Reduce Your External Attack Surface
Catalog known and unknown assets across your entire external attack surface. Identify vulnerable technology and misconfigurations, prioritize them, and speed up remediation.
What our clients say
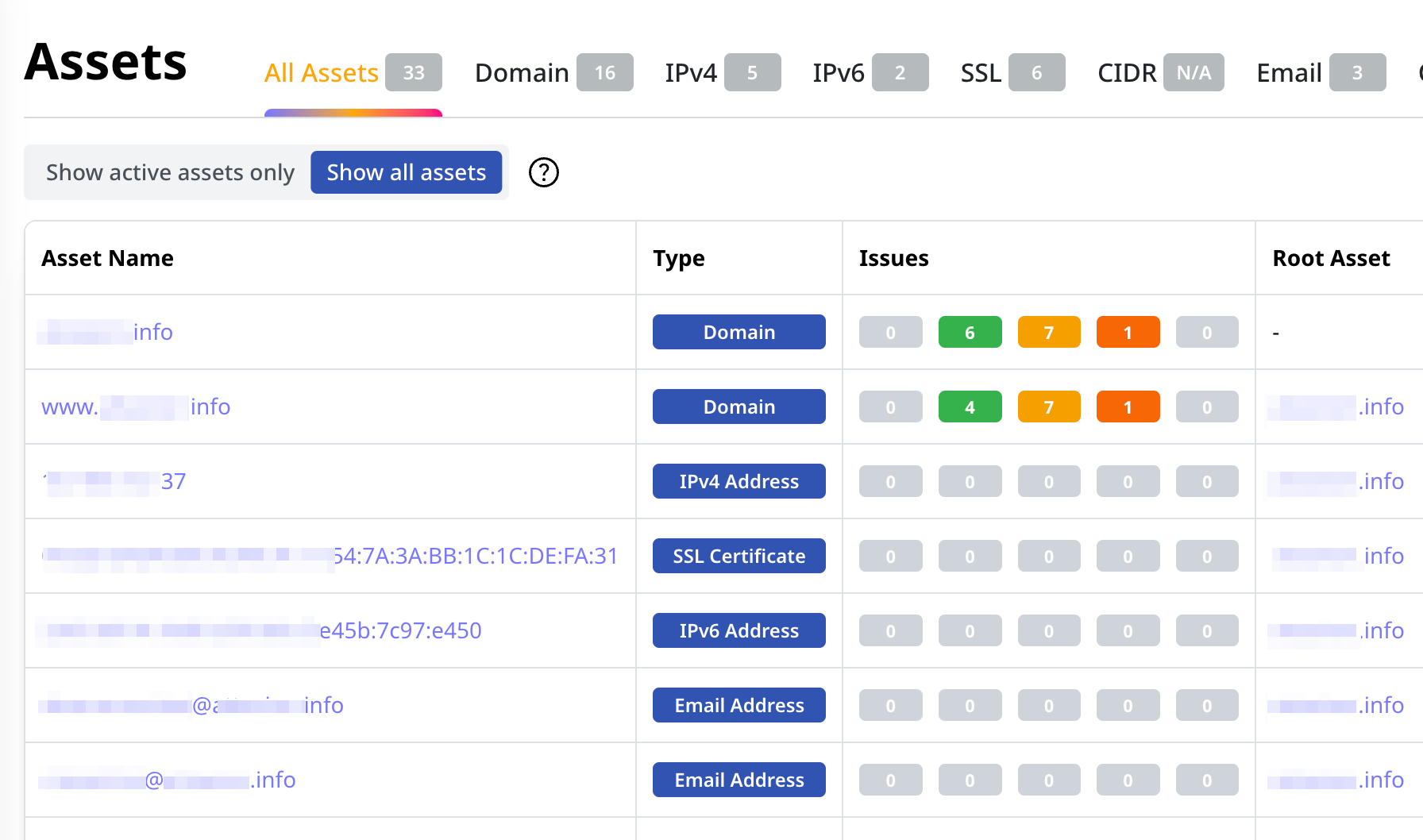
Get a Complete Asset Inventory
With its advanced cyber reconnaissance techniques, Attaxion builds a complete and automatically updated list of your external assets.
