Top External Attack Surface Management Vendors
There’s hardly any organization that has decreased its digital footprint over the past few years. It only keeps increasing, for everyone.
The growing number of digital assets requires solutions that can provide inventory, information, protection, and continuous monitoring for all of them at once. These solutions must also automatically add new internet-facing assets to the inventory as they appear in the organization’s network.
That means that external attack surface management (EASM) platforms have become a must-have information security tool for companies of all sizes.
Where there’s demand, there’s supply, so many security vendors have introduced their own attack surface management solutions.
In this article, we provide a guide on choosing the best EASM platform for your specific needs. We explain how to evaluate an External Attack Surface Management platform, what features and qualities to look for, and also provide a list of the best EASM platforms to choose from.
Table of Contents
How to Choose the Right External Attack Surface Management Platform for Your Needs
A great EASM platform should excel at the namesake process – external attack surface management. We have an entire guide dedicated to EASM which we recommend you to check. Here, we’ll quickly list the 4 main steps of the EASM process: asset discovery & vulnerability scanning, vulnerability prioritization, vulnerability remediation, and continuous monitoring.
A great EASM tool should perform all of these steps well.
Key EASM Platform Features
Asset Discovery
One of the most important tasks for any EASM platform is discovering known and unknown internet-facing assets that the organization has and helping security teams build an asset inventory.
That goes beyond subdomain enumeration. EASM platforms often employ various cyber reconnaissance techniques, allowing them to find open ports, IP addresses, and sometimes even leaked email addresses. So, where do EASM platforms differ when it comes to asset discovery?
- Asset types. The more different asset types a platform can discover for you, the closer to covering the entire attack surface it gets.
- Asset coverage. Reconnaissance techniques differ from platform to platform, which makes some of them more effective at discovering known and unknown assets than others. The higher the asset coverage – the better: it provides more visibility into the organization’s attack surface.
- Turnaround time for root asset verification. Attack surface management tools require you to add and verify ownership of several root assets so that the tool can search for related assets. Sometimes this verification requires adding a DNS record or a text file, sometimes it’s a fully manual process between the security team and the customer support team of the tool. This takes some time – from about 5 minutes in some cases to about a month in others. The shorter the time from submitting a root asset to starting a scan, the faster you can get value out of the EASM tool.
Vulnerability Scanning
As an EASM tool discovers new assets, it scans them for vulnerabilities. It also keeps regularly scanning existing assets to verify if the vulnerabilities were fixed or if there are new, previously unknown ones. The main differentiators here are the vulnerability databases used and the vulnerability scanner.
- Vulnerability scanner. Some scanners are more capable of detecting vulnerabilities than others. Of course, the better the scanner, the better picture of your attack surface you can get.
- False positives. In an attempt to make their scanners find more vulnerabilities, some vendors introduce another problem – lots of false positives. Going through hundreds of false positives slows down addressing real problems and is very frustrating for the security teams. Obviously, the fewer false positives, the better. Some EASM vendors use payload-based scanners, which reduce the number of false positives.
- Vulnerability databases. A scanner can only detect a vulnerability that is known to it. So, the quality of vulnerability databases matters a lot. Some vendors also employ crowdsourcing so that their scanners can find vulnerabilities that haven’t yet been added to official databases.
Vulnerability Prioritization and Remediation
EASM platforms are often used for vulnerability management, so the ease and flexibility of prioritizing the most critical issues is an important factor when choosing EASM software.
- Prioritization flexibility. Some vendors only allow to prioritize vulnerabilities by severity (critical vulnerabilities, high severity, medium severity, and low severity). Some add scores such as CVSS and EPSS to the mix. Few offer to prioritize also based on business criticality of the vulnerable asset and other factors. The more prioritization options, the better.
- Remediation options. Most EASM platforms offer to create tickets with support systems such as Jira and ServiceNow that contain all information about issues. That’s usually as much as they can help security teams with remediation. Very few have additional capabilities such as closing open ports with one click of a button, but these need deeper integration with your tech stack – this function doesn’t just work out of the box.
Continuous Monitoring
Continuous monitoring is the 4th step in the EASM process, and apparently, vendors have a different perception of the word “continuous”. For some, it’s regular – say, weekly scans. For others, it’s the same plus scans that are triggered by events like adding a new vulnerability to the database.
Few EASM vendors offer the ability to prioritize assets, allowing some to be scanned more frequently and others less often. Finally, there are very few that truly scan continuously, without ever pausing the scanner.
What Else to Look For In an EASM Platform
Scalability & Pricing
External attack surface management vendors often charge their customers for the size of the attack surface they need to cover. But often, the pricing is very obscure.
Few vendors – like Attaxion and Intruder – have public pricing that gives the prospects an idea of how much they will need to pay for the tool. Some other external attack surface management companies – like Detectify – provide only the starting price and leave the rest to discussion.
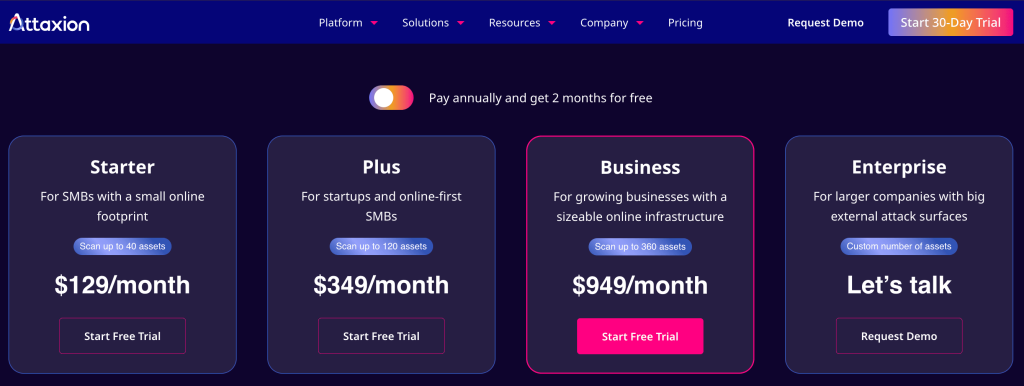
Most vendors, however, hide the pricing completely. Usually, that means that even the starting price is very high and not accessible for small or medium-sized companies.
