PLATFORM CAPABILITIES
PLATFORM CAPABILITIES
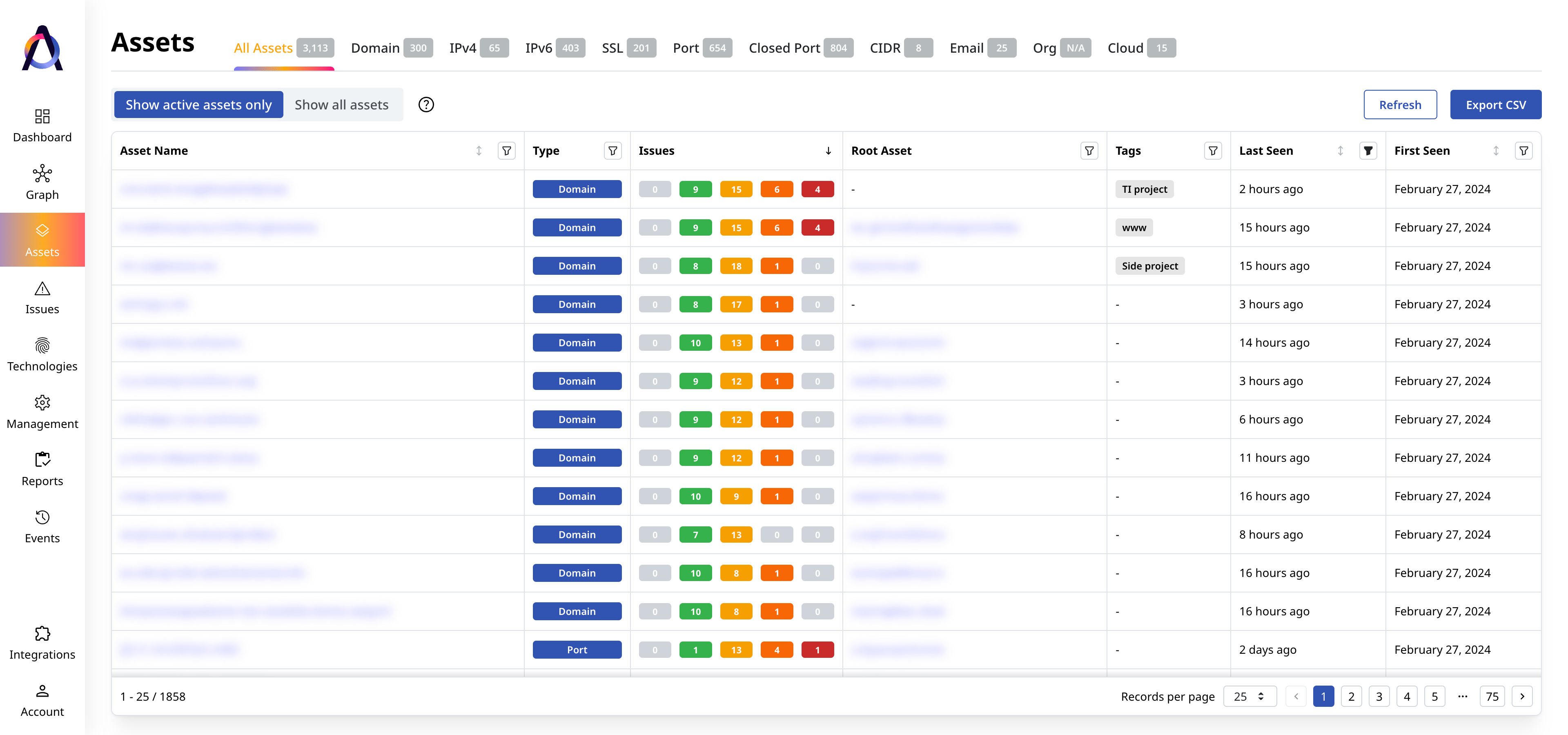
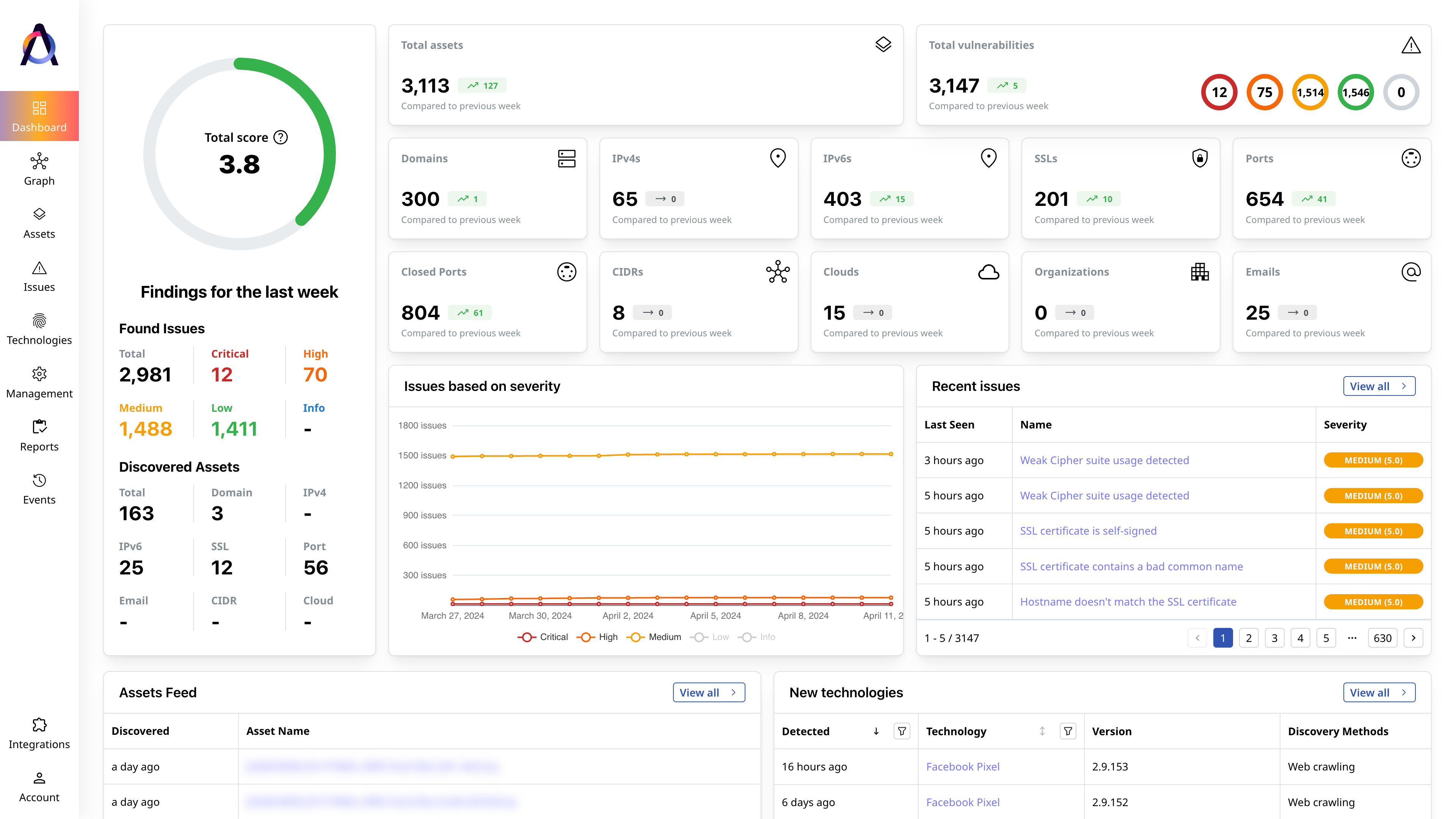
Attack Surface Discovery
Discover your true Internet-facing assets and their security vulnerabilities faster.
Identify Internet-facing assets
Find and catalog your organization’s external assets and their technologies with AI-powered discovery methods and reconnaissance techniques.
Map asset-to-asset connections
Analyze the relationships between assets, including their strengths and characteristics, through extensive asset mapping.
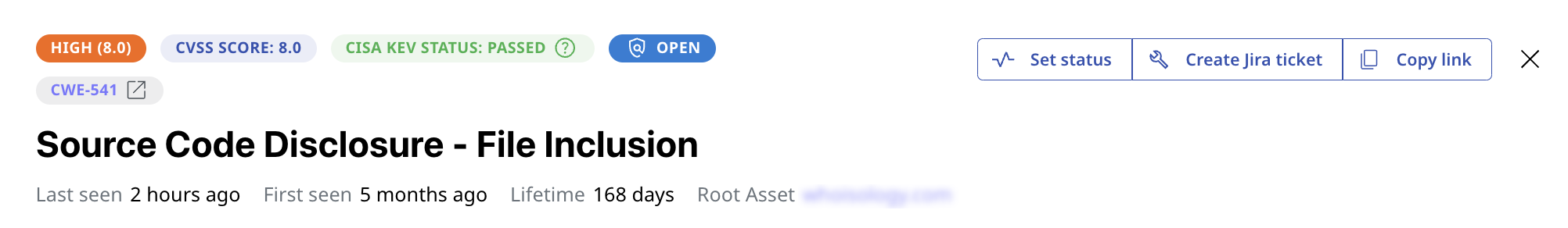
Detect and evaluate security gaps
Scan your assets and compile the vulnerabilities and issues attackers may exploit to plan risk management strategies.
-
Superior Coverage
Discover twice as many assets and their security issues for more asset types.
-
Start Right Away
Jump into action—find and protect your vulnerable assets within hours.
-
Any Security Budget
Small or very large attack surface? Attaxion has the right pricing for you.
Our Discovery Features
- ✅ Overview and scoring of the entire attack surface
- ✅ Complete asset inventory with context
- ✅ Complete issue inventory with security insights
- ✅ Current and historical view of the attack surface
- ✅ Mapping of asset connections and dependencies
- ✅ Technology discovery and classification
- ✅ Asset grouping and filtering
- ✅ Role-based access control
What security experts say
FAQs
Featured Resources

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

CWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like CWE, CVE, and CVSS. These term[...]

How to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sensitive information, or disrupt[...]