Simplify Cybersecurity Compliance
Eliminate potential compliance issues by ensuring all external assets are cataloged, scanned for vulnerabilities, and remediated according to priorities.
What our clients say
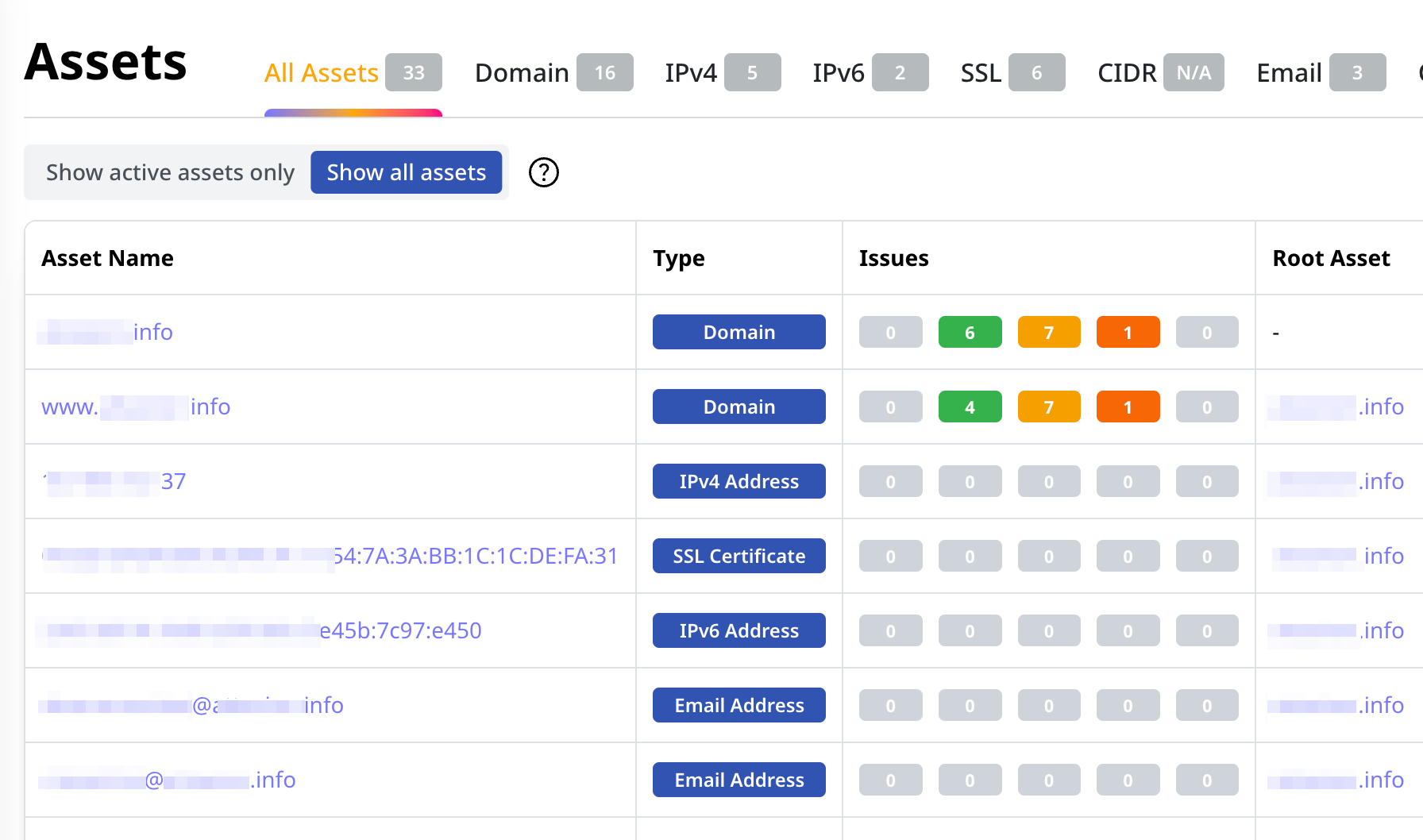
Get a Comprehensive Asset Inventory
Don’t let unknown or forgotten assets become a non-compliance threat. Attaxion builds a complete inventory of your organization’s external assets, including those you didn’t know about.
