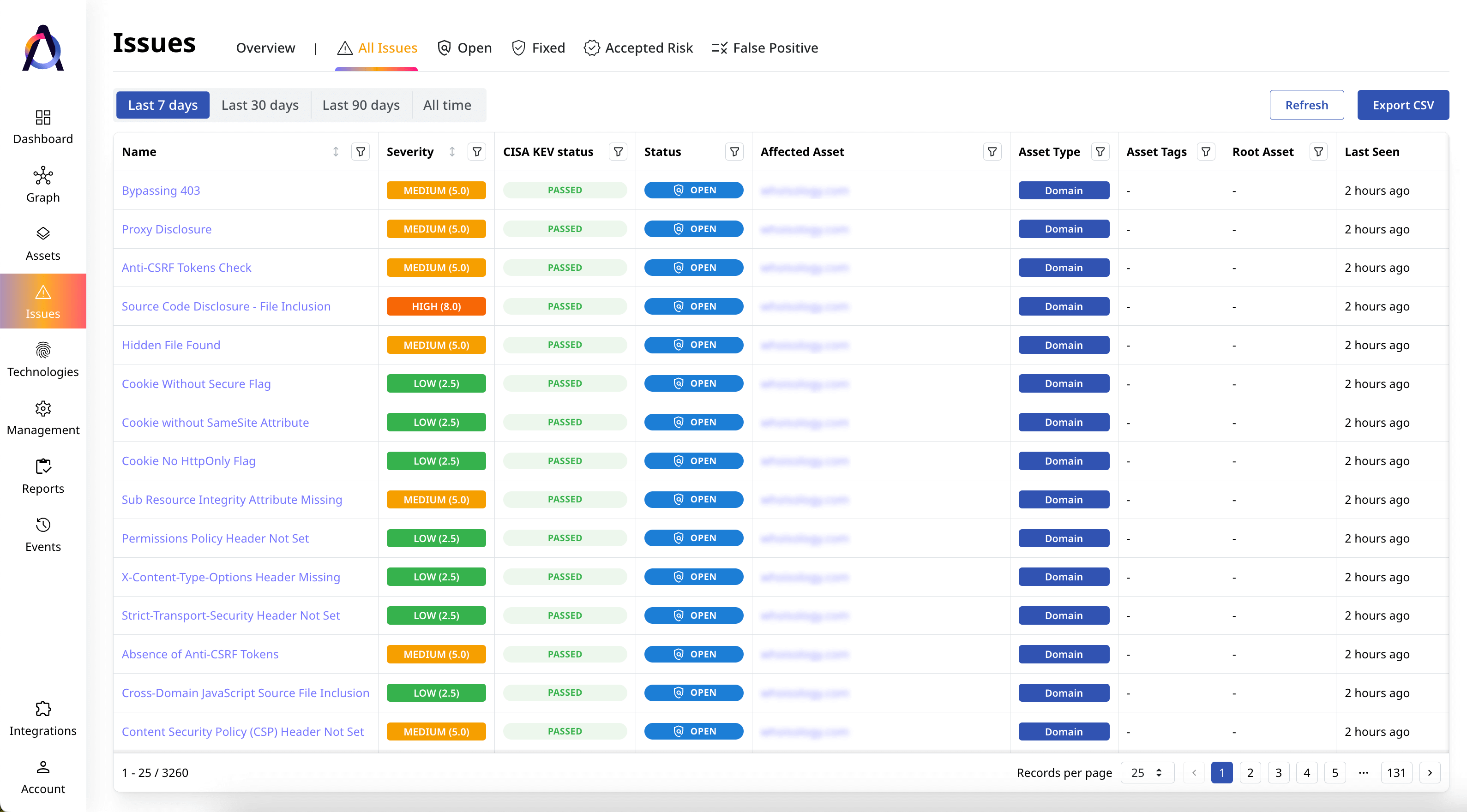
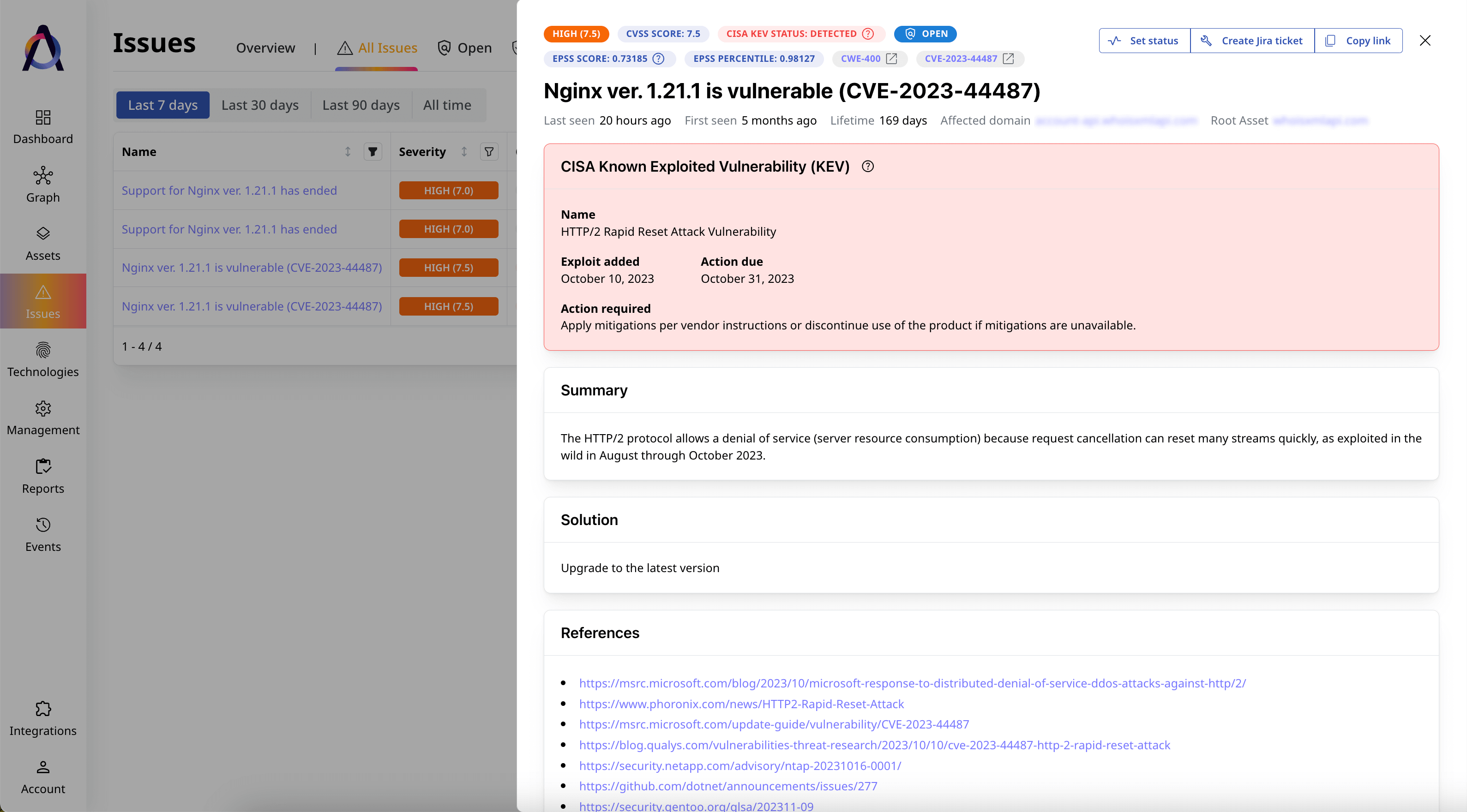
Access deep vulnerability intelligence
Gather detailed context about the major risks affecting your external assets, along with guidelines for remediation.
Plan and automate remediation tasks
Manage remediation efforts by planning tasks and automatically creating tickets on designated channels.
Track and report progress
Stay on top of vulnerabilities by categorizing and tracking their remediation status while keeping your team informed.
