The sheer volume of potential attack vectors is staggering. In 2025 alone, 48,177 Common Vulnerabilities and Exposures (CVE) records were published — up by more than 20% compared to the previous year. Each of these CVE represents a possible crack in the digital wall that threat actors can exploit. This shows how important vulnerability assessments are. They are the first line of proactive defense against cyber threats.
In this post, we dove deep into the security process, tackling its benefits, challenges, common types, and essential steps.
What Is Vulnerability Assessment?
Vulnerability assessment identifies and evaluates security issues in digital systems and infrastructures that can potentially pave the way for cyber attacks. It is performed on both internal and external systems. However, this post focuses only on external vulnerability assessment—a critical part of the external attack surface management (EASM) process (i.e., a cybersecurity measure that aims to detect and tackle vulnerabilities before attackers can exploit them).
Vulnerability assessment usually involves scanning a target system for security weaknesses, misconfigurations, and vulnerabilities, such as those listed on MITRE’s Common Weakness Enumeration (CWE) and CVE lists.
Table of Contents
- Benefits of Vulnerability Assessment
- What Is Vulnerability Assessment Methodology?
- Key Steps in Vulnerability Assessment
- Vulnerability Assessment Checklist
- Common Types of Vulnerability Assessment
- Challenges in Vulnerability Assessment
- Vulnerability Assessment versus Penetration Testing versus Vulnerability Management
- Frequently Asked Questions
Benefits of Vulnerability Assessment
Vulnerability assessment offers several benefits that contribute towards providing organizations a clear understanding of their security posture. We talk more about these benefits below.
Faster Remediation of Vulnerabilities
Conducting regular and thorough vulnerability assessments enables organizations to proactively identify security weaknesses before attackers can find them. Since the assessment provides actionable details (e.g., location, affected assets, severity, and exploitability of vulnerabilities), security teams can immediately address them.
Risk Prioritization
Not all vulnerabilities are created equal, as some pose a greater threat than others. Vulnerability assessment is crucial for this reason. It identifies the most critical security flaws, effectively allowing security teams to prioritize risks and maximize limited human resources. Assessments answer questions, such as:
- How easily can a vulnerability get exploited?
- What will the potential impact be if it gets exploited?
- What systems will get affected?
- How fast can attackers reach sensitive information after exploiting the vulnerability?
- Which vulnerabilities should be addressed first?
Protect Sensitive Data and Limit Financial Implications
Vulnerability assessments play a critical role in safeguarding sensitive data, such as customer information, financial records, and intellectual property. And most people would agree that preventing a data breach is far more cost-effective than managing its aftermath. The €251-million fine imposed by the Irish Data Protection Commission (DPC) on Meta following a data breach is a glaring example.
Indeed, data breaches can lead to severe financial repercussions, including regulatory fines, legal fees, loss of customer trust, and reputational damage. And since vulnerability assessment can minimize these risks, why not take every available precaution?
Improve Incident Response Time
While vulnerability assessments aim to prevent breaches and other cyber attacks, residual risk (i.e., the portion of risk remaining after mitigation efforts) still exists. In other words, cyber events can still occur.
However, assessments can make organizations better prepared for attacks as they provide a thorough understanding of systems and their vulnerabilities. The information gathered during the assessment can help in developing faster and more effective incident response plans.
Regulatory Compliance
Many industries are subject to regulations that require organizations to protect sensitive data and maintain strong security practices. The General Data Protection Regulation (GDPR), for instance, mandates all organizations handling the personal data of European Union (EU) residents to adhere to strict data protection protocols. Vulnerability assessments are often a key initial step in meeting data privacy and cybersecurity compliance requirements.
What Is Vulnerability Assessment Methodology?
To reap all the benefits of vulnerability assessment we discussed above, organizations would need a structured approach by establishing a vulnerability assessment methodology. This methodology is the overall strategic plan that details the types of assessments to be performed, the tools to be used, and the risk assessment framework. It involves planning and reporting the findings, and in between these are some essential steps that we dive into in the next section.
Key Steps in Vulnerability Assessment
All types of vulnerability assessments roughly follow the same procedure that begins with asset discovery. Below are the phases of vulnerability assessment.
Asset Discovery and Evaluation
As a first step, you need to create an updated catalog of all your assets and determine which ones are critical to your operations. Part of this step is looking at the assets the way attackers would and assessing which ones they would find most attractive.