In our experience, the prices that different EASM vendors ask for almost the same functionality may differ by a couple of orders of magnitude.
Integrations
EASM tools assume an outside-in perspective and do not depend on the rest of your security tech stack to function. However, it’s always convenient when you can integrate your tech stack to make the most out of it.
So, one of the important parameters to look for when choosing an external attack surface management tool is integrations with other tools – from messengers to task trackers, and from compliance platforms to SIEM tools.
Reporting
One of the main reasons why security teams use EASM software is to meet compliance requirements. Some platforms offer to just create reports that list assets or vulnerabilities, while others have reports tailored to specific regulations like GDPR, CCPA, PCI, and more.
Setup and Maintenance
Some EASM platforms are easier to start working with than others – that depends on the user-friendliness of the interface, the amount of customization available, and whether the tool requires deployment or not. Most EASM platforms are user friendly and do not require any deployment, however, for some, the process of setting everything up is quite tedious.
Usually, it’s a trade-off for customization – the more things you can tweak to suit your own needs, the more difficult the setup process would be.
Support and Training
Just like with every SaaS platform, the quality of support matters: how fast they reply, how helpful they are, the quality of documentation, and more.
Some vendors offer to train your security team to use the tool, some just point to the documentation and rely on automatic onboarding.
Top EASM Vendors and Platforms
1. Attaxion
Attaxion is an external attack surface management platform developed by a namesake vendor that stands out for two main reasons: having the widest asset coverage and being one of the most affordable EASM solutions at the same time.
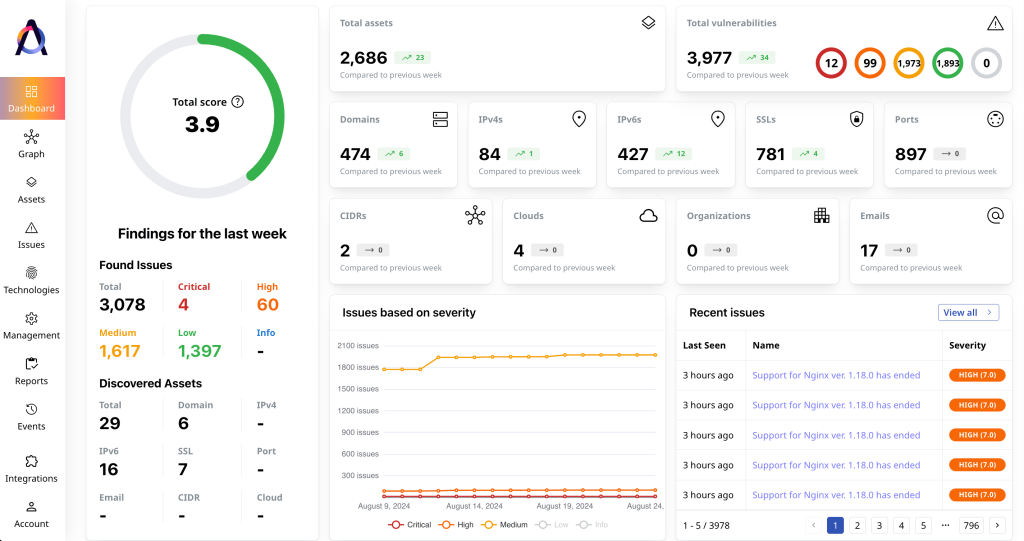
Attaxion’s Key Features and Differentiators
- Unmatched asset coverage. Attaxion typically finds more assets than any other EASM platform we’ve tested – all thanks to the many different reconnaissance techniques it uses for asset discovery.
- Scalability and affordability. Attaxion’s flexible pricing model makes it suitable for any kind of business – from SMBs to giant corporations. Starting at just $129/month (if paid monthly, annual plan is even cheaper), Attaxion is perhaps the most affordable EASM platform out there.
Attaxion Pros
In addition to superb coverage and accessible pricing, Attaxion has some other strong sides:
- Building dependency and discovery graphs to trace potential attack vectors and paths.
- Continuous scanning that helps find new assets and vulnerabilities much quicker.
- Integrations with GCP, AWS, Azure, and Digital Ocean.
- CISA KEV vulnerability detection – Attaxion points out if an issue is a known exploited vulnerability.
- EPSS score – in addition to CVSS, Attaxion also allows the use of the AI-based Exploit Prediction Scoring System for vulnerability prioritization.
- Quick time to value – initial setup takes a few minutes, and you get an overview of your organization’s attack surface in less than 24 hours.
- Low false positive rate.
Attaxion Cons
As a platform, Attaxion is quite young and it hasn’t yet amassed the sheer number of features and integrations that some other solutions have. So, its weaker sides are:
- Few integrations with ticketing systems and messengers.
- Not very flexible reporting options.
However, Attaxion is evolving rapidly, adding new features on a monthly basis, and also offering to build integrations on demand, which partially compensates for the lack of them.
Attaxion Demo and Pricing
Free trial: ✅(30 days)
Demo: ✅
Attaxion offers a short interactive demo tour for those who want to get a quick idea of the product in less than 60 seconds. In addition to that, Attaxion has a free 30-day trial if you’d like to explore the platform more in-depth and understand if it suits your needs.
