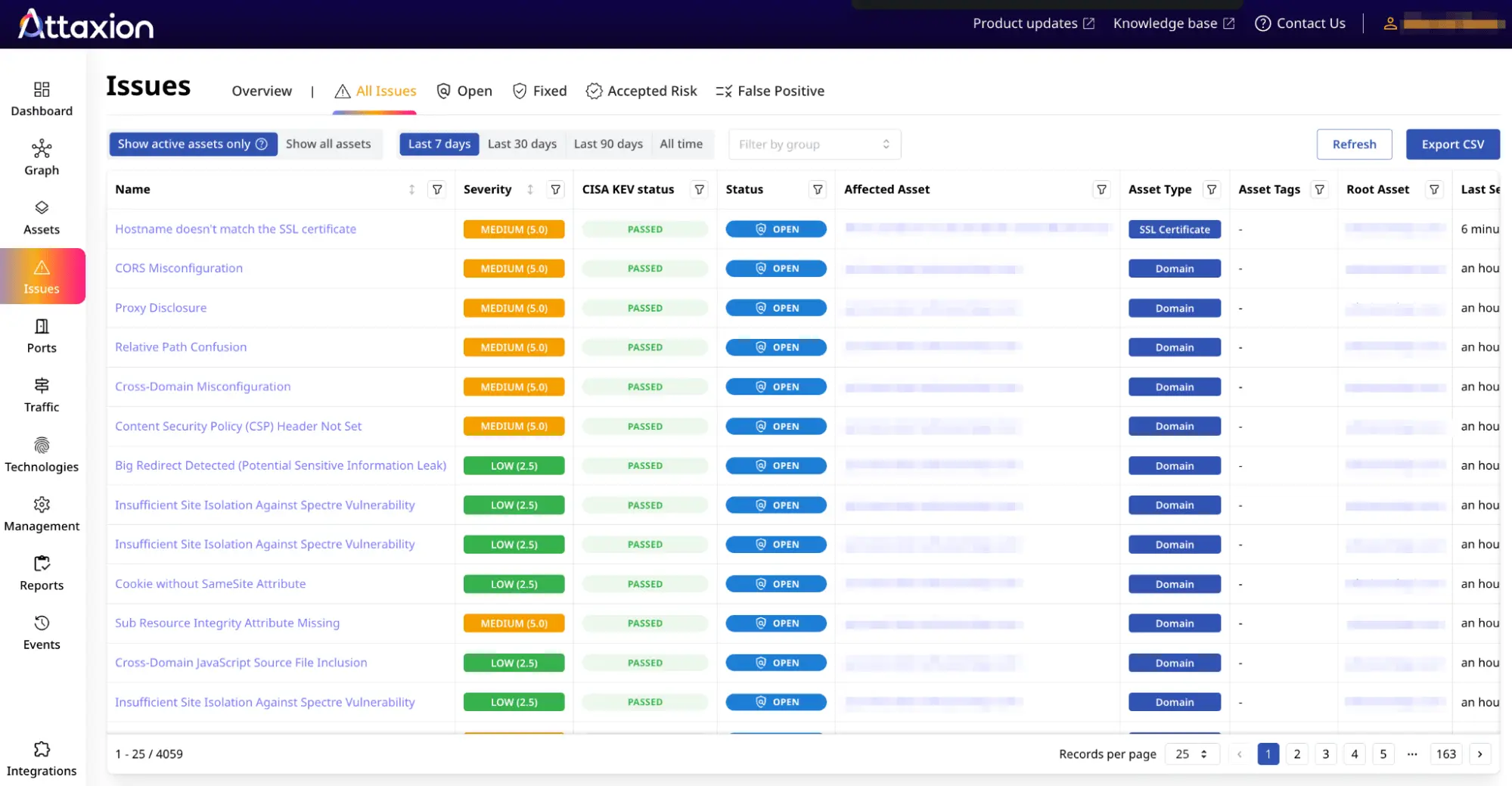
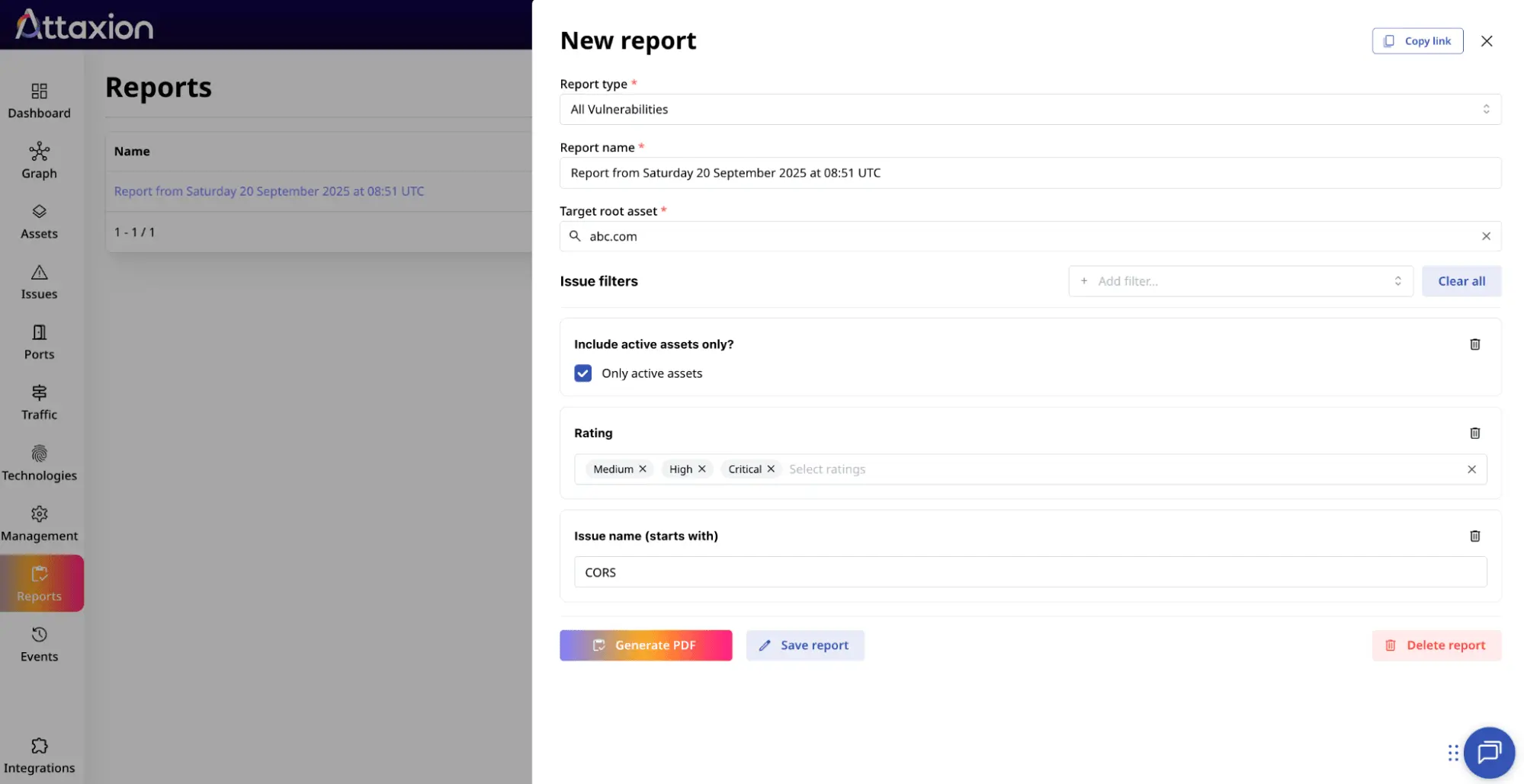
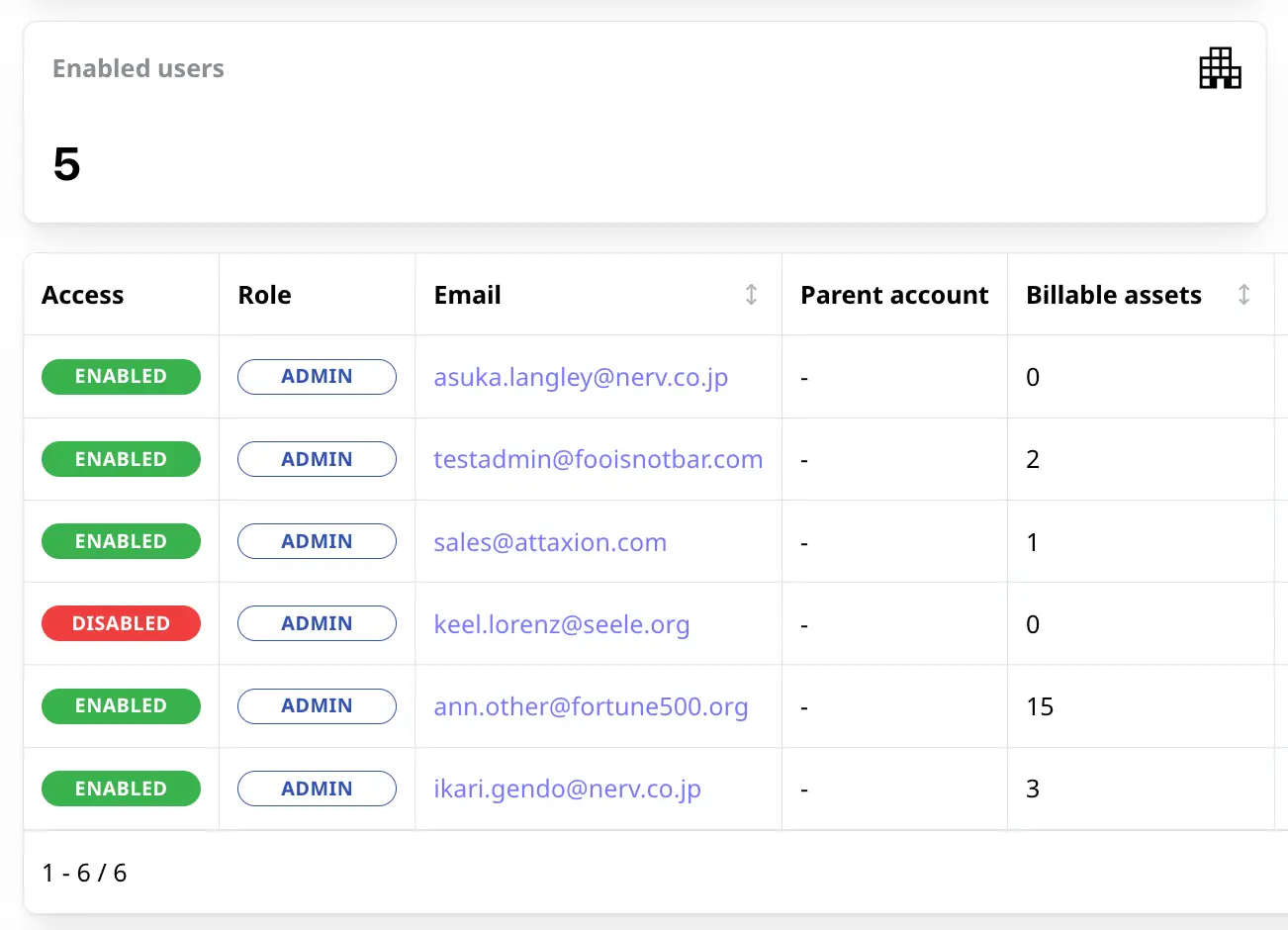
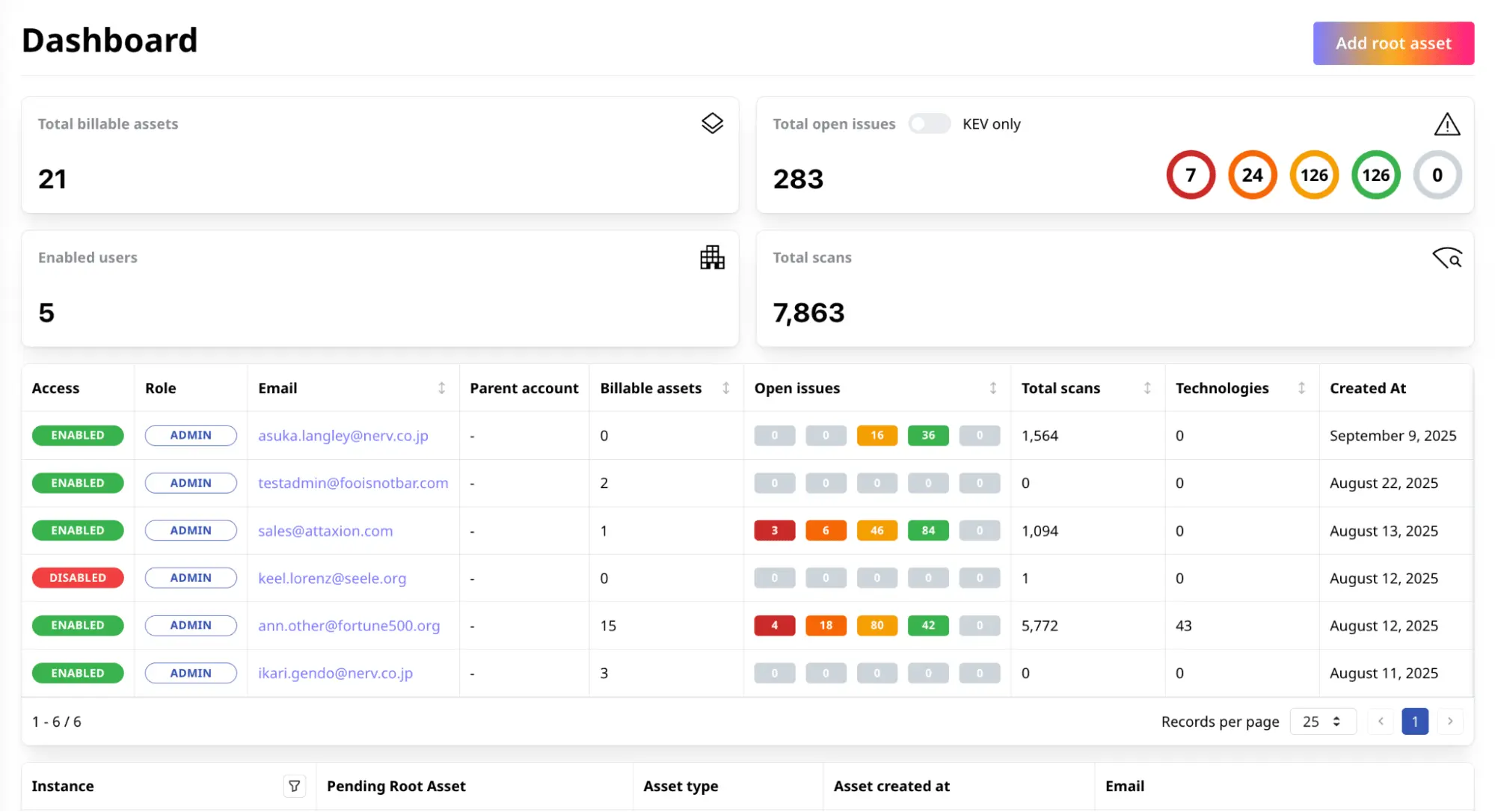
Partnership for IT security service providers and resellers
Partnership for IT security service providers and resellers
MSP/MSSP and Partner Program
Get full visibility into your customers’ external attack surfaces, reduce exposures, and scale your revenue with high margins and exclusive partner discounts.
Our Partners


-
Better security for your clients
Offer your customers full visibility into their external attack surfaces.
-
Get more customers
