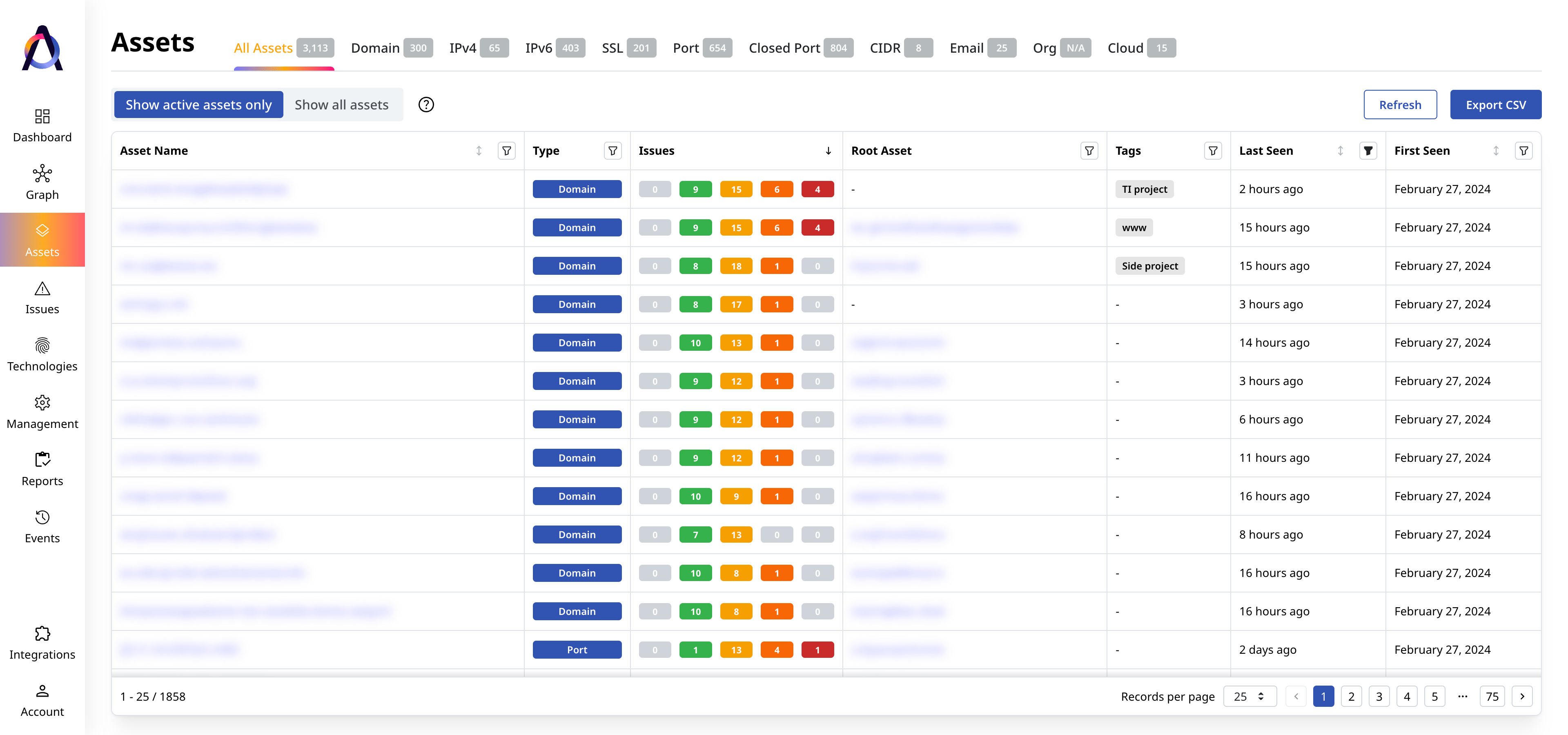
Agentless Exposure Management
Agentless Exposure Management
Full Attack Surface Coverage for Lean Security Teams
Find all your web-facing assets, continuously uncovering and reducing cyber risks with Attaxion.