When it comes to pricing, Attaxion doesn’t hide how much it costs. It’s one of the most affordable EASM software platforms out there, with monthly pricing starting as low as $129/month for an attack surface of up to 40 assets of all kinds.
The pricing is asset-based, and if the trial reveals that you have more than 360 assets in your attack surface, then it’s better to discuss the pricing with a sales rep.
Our Verdict on Attaxion
As the team behind Attaxion, we obviously are biased toward our product. But we’ve done a lot of competitor research and testing to objectively compare Attaxion with the rest of the platforms on the market.
Attaxion is among the best EASM platforms for those who care about actually protecting their external attack surface, rather than focusing on bells and whistles. Its superior coverage helps create a complete picture of an organization’s entire external attack surface and affordable price allows organizations with tight security budgets to still add modern and robust information security tools to their stack.
2. Microsoft Defender EASM
Microsoft Defender External Attack Surface Management (aka Defender EASM) is Microsoft’s own take on EASM. Like other EASM solutions, it continuously discovers and maps your organization’s digital attack surface to provide a holistic overview of its online infrastructure. Defender EASM is a part of a larger product called Microsoft Defender for Cloud.
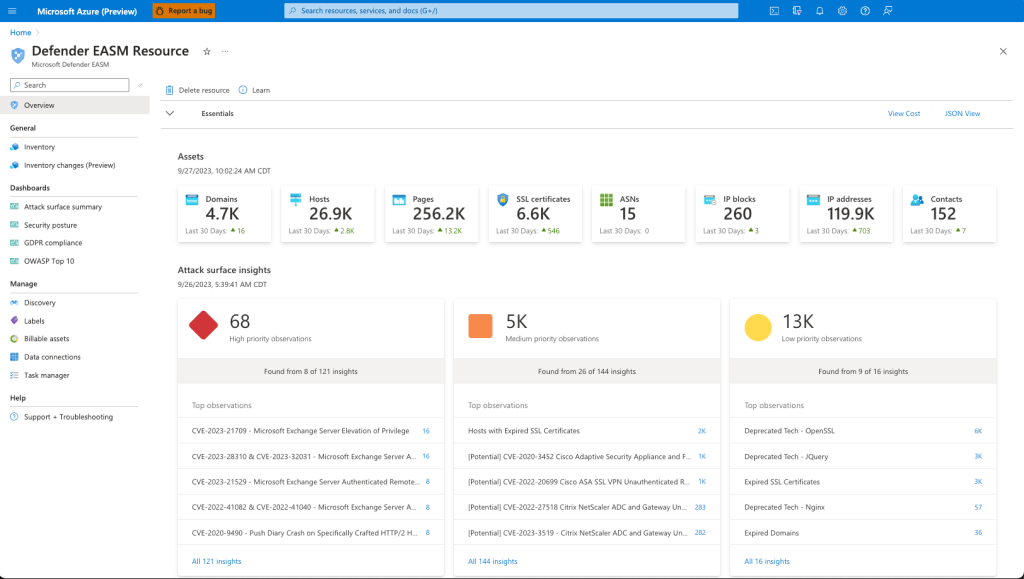
Microsoft Defender EASM’s Key Features and Differentiators
- Defender EASM is a part of Azure. Being a Microsoft product, it’s no surprise that Defender EASM is tied to Azure. You’ll need an Azure account to use it, and it’s easier to connect it to Azure instances, even though its parent product, Defender for Cloud, also supports GCP and AWS.
- Policy engine automation. Microsoft Defender EASM allows security teams to set up policies that automatically adjust asset status or parameters based on certain conditions. It doesn’t help with automatic remediation, but could be handy for prioritization and filtering.
Microsoft Defender EASM Pros
- Good support. Many G2 reviewers mistake Defender EASM for other Defenders, so not all its reviews are in fact about it. From the ones that are, it seems that the users liked their interactions with support.
- Integrations with the rest of Microsoft tech stack. Defender EASM integrates with other Defenders – Microsoft Defender for Endpoint, Microsoft Defender for Cloud, Microsoft Sentinel (SIEM), etc.
Microsoft Defender EASM Cons
- Azure-centric. If the majority of your infrastructure isn’t based in Microsoft Azure cloud, Defender EASM is likely not for you. It’s tightly tied to Azure in many aspects and is much less useful if you have a significant portion of your infrastructure sitting in Google’s or Amazon’s clouds.
- Complicated setup and not user-friendly. According to various G2 reviews, Defender EASM can be hard to set up and navigate in comparison to its competitors.
- Can be expensive. There are some complaints about Microsoft Defender EASM being expensive.
- High false positive rate. G2 users also complained about Defender EASM generating a lot of false positives.
Microsoft Defender EASM Demo and Pricing
Free trial: ✅(30 days)
Demo: ❌
Defender EASM is one of the few solutions that offer a free trial (for 30 days) and transparent pricing. It’s priced at $0.011 per asset per day. However, a lot of questions are raised about what is considered an asset (it seems that website pages are considered assets as well, which no other EASM platform does). So, despite looking transparent, the pricing is in fact quite obscure.
We couldn’t find a publicly available Defender EASM demo.
Our Verdict on Microsoft Defender EASM
If your organization’s infrastructure is based in Microsoft Azure, Defender EASM may be a very attractive solution. It’s relatively affordable for smaller attack surfaces and integrates well with the rest of Microsoft’s solutions. But if you don’t use Azure at all or have only a small portion of your infrastructure in it, EASM becomes much less attractive.
3. Censys ASM
Censys ASM is a logical extension of Censys’s business, with their main product being Censys Search, a search engine for internet-facing assets. Censys ASM is an external attack surface management platform that relies on Censys Search reconnaissance for asset discovery.
