Enhance Shadow IT Visibility
Identify shadow IT assets and technologies to effectively manage your real attack surface.
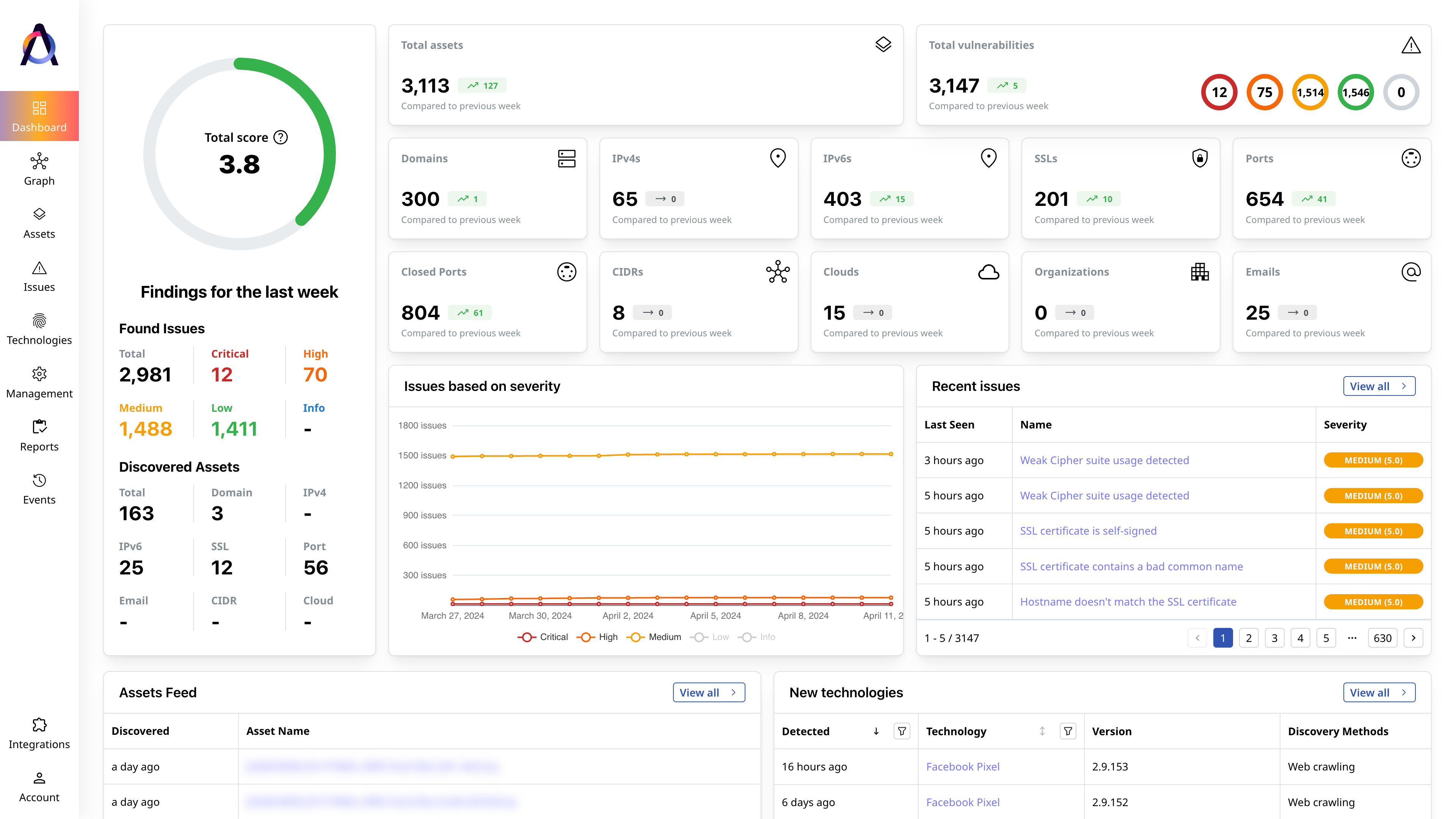
Detect forgotten and unsanctioned assets
Find all your public-facing assets, including hidden and non-compliant cloud resources and other forms of shadow IT.
