Best Microsoft Defender EASM Alternative: Attaxion
Microsoft Defender EASM is one of the most well-known external attack surface management (EASM) platforms on the market. It’s also very different from most other platforms for a variety of reasons — from having a non-standard UI to being a part of the Microsoft Azure platform, with its benefits and drawbacks.
Attaxion is another cybersecurity platform covering the entire EASM cycle — asset discovery and inventory, vulnerability scanning, prioritization, remediation, and continuous monitoring. This makes Attaxion a viable Defender EASM alternative, primarily aimed at smaller security teams, while Microsoft’s EASM is supposed to be one-size-fits-all. In this article, we compare the two platforms, describing their approaches to each of the stages of the EASM process. And we start with pricing.
 PART 1
PART 1
Pricing
Microsoft Defender EASM Pricing
Microsoft Defender EASM is priced per asset. Every domain, subdomain, host, or IP address is considered a billable asset. If the IP address is known to be associated with a domain or subdomain from the list, they together form a different kind of billable asset — a domain-IP pair, which helps reduce costs. The pricing seems to be quite straightforward – it’s $0.011 per billable asset per day. There are no tiers, everything is included. Defender EASM comes with a generous 30-day free trial.
However, as it often happens with cloud platforms with pay-as-you-go plans, there are horror stories about novice Azure users receiving $13k bills because, it seems, Defender EASM decided that some part of Cloudflare infrastructure belonged to them and billed them for it. Another problem is that Defender sometimes tends to generate asset false positives, pulling in infrastructure that is not directly associated with any of your assets. At least in the interface, it’s easy to see the number of assets you are being billed for.
Assets are not limited to things you have in your Azure account — there’s no problem with adding things from outside Azure. However, having an Azure account is a prerequisite for using Microsoft Defender EASM.
Attaxion Pricing
Attaxion is also priced per asset. Domains, subdomains, and IP addresses are considered billable assets. Attaxion offers several different tiers, with the Starter plan being the most affordable one and covering up to 40 assets per month. There are also Plus and Business plans covering up to 120 and up to 360 assets, respectively. Bigger attack surfaces are covered by the Enterprise plan. On any of the plans, you can commit to a yearly contract and get a discount.
If your external attack surface contains more assets than your chosen plan covers, Attaxion’s representatives will reach out to you so that you can decide whether to switch to a plan that covers more assets or leave some assets unprotected. Due to the monthly or yearly payment schedule and fixed plans, Attaxion costs are always predictable – you never end up in a situation where you’re expected to pay more than what the plan you’re subscribed to costs.
Attaxion also has a 30-day free trial.
How They Compare
Theoretically, Microsoft Defender EASM should be less expensive than Attaxion, but due to its asset discovery and validation techniques that occasionally generate false positives, it tends to bloat the attack surface and becomes much more expensive (up to 10 times, according to the experience of Attaxion’s clients that have switched from Defender EASM).
Also, with Defender EASM you need to keep an eye on costs, or they may spiral out of control if the platform accidentally attributes some public cloud infrastructure to your attack surface and you’ll end up with a giant bill by the end of the month. These bills can be disputed, and Microsoft is usually understanding, but it’s still unnerving. Such things do not happen with Attaxion.
 PART 2
PART 2
Asset Discovery
Asset Discovery with Microsoft Defender EASM
Just like every other EASM, working with Microsoft Defender EASM starts with providing a number of seed assets that are then used to map your external attack surface by discovering related assets using a variety of cyber reconnaissance techniques. Initial discovery takes 24-48 hours.
When adding seeds, you can start with WHOIS organizations (using a name to identify related assets), a list of domains, IP addresses or IP blocks, hosts, emails, or ASNs. For each type, you can add both the assets to use as seeds and assets that need to be excluded from asset discovery.
