Manage Third-Party Risks
Identify and assess all third-party risks, prioritize and mitigate the most important ones, and continuously monitor for new third-party technologies and associated risks.
What our clients say
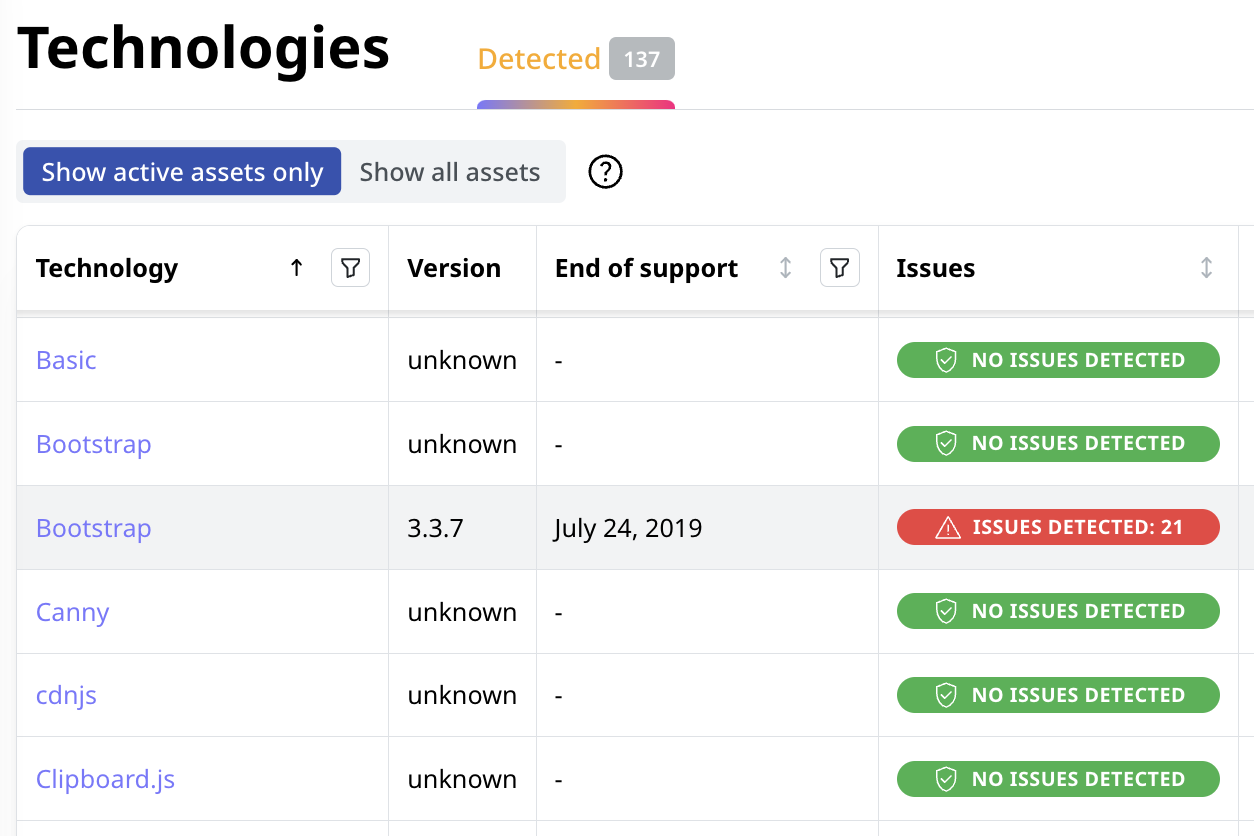
Identify All Third-Party Vendors
Attaxion allows you to quickly get a complete overview of the third-party technologies and tools in your external attack surface.
