Test Web Application Security
Run fully automated security testing for web apps across your entire external attack surface and speed up vulnerability prioritization and mitigation.
What our clients say
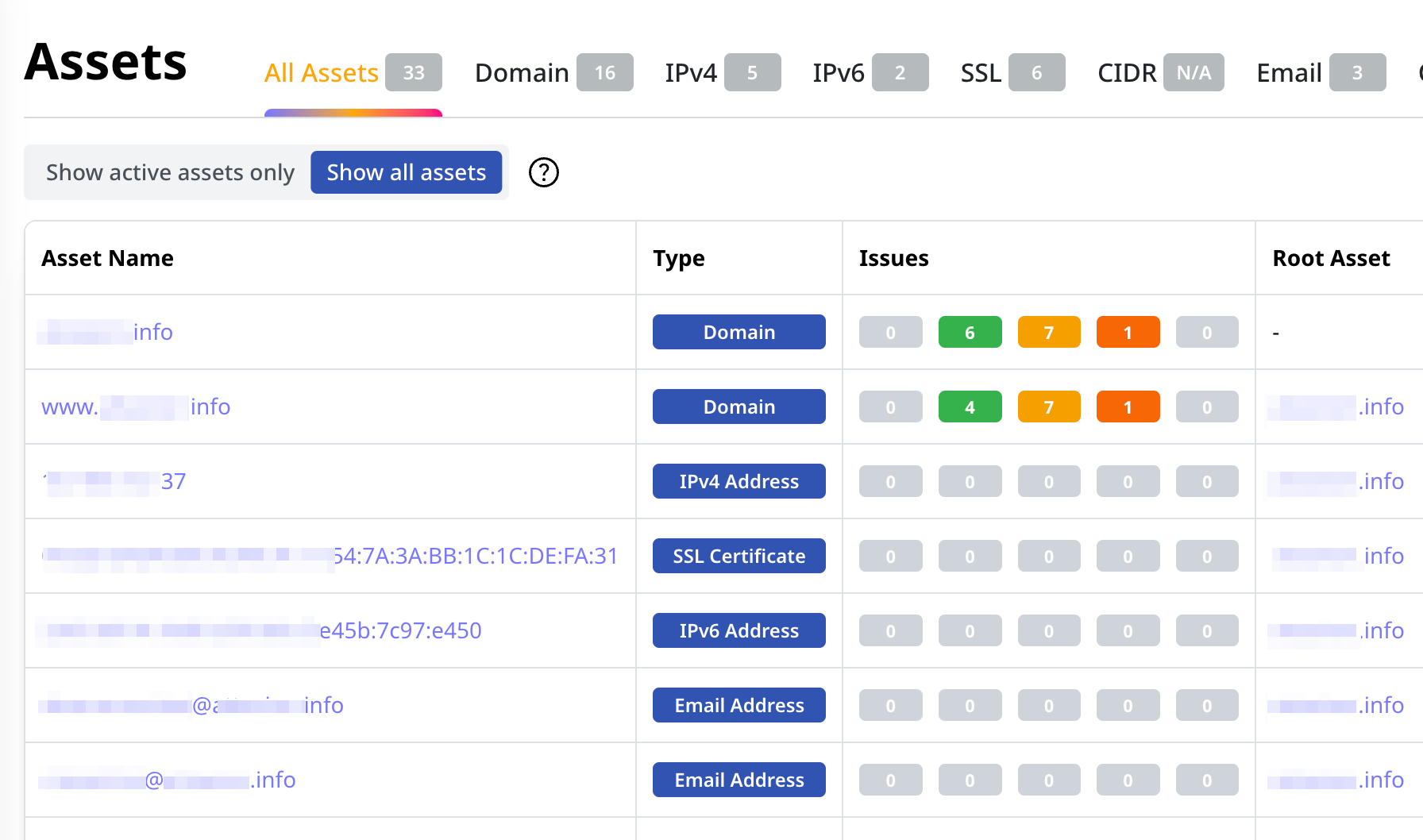
Find and Test All Your Web Apps
Don’t limit yourself to the chosen few – Attaxion discovers web applications across your entire external attack surface, including those you didn’t know or forgot about.