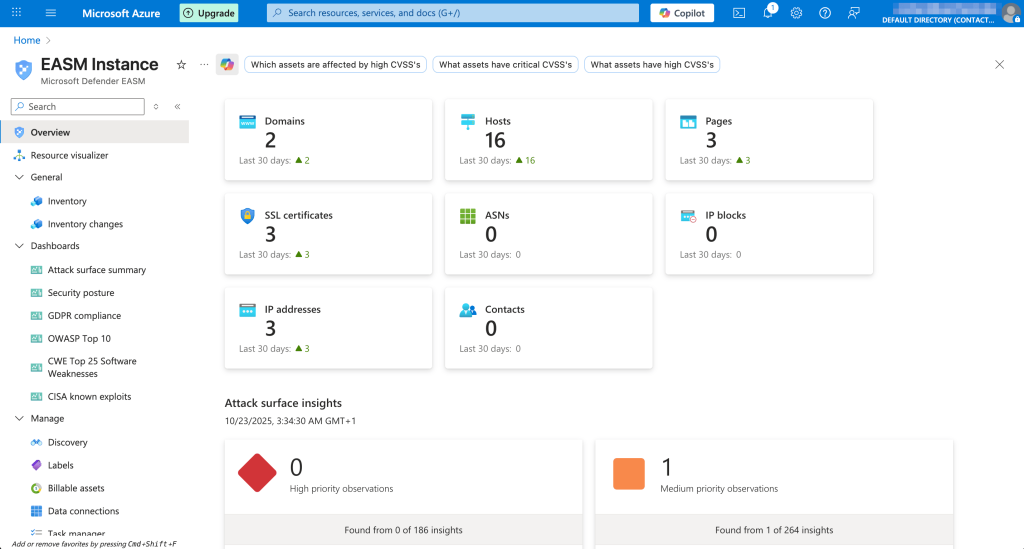
Every asset that Defender EASM discovers (or takes as a seed) is displayed under the Inventory tab. Here’s the list of asset types that Defender EASM can discover:
- Domains
- Hosts
- Pages
- SSL certificates
- ASNs
- IP netblocks
- IP addresses
- Contacts (email addresses)
When displaying the assets, Defender EASM has very flexible filters if you want to look into some specific portion of your assets, allowing you to combine the filters as well. When Defender EASM stumbles upon a new domain that it thinks can be related to your attack surface, it adds it to the list of candidates for you to approve it. After approval, Microsoft’s platform will run discovery for it as well.
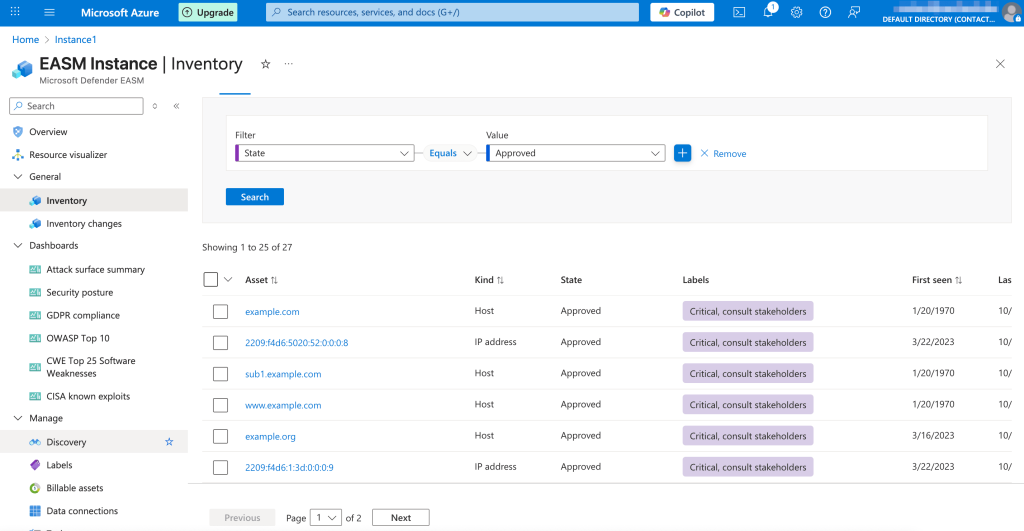
Normally, Defender EASM runs discovery scans weekly, but we’ve seen it run slightly more often. You can also trigger a scan manually.
Asset Discovery with Attaxion
Attaxion is not very different from Defender EASM in terms of how you start — you begin with adding root assets, such as domains, IP ranges, or WHOIS organization names. From there, it expands the inventory using a mix of passive and active cyber reconnaissance techniques to uncover related domains, subdomains, SSL certificates, IP netblocks, open ports, contact details, and more.