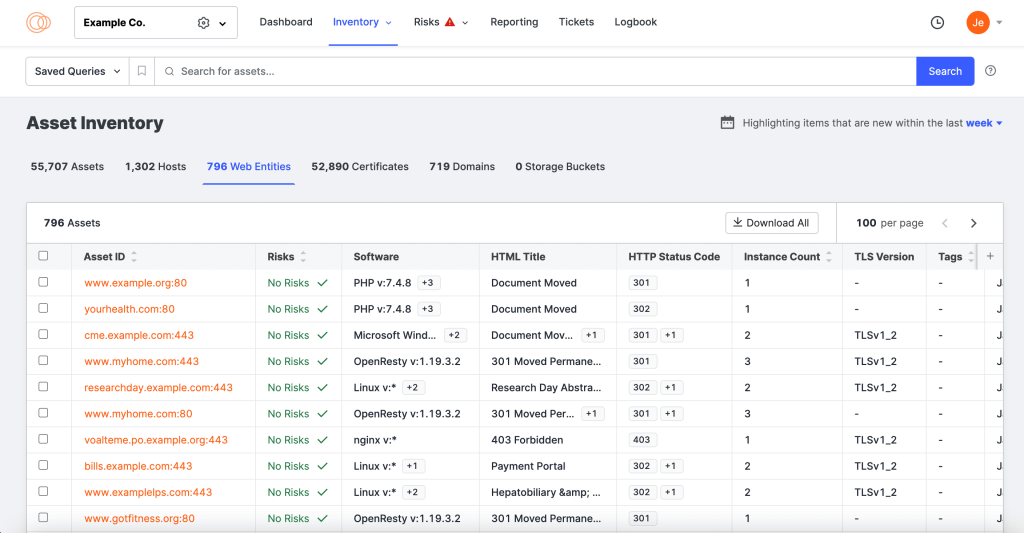
Censys ASM Key Features and Differentiators:
- High asset coverage. Censys ASM is among the platforms that manage to find the most assets. Not as many as Attaxion, but it’s still good at covering a huge part of the external attack surface. Gartner peer reviews also mention asset coverage as its stronger side.
- Non-standard port discovery. Censys ASM searches across the whole spectrum of ports (all 65k of them), allowing it to discover more potential attack vectors that can be used by potential external threats. Not all EASM platforms do that.
Censys ASM Pros:
- Convenient dashboards. Gartner peer reviews mention that users are particularly happy with Censys ASM’s dashboards.
- Integrations with Tenable VM and Microsoft Sentinel. In addition to typical integrations with messengers and support project management platforms, Censys ASM offers integration with a vulnerability management tool and a cloud-native SIEM tool.
- Manual severity adjustment. Censys ASM takes several variables into account when calculating issue severity, but you can adjust it manually for better risk prioritization.
Censys ASM Cons:
- Steep learning curve. Censys ASM doesn’t have overwhelming functionality, but it requires you to get acquainted with Censys Search Language Syntax to be able to query assets.
- Incomplete view of the organization’s digital footprint – Censys ASM doesn’t find all the internet-facing assets that an organization may have (according to a Gartner peer review)
Censys ASM Demo and Pricing
Free trial: ❌
Demo: ❌
Our Verdict on Censys ASM
Censys ASM is a relatively young EASM solution, aimed primarily at larger enterprises. Its main strength is the Censys Search engine under its hood which provides it with good asset coverage.
However, when it comes to functionality, Censys ASM doesn’t offer anything special that much more affordable solutions like Attaxion or Detectify don’t have. And the difference in price is drastic – Censys ASM starts at about $60,000 per year (according to a British government website that offers to sell it).
Read a detailed comparison between Censys ASM and Attaxion
4. Palo Alto Cortex Xpanse
Palo Alto Cortex Xpanse is an ASM tool developed by US-based company Palo Alto, which also offers a set of other security platforms. Cortex Xpanse is aimed exclusively at giant enterprises with large security teams and internal SOCs. It offers some exclusive features that other EASM tools don’t have. At the same time, its enterprise-exclusive aim has its own flaws, and we are not talking only about pricing.
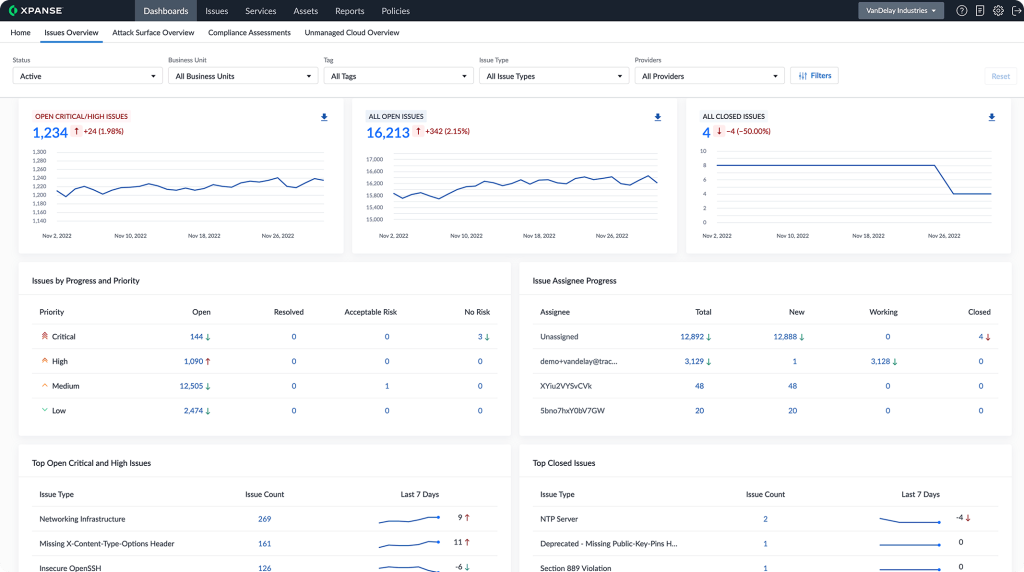
Palo Alto Cortex Xpanse Key Features and Differentiators
- In-app remediation capabilities. Unlike most EASM tools, Palo Alto Cortex Xpanse offers the ability to restrict open ports en masse from within the app.