Vulnerability Scanning and Testing
After creating a catalog of all your assets and determining which ones are most critical to your day-to-day operations, vulnerability scanning ideally takes place. The most critical and attractive assets are scanned for security issues, such as information exposure (CWE 200), security misconfigurations, and Simple Network Management Protocol (SNMP) vulnerabilities.
To do this, security analysts use various automated tools that glean data from vulnerability databases, threat intelligence feeds, and other cyber intelligence sources.
However, scanning alone may not uncover all risks—including those that involve errors in an application’s design or complex attack chains where attackers combine multiple, seemingly minor vulnerabilities. This is where vulnerability testing comes in. Attack simulations, such as penetration testing, are conducted to further detect vulnerabilities that scanners may have overlooked.
Vulnerability Analysis and Prioritization
The next step digs deeper into the discovered vulnerabilities to remove false positives and identify which should be addressed first. Aside from pinpointing the source of the weakness (i.e., whether it is a coding error, a misconfiguration, or an outdated system component), analysts also determine the impact of an exploitation.
Based on these analysis, analysts then rank vulnerabilities, which entails asking questions like:
- What is the likelihood that threat actors will exploit the vulnerability? The Exploit Prediction Scoring System (EPSS) can help answer this as the vulnerability scoring system is designed to predict the likelihood of exploitation.
- Are these vulnerabilities being actively exploited in the wild? Taking into account the Known Exploited Vulnerabilities (KEV) Catalog maintained by the Cybersecurity and Infrastructure Security Agency (CISA) enables security teams to see which vulnerabilities have already been exploited.
- How critical is the affected system? No scoring method will be able to fully answer this question for you. The criticality of a system depends on your business context, bringing us back to the importance of having a complete and contextualized asset inventory.
In certain cases, security analysts may need to manually verify if the vulnerability detected is indeed a real problem, helping ensure resources are not wasted on false alarms.
Remediation Plan Creation
At this stage, analysts translate the findings into a concrete plan that outlines the resources required for remediation, timeline, and technical details of each vulnerability. For example, if a vulnerability assessment identifies a critical issue in an organization’s web server due to an outdated version of Apache, the remediation plan could include:
- Vulnerability: The specific CVE ID, if applicable
- Affected systems: Web server and other applications running on the outdated Apache
- Severity level: High
- Recommended action: Specific implementation steps instructing the IT team to update to the latest Apache version, including the exact command line steps or GUI configurations
- Remediation timeline: Within 2 weeks
- Responsible parties:
- System administrators will deploy the correct update and security patches
- IT security team will monitor the affected systems for vulnerabilities
Vulnerability Assessment Report Creation
All steps previously mentioned should be documented in a vulnerability assessment report. This report contains a detailed list of all the vulnerabilities identified, organized by system or application, with their severity, potential impact, and recommended remediation steps.
Continuous Assessment
The previous five steps in vulnerability assessment are not one-time activities. They must be done regularly, especially since new vulnerabilities emerge all the time. That said, automated vulnerability scans should be conducted frequently. EASM and other security tools must continuously monitor systems for weaknesses, suspicious activities, and potential attacks.
Vulnerability Assessment Checklist
Everything described above can be a handful and prone to mistakes if you rely on memory — there’s always a possibility that you might miss a server or skip a critical configuration check. A security vulnerability assessment checklist solves this problem. It serves as a roadmap to ensure your team follows the same process every time.
Different assessments require different checklists, so there’s no one correct checklist, the most complete checklist, or anything like that. You’ll need to create your own, most likely, but what we can do here to help is provide some ideas and examples.
Many vulnerability assessment checklists use a Yes/No format to force the person performing the assessment to give a clear answer. This makes it much easier to track progress and report to leadership.
The content of the checklist is usually based on established security standards. These frameworks provide a list of known best practices that serve as a foundation for the checklist.
- National Institute of Standards and Technology (NIST): The NIST Cybersecurity Framework is a federal guideline that many large corporations use to meet high security standards.
- Center for Internet Security (CIS) Benchmarks: CIS Benchmarks provide specific settings for hardware and software to ensure they are hardened against attacks.
- Open Web Application Security Project (OWASP): OWASP provides guidance on web application security, focusing on risks like SQL injection or broken authentication.