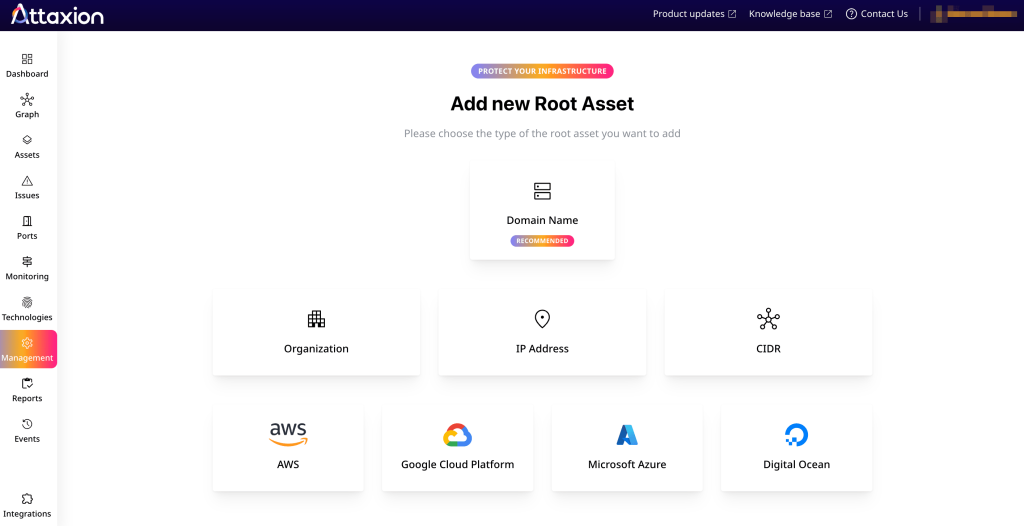
To protect against unauthorized scanning, Attaxion requires users to verify ownership of root assets before discovery continues. You can verify them by adding a TXT DNS record to a domain or uploading a text file to the root directory, for example.
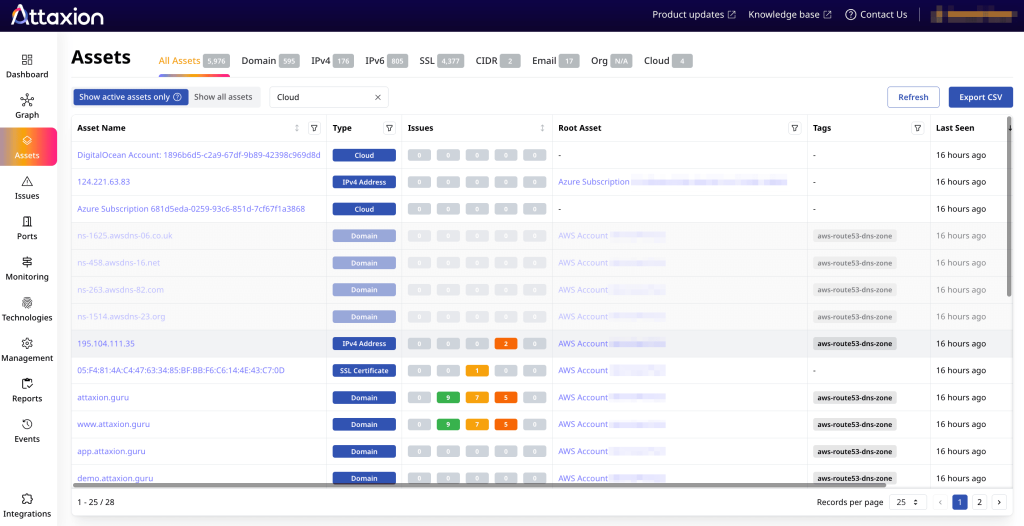
The process with root asset candidates works exactly like it does in Defender EASM — newly discovered domains become candidates that you need to approve before discovery proceeds.
In addition to the more traditional ways of adding assets, Attaxion supports cloud connectors. You can link Attaxion directly to your AWS, GCP, Azure, or DigitalOcean account to pull asset lists straight from your cloud environments. When you add new resources to this infrastructure, they’re automatically added to Attaxion as well.