- Remediation playbooks. Cortex Xpanse allows SOC employees to create remediation playbooks specific for each organization that help assign issues to specific people and track progress on their remediation.
Palo Alto Cortex Xpanse Pros
- Internal attack surface coverage. As an ASM tool, Cortex Xpanse covers both internal and external attack surfaces.
- Solid anti-ransomware protection. Users specifically praise how Cortex Xpanse protects against ransomware – one of the most relevant security risks nowadays.
- Highly customizable reports and dashboards.
Palo Alto Cortex Xpanse Cons
- Complex. A peer review calls Cortex Xpanse “wayward” – it’s quite complex and can be hard to set up the way you want it to work.
- Expensive. Palo Alto isn’t shy with price tags – Cortex Xpanse pricing starts in the six-digit range. It’s the most expensive tool on our list, even Censys ASM doesn’t cost that much.
Palo Alto Cortex Xpanse Demo and Pricing
Free trial: ❌
Demo: ❌
Palo Alto doesn’t disclose Cortex Xpanse pricing openly, but on the internet, it’s possible to find that it starts at $249,999 per year for 1,000 IP addresses. That’s one order of magnitude more than most other tools, and the most affordable ones are two orders of magnitude cheaper.
There’s no free trial and no public demo available.
Our Verdict on Palo Alto Cortex Xpanse
Cortex Xpanse is the most functional solution on the list – from covering the internal attack surface to automatically closing open ports and creating remediation playbooks. It’s also the most expensive one – and at this price it doesn’t offer the highest external attack surface coverage.
This peer review suggests that an organization was mostly able to reduce its internal attack surface, while tackling the external one proved to be more difficult. With its pricing and somewhat steep learning curve, it’s only suitable for huge enterprises that are not in any rush to cover their external attack surface and have no restrictions when it comes to their cybersecurity budget.
Read a more detailed comparison between Palo Alto Cortex Xpanse and Attaxion
5. Detectify
Detectify is a Swedish EASM platform primarily geared toward small and medium-sized businesses. It combines dynamic application security testing (DAST) and external attack surface management.
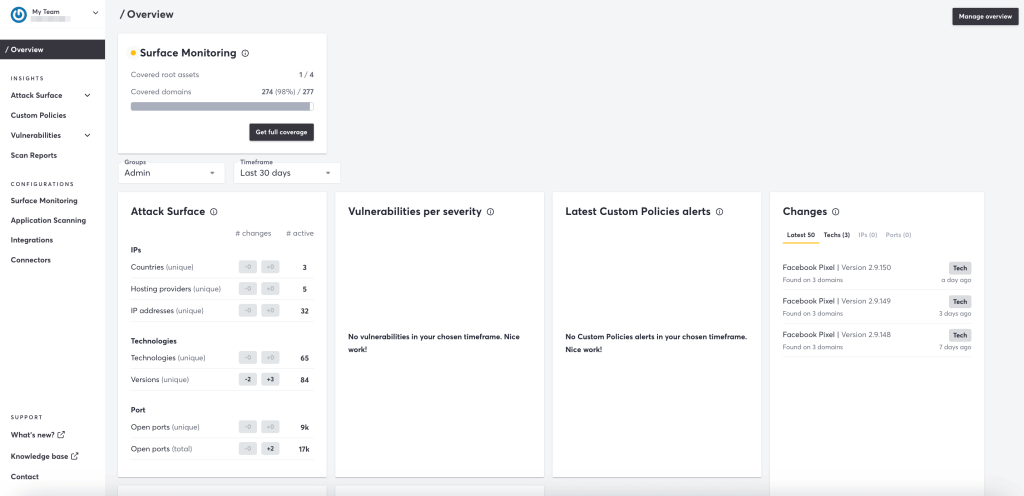
Detectify’s Key Features and Differentiators
Detectify stands out from the crowd for two reasons:
- Affordability. It’s one of the very few relatively affordable EASM platforms.
- Payload-based vulnerability scanning. Unlike many other external attack surface management tools, Detectify identifies if there is a security vulnerability not only by checking the configuration but by actively trying to exploit it. As a result, the number of false positives that Detectify generates is low.
Detectify Pros
- Easy to set up and use. Some may even call Detectify’s interface minimalistic.
- Crowdsourced threat intelligence. Detectify relies on a community of ethical hackers to add vulnerabilities, sometimes before they are issued a CVE number.
Detectify Cons
- Weaker asset discovery capabilities. Detectify finds significantly fewer assets than the tools with better reconnaissance techniques.
- Basic reporting. Detectify doesn’t offer compliance reports or anything else aside from notifications.
- Limited customization. That was one of the user complaints from Gartner peer reviews. They wanted an option to tweak scanning, enabling or disabling some modules. But Detectify doesn’t allow that.
Detectify Demo and Pricing
Free trial: ✅(14 days)
Demo: ❌
Detectify offers a 14-day free trial for you to get a taste of how it works before committing to anything. It’s one of the very few EASM platforms (along with Attaxion) that does that.
Detectify’s pricing starts at 275 EUR (300 USD at the moment of writing) for 25 subdomains.
Our Verdict on Detectify
Detectify is the second of the two more affordable EASM platforms, which makes it look similar to Attaxion. Both are quick to set up and easy to understand, but very different when it comes to their main strengths.
Detectify boasts payload-based vulnerability scanning, lowering the number of false positives, but its discovery engine is weaker, not covering significant portions of the organization’s external attack surface.