Learn more:
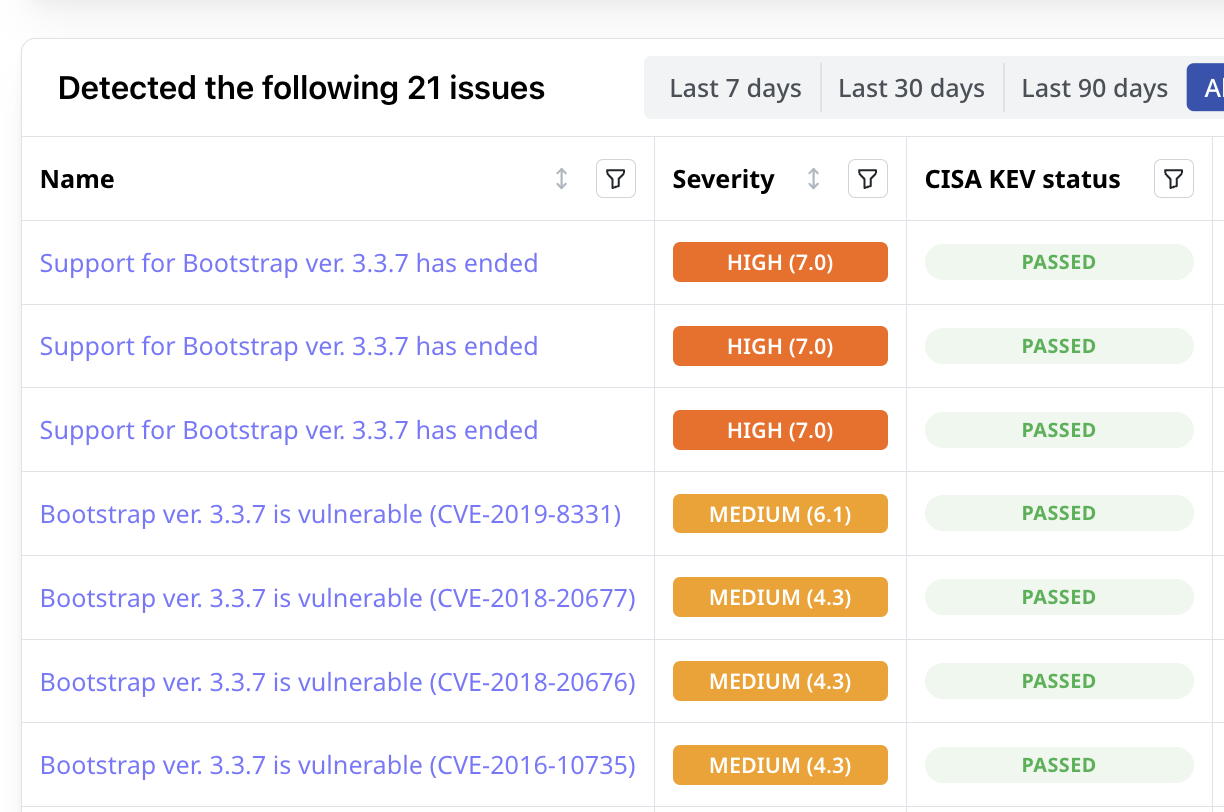
Prioritize Vulnerabilities Based on Business Risk
Make sure business-critical assets and vulnerabilities with a high likelihood of exploitation are prioritized. Attaxion provides you with much more than just CVSS numbers for your prioritization efforts.