-
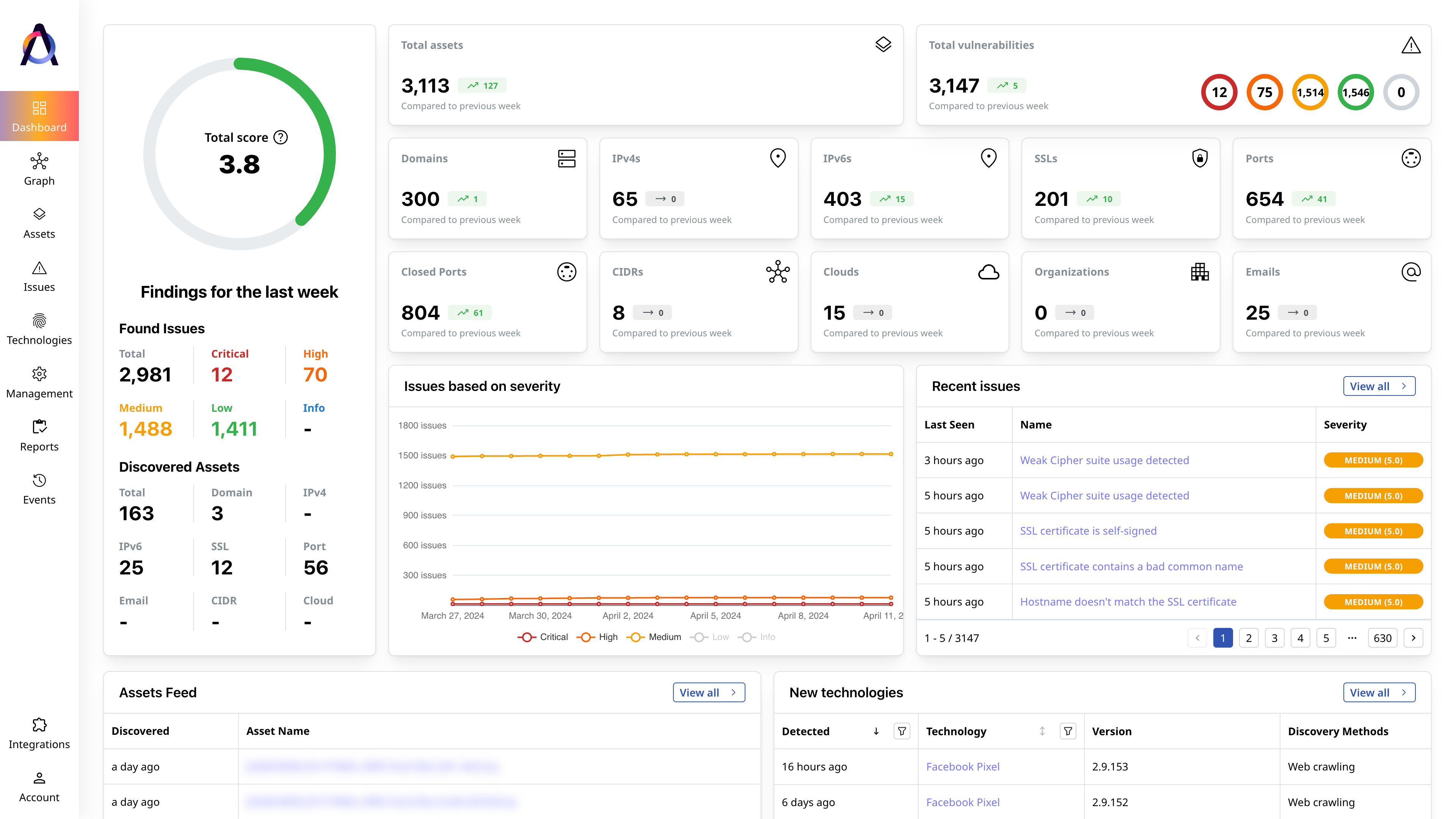
Highlight critical and exploitable issues
Prioritize vulnerabilities and misconfigurations based on AI insights about their severity, exploitability, and affected assets.
Learn More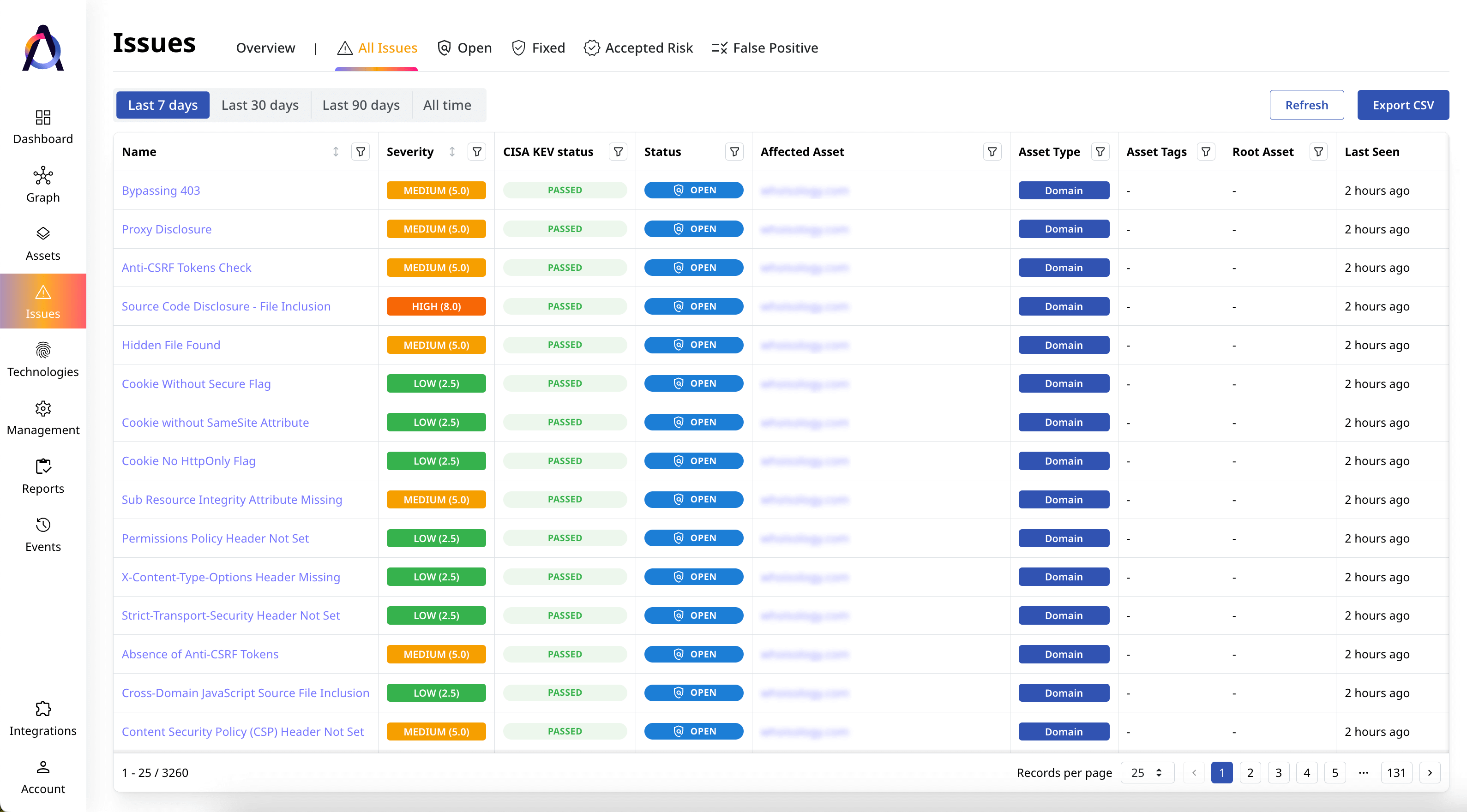
-
Plan and automate risk remediation
Easily assign remediation tasks within your existing workflows and track improvements in your security posture.
Learn More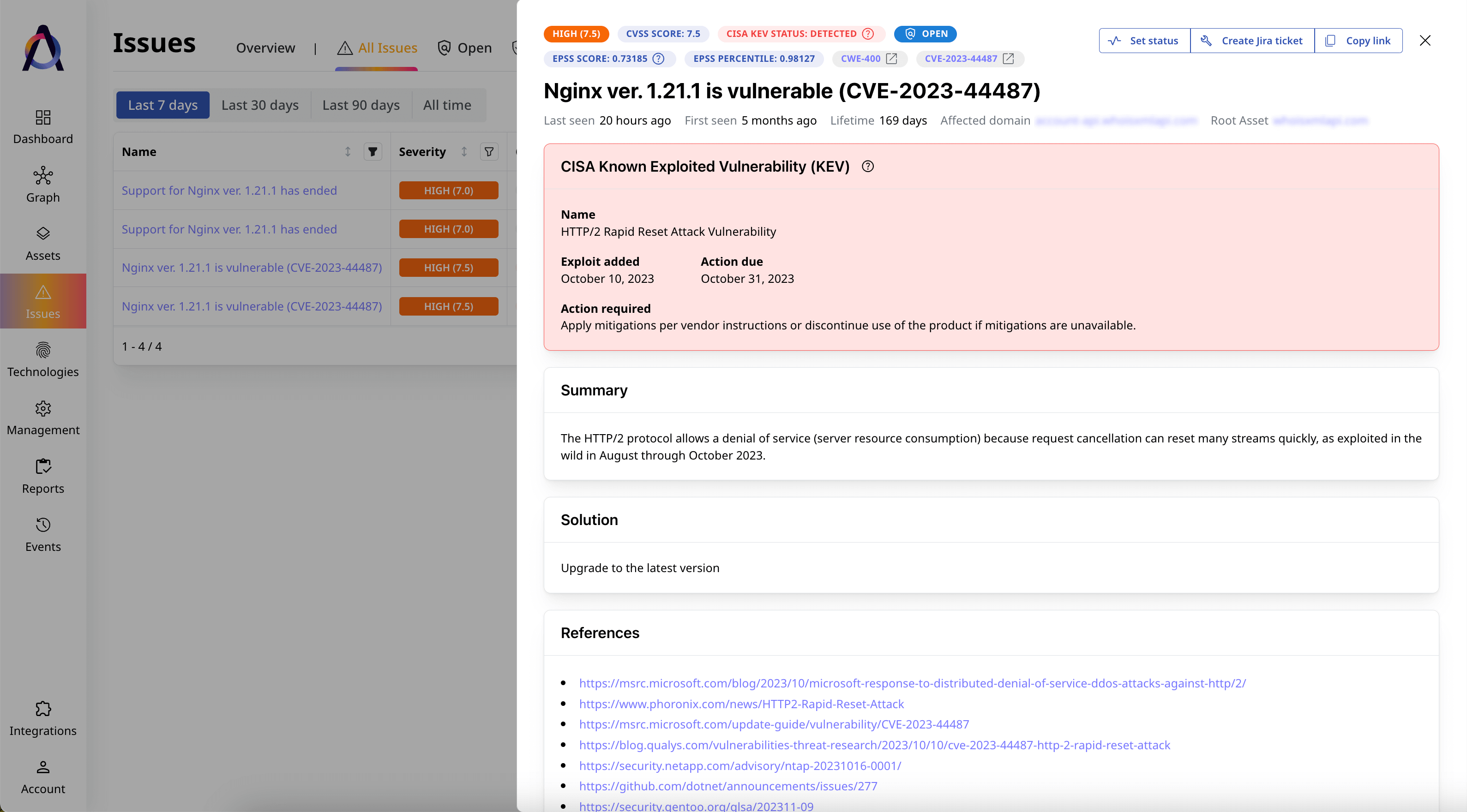
-
Agentless traffic monitoring
Continuously monitor traffic to and from your IP addresses — no agents required. Detect communication with malicious IPs and use threat intelligence to take fast, informed action.
Learn More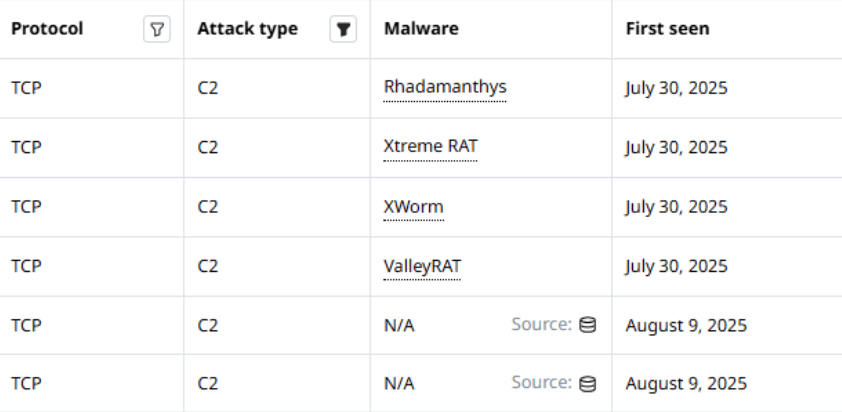
97%
more total assets found3x
as many unique assets found9+
asset types trackedSolutions per Use Case and Case Studies
-
Learn more
Reduce Your External Attack Surface
Continually eliminate pressing attack vectors in your expanding digital perimeter.