Learn more:
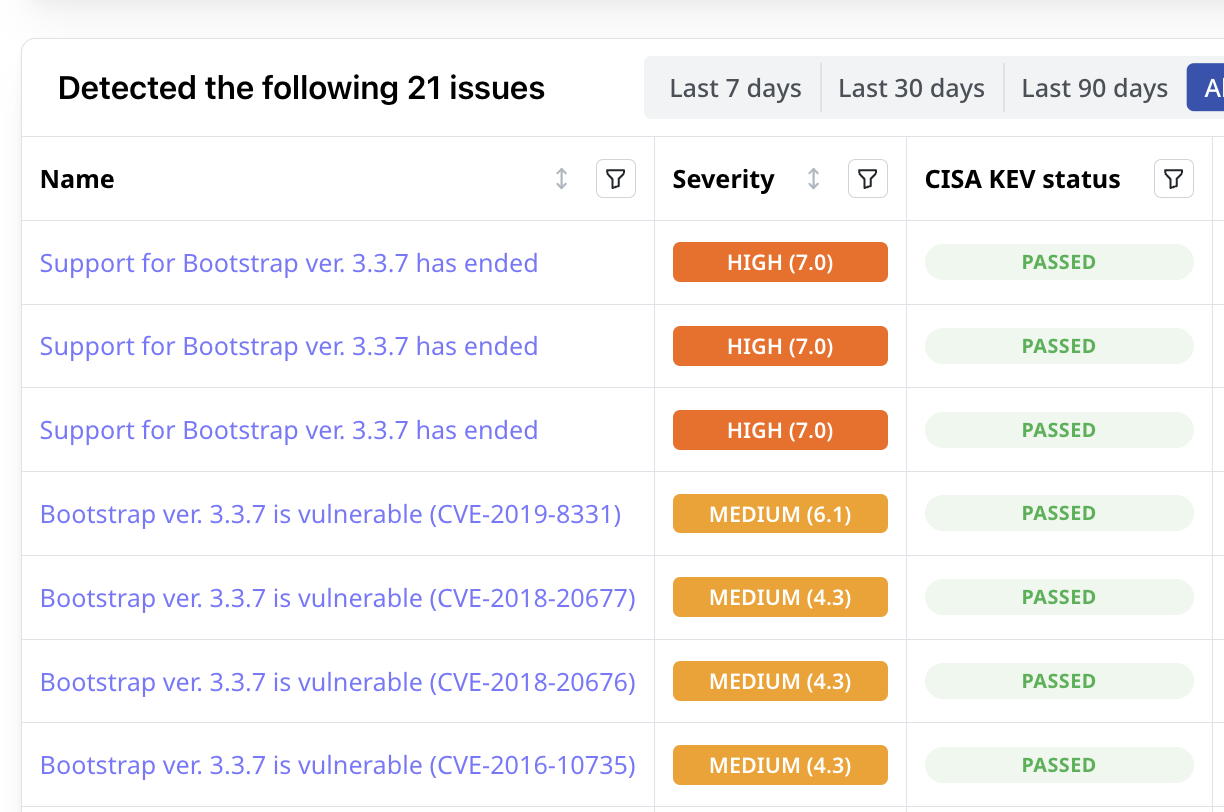
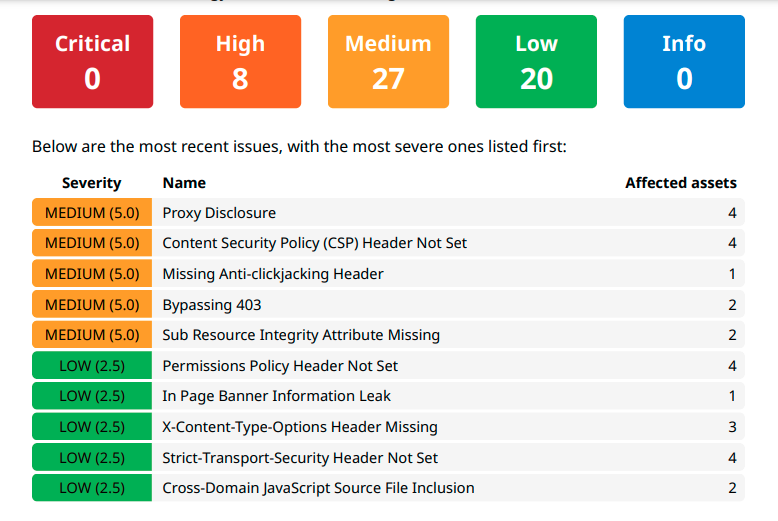
Identify Vulnerabilities, Exposures, and Misconfigurations
Attaxion finds issues plaguing web applications, be it vulnerable third-party technology, XSS, open ports, or something else. Get a complete vulnerability assessment for all your web applications.