Learn more:
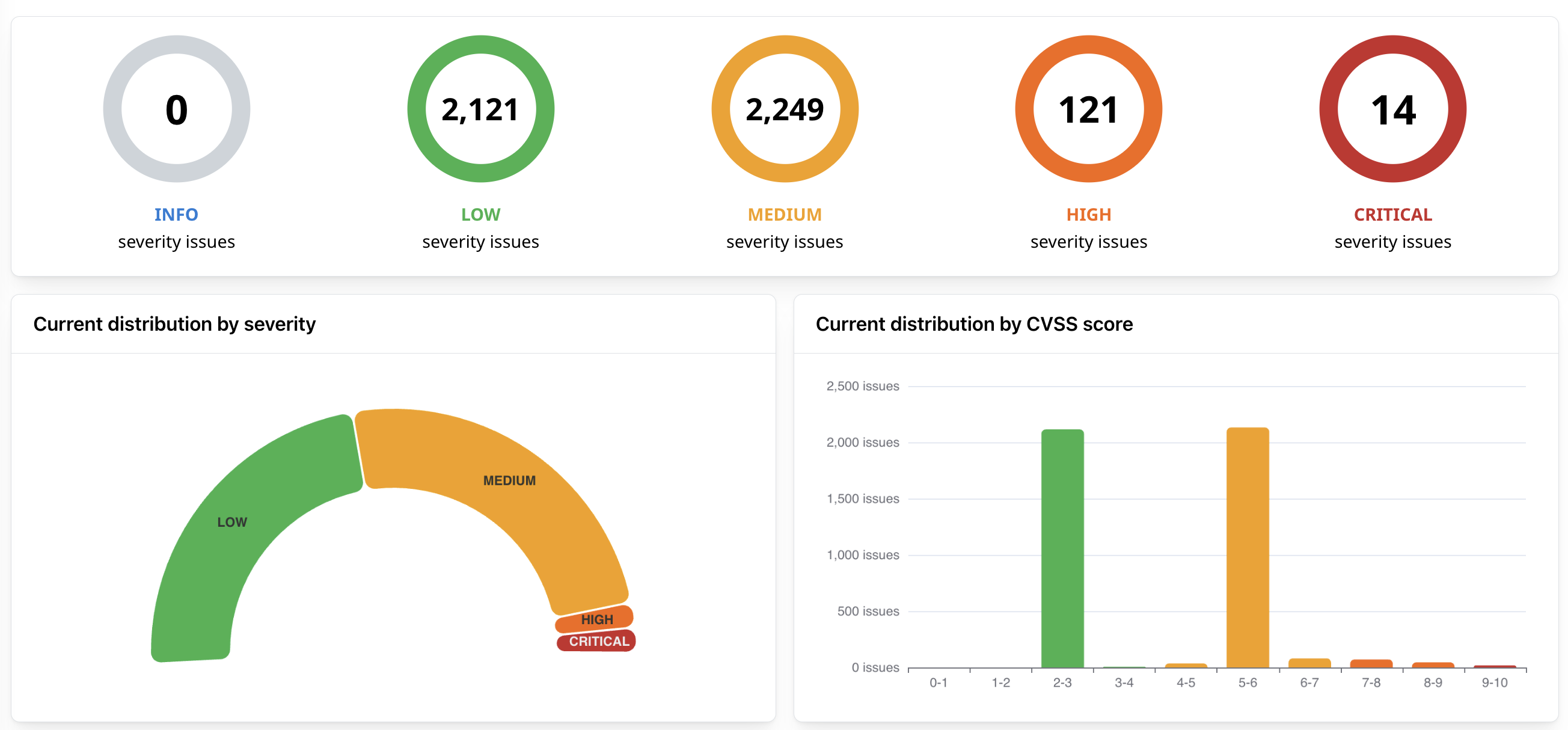
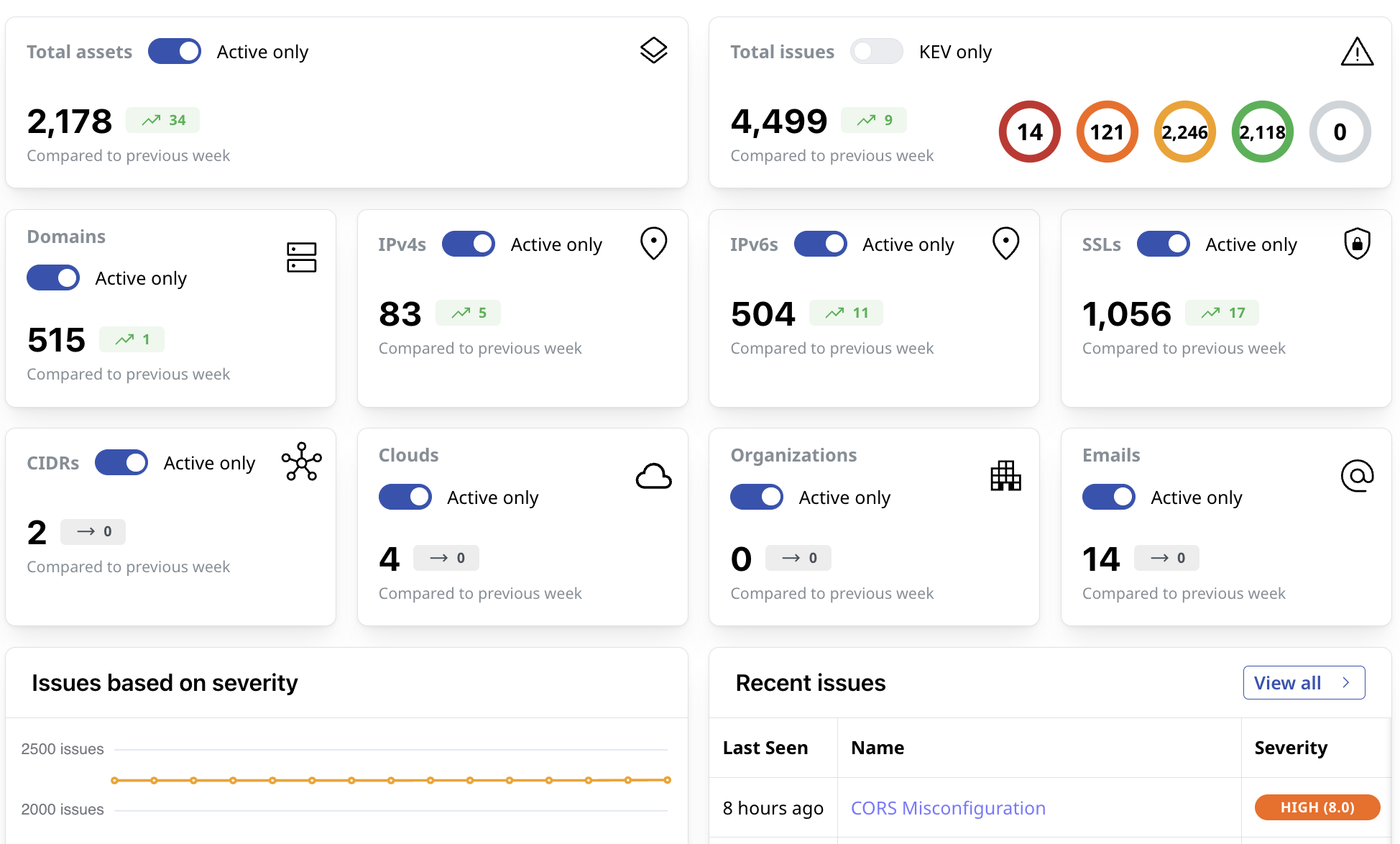
Report on Remediation Efforts
Use Attaxion’s dashboards and reports to understand and communicate how vulnerabilities discovered in your organization’s external attack surface are remediated.
Learn more:
Get More Value From Penetration Testing
Focus pentesting efforts on non-obvious issues and ensure that systems not covered by penetration tests also stay secure.
Learn more:
Maintain Continuous Compliance
Get notified through your existing tools about newly discovered assets and important issues to take action before the cybercriminals or auditors can.
Learn more:
Start Using Attaxion to Simplify Cybersecurity Compliance
Get started in a few clicks and get the first results in 2 hours. Attaxion is easy to navigate and provides a complete image of your organization’s external attack surface, including third-party technology.
Why Choose Attaxion for Cybersecurity Compliance?
-
Highest Asset Coverage
Attaxion can discover more external assets than other solutions, ensuring comprehensive visibility into your external attack surface and reducing risks of accidental non-compliance.
-
Complete Third-Party Technology Inventory
Attaxion builds and maintains a complete inventory of the third-party technologies used across all your external assets, highlighting technology versions and related assets that pose higher risks.
-
Risk-Based Prioritization
Factor exploitability and CISA KEV data on real-world malicious usage of vulnerabilities into your issue prioritization.
Featured Resources

Securing ISO 27001 Compliance: Attack Surface and Risk Management Essentials
Building customer trust takes a lot of hard work, and a single security incident can jeopardize it all. In fact, IBM’s Cost of a Data Breach Rep[...]

New EU Product Liability Directive: What Software Companies Need to Know
Software supply chain vulnerabilities are a multimillion-dollar problem, according to a study by Juniper Research, and it’s not going away. The cost o[...]

Detecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the reason can be a security weaknes[...]