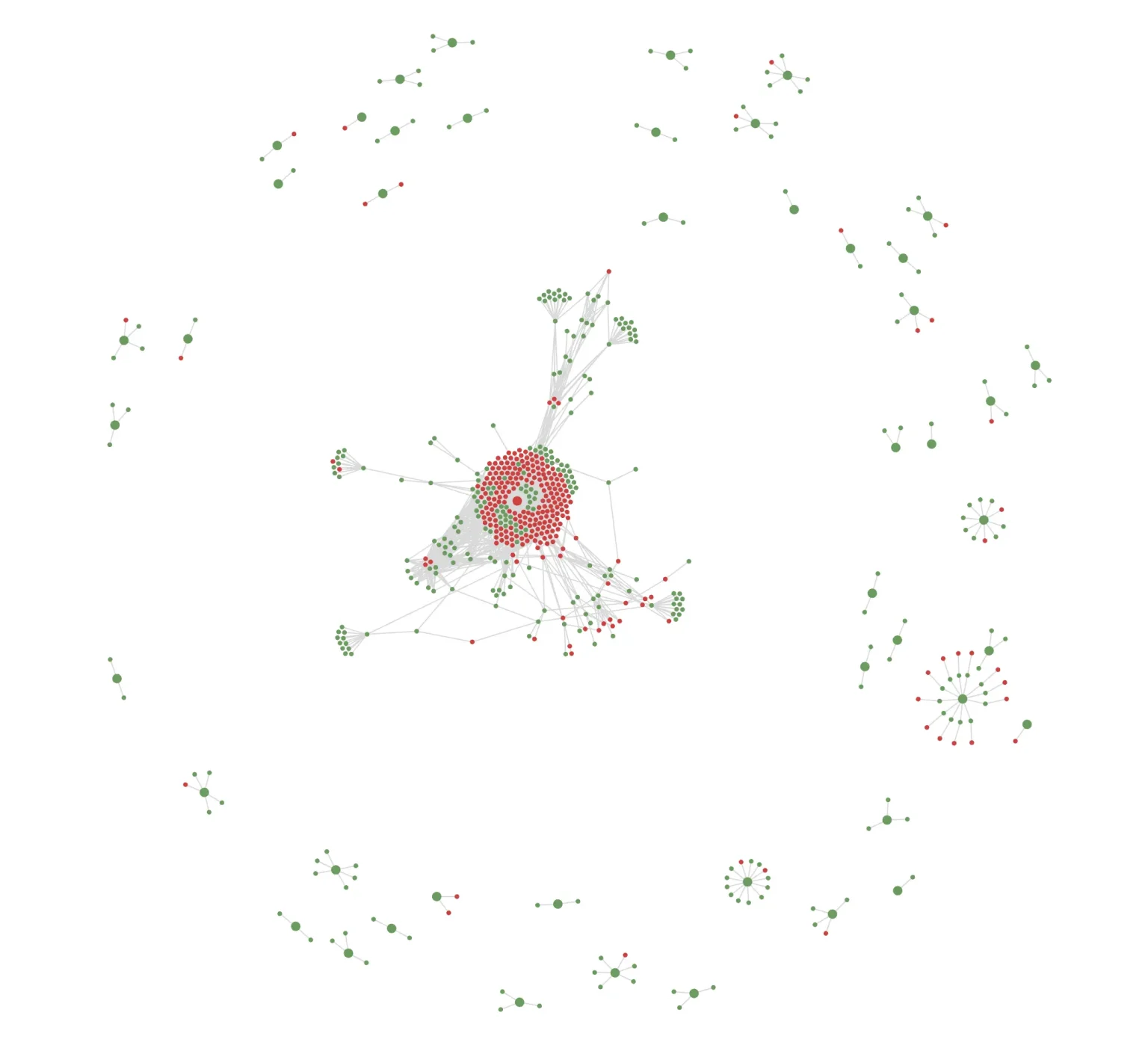
Establish new asset-to-asset connections
Map and assess the strength and characteristics of the relationships between newly found and known assets.