Read a detailed comparison between Detectify and Attaxion
6. Intruder.io
Intruder.io is a vulnerability scanner and a vulnerability management tool that has recently been positioned as an EASM tool as well, even though it lacks some EASM capabilities.
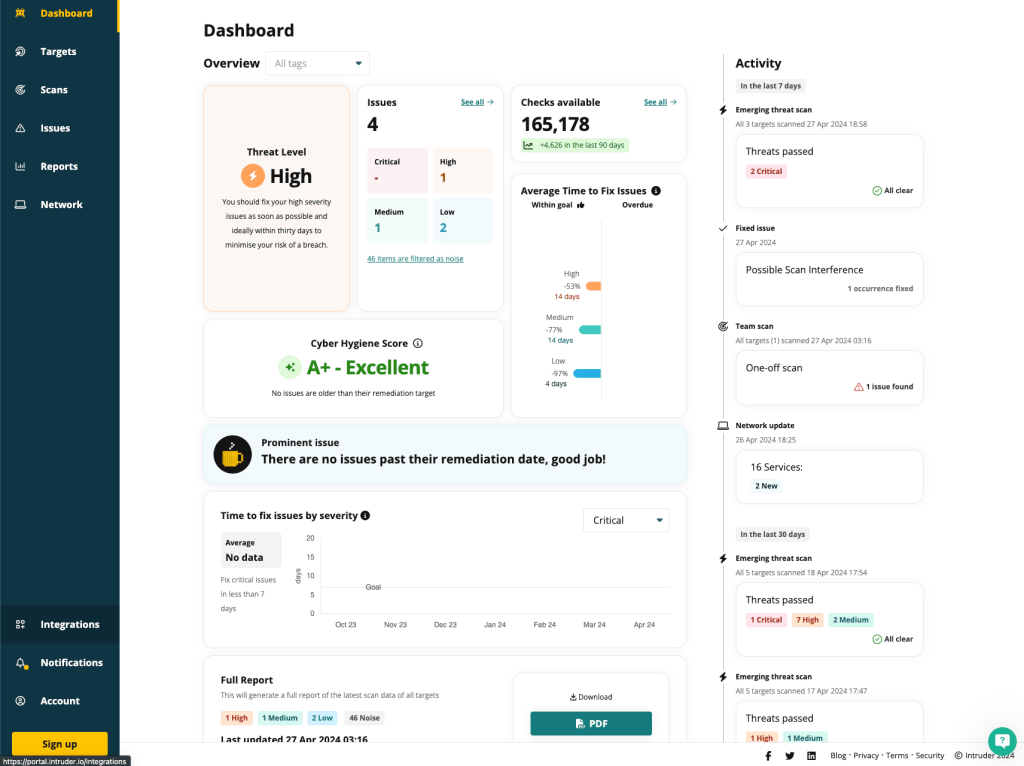
Intruder’s Key Features and Differentiators
Intruder is quite different from the rest of the tools in this list, and there are a number of reasons for that.
- No asset discovery. Unlike full-fledged EASM tools, Intruder only scans the assets that you provide it, without trying to find related assets. The only situation when it can cover your external attack surface is if you know each and every asset that belongs there and provide them to Intruder.io.
- Pricing and scalability. Again, unlike most EASM tools, Intruder has transparent pricing that starts as low as $99/month for the most basic version that only protects one domain and IP address. We’ll discuss the pricing in more detail below.
Intruder Pros
- Easy to set up.
- Flexible reporting and dashboards. Intruder is very user-friendly. It allows you to easily create compliance reports and offers an intuitive dashboard that covers both the state of monitored assets and the efforts of the security team. Intruder also offers a flexible notification setup.
- Integrations with compliance tools. In addition to the usual integrations with Slack, Teams, Jira, and so on, Intruder is also integrated with compliance platforms Vanta and Drata.
Intruder Cons
- No asset discovery. We are repeating ourselves, but that’s too important: on everything but the Enterprise plan, Intruder only scans the assets that you provide (or those that it pulls from the public cloud accounts using integrations), which means that it just doesn’t cover the first stage of the EASM process.
- Tricky pricing. While $99/month sounds like a great deal, it’s not realistic. For this price, you get only 5 infrastructure licenses for the Essential tier, which doesn’t include integrations, emerging threat scans, and other useful options. Trying to cover an attack surface even of a small business brings Intruder’s costs to about $10,000 per year, which is still less than for many other tools, but much more than it may seem at first glance. There are reviews on G2 where users complain about the pricing being high, even though it may initially seem low.
- Limited vulnerability discovery capabilities. In our tests, Intruder didn’t find some of the security flaws that other tools discovered. Note: The choice of the vulnerability scanner in Intruder depends on the tier. We tested it on the Cloud tier with Tenable Nessus as the vulnerability scanner.
Intruder Demo and Pricing
Free trial: ✅(14 days)
Demo: ❌
Intruder offers a free 14-day trial of its Cloud tier, which allows you to get a proper understanding of how it works and what it is capable of.
Essential tier starts at around USD $99/month for the Essential plan for 5 infrastructure licenses and from USD $180/month for the Cloud plan for the same amount of licenses. Web application licenses that offer authenticated scanning need to be purchased separately.
Our Verdict on Intruder
As a vulnerability scanner and vulnerability management tool, Intruder is a useful tool for companies of different sizes. Its easy UI and good reporting capabilities could be great for teams that don’t have a security department at all.
However, Intruder is not a full-fledged EASM tool due to the lack of asset discovery capabilities.
Read a detailed comparison between Intruder.io and Attaxion
7. Acunetix by Invicti
Acunetix by Invicti is a well-known dynamic application security testing (DAST) tool that also includes some features commonly found in external attack surface management platforms. It’s aimed at organizations of different sizes that require in-depth, automated testing of web applications.
