PLATFORM CAPABILITIES
PLATFORM CAPABILITIES
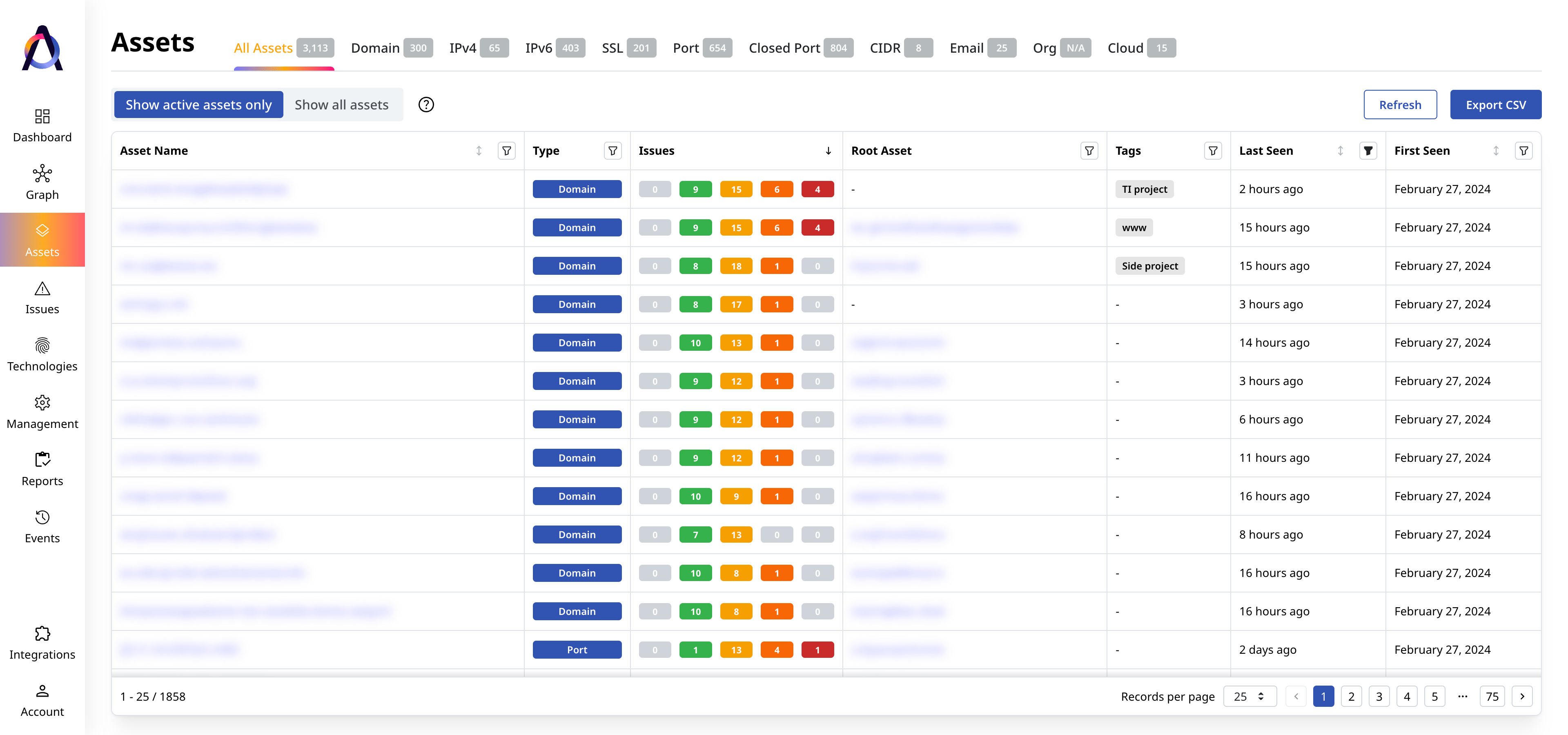
Continuous Monitoring
Maintain complete visibility over your Internet-facing assets and security issues.
Automatically discover and validate new assets
Find and catalog new external assets and technologies as your digital infrastructure expands.