Attaxion allows you to choose between using only passive or passive and active reconnaissance. Passive mode offers a stealthier approach that is guaranteed not to trigger intrusion detection systems, while active mode enables better discovery and vulnerability scanning.
How They Compare
When it comes to discovery, the two platforms are mostly similar. Defender EASM makes it a little more convenient by not requiring you to verify seed assets. But its discovery is slower (took it more than 48 hours to show any discovered assets) and runs infrequently, while Attaxion delivers first results in about an hour after verifying the first root asset and runs discovery scans roughly daily.
Also, for our test infrastructure, Attaxion found a few more active subdomains than Defender EASM.
 PART 3
PART 3
Vulnerability Scanning
Vulnerability Scanning with Microsoft Defender EASM
Upon discovering assets, Microsoft Defender EASM scans them for vulnerabilities and uses a proprietary vulnerability scanner for that. It doesn’t have a dedicated vulnerability tab though. Instead, it takes a dashboard-focused approach, offering several theme-based dashboards and showing related findings on them, including vulnerability and misconfiguration data.
The easiest way to see what’s vulnerable or needs attention is to go to the Attack Surface Summary dashboard, which shows issues (or observations, as Microsoft calls them) divided into three groups by severity: high, medium, and low. High and medium categories primarily reference different CVEs tied to technologies, while low-priority items include things like expired SSL certificates, self-signed certs, expired domains, and so on.
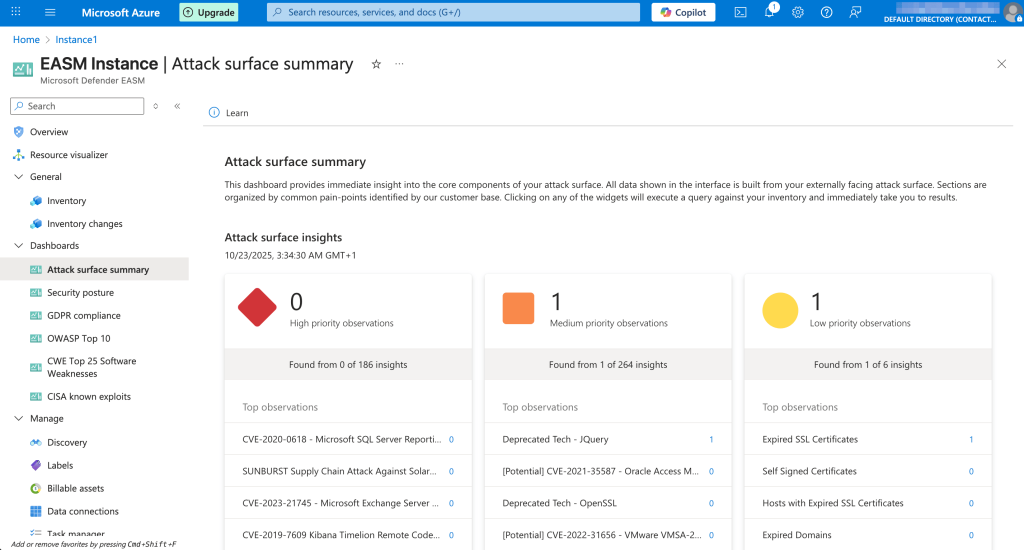
There’s also the CISA Known Exploits view that shows which of the discovered CVEs map to the CISA KEV catalog of actively exploited vulnerabilities. Two more dashboards are dedicated to CWE Top 25 and OWASP Top 10, highlighting any matching software weaknesses present in the attack surface.
The GDPR Compliance tab reports on things like SSL certificate expiration, PII exposure, login configuration, and cookie posture. Finally, the Security Posture tab summarizes CVE exposure, domain registrar and registrant data, open ports, and related infrastructure details.
Microsoft’s “there’s a dashboard for that” approach is both a blessing and a curse: while some dashboards are really useful, it would’ve also been just as useful to have a dedicated vulnerabilities tab for the entire attack surface, from which you could’ve drilled down into details. Every other attack surface management solution we’ve tried has that tab.