-
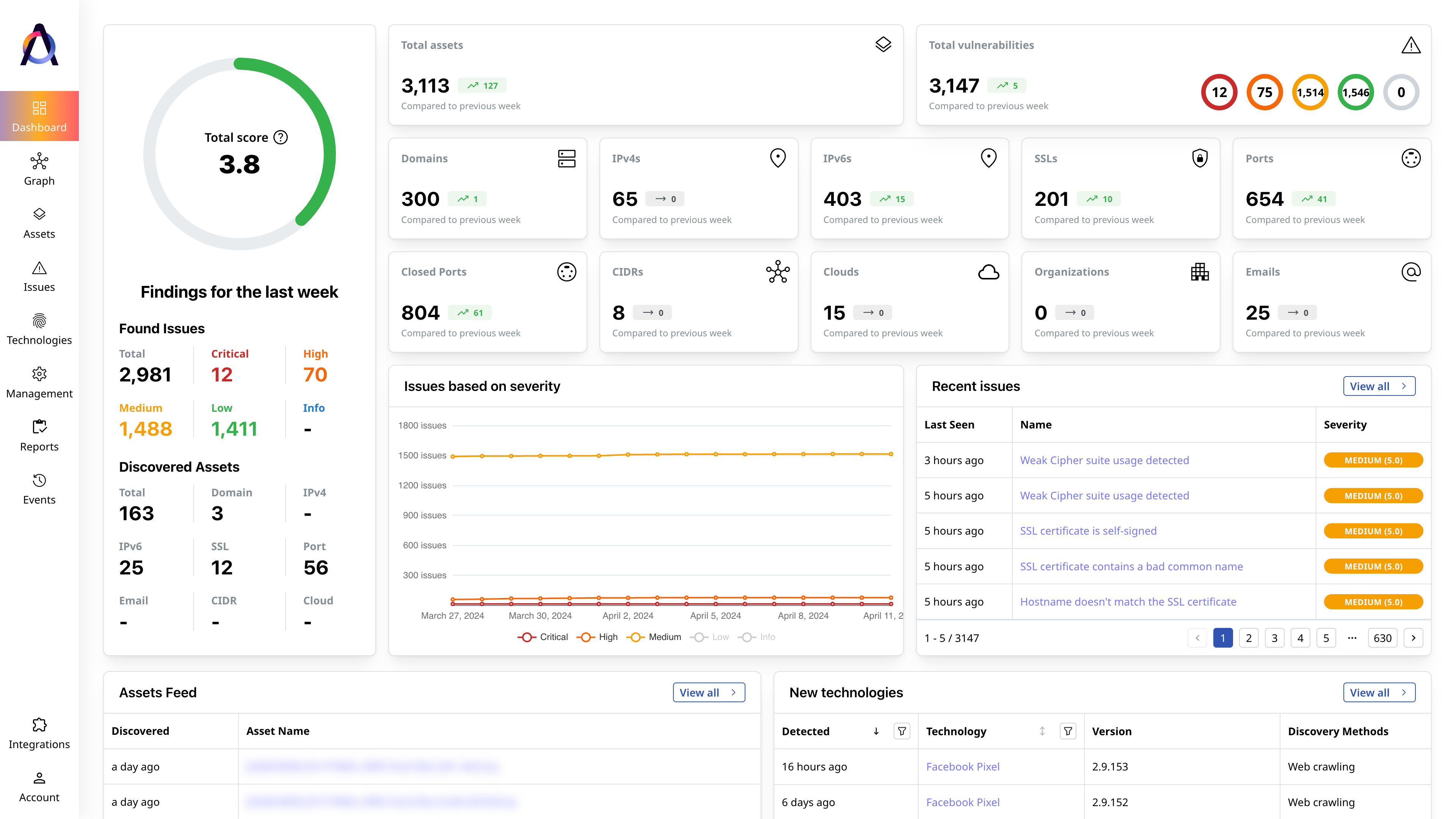
Superior Coverage
Discover twice as many assets and their security issues for more asset types.
-
Start Right Away
Jump into action—find and protect your vulnerable assets within hours.
-
Any Security Budget
Small or very large attack surface? Attaxion has the right pricing for you.
Our Remediation Features
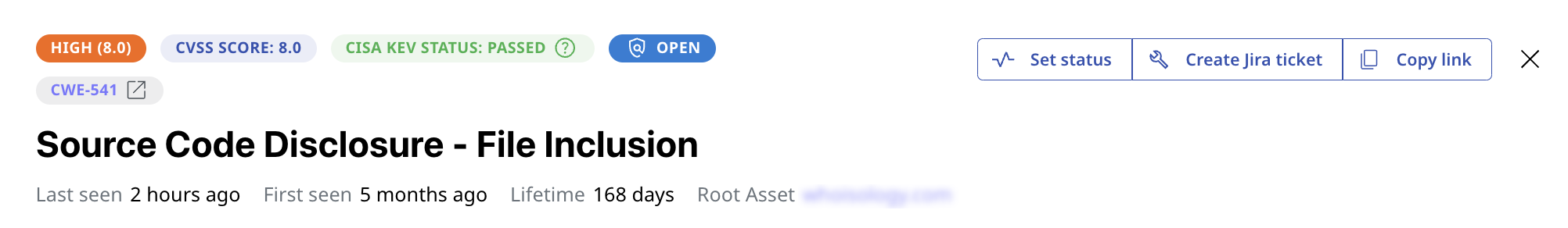
- ✅ Overview and scoring of the entire attack surface
- ✅ CVSS severity ranking
- ✅ Exploitable vulnerability identification via KEV and EPSS
- ✅ Remediation guidance for security issues
- ✅ Issue status—open, fixed, accepted risk or false positive
- ✅ Ticket creation with Jira integration
- ✅ References from CVE, CWE, and EUVD databases
- ✅ Exportable vulnerability reports
What security experts say
Featured Resources

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

CWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like CWE, CVE, and CVSS. These term[...]

How to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sensitive information, or disrupt[...]