Learn more:
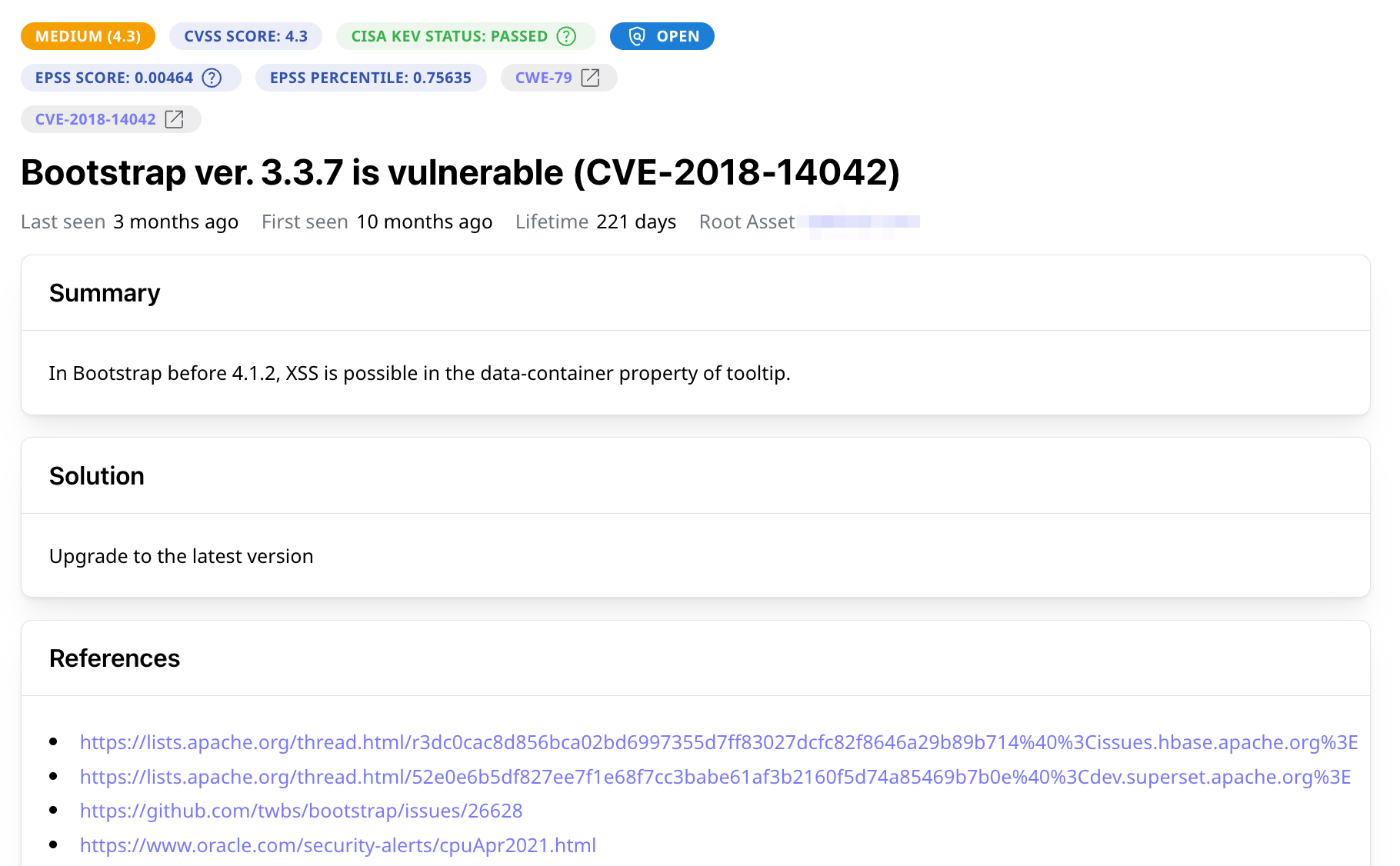
Prioritize and Remediate Issues
First things first: with EPSS and CISA KEV data, Attaxion helps you prioritize critical issues that are more likely to be exploited or even known to be exploited in the wild. Speed up the process – create support tickets with information about issues in 1 click.
