Building customer trust takes a lot of hard work, and a single security incident can jeopardize it all. In fact, IBM’s Cost of a Data Breach Report 2023 pegged the cost of reputation loss, diminished goodwill, and other contributors to lost business due to a data breach at US$1.3 million.
While there’s no silver bullet to completely eradicate risks and minimize attack surfaces, there are frameworks that help organizations manage them. The International Organization for Standardization (ISO) developed several standards that allow businesses to adopt proactive risk management measures, reduce operational downtime, increase overall business performance, and enhance reputation.
In this post, we will focus on best practices to achieve ISO/IEC 27001 certification, which demonstrates an organization’s strong commitment to information security. Compliance with this standard can significantly boost customer confidence and trust in an organization’s ability to handle sensitive data, a major differentiator in competitive markets.
What Is ISO 27001?
The ISO/IEC 27001 standard provides a framework for organizations to build a robust information security management system (ISMS), published by the ISO and the International Electrotechnical Commission (IEC). It was last updated in 2022, hence the name “ISO 27001:2022.”
An organization that is ISO/IEC 27001-certified assures clients and business partners that its IT infrastructure meets international standards, thus helping raise customer trust. That is because ISO/IEC 27001 guides organizations through risk assessment, risk management, and continuous improvement with the ultimate goal of safeguarding valuable information.
Its companion standard, ISO/IEC 27005, assists organizations in fulfilling the requirements of ISO/IEC 27001, specifically in addressing information security risks.
From ISO 27001 to Managing Your Risks and External Attack Surface
Risk assessment and management are important aspects of ISO/IEC 27001, prompting organizations to evaluate their assets and vulnerabilities systematically. Below are some of the key activities relevant to this standard, most of which can be conducted with external attack surface management (EASM) capabilities.
Asset Discovery
Advanced asset discovery methods enable organizations to see beyond what they know, enabling them to detect the growing usage of unsanctioned or shadow IT assets. And since the number of assets continuously rises as business operations continue and expand, asset discovery is a continuous process.
As part of this activity, it’s essential to make a complete and ongoing list of all assets across your organization, including external assets in the form of domains, subdomains, IP addresses, and cloud instances, that are detectable through EASM.
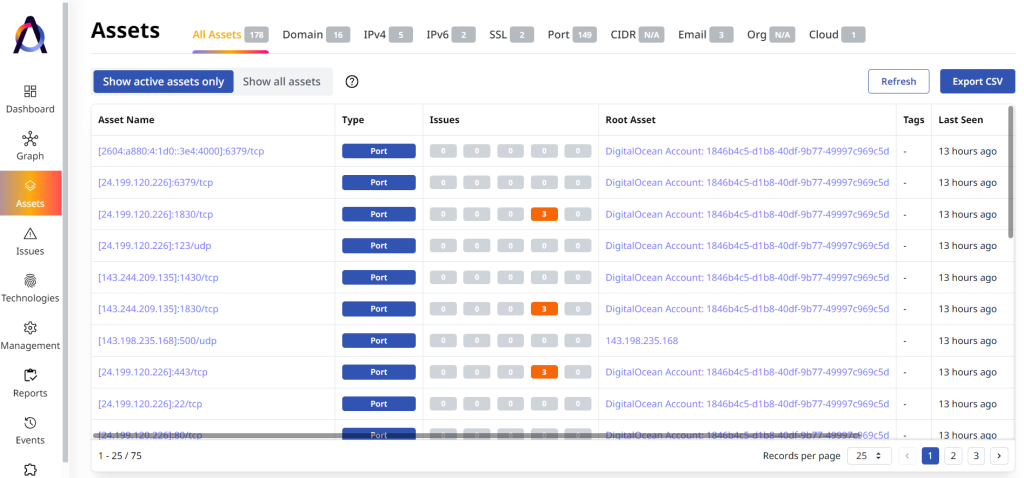
Additionally, information about the Secure Sockets Layer (SSL) and other certificates associated with your domains and subdomains can be valuable for identifying potential vulnerabilities.
Risk Identification
Once organizations have identified all of their assets, they need to determine the threats attached to each. That involves scanning the assets for security misconfigurations, weaknesses, and vulnerabilities.
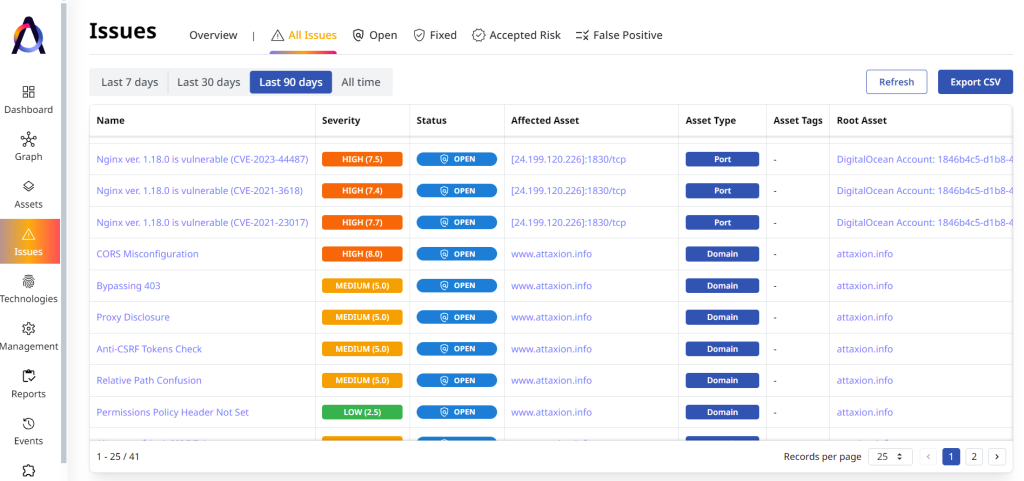
Like asset discovery, risk identification is a never-ending process. It takes into account new vulnerabilities, emerging threats, and new exploits that threat actors leverage. This is a crucial step, especially since as many as 612 new common vulnerabilities and exposures (CVEs) can be detected weekly.