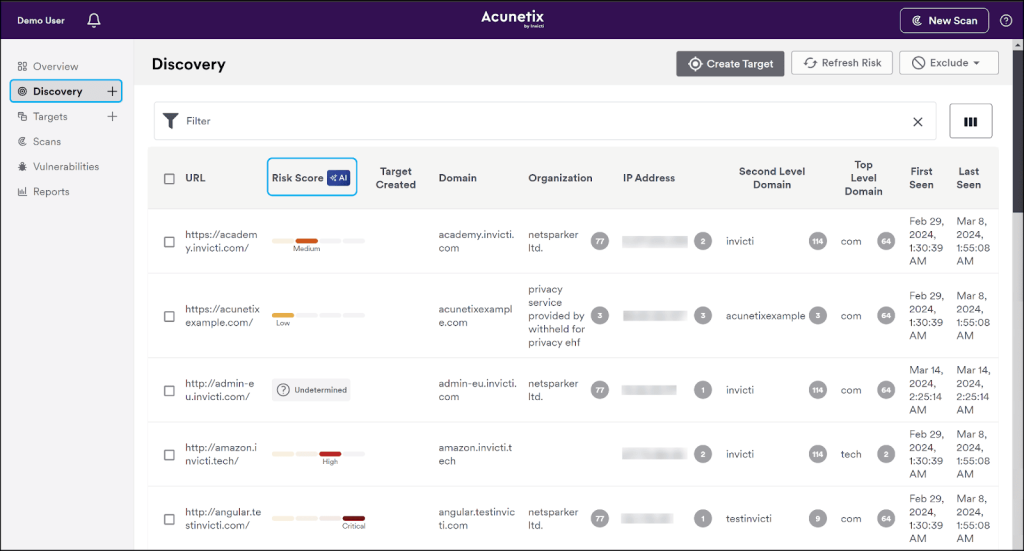
Acunetix’s Key Features and Differentiators
Acunetix is designed to provide deep vulnerability scanning for web applications. While it doesn’t offer the full asset discovery capabilities of some EASM tools, it directly competes with them, as, unlike Intruder.io, for example, it offers asset discovery. Here’s what makes Acunetix stand out:
- Website and subdomain discovery. Acunetix goes beyond scanning the assets you directly provide by finding related domains and subdomains. An average DAST tool doesn’t do that.
- AI-based asset prioritization. Acunetix uses AI to rank websites based on their potential risk before starting a vulnerability scan. This predictive approach helps teams prioritize what to scan first.
- Payload-based scanning. Acunetix uses a heavy payload-based vulnerability scanner. On the one hand, it provides high-quality results with a low false-positive rate. On the other hand, it’s fairly intrusive and can significantly slow down the app that is undergoing a scan. That’s why Acunetix offers flexible scheduling options to reduce the risk of disruptions.
Acunetix Pros
- Powerful vulnerability scanner. Acunetix is designed to dive deep into web app vulnerabilities, offering reliable, fact-based results with a low false positive rate.
- Flexible reporting and notifications. The tool provides highly customizable reporting options, including compliance reports, and integrates with various communication tools like Slack and email for alerts.
- Impressive set of integrations. Acunetix offers plenty of integrations with a variety of different tools, from popular bug tracking tools like Jira, Redmine, and ServiceNow to penetration testing platforms like Metasploit, and from CI/CD tools like GitHub Actions, GitLab CI, and TeamCity to secret management systems like HashiCorp Vault or Azure Key Vault. That makes it well-suited for DevSecOps.
Acunetix Cons
- Limited asset discovery. Since Acunetix is more a DAST than a EASM, its asset discovery capabilities are limited. It uses a few cyber reconnaissance techniques and finds fewer assets than full-fledged EASM tools. It also doesn’t discover assets like CIDRs at all.
- Intrusive scanning. Acunetix’s vulnerability scans are very thorough, but they can be intrusive and may slow down or knock out web applications during testing, especially if not properly scheduled.
- False positives in asset discovery. Some users have reported that Acunetix occasionally identifies domains or subdomains that don’t belong to their organization as their assets. So, while in vulnerability scanning Acunetix maintains a low false-positive rate, this doesn’t always apply to asset discovery.
Acunetix Demo and Pricing
- Free trial: ❌
- Demo: ❌
Acunetix doesn’t offer an openly available free trial or a public demo, but you can talk to sales to arrange one. Pricing information is not readily available on the website, but third-party sources list the lowest price at $4,500 and the highest at $26,600 per year, depending on the source and the number of websites you want to scan.
If these pricing estimates are correct, then Acunetix is somewhere in the middle of the EASM pricing spectrum.
Our Verdict on Acunetix
Depending on how you look at it, Acunetix is either a DAST tool on steroids or an EASM tool with weak asset discovery capabilities. Its stronger sides include a powerful vulnerability scanner, great reporting capabilities, and a massive list of integrations.
However, if you’re looking to protect your entire external attack surface, Acunetix may not fully meet your needs due to its limited asset discovery and a highly intrusive scanner.
Read a detailed comparison between Acunetix and Attaxion
8. UpGuard Breach Risk
UpGuard is a cybersecurity platform offering both a third-party risk management (TRPM) tool called Vendor Risk and an EASM tool (they say it’s ASM, but in fact it’s EASM) called Breach Risk (previously known as BreachSight). The two share a lot when it comes to workflows, but the difference is that Vendor Risk focuses on third-party assets, while Breach Risk covers first-party assets. UpGuard is used by organizations of all sizes as it has a flexible and scalable pricing model.