-
Learn more
Test Web Application Security
Run fully automated security testing for web apps across your entire external attack surface.
-
Learn more
Manage Third-Party Risks
Identify, assess, continuously monitor for new third-party technologies and associated risks.
-
Learn more
Assess Mergers and Acquisitions Risks
Obtain insights into target candidates’ security posture and inherited cyber risks.
-
Learn more
Simplify Cybersecurity Compliance
Eliminate potential compliance issues by ensuring all external assets are cataloged and scanned for vulnerabilities.
-
Learn more
Finance
How a regional bank introduced risk-based vulnerability management and strengthened its compliance and security with Attaxion.
-
Learn more
SaaS
How Totalmobile gained full attack surface visibility, uncovered shadow IT, and implemented EASM with Attaxion.
-
Learn more
Software Agency
How Pollysoft automated full visibility over their external assets and critical vulnerabilities.
-
Learn more
Education
How a small security team achieved reliable scanning across servers and web apps using Attaxion’s attack surface management.
-
Learn more
Manufacturing
How automated asset discovery with Attaxion speeds up remediation for Rand Machine Products.
What security experts say
Featured Resources

Detecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the reason can be a security weaknes[...]

Securing ISO 27001 Compliance: Attack Surface and Risk Management Essentials
Building customer trust takes a lot of hard work, and a single security incident can jeopardize it all. In fact, IBM’s Cost of a Data Breach Rep[...]

The Importance of Asset Attribution to External Attack Surface Management
The prevalence of cyber attacks has become a harsh reality. A study shows that 69% of organizations have fallen victim to a cyber attack originating f[...]