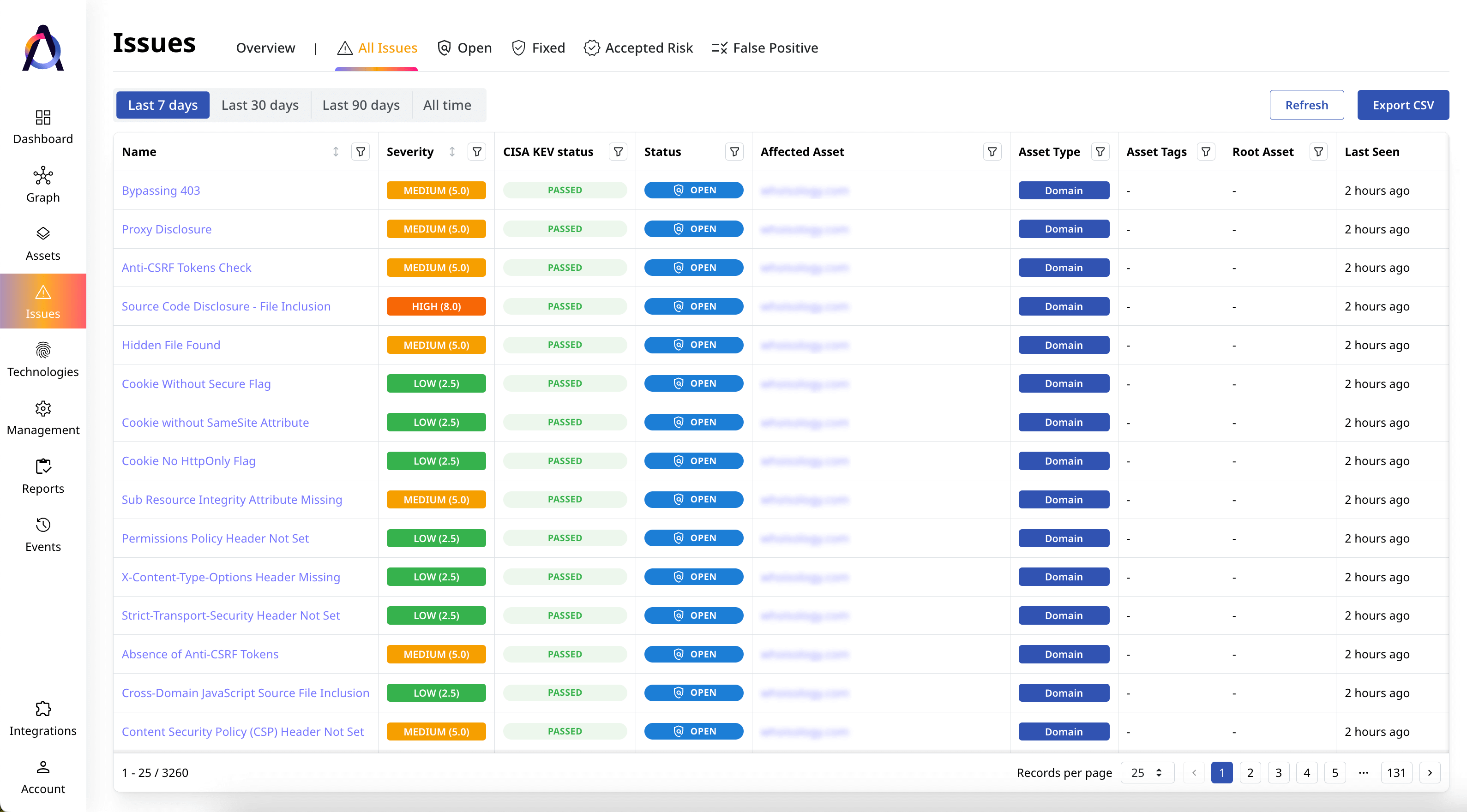
Review emerging vulnerabilities
Automatically scan all your assets for known and new vulnerabilities and other security issues.