While these standards are great, a good checklist is also unique to the business. The New York State Department of Health, for instance, has a 15-page checklist specifically for public water systems. Some people are even selling vulnerability assessment checklists targeted at specific industries, such as this checklist for schools.
Still, it’s best to customize the checklist to your organization’s specific needs. A bank might add extra steps for its ATM network, while an e-commerce company might focus more on the specific third-party vendors it uses.
Regardless of the industry, however, a vulnerability assessment checklist is commonly broken down into three parts: pre-assessment, assessment, and post-assessment.
Phase 1: Preparation and Scoping (Pre-Assessment)
- Define the boundary. Determine which IP addresses, applications, and cloud environments are part of the test.
- Update your inventory. Ensure your list includes all physical hardware and virtual machines.
- Get permissions. Confirm that stakeholders know when the scan will happen. This prevents false alarms for the IT team.
Phase 2: Discovery and Scanning (Assessment)
- Run discovery scans. Look for unknown devices or shadow IT services running on the network.
- Perform credentialed scans. Log in to systems to find deep-level vulnerabilities that a basic scan might miss.
- Check for misconfigurations. Look for default passwords, unencrypted traffic, or open ports that should be closed.
Phase 3: Vulnerability Analysis and Remediation (Post-Assessment)
- Filter the results. Review the report to find and remove false positives.
- Rank by risk. Use a scoring system like Common Vulnerability Scoring System (CVSS) or EPSS to decide which holes to address first.
- Create a remediation plan. Assign tasks to the right teams. Set deadlines for when the patches must be finished.
- Verify the work. Run a new scan to make sure the security vulnerabilities are gone.
Example of a Vulnerability Assessment Checklist
Here are a few examples of generic questions that might be on a vulnerability assessment checklist.
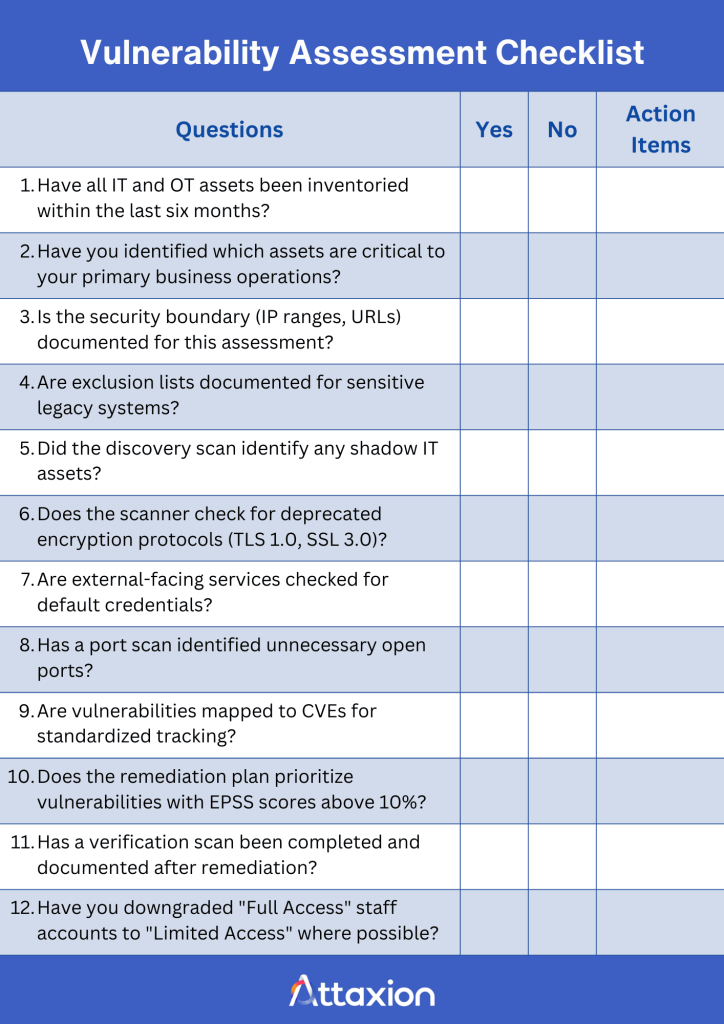
Common Types of Vulnerability Assessment
Vulnerability assessments are categorized based on the target system or infrastructure component being tested. Each type may require using specialized tools and solutions. We’ll discuss some of the most common types of vulnerability assessment in greater detail below, but here’s a table that provides a quick differentiation.