In general, this unconventional approach to UI (and that’s just one example, the entire UI is somewhat unusual) makes Microsoft EASM’s learning curve steeper.
When it comes to actual scanning results, for our test infrastructure, Defender EASM flagged just one issue — an expired certificate. We’re pretty sure there are more, including outdated tech. The attack surface overview includes a “Requires Investigation” category, and a couple of our assets were flagged as such. But Defender EASM didn’t show any supporting observations — why were they flagged — making next steps unclear.
Vulnerability Scanning with Attaxion
Attaxion uses a mix of vulnerability scanning tools, including ZAP by Checkmarx for web application scanning. Every issue that it finds, including vulnerabilities, misconfigurations, and more appear in the Issues tab, where the dashboard shows issue distribution by severity and highlights how the security posture has changed over time.
Below the dashboard, Attaxion lists all unique vulnerabilities across the environment. Clicking on a vulnerability reveals the affected assets, and from there, you can drill down into the full issue details, including status (open or possibly fixed), technical context, remediation guidance, and links to external references.
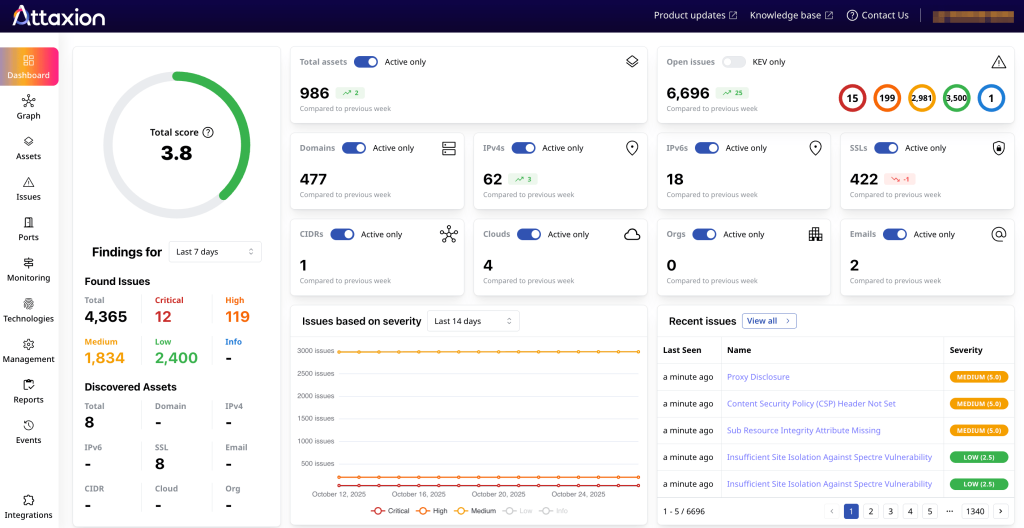
You can mark findings as fixed, accepted risk, or false positive, and track their lifecycle directly in the platform. While you can’t trigger vulnerability scans manually, Attaxion handles this automatically with daily rescans to keep exposure data up to date.
How They Compare
In testing, Attaxion surfaced significantly more relevant issues across test infrastructure compared to Defender EASM. Its interface is also a little more straightforward. Defender’s stronger side is dashboards for CWE Top 25, OWASP Top 10, and more, giving you information about your attack surface from these specific angles at a glance.
 PART 4
PART 4
Vulnerability Prioritization and Remediation
Vulnerability Prioritization and Remediation with Microsoft Defender EASM
With prioritization, Defender EASM extends the usual basic prioritization by severity ratings — high, medium, and low — with helpful context via a dedicated CISA Known Exploits dashboard. This view filters vulnerabilities that appear in the CISA KEV catalog, allowing teams to focus on exposures known to be actively exploited.
Another helpful tool for prioritization is tagging. Assets can be tagged either manually or by policies — rules that trigger upon detection of certain things in the attack surface and can assign tags to assets. That helps teams categorize and prioritize findings by business relevance or operational context.
Defender EASM doesn’t include built-in remediation workflows. To assign tasks or integrate with systems like Jira, you’ll need to first connect the platform to either Defender for Cloud or Azure Log Analytics. From there, you can connect to Jira or other ticketing systems.