Learn more:
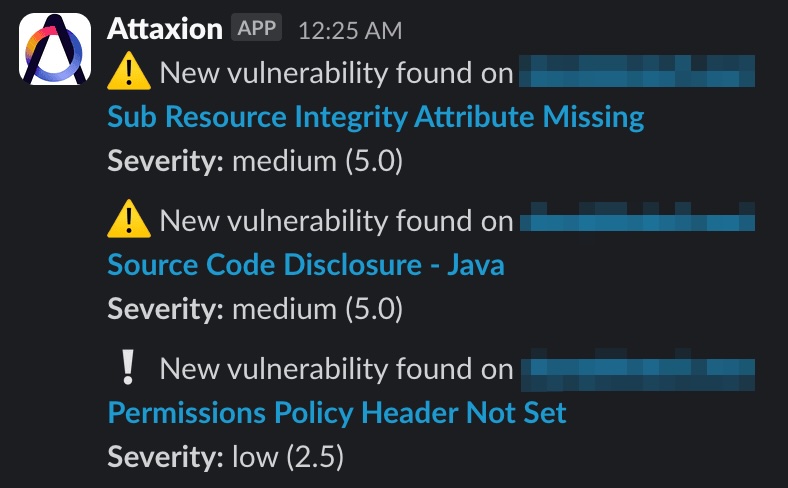
Get Notified About New Issues
Attaxion’s vulnerability catalog is regularly updated with new entries, and it continuously runs scans across all of your web applications, discovering assets vulnerable to emerging threats.
Learn more:
Demonstrate Progress with Reports and Dashboards
Make your work easy to understand for stakeholders with detailed reports for each web app you manage.
Learn more:
Start Using Attaxion for Dynamic Application Security Testing
Get started in a few clicks and get the first results in less than 2 hours. Attaxion is easy to navigate and provides a complete image of your organization’s external attack surface, including all the web apps.
Why Choose Attaxion for Cybersecurity Compliance?
-
Unmatched Asset Discovery
Attaxion can discover more external assets than other solutions, leaving no web app in your organization’s infrastructure unsecured.
-
Complete Third-Party Technology Inventory
Attaxion builds and maintains a complete inventory of the third-party technologies used across all your web apps, highlighting technology versions and related assets that pose higher risks.
-
No Downtime or Disruption
Forget postponing scans because you’re worried about business continuity. Attaxion continuously analyzes your web applications and finds vulnerabilities and misconfigurations without causing any disruptions.
Frequently Asked Questions
Featured Resources

Detecting the Top 25 CWEs with EASM
Everything happens for a reason. For most vulnerabilities on the Common Vulnerabilities and Exposures (CVE) list, the reason can be a security weaknes[...]

Active and Passive Vulnerability Scanning: What Is the Difference?
Vulnerability scanning is an integral part of attack surface analysis, helping security teams identify security issues, misconfigurations, and weaknes[...]

OWASP Top 10 Vulnerabilities Detection through EASM
Threat actors strategically capitalize on their knowledge of existing vulnerabilities to target susceptible victims. They tend to exploit older vulner[...]