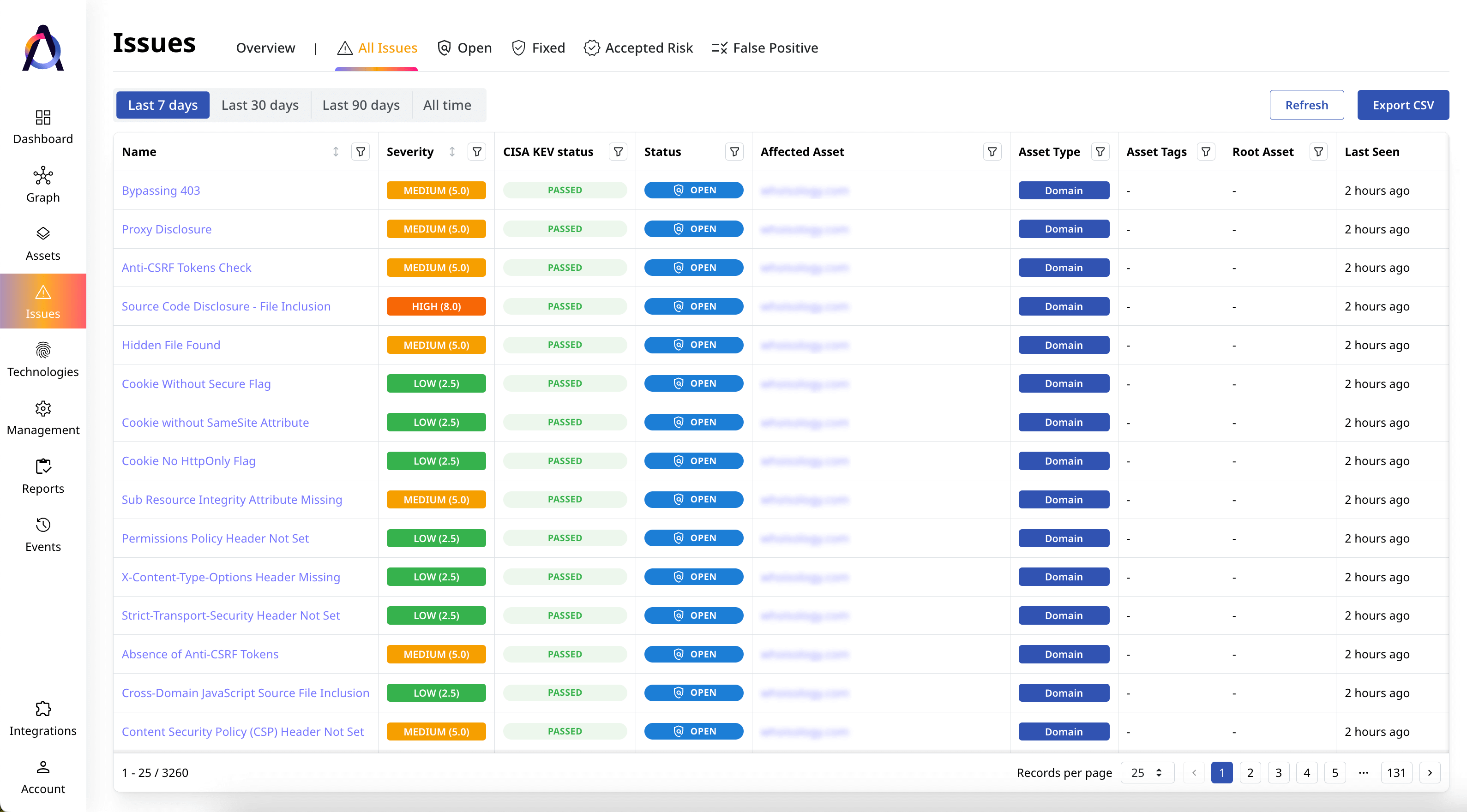
Identify and remediate vulnerabilities
Scan shadow IT assets for security gaps and analyze vulnerability intelligence to plan remediation efforts.