Learn more:
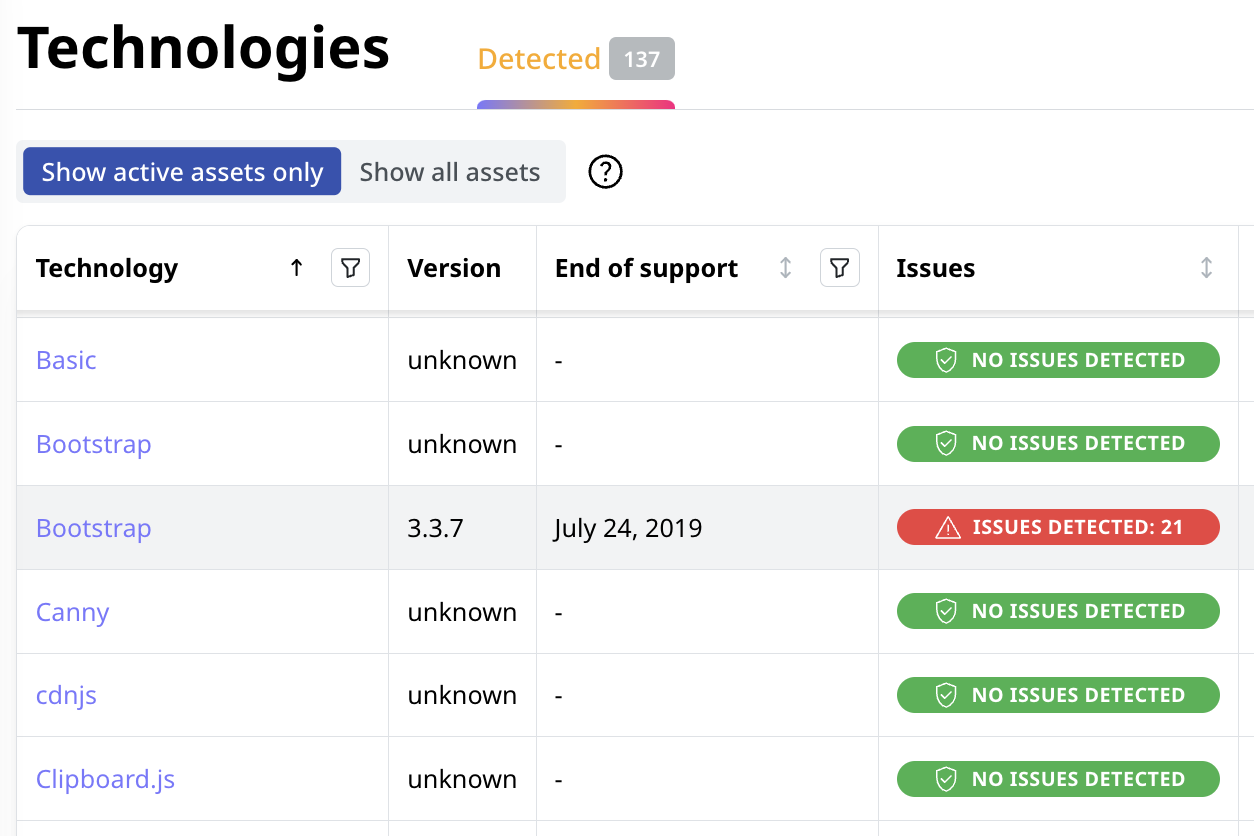
Identify Third-Party Technologies
In addition to a full asset inventory, Attaxion identifies third-party technologies used within your organization, highlighting vulnerable versions and associated assets.
Learn more:
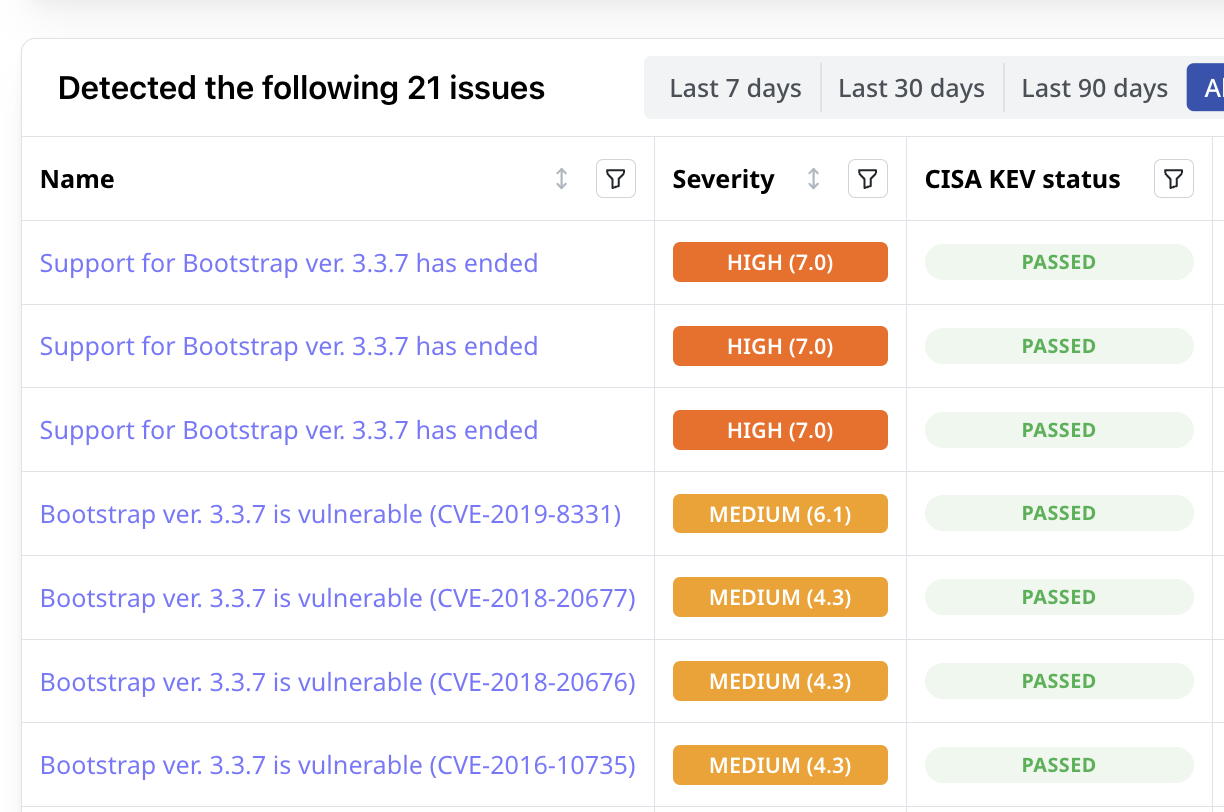
Prioritize Issues Based on Their Potential Impact
Attaxion finds security issues such as vulnerabilities, open ports, and misconfigurations in your internet-facing infrastructure. It then helps you prioritize them based on their severity, exploitability, and historical exploitation data.