| Type of Assessment | Target System | Commonly Used Tools |
| Network-based vulnerability assessment | Network devices and infrastructures | – EASM – Network vulnerability scanners Penetration testing tools |
| Application vulnerability assessment | Web applications and software | – EASM – Dynamic application security testing (DAST) tools – Web vulnerability scanners |
| Database vulnerability assessment | Databases | – Data security solutions – Structured Query Language (SQL) auditing tools |
| Host-based assessment | Hosts (e.g., servers and workstations) | – Endpoint detection and response (EDR) solutions – Agent-based vulnerability scanners |
Network-Based Vulnerability Assessment
This type of vulnerability assessment focuses on identifying open ports, outdated software, and other weak points in network devices and infrastructures, including Internet-facing firewalls and DNS configurations.
Application Vulnerability Assessment
This assessment aims to detect vulnerabilities in software and web applications that can give way to common web application attacks, including denial-of-service (DoS) and brute-force attacks. These attacks can allow threat actors access to financial data, login credentials, and other sensitive information.
Database Vulnerability Assessment
This type of assessment specifically targets databases, which often contain highly sensitive information. Assessments aim to identify weaknesses in the database system that can get exploited to compromise the data it contains. A database vulnerability assessment looks for issues like missing patches, weak credentials, misconfigurations, weak data encryption, and other vulnerabilities.
Host-Based Assessment
A host-based vulnerability assessment focuses on individual systems or “hosts,” such as servers, workstations, laptops, and mobile devices. It examines the security posture of these individual machines, looking for vulnerabilities within the operating system (OS), applications, and configurations.
Challenges in Vulnerability Assessment
While vulnerability assessments help organizations level the playing field against adversaries, it is not without challenges. Some of the most common hurdles in conducting assessments are false positives, evolving threats, and collaboration between different teams.
Managing False Positives
False positives are a major headache in vulnerability assessment. They occur when a vulnerability scanner flags an issue that is not a real threat, consequently wasting valuable time and resources spent in investigating them.
False positives may also result in alert fatigue that can cause analysts to ignore alerts and potentially miss critical threats. As such, it’s crucial to choose vulnerability assessment tools and solutions that deliver minimal false positives, typically those that integrate contextual analysis into detection algorithms.
Adapting to Evolving Threats
New vulnerabilities and attack techniques emerge all the time, making it difficult to keep vulnerability assessments up-to-date. For example, vulnerability assessment tools will generally not be able to detect zero-day vulnerabilities since these are exploited before they are even discovered.
On top of that, organizations constantly deploy new technologies and systems. These necessary business activities inevitably expand the attack surface, which vulnerability assessments must account for.
Automating vulnerability assessment and integrating threat intelligence into solutions can help security teams improve their efficiency in detecting and assessing emerging threats.
Ensuring Cross-Functional Collaboration
Vulnerability assessments require cooperation between different teams within an organization, including personnel in security, IT development, and management. These teams typically have different priorities so it may be difficult to agree on remediation timelines and resource allocation.
For instance, development teams may prioritize speed and functionality to meet deadlines and market demands. Meanwhile, security teams may prefer to launch secure products even if that involves some delays.
Aside from providing training on vulnerability assessment and remediation best practices, one way to overcome this challenge is to establish clear communication channels and collaboration processes between different teams.
Vulnerability Assessment versus Penetration Testing versus Vulnerability Management
Vulnerability assessment, penetration testing, and vulnerability management are all cybersecurity processes that serve distinct purposes. Here’s a TL;DR version of their differences.
| Vulnerability Assessment | Penetration Testing | Vulnerability Management | |
| Focus | Identify security weaknesses in systems, applications, and networks | Simulate real-world attacks to exploit vulnerabilities | Continuously monitor, assess, and remediate vulnerabilities |
| Scope | Broad coverage of assets and infrastructures | Focused attack simulations on specific systems | Comprehensive life cycle approach to vulnerabilities |
| Methodology | Automated scanning and analysis with manual validation | Manual testing with ethical hacking techniques | Continuous risk assessment and remediation |
| Common tools used | – Application scanners – EASM platforms – Network scanners – Vulnerability scanners | – Exploitation tools – Network analysis tools – Social engineering tools – Web application testing tools | – EASM platforms – Patch management systems – Vulnerability risk management platforms – Ticketing or workflow systems |
Vulnerability assessment aims to find potential problems and provide an overview of an organization’s security posture. It focuses on identifying vulnerabilities using both automated tools and manual reviews. Assessments are broad and cover a wide range of assets.
