No entity across industries and regions is safe from cyber attacks. The European Union (EU) Agency for Cybersecurity (ENISA) annual Threat Landscape Report analyzed thousands of security incidents targeting public administration offices (19%), individuals (11%), the health sector (8%), digital infrastructure (7%), and digital service providers (6%), to name a few. The ENISA report also recorded 24,690 new vulnerabilities from 1 July 2022 to 30 June 2023.
The increasing number of attacks, made possible by numerous vulnerabilities, prompted lawmakers to act. Among the resulting initiatives is the Network and Information Systems (NIS) Directive, introduced in 2016 and updated in 2023 in the form of NIS 2. Member states must formally adopt and make public the measures essential for adhering to the NIS 2 Directive before 17 October 2024, and apply them by 18 October 2024.
What Is NIS 2?
NIS 2 is an updated version of the original NIS Directive, an EU legislation that aims to boost cybersecurity across member states. NIS 2 requires entities within member states to take appropriate steps to secure their digital infrastructure, which should include at least the following:
- Risk analysis and information system security
- Incident handling
- Business continuity
- Supply chain security
- Security in network and information systems acquisition, development, and maintenance, including vulnerability handling and disclosure
- Cybersecurity risk management assessment
- Basic cyber hygiene practices and cybersecurity training
- Policies and procedures regarding the use of cryptography and encryption
- Human resource security, access control policies, and asset management
- Use of multifactor authentication (MFA) or continuous authentication solutions
These requirements mean companies would need to have cybersecurity strategies in place, notably related to:
- Asset management: Keeping track of all IT assets and ensuring they are properly secured.
- Risk analysis: Identifying potential threats and vulnerabilities to systems and data and creating policies to mitigate risks.
- Incident response plan: Having a plan to detect, respond to, and recover from cyber attacks.
What Are the Main Updates Introduced with NIS 2?
The main changes to the directive that entities within the EU must take note of are:
- Broader scope: Previously, only operators of essential services (OESs) like energy or transportation had strict cybersecurity rules. Now, medium-sized and large entities in those sectors and those providing related services must also comply. They could include companies that support critical infrastructure or provide essential services online.
- Stronger risk and incident management and cooperation: Better incident management and cooperation is emphasized. That means having a response plan for cyber attacks, reporting them promptly, and potentially collaborating with authorities for coordinated responses.
- New essential and important entities category: The directive now includes “essential” (e.g., organizations previously classified as OESs, such as operators of district heating or cooling, energy distribution system operators, air carriers, credit institutions, postal service providers, and DNS service providers) and “important” entities (i.e., organizations that do not qualify as essential entities but play a vital role in critical sectors).
- Executive accountability: Company executives may be liable for incidents if they’re deemed responsible for a violation.
What Dates Should You Remember?
Member states must adopt and publish the measures necessary to comply with the NIS 2 Directive before 17 October 2024, and apply them by 18 October 2024.
By 17 January 2025, each member state must report to the European Commission regarding the specific penalties it has chosen for noncompliance and how it plans to enforce said penalties.
Member states are also required to report future changes they make to their national NIS 2 implementations to keep the commission informed about how the directive is being applied in practice.
What Are the Penalties for Noncompliance?
Specific penalties may vary depending on the member state an organization operates in, but NIS 2 sets out general guidelines for imposing administrative fines. The penalties should be strong enough to deter companies from breaking the rules but also be fair and scaled to the severity of a violation. Financial penalties can amount to:
- €10 million or 2% of the global annual revenue of essential entities
- €7 million or 1.4% of the global annual revenue of important entities
In addition to fines, some member states may implement other penalties, such as temporary suspension of certifications or authorizations and temporary barring of executives.
What You Can Do
NIS 2 recognizes that traditional IT infrastructure is no longer threat actors’ sole target. It broadens the scope to include new technologies and sectors, forcing organizations to consider their entire attack surface, including their public-facing environments.
As an external attack surface management (EASM) platform, here’s how Attaxion can support your NIS 2 compliance needs.