Use Attaxion’s findings to show your prospects the value you can provide.
-
New revenue opportunities
Scale together with your customers and increase your margins.
Partner programs for every model
Attaxion teams up with a wide range of channel partners, MSPs/MSSPs, and resellers. Become a part of our Partner Program and add a new steady stream of recurring revenue while getting the needed help through technical training, marketing collaterals, and more.
High margins
Add a steady stream of revenue, while improving your customers’ security posture.
Protect 1 customer or 100
Start as small as you need and scale as big as you need – with its transparent and flexible pricing, Attaxion is a great fit for your clients, no matter their size.
Flexible multi-tenant architecture
Attaxion is built for MSPs and MSSPs, allowing you to easily manage multiple workspaces, create dedicated instances for each customer, define roles, adjust access permissions, and clearly see costs per customer.
Quick customer onboarding
Initial setup takes just a few minutes. Attaxion partners can verify root assets with one click to provide value to customers and prospects without having to go through tedious verification processes.
Multiple use cases, one platform
Exposure management, external attack surface management, vulnerability management, M&A risk assessment – Attaxion enables you to do all of that and more.
What our clients say
Frequently asked questions
Featured Resources

Detecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the reason can be a security weaknes[...]

NIS 2 Compliance: From Asset Discovery to Risk Management
No entity across industries and regions is safe from cyber attacks. The European Union (EU) Agency for Cybersecurity (ENISA) annual Threat Landscape R[...]

Overcoming the Top SOC Challenges with EASM
A day in the life of a security operations center (SOC) analyst likely involves sifting through mountains of data and alerts, searching for clues that[...]