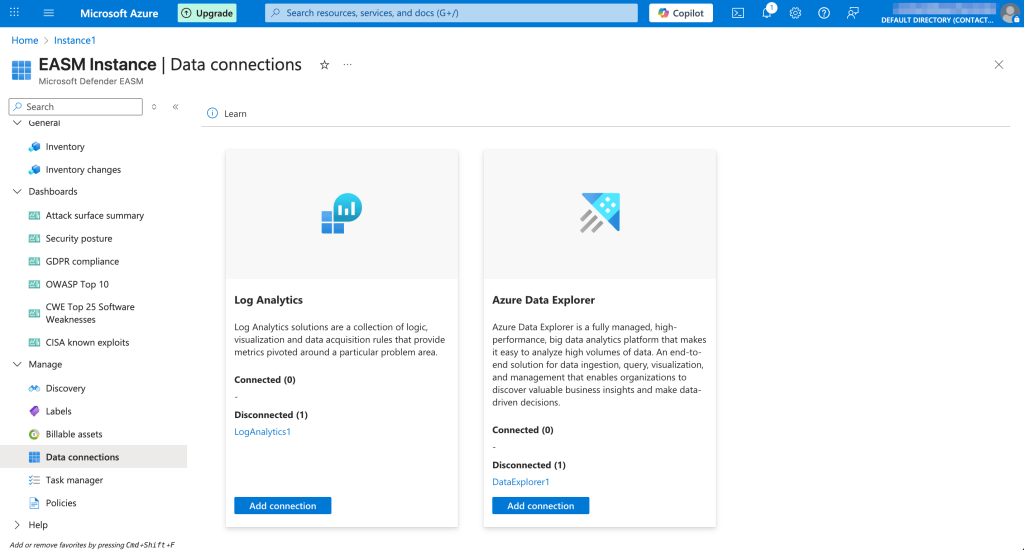
It’s understandable why Microsoft takes this route: why build connectors for an app when you can instead connect it to your other app that already has those connectors? It also helps get all the security data in one place. But at the same time, it makes things unnecessarily complicated and forces you to get even more ties with Azure.
Overall, to work with Defender EASM, it would really help to have an engineer with Azure experience on the team, and for those without Azure experience the process of integrating everything may feel daunting.
Vulnerability Prioritization & Remediation with Attaxion
Attaxion makes risk-based prioritization more practical by layering multiple signals. In addition to CVSS and CISA KEV data, for each CVE it also includes EPSS scores, helping teams quickly assess which vulnerabilities are most likely to be exploited in the real world. An integration with the EU vulnerability database (EUVD) has also been introduced recently to ensure even broader context and add regional specifics.
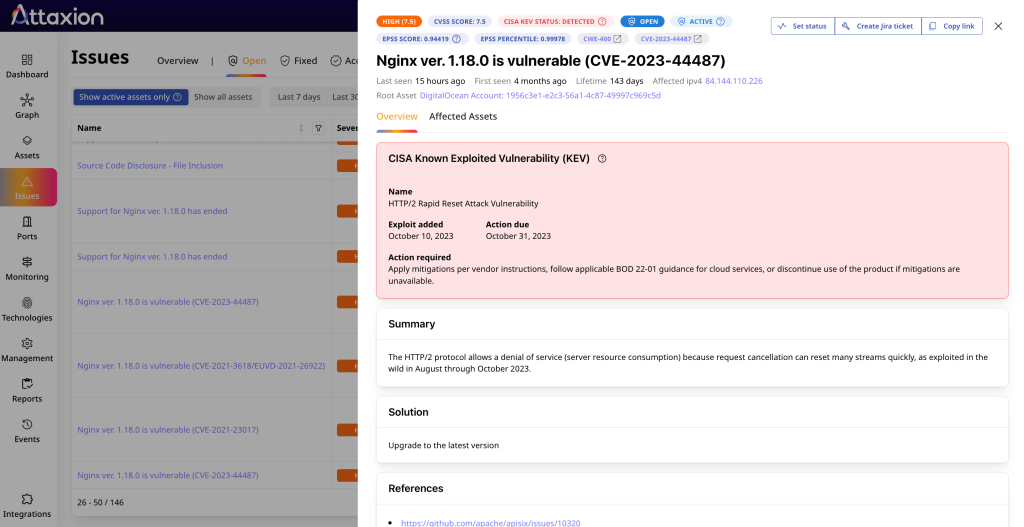
Attaxion applies some tags to assets automatically, but you can also add them manually. There is no way to set up policy-based tagging, but the combination of existing rules and manual tagging already covers most use cases for tags helping prioritizing by risk or business impact. Tags can be also added, removed, or modified via the API.