-
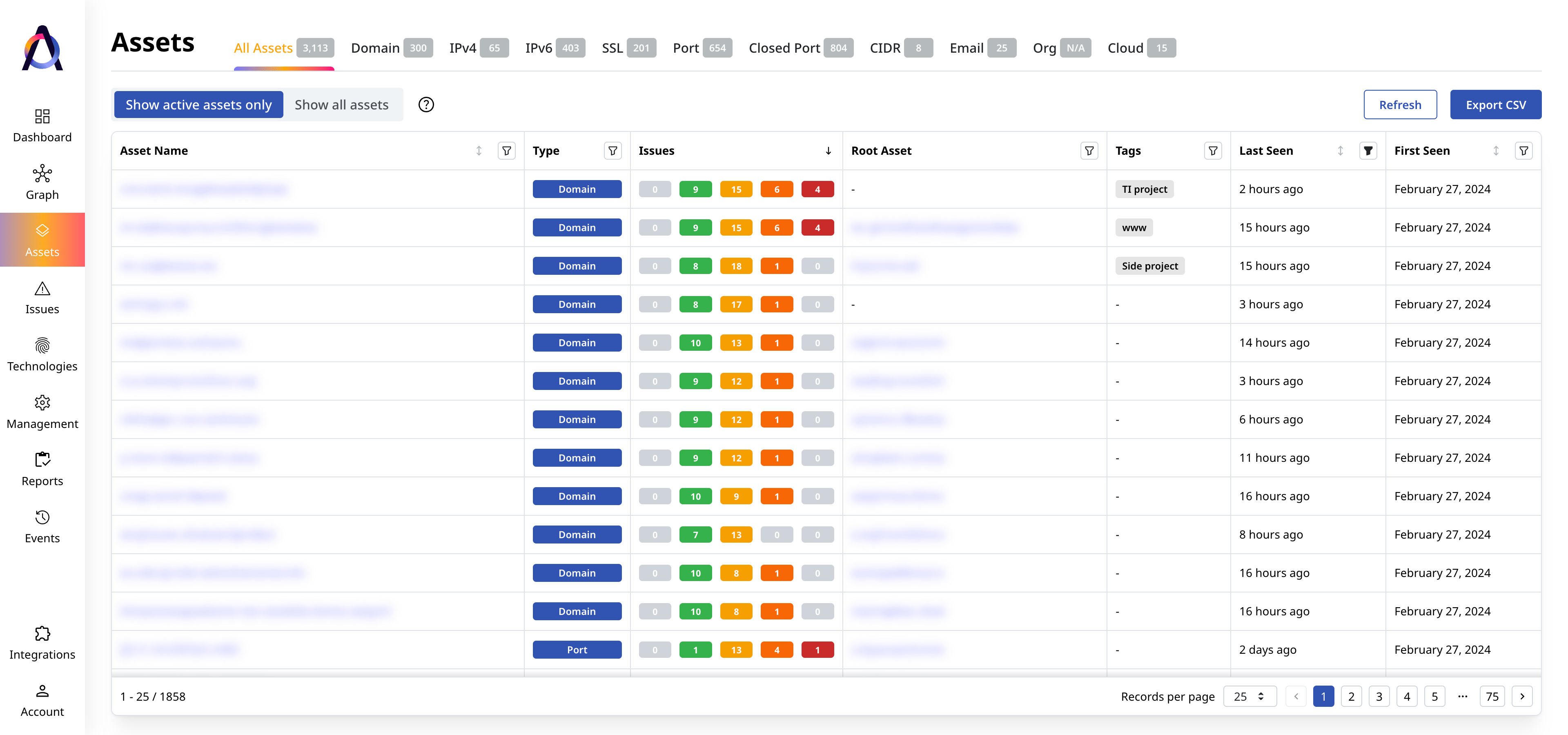
Complete Inventory
Access catalogs of all your Internet-facing assets and their issues.
-
Cloud Provider Integrations
Integrate your cloud assets across popular cloud service providers.
-
Deeper Context
Explore your assets’ health, connections, and technologies.
What security experts say
Featured Resources

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

CWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like CWE, CVE, and CVSS. These term[...]

How to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sensitive information, or disrupt[...]