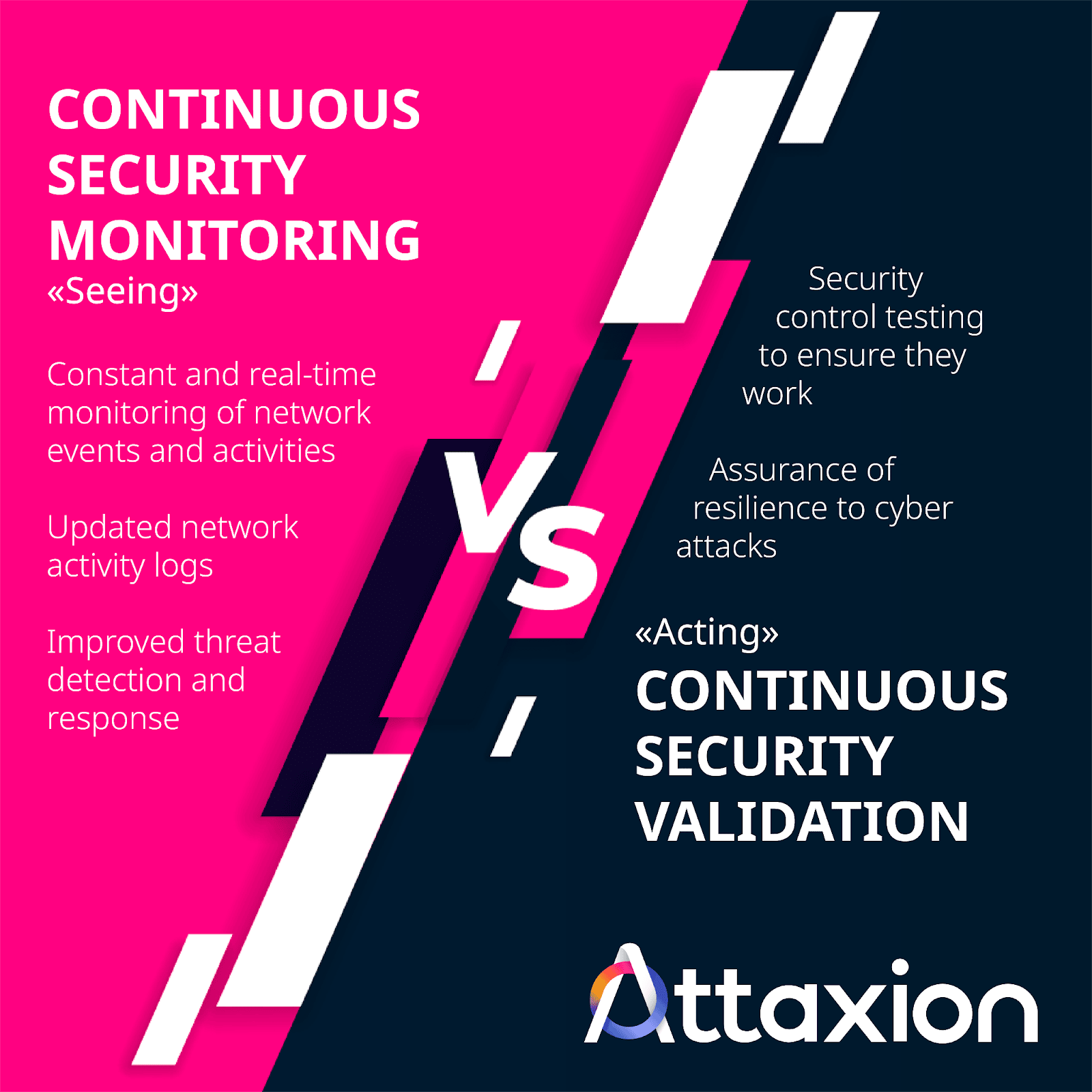
Continuous security validation (CSV) is a proactive cybersecurity approach that involves assessing and validating an organization’s security controls to determine if they actually work and are adequate to the continuously changing threat landscape.
It has become necessary because attackers constantly change tactics, techniques, and procedures (TTPs), making previously working security controls ineffective. Security teams need to keep up, which is why they have to continuously validate the existing security controls’ effectiveness and introduce new ones if necessary.
If cyber attackers, for instance, shift to exploiting particular open ports, then it may be time for security teams to implement solutions capable of automatically detecting such ports and scanning associated assets for vulnerabilities to strengthen their existing policies and procedures.
Table of Contents
- How Does Continuous Security Validation Work?
- Tools Used for Continuous Security Validation
- What Are the Benefits of Continuous Security Validation?
- FAQ
How Does Continuous Security Validation Work?
If you want to describe continuous security validation as a process, you could divide it into four steps – discovery, validation, analysis/prioritization, and optimization.

1. Discovery: establishing the baseline
Every organization has some security controls in place, whether they are many or few, basic or advanced. Continuous validation starts with setting a baseline – discovering the current state of security controls that the organization has and their effectiveness.
For that, security practitioners first use discovery tools such as external attack surface management (EASM) platforms to define the scope and identify the possible attack vectors, and then simulate attacks to see if current security measures are sufficient to protect the organization against them.
All tactics and techniques used are mapped to the MITRE ATT&CK framework, allowing organizations to see what stages of an attack they can detect/respond to – and what they missed.