Asset Discovery and Inventory
NIS 2 demands a comprehensive understanding of your attack surface, mandating that a member state’s computer security incident response team (CSIRT) must have the ability to monitor Internet-facing assets to detect their vulnerabilities upon an entity’s request.
To comply, organizations must go beyond traditional asset discovery methods to identify all their external assets, including domain names, subdomains, Secure Sockets Layer (SSL) certificates, IP addresses, ports, cloud instances, and software-as-a-service (SaaS) technologies. A centralized inventory to track and manage all assets in one dashboard can help ensure that nothing gets overlooked.
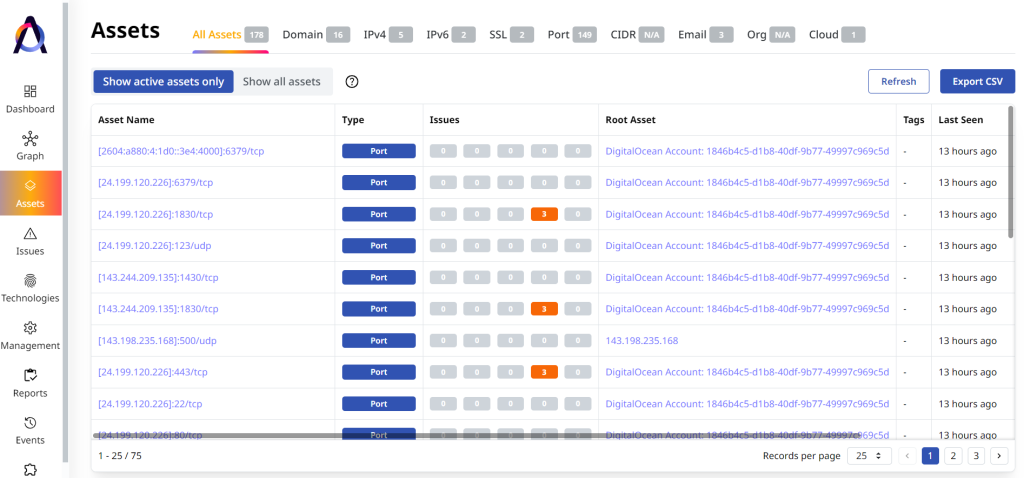
Automated and Regular Vulnerability Scanning
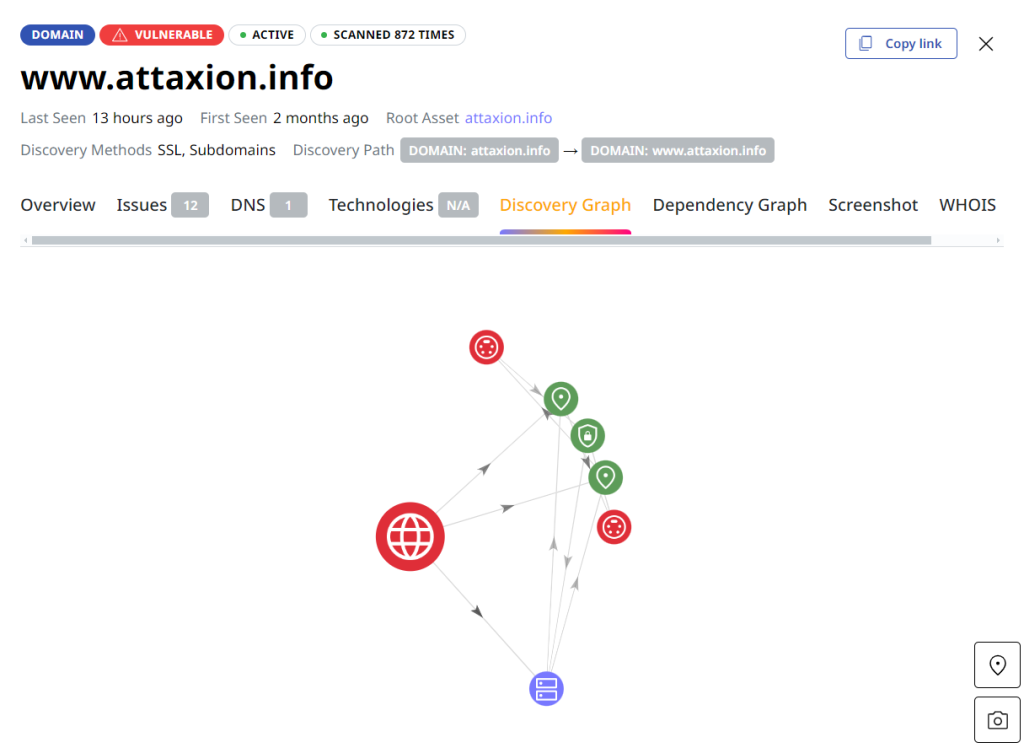
The NIS 2 Directive requires organizations to regularly identify and address weaknesses in systems through proactive and unintrusive vulnerability scans. Attaxion offers automated vulnerability scanning capabilities that can help meet this requirement by:
- Scanning systems regularly: Automatically scan your network and information systems for potential vulnerabilities ongoingly.