When it comes to remediation, Attaxion shows all the necessary vulnerability details and actionable advice, which you can use to populate Jira tickets for remediation in one click. If you need custom workflows, Attaxion provides an API you can use to connect with ticketing systems or other tools in your stack.
How They Compare
Attaxion is a clear winner in prioritization, thanks to the additional context added by EPSS and the EUVD integration. With remediation, it’s a bit more complicated: Attaxion has a straightforward integration with Jira to create support tickets with remediation suggestions, while Defender EASM makes you go through setting up additional tools, but then offers more integrations.
 PART 5
PART 5
Continuous Monitoring
Continuous Monitoring with Defender EASM
Defender EASM performs regular discovery scans to detect new assets and surface changes across the organization’s external attack surface. By default, scans are set to run weekly, but in reality they are a little more frequent, and you can also trigger a discovery scan to run manually through the Discovery view under the Manage section. Any newly identified assets are automatically evaluated for exposure and vulnerability risks. There is no way to manually trigger a vulnerability scan though, only the asset discovery scans.
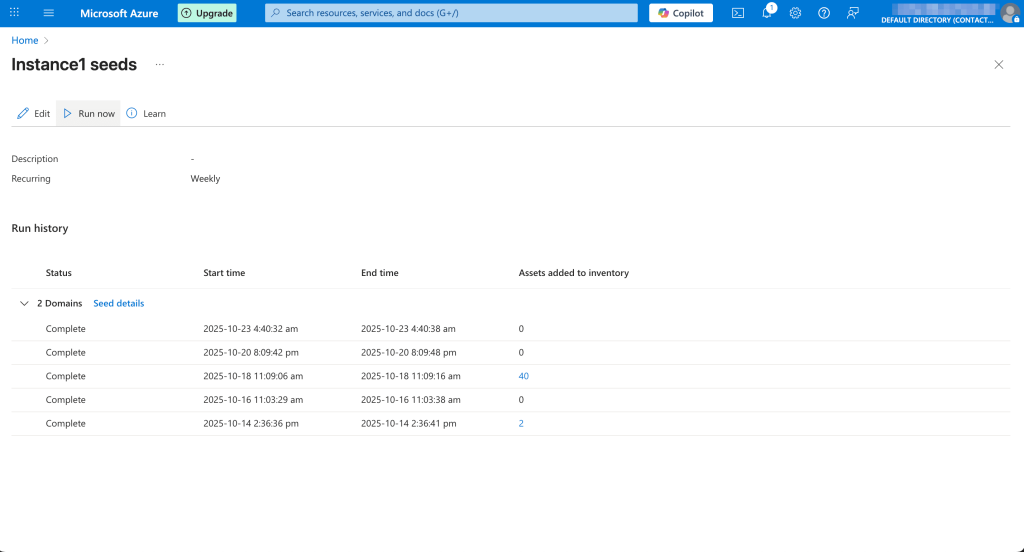
Unlike other platforms, Defender EASM doesn’t support native alerting. To enable notifications, users must connect the instance to Log Analytics or Azure Data Explorer. From there, you can set up connections with messengers and generate alerts, but, as we’ve already discussed, the setup isn’t straightforward and requires additional Azure knowledge.
Defender EASM supports reporting through its Copilot integration (but Copilot needs to be set up first) or through the very same Log Analytics connector — there’s no way to generate reports from the tool itself.
Continuous Monitoring with Attaxion
Attaxion scans the entire external attack surface much more frequently (daily on average), with discovery and vulnerability scanning for newly found assets running automatically. You can set up alerts for newly discovered assets, vulnerabilities (by severity), and more. Alerts are delivered either via email or via Slack.