Risk Analysis
The next step is to analyze each risk’s impact and likelihood of occurrence. Manually doing so can take up time and resources, so automation is paramount.
While ISO/IEC 27001 doesn’t dictate a specific risk scoring and analysis method, the Common Vulnerability Scoring System (CVSS) is commonly used. CVSS is an industry-standard method for assessing the severity of software vulnerabilities, taking into account various exploitability (e.g., the attacker’s required skill level and availability of exploit code) and impact metrics (e.g., impact on data confidentiality, integrity, and system availability).
Automated vulnerability scanners, such as those that are part of EASM capabilities, would then rank vulnerabilities based on their CVSS scores using qualitative severity ratings like low, medium, high, and critical.
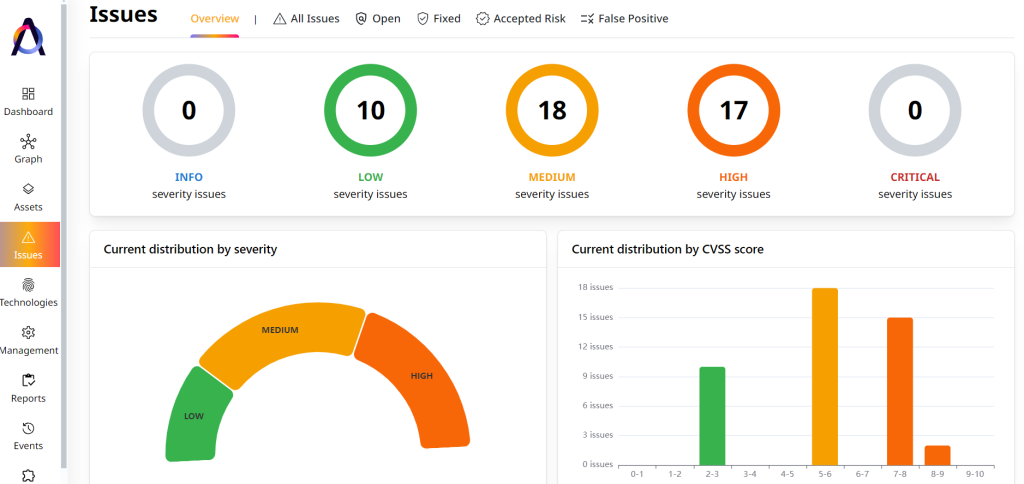
Risk Assignment
After determining severity levels, organizations can start assigning the identified risks to various members who would be responsible for addressing each issue. Attributing ownership allows creating a proactive approach to security and ensuring that no critical issues will fall through the cracks.
Risk assignment can be done within the EASM platform through integration with commonly used project management systems, helping smoothen communication and collaboration.
Risk Treatment Plan
Different risks require different approaches. Depending on their severity, risks can be addressed in various ways.
- Risk acceptance: This strategy is suitable for low-level risks or those where the cost of mitigation outweighs the potential impact. For example, a minor vulnerability in a rarely used internal system may be deemed acceptable after considering the cost or workload of patching it.
- Risk reduction: As the most common approach, risk reduction involves taking steps to mitigate the likelihood or impact of a risk (e.g., implementing security controls, deploying patches, or conducting security awareness training for employees). The goal is to make the risk less severe, even if it cannot be entirely eliminated.
- Risk remediation or avoidance: This is the ideal scenario where organizations can completely remediate or avoid the risk altogether. For example, they may disable unnecessary functionalities or eliminate outdated systems.
- Risk sharing: Since some risks are unavoidable, another approach is to transfer some of their potential financial impact to another party, typically through cyber insurance. In the event of a cyber attack, the insurance policy would cover some or all of the associated costs, such as data recovery or regulatory fines.
Risk Monitoring
The risk management process isn’t a one-time event. The final step requires organizations to monitor the effectiveness of implemented controls continuously. Risk monitoring is crucial because cyber threats constantly evolve. Regular monitoring helps identify if existing controls are still adequate in the face of new vulnerabilities and attack tactics.
In addition, an organization’s IT infrastructure, assets, and attack surface will likely change over time. New systems are added, applications are updated, and employee roles evolve. Monitoring ensures controls remain aligned with its current security posture and address newly introduced risks.
Conclusion
ISO/IEC 27001 is a widely recognized international standard, with more than 70,000 certificates reported in 150 countries for organizations across all sectors. Compliance with this standard requires a thorough approach to risk management, which showcases an organization’s dedication to protecting sensitive information and helps reinforce customer trust.
Support ISO/IEC 27001 compliance with comprehensive risk management aided by EASM capabilities. Start your free trial now to see how Attaxion can help.