Learn more:
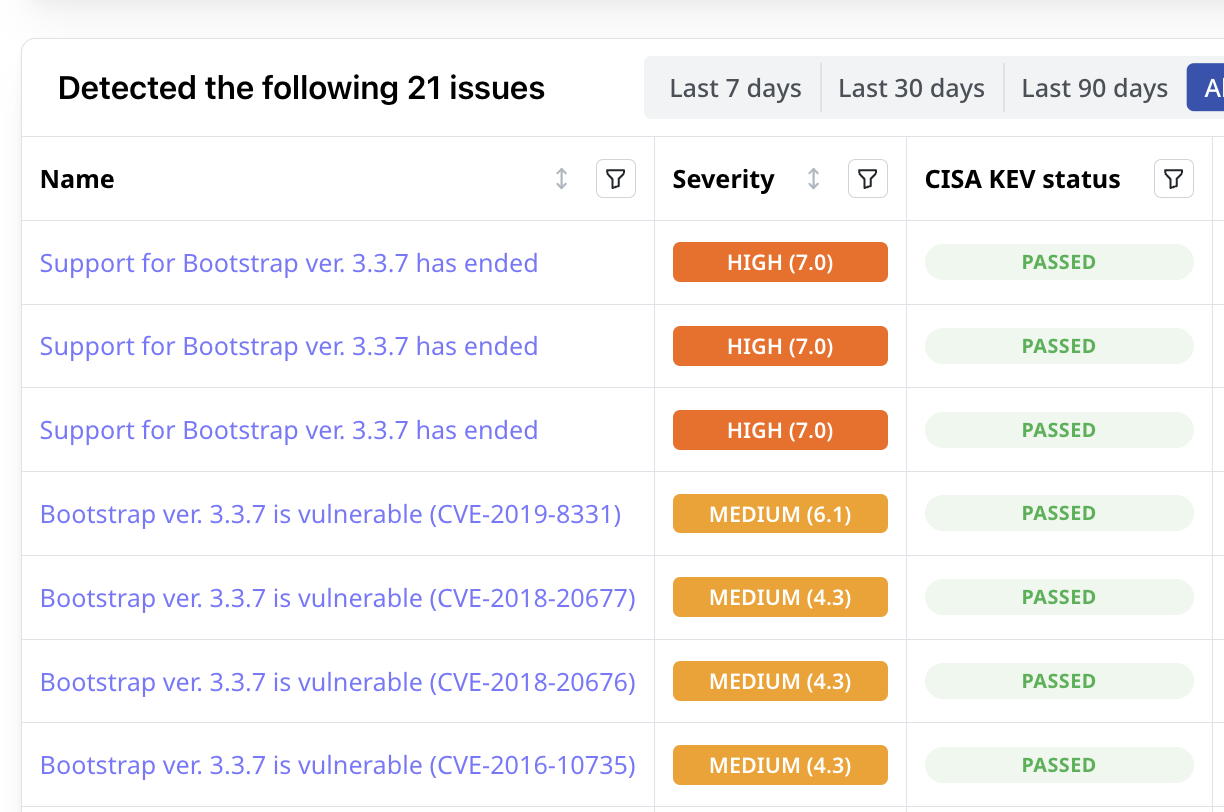
Assess Each Third Party
Attaxion uses a powerful vulnerability scanner relying on a dynamic application security testing approach that helps uncover risks associated with every third-party vendor.