- Minimizing disruption: These scans won’t disrupt daily operations.
- Assessing vulnerabilities: Obtain clear insights into the vulnerabilities identified, including asset dependencies and discovery paths, and recommended mitigation methods.
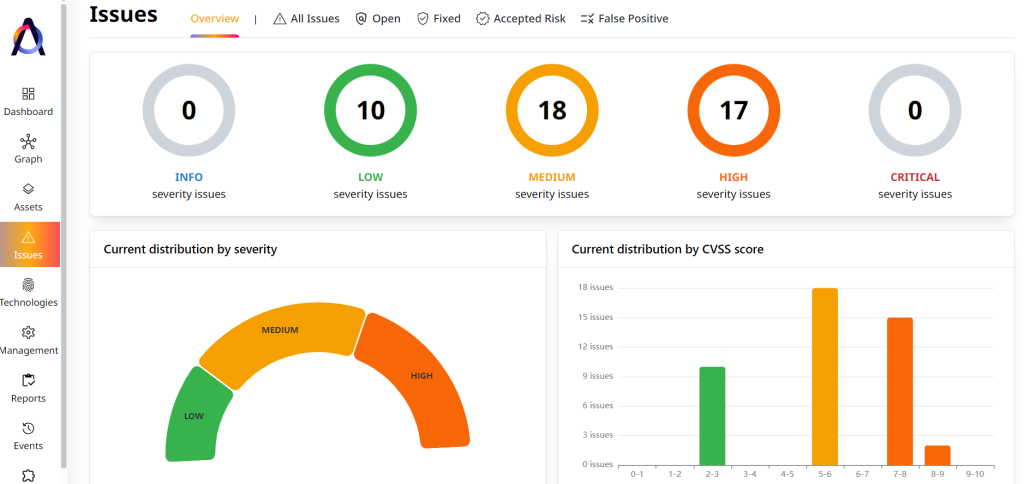
Risk-Based Prioritization
Member states are required to adopt a risk-based approach to monitoring entities within their countries, frequently and rigorously checking up on high-risk entities. In the same way, essential and important entities would need to implement a risk-based vulnerability management approach. That means focusing their efforts on the areas that pose the biggest threat first.
Attaxion can help by enabling organizations to classify assets and prioritize vulnerabilities based on severity. The vulnerabilities are ranked based on their Common Vulnerability Scoring System (CVSS) scores expressed in qualitative ratings (i.e., low, medium, high, and critical).
Conclusion
While the initial implementation of NIS 2 may require significant effort, the long-term security benefits are also expected to be important. Organizations across the EU will have a stronger foundation for cybersecurity, leading to fewer data breaches and improved security posture. For regulators, NIS 2 represents a significant step toward a more harmonized and robust cybersecurity environment within the EU.
Learn how our EASM platform can support your NIS 2 compliance requirements. Kick off your 30-day free trial with Attaxion today.

