PLATFORM CAPABILITIES
PLATFORM CAPABILITIES
Agentless Traffic Monitoring
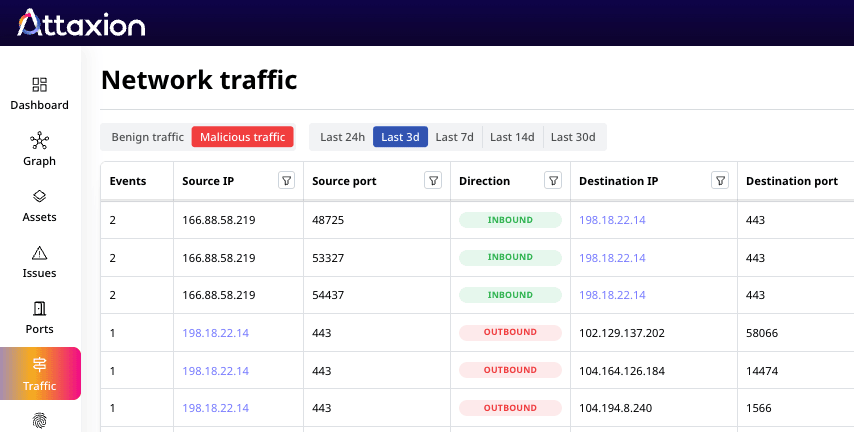
Analyze network traffic coming to and from your infrastructure IP addresses, detecting malicious traffic with details down to the malware family — no deployment and no agents required.
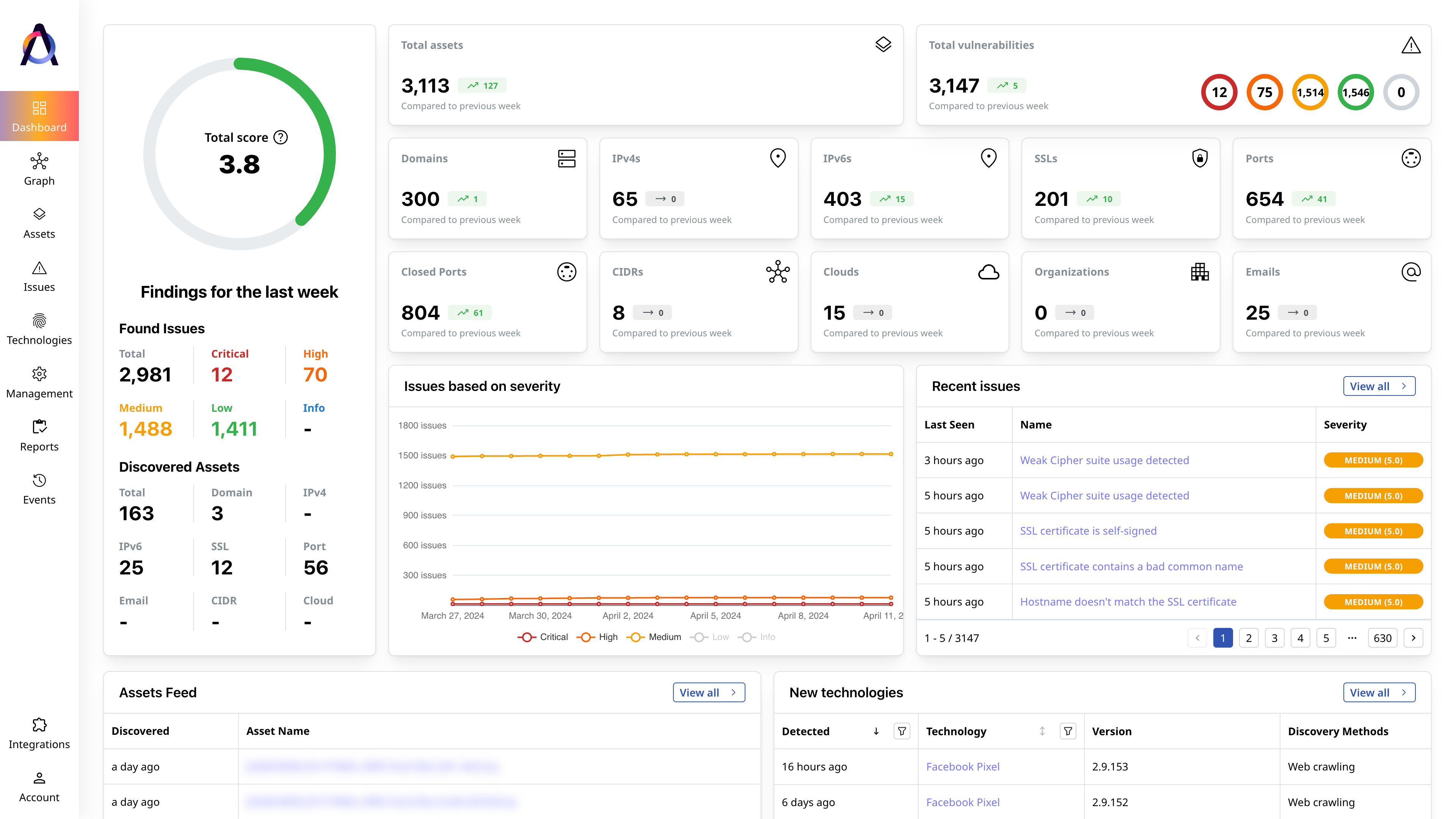
Detailed infrastructure traffic analysis at your fingertips
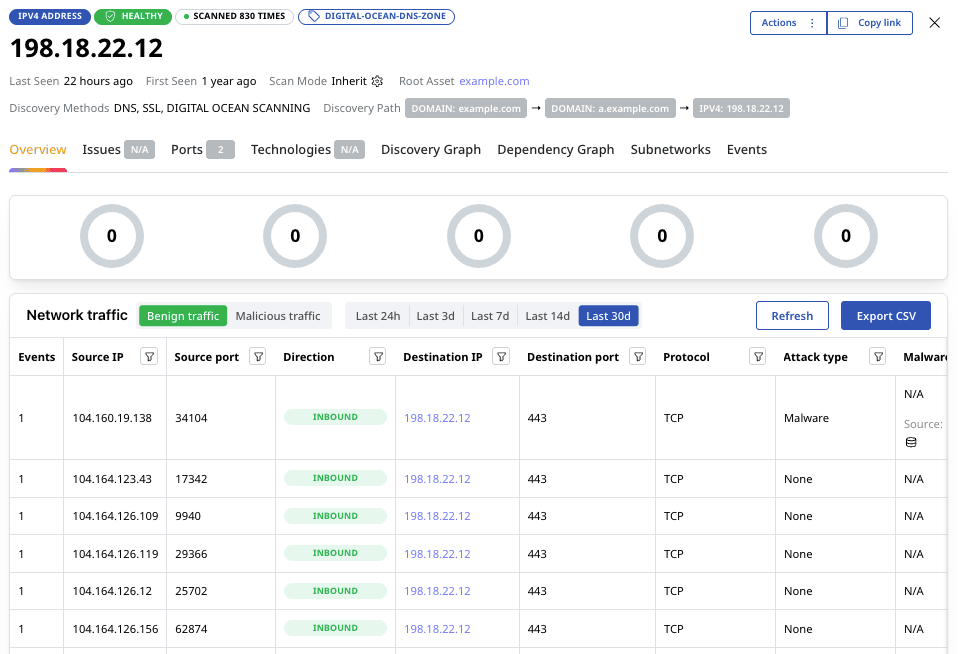
Get a clear view of all inbound and outbound traffic to your exposed IP addresses — including source and destination IPs, ports, protocols, and timestamps. Spot patterns, understand behavior, and detect suspicious connections at a glance, all powered by real-time NetFlow data.
Agentless operation
Attaxion’s Agentless Traffic Monitoring doesn’t require you to install any agents or sensors. No time wasted installing or setting up – get to the value right away.
Malware communication detection
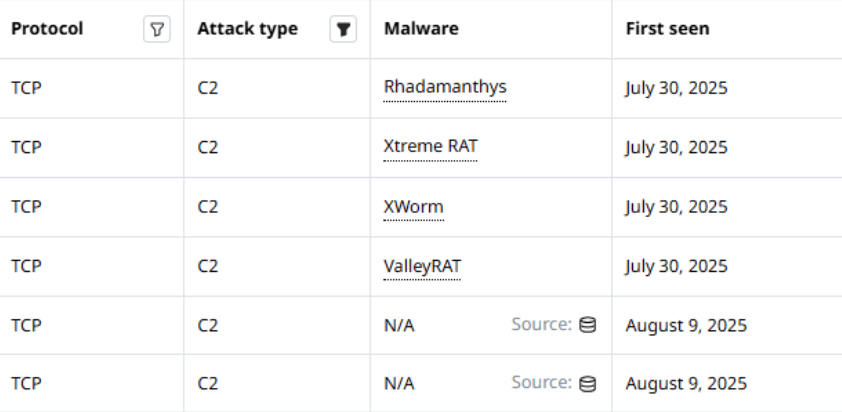
See which of your infrastructure IPs talk to IP addresses with a bad reputation – and act quickly. Agentless Traffic Monitoring integrates with IoC threat intelligence feeds, providing useful context, in some cases with details all the way down to the specific malware family.
Retroactive data
No need to wait while the data is collected – you can see historical traffic data immediately after you enable Traffic Monitoring.
Agentless Traffic Monitoring Use Cases
-
Risk Prioritization
Identify which vulnerabilities need immediate attention by correlating asset exposure with live traffic data. If a vulnerable asset is actively communicating with a known malicious IP, you’ll know it’s time to act.
-
Incident Response
Speed up investigations by instantly seeing which assets send or receive suspicious traffic. Agentless Traffic Monitoring provides the context needed to isolate threats and respond faster.
-
Threat Hunting
Proactively uncover threats without deploying sensors. Use NetFlow data and integrated threat intelligence to track malicious behavior across your external-facing assets.
What security experts say
FAQs
Featured Resources

How Are Attack Vectors and Attack Surfaces Related?
Attack vectors and attack surfaces are deeply intertwined cybersecurity concepts. In a nutshell, an attack surface is the sum of all attack vectors in[...]

CWE Vs. CVE Vs. CVSS: What Are the Differences?
When protecting your digital infrastructure from threats, it’s critical to become familiar with security standards like CWE, CVE, and CVSS. These term[...]

How to Find Vulnerabilities in a Website
Website vulnerabilities are exploitable weaknesses that allow attackers to access data without authorization, steal sensitive information, or disrupt[...]