Learn more:
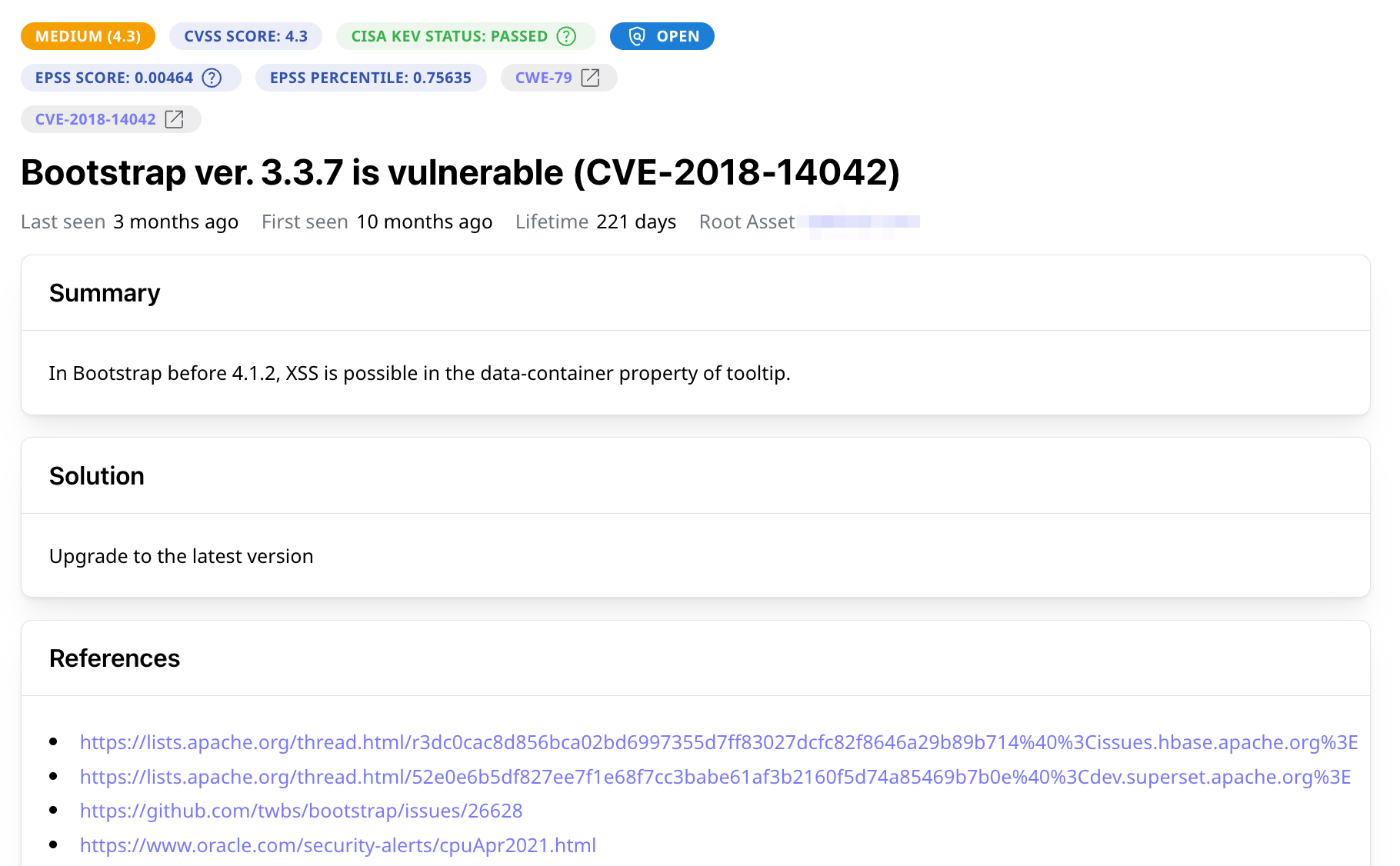
Mitigate Third-Party Risks
Get all important information about each risk to prioritize them according to their severity, exploitability, and asset criticality. Create tasks for support engineers in 1 click.