That allows them to understand which controls are misconfigured or underperforming. The output of this exercise is the baseline report that contains the following information:
- What attacks are detected/prevented and what are not;
- What tactics and techniques are used in those attacks;
- What security controls are supposed to prevent them and how well they actually do their job.
The baseline is a starting point. From there, security validation is configured to run continuously.
2. Validation: running continuous tests
After the baseline is established, the organization defines the schedule for running tests (whether it’s daily, weekly, or monthly).
The tests should be non-disruptive so as to not impact business continuity. At the same time, they should emulate real-world adversary behavior. For this, organizations use breach and attack simulation (BAS) platforms that simulate TTPs used by real-world advanced persistent threat (APT) actors.
It’s worth noting that as the adversary behavior changes over time, so should the tests. So, security teams often complement BAS tools with threat intelligence sources to add new and updated TTPs and run attacks that simulate current threat actors that are relevant to the industry and region the company works in.
3. Analysis: gap detection
One of the main points where CSV differs from penetration testing or most other cybersecurity exercises is that its aim is not only to find vulnerabilities and assess what damage can be done exploiting them, but also to discover inefficient security controls that resulted in these vulnerabilities being there.
So, while BAS tools output which simulated attacks succeeded and which TTPs these attacks can be mapped to, the job of the security team is to analyze this output and define which of the existing security measures were not effective enough and what needs to be implemented.
Security teams have to look at telemetry to see if the attacks were identified, if proper alerts were sent, if there was enough context in the alert to enable proper incident response, and so on.
The output of this part of the process is a detailed breakdown of what has been blocked, detected, or missed, as well as remediation plans tied to specific controls.
This step is sometimes called prioritization, as there is indeed a lot of prioritization to be done when figuring out what ineffective security controls to address first.
4. Optimization: remediation and retesting
As in every continuous process, the last step is to implement the necessary changes and to run the tests again to see if the updated security controls were sufficient.
Tools Used for Continuous Security Validation
To cover the entire CSV process, you’ll need a variety of tools. Below, we describe the ones that are necessary.
- External attack surface management platforms. To discover public-facing assets and run vulnerability scanning to define the scope and potential attack vectors (examples: Attaxion, Cortex Xpanse).
- Breach and attack simulation tools. To emulate real-world TTPs and validate detection, prevention, and response effectiveness (examples: SafeBreach, Cymulate).
- SIEM and XDR platforms. To collect telemetry, detect, and alert on simulated attacks (examples: Splunk, Microsoft Sentinel).
As the organization grows, you can always add more security tools such as a security orchestration, automation, and response (SOAR) platform to validate if the incident response workflows actually trigger and work correctly. Other security automation tools can also help. The three listed above — EASM, BAS, and SIEM — are the must-have tools to enable CSV in an organization of any size though. There are also specialized automated security validation platforms that combine several of those tools, which can be effective, but usually are on the expensive side.
What Are the Benefits of Continuous Security Validation?
CSV is unique in the sense that it continuously assesses the organization’s security posture. In comparison with processes that simply aim to eliminate vulnerabilities, that has a lot of benefits:
Real-time visibility into security effectiveness
CSV provides continuous, actionable insights into whether your existing security controls (EDR, SIEM, firewalls, etc.) offer an adequate response to security threats right now — not when the last audit happened. This ongoing validation helps identify gaps, policy mismatches, and control failures early — leading to continuous improvement.
Proactive threat readiness
CSV simulates real-world threats regularly, helping your security team stay prepared and incident-ready. Tests use attack techniques from MITRE ATT&CK — the same as those that real threat actors use — so the organization’s protections are regularly tested against realistic attack scenarios.
Accelerated remediation cycles
CSV enables rapid retesting of fixes, speeding up security hardening. As a result, it reduces exposure time by tightening the detection-response-remediation loop.
Enhanced network and telemetry visibility
CSV highlights what’s being logged correctly, and what gets missed. It helps security teams prioritize efforts based on actual detection gaps rather than assumptions, and can uncover areas where log management or detection coverage need attention.
Compliance support
Organizations can confirm that applied mitigations and security policies are actually effective—not just assumed to be. This makes them continuously ready for compliance audits, saving time and effort required for preparation.
Potential cybersecurity cost reduction
CSV helps identify ineffective controls and redundant security tools, potentially optimizing security spending. At the same time, it helps lower the likelihood or impact of breaches, contributing to brand protection, customer trust, and reduced incident-related costs.
Develop a cyber threat model for an organization
CSV was first introduced in a 2019 ISACA article, where its author, Berk Algan, emphasized that, among other things, CSV helps organizations develop a relevant threat model that allows them to focus on higher risks and key information assets, instead of spreading their attention across everything that they have.
Key Takeaways
- Continuous security validation is a proactive cybersecurity approach that requires consistently assessing and validating an organization’s security controls to prioritize remediation actions.
- The approach is not a one-time process. Its phases—discovery, validation, analysis, and optimization—must be conducted in a constant loop to ensure an organization’s network stays safe from all threats at all times.
- It improves network visibility, increases the effectiveness of security solutions, and more to help reduce costs, reassure third parties they are protected from critical threats, and protect an organization’s brand and operations.
- Continuous security validation extends beyond continuous security monitoring.It empowers security teams to not only identify issues but also take action on them and adjust security controls to ensure that attacks aiming to exploit similar issues get detected and blocked.
Ready to find out how Attaxion can help with your continuous security validation efforts? Start your 30-day trial now!