Learn more:
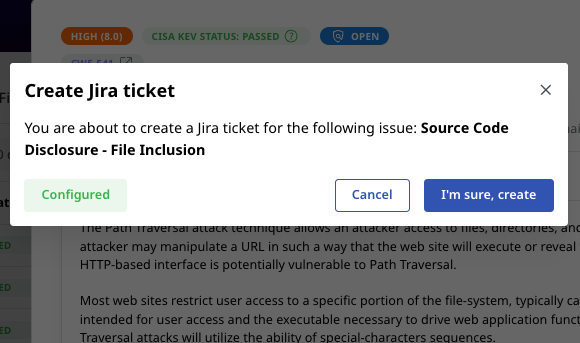
Speed Up Remediation
Create support tickets for issues with remediation advice in 1 click.
Learn more:
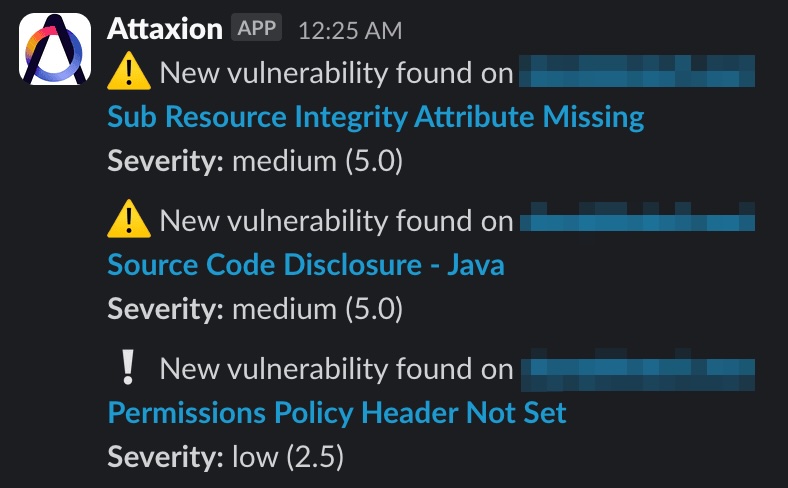
Get Notified About New Issues
Attaxion continuously discovers new assets and scans your entire asset inventory for vulnerabilities and emerging threats. Stay on top of potential issues with timely notifications and reports.
Learn more:
Start Using Attaxion for Attack Surface Management
Get started in a few clicks and get the first results in 2 hours. Attaxion is easy to navigate and continuously provides a complete image of your organization’s external attack surface, speeding up prioritization and remediation.
Why Choose Attaxion for Cybersecurity Compliance?
-
Highest Asset Coverage
Attaxion can discover more external assets than other solutions, providing you with the most complete picture of your external attack surface.
-
Actionable Vulnerability Assessment
Attaxion provides you with a detailed vulnerability assessment, helping prioritize issues with CVSS and EPSS scores and CISA KEV data alongside actionable remediation suggestions.
-
Asset-Based Pricing
Nowadays, external attack surface management is important for everyone, not just giant corporations. Attaxion has a plan for organizations of all sizes – from small businesses with a growing digital footprint to large enterprises with tens of thousands of internet-facing assets.
Featured Resources
- Guides

Detecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the reason can be a security weaknes[...]

10 Critical Attack Surface Metrics to Track
With recent regulatory changes pushing cybersecurity to the boardroom, effective attack surface monitoring and visualization techniques are more cruci[...]

External Attack Surface Management (EASM): The Complete Starter Guide
This detailed guide tackles everything you need to know about EASM and how to start attack surface reduction.