Learn more:
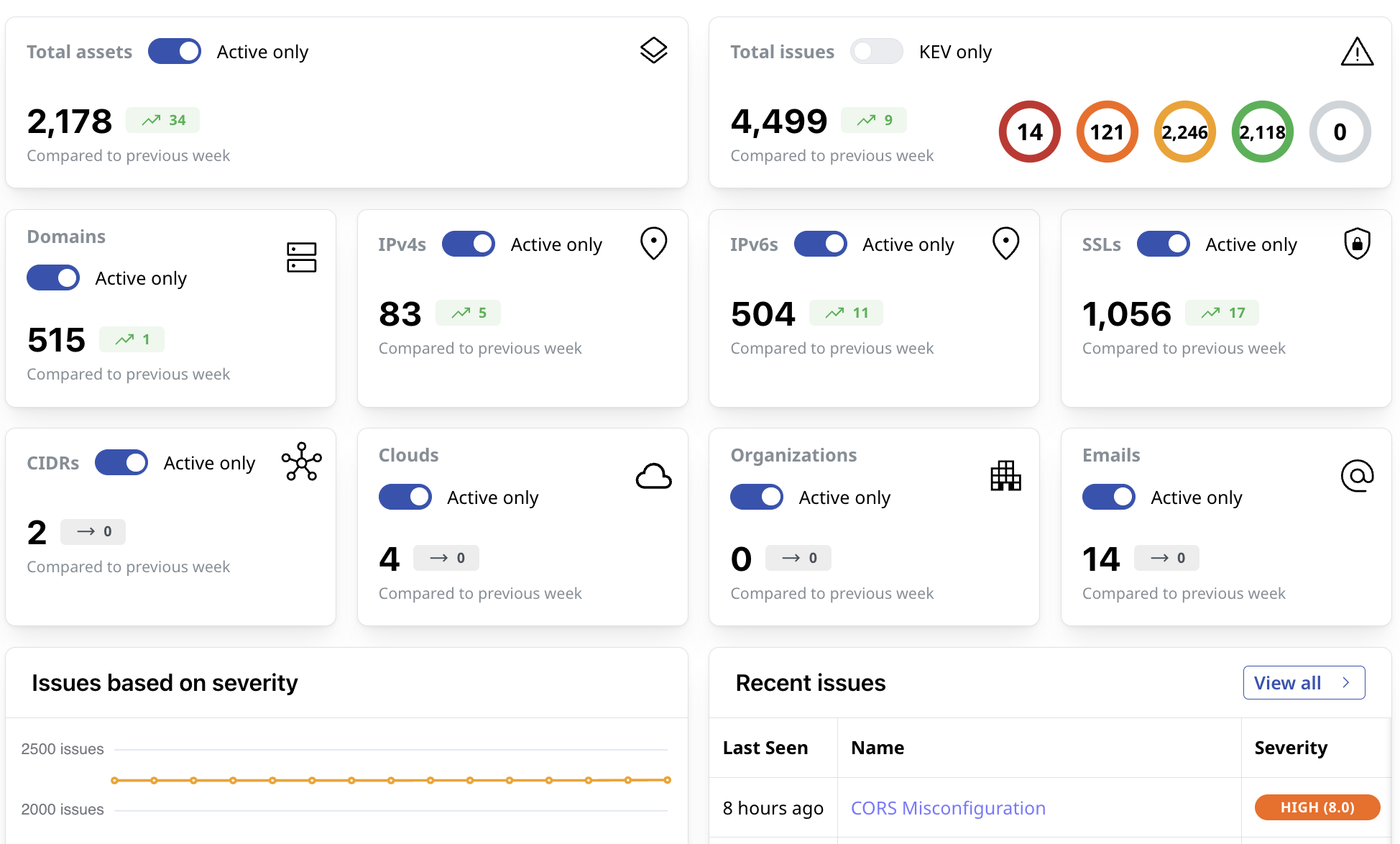
Continuously Monitor All Third Parties
Attaxion continuously scans your infrastructure for new third-party technologies and associated risks so that you can react timely and prevent potential exposures.
Learn more:
Promptly Respond to Issues
Get notified through your existing tools about newly discovered assets and important issues to take action before the cybercriminals can.
Learn more:
Start Using Attaxion for Third-Party Risk Management
Get started in a few clicks and get the first results in 2 hours. Attaxion is easy to navigate and provides a complete image of your organization’s external attack surface, including third-party technology.
Why Choose Attaxion for TPRM?
-
Highest Asset Coverage
Attaxion can discover more external assets than other solutions, offering a full picture of your external attack surface, including about third parties.
-
Complete Third-Party Technology Inventory
Attaxion builds and maintains a complete inventory of the third-party technologies used across all your external assets, highlighting technology versions and related assets that pose higher risks.
-
Risk-Based Prioritization
Factor exploitability and CISA KEV data on real-world malicious usage of vulnerabilities into your issue prioritization.
Featured Resources

10 Critical Attack Surface Metrics to Track
With recent regulatory changes pushing cybersecurity to the boardroom, effective attack surface monitoring and visualization techniques are more cruci[...]

Detecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the reason can be a security weaknes[...]

Overcoming the Top SOC Challenges with EASM
A day in the life of a security operations center (SOC) analyst likely involves sifting through mountains of data and alerts, searching for clues that[...]