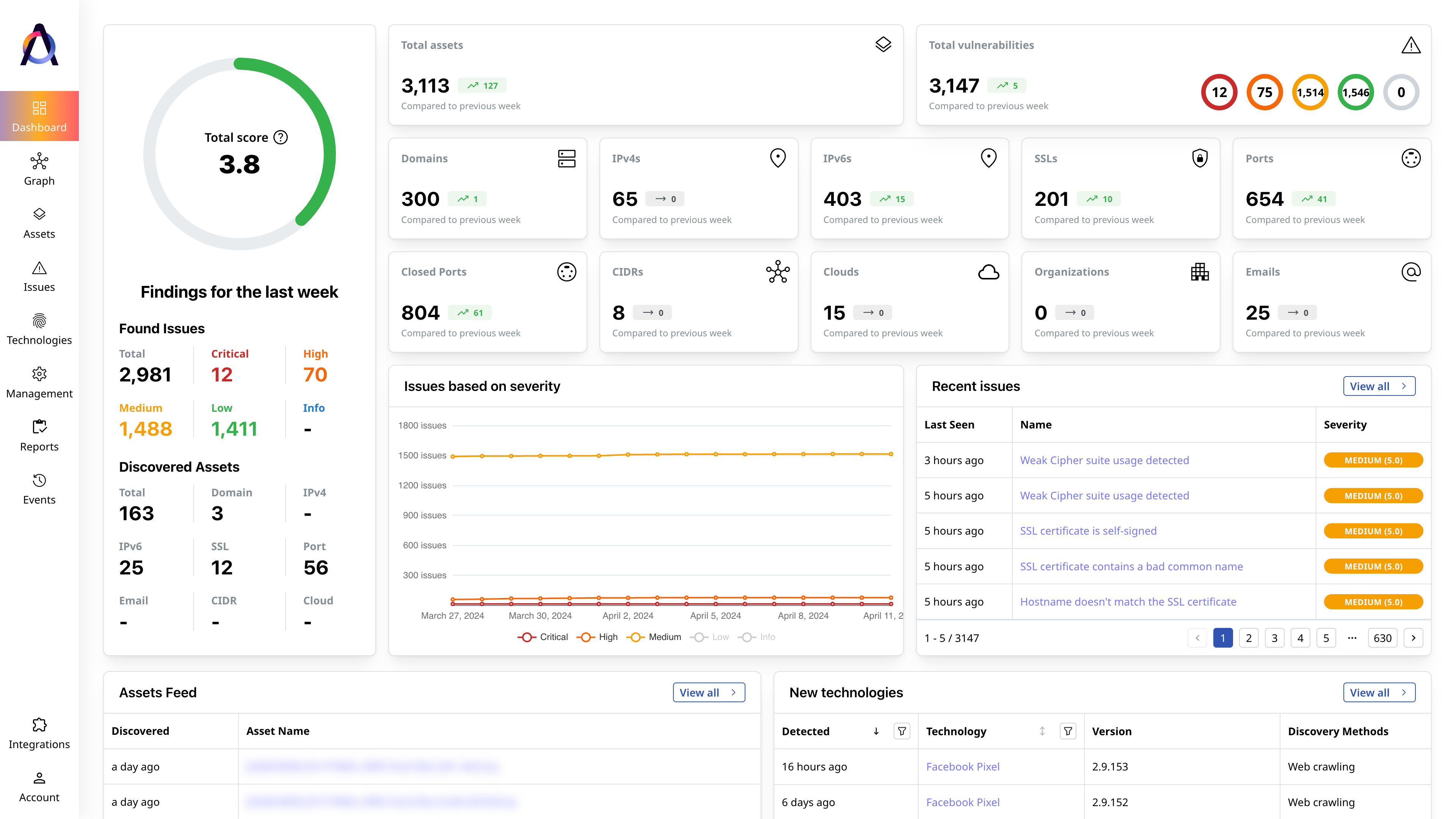
Monitor your overall risk
Manage the health of your whole public-facing infrastructure and its aggregated exposure to threats.
-
Superior Coverage
Discover twice as many assets and their security issues for more asset types.
-
Start Right Away
Jump into action—find and protect your vulnerable assets within hours.
-
Any Security Budget
Small or very large attack surface? Attaxion has the right pricing for you.
Our Monitoring Features
- ✅ Dynamic overview and scoring of the attack surface
- ✅ New findings for last 7, 30, 90 days
- ✅ Real-time new asset discovery
- ✅ Real-time new issue detection
- ✅ Remediation progress tracking
- ✅ Identification of new root asset candidates
- ✅ Alerts via email, Slack, and Jira
- ✅ Logging of all new events
What security experts say
Featured Resources

CWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like CWE, CVE, and CVSS. These term[...]

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

How to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sensitive information, or disrupt[...]