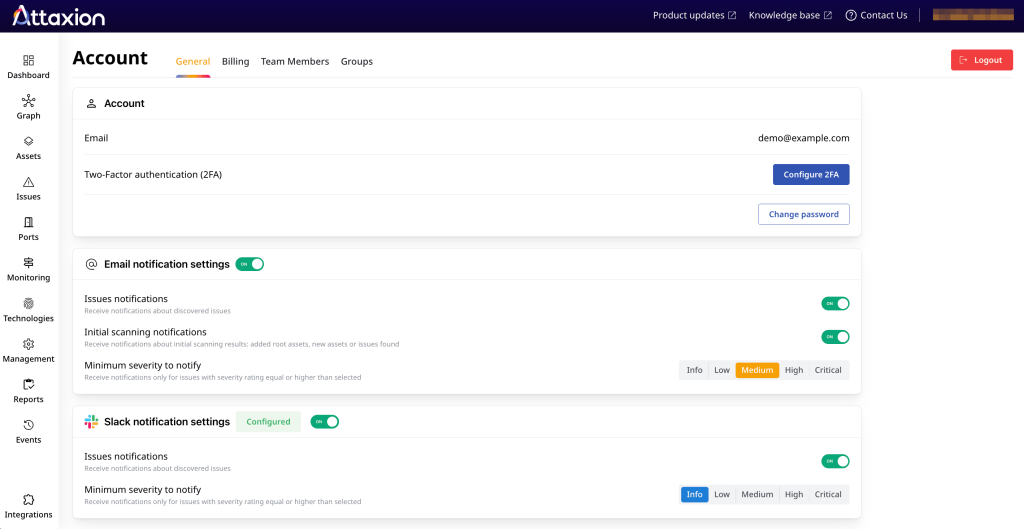
You can also generate vulnerability reports that can be customized to include specific assets or, for example, only vulnerabilities listed in the CISA KEV catalog.
Attaxion also has two unique features that are related to continuous monitoring: Agentless Threat Hunting and the IoC Database Monitoring.
Agentless Threat Hunting shows you the NetFlow traffic between IPs in your infrastructure and external IPs, using threat intelligence to highlight traffic to and from known malicious assets. It doesn’t require you to install any agents, upload PCAPs, or anything else — it starts working immediately after you enable it and even offers retroactive data for the last 30 days.
The IoC Database Monitoring matches your assets against a continuously updated database of indicators of compromise (IoCs) and tells you if your assets share infrastructure with known malicious domains or are connected to known malicious IPs.
How They Compare
Attaxion wins this comparison as well, not only because of the scanning frequency that averages daily, but also thanks to its additional monitoring capabilities that allow for network traffic analysis and infrastructure reputation monitoring.
 PART 6
PART 6
Conclusion
Microsoft Defender EASM stands out from the rest of the EASM crowd because of its distinctly Microsoft approach to everything: the UI would be mostly familiar to Azure users, the connections to other Azure services make it much more powerful and give it almost limitless integration capabilities, including with products from the Defender line and Microsoft Sentinel. Its other stronger sides include nice dashboards and the ability to introduce security policies.
At the same time, Defender EASM is clearly not designed to be used on its own. It needs to be connected to Defender for Cloud to enable support ticket creation for remediation, and to Log Analytics to enable notifications. Microsoft pushes you to use more of its products, increasing the spend. For those heavily invested in Azure, that’s probably fine, but for those with more diverse infrastructure, that’s not a welcome push.
That’s why security teams keep looking for Defender EASM alternatives. As one such alternative, Attaxion offers the same main functionality, but it also makes it easy to send alerts, generate reports, and integrate with other tools. On top of that, it has unique functions like Agentless Traffic Monitoring and IoC Database Monitoring that help with threat hunting and risk prioritization.
Perhaps, most importantly, in our comparison Attaxion proved to be more effective in the two main EASM disciplines: it found more assets and more vulnerabilities than Defender EASM. That, together with the more friendly UI and lower costs, make it a great Defender EASM alternative for small security teams.
Ready to discover and manage your external attack surface with Attaxion? Start a 30-day free trial, or request a personal demo.