On the other hand, penetration testing has a narrower scope as it targets specific systems. It aims to determine if vulnerabilities can be exploited through attack simulations using real-word attack methods.
Vulnerability management encompasses vulnerability assessment, penetration testing, and other related activities. The goal is to proactively manage and reduce an organization’s overall vulnerability risks through a continuous cycle of vulnerability scanning, assessment, remediation, and reporting.
—
Vulnerability assessment is among the most important cybersecurity processes to help ward off cyber attacks, especially since more than 220,000 CVEs and CWEs affect widely used software, applications, and systems today.
Learn how Attaxion can help you stay ahead of attackers with a comprehensive vulnerability assessment methodology. Start your free trial now.
Frequently Asked Questions
What Are The Different Types of Vulnerability Assessment Tools?
Some examples of vulnerability assessment tools include EASM, DAST, data security solutions, EDR solutions, network vulnerability scanners, penetration testing tools, SQL auditing tools, vulnerability scanners, and web vulnerability scanners.
Each tool has distinct purposes and use cases, so ultimately, the choice depends on the type of assessment you seek and the system(s) being targeted.
What Types of Threats Does Vulnerability Assessment Find?
A vulnerability assessment typically discovers known CVEs, CWEs, security misconfigurations, missing patches, weak passwords, and other vulnerabilities that expose organizations to threats, such as:
- SQL injection: This attack allows an attacker to inject malicious SQL code into a web application to gain access to a database.
- Cross-site scripting (XSS): This attack allows an attacker to place malicious scripts into a website, which can then steal user data or perform other malicious actions. Some vulnerabilities allow attackers to bypass authentication methods and gain unauthorized access to a system.
- Broken authentication: Weaknesses in authentication can make it easier for attackers to crack passwords.
- Sensitive data exposure: Some vulnerabilities may expose sensitive data, such as credit card numbers and personal information.
What Are Some Vulnerability Assessment Best Practices?
An effective vulnerability assessment program is crucial to proactively identify and mitigate security risks. Here’s a curated list of best practices in the context of EASM.
- Continuous asset discovery and inventory: Organizations typically implement automated and nonstop asset discovery to regularly identify all hardware, software, cloud instances, IoT devices, and other IT assets. The key to effectively doing this is to address visibility challenges—specifically those involving cloud and shadow assets—by using tools that can discover assets across different technologies and cloud service providers.
- Asset inventory enrichment: Since a plain list of assets is not enough, it is crucial to enrich the catalog with contextual information (e.g., business criticality, data sensitivity, location, and software versions). These details are important factors that can affect prioritization.
- Vulnerability scanning prioritization: While scanning all systems and applications is necessary, critical systems must be scanned more frequently than others. These could include databases containing sensitive client information, servers hosting critical operations, and other systems that, if compromised, may lead to severe consequences.
- Vulnerability prioritization and risk management: The most widely used risk-scoring method is probably the Common Vulnerability Scoring System (CVSS), which assigns a score of 0 to 10 to vulnerabilities based on their impact and exploitability. While CVSS scores are important, it’s also wise to use a combination of risk-scoring standards and methods to account for your organization’s specific context and risk mitigation strategies.
- Actionable remediation plan: Develop a well-defined remediation process that covers patching, configuration changes, mitigations, and compensating controls. It should also detail the team members responsible for each remediation task so they understand their responsibilities better. After remediation, rescan systems to ensure the vulnerabilities have been effectively addressed.
- Clear reporting and communication: Create vulnerability assessment reports that are concise and easy to understand. Include executive summaries that highlight key findings and their potential impact on the business. The report should also provide detailed information about each vulnerability (e.g., description, severity, affected assets, and remediation recommendations). In addition, an overview of key metrics, such as the number of open vulnerabilities and time to remediation, can help communicate an organization’s security posture more effectively.