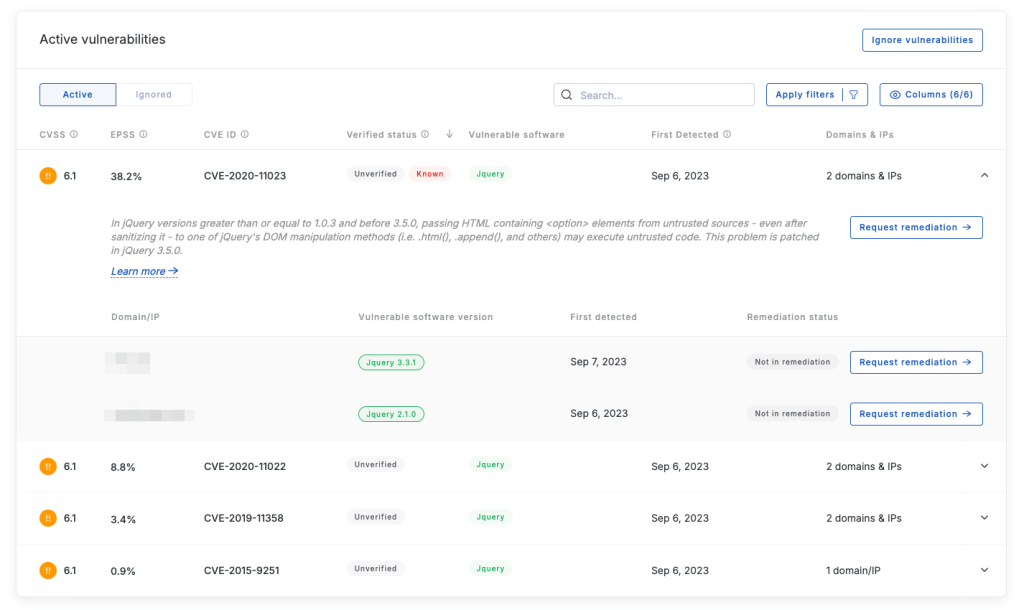
UpGuard Breach Risk Key Features
- Typosquatting and identity breach detection. UpGuard Breach Risk detects newly registered domains that seem to be suspiciously similar to yours and notifies you about that. It also looks for data breaches on the Internet in which your employee credentials have been exposed.
- Remediation workflows. Both Vendor Risk and Breach Risk allow users to create remediation requests, defining scope and assigning them to a specific person, and then track remediation progress.
- Scanning without ownership verification. UpGuard can scan your domains without any ownership verification, simplifying the process of adding new assets.
UpGuard Breach Risk Pros
- Part of a comprehensive security platform. Upguard’s TRPM and ASM – Vendor Risk and Breach Risk – are two parts of one platform, sharing a common interface. That simplifies work for security teams with most of the things being managed from one and the same place.
- Neat and tidy UI. UpGuard’s platform is very well designed from the user experience standpoint, offering intuitive workflows and all comprehensive reporting.
- Speed. UpGuard Breach Risk scans new assets almost instantly, providing a high-level overview and recommendations within moments.
UpGuard Breach Risk Cons
- Subpar asset discovery. During our test, UpGuard Breach Risk failed to discover related domains and subdomains, requiring manual additions. This means that users will likely need an additional tool for asset discovery and inventory to get a complete picture of their external attack surface.
- Superficial vulnerability scanning. UpGuard uses the same non-intrusive vulnerability scanner for both Breach Risk and Vendor Risk, which resulted in false positives and some missed vulnerabilities. While this approach avoids triggering security defenses, it lacks depth compared to more advanced vulnerability scanners.
- Integrations and API only available on pricier plans. While UpGuard Breach Risk’s starting price appears low, it does not include integrations or API access. Users requiring these features will need to pay significantly more — often several times the base price
UpGuard Breach Risk Pricing
Free trial: ✅ (14 days)
Demo: ❌
UpGuard has a free plan for Vendor Risk, but Breach Risk is not included in it. However, you can get a 14-day free trial of both without any limitations.
UpGuard’s Breach Risk solution starts at 250 per month (billed annually, i.e. $3,000 per year), which is on the lower side of the spectrum, but during our evaluation, we were only offered a $6,000 per year option.
Our Verdict on UpGuard Breach Risk
UpGuard Breach Risk feels more like an add-on to Vendor Risk rather than a fully independent ASM platform. While its integration with Vendor Risk, typosquatting detection, and user-friendly interface are strong advantages, it falls short in core ASM functionalities like attack surface discovery and in-depth vulnerability scanning.
For organizations already using Vendor Risk, Breach Risk could be a useful and relatively cost-effective addition. However, as a standalone EASM tool, UpGuard Breach Risk lags behind competitors in terms of effectiveness.
Read a detailed comparison between UpGuard and Attaxion
9. Beagle Security
Beagle Security is a DAST tool with automated penetration testing capabilities, designed to help organizations identify security flaws in their web applications and APIs. It focuses heavily on DevSecOps and integration into the software development lifecycle, but it can also serve as a solution for traditional vulnerability management.
Beagle Security’s Key Features and Differentiators
Beagle Security is one of the two platforms in this list that primarily focuses on DevSecOps—Acunetix is the other one. Its asset discovery is very limited (it only offers subdomain discovery) and can’t compare to most EASM platforms, but it stands out in these other areas:
- Penetration testing as a core offering: Beagle Security offers automated penetration testing for web applications and APIs, leveraging AI to enable human-like automation.
- Proprietary vulnerability scanning technology: It relies on a proprietary vulnerability scanner that can provide improved results if the user specifies technologies (programming languages, frameworks, databases) used in the web app. Even though some G2 users complain about false positives, the same users mention that, upon request, the Beagle Security team would step in to manually verify which of the positives are true and which are false.
- Integration into the software development lifecycle: While other EASM tools might integrate with broader security ecosystems, Beagle’s focus is on enabling developers to find and fix vulnerabilities early.
Beagle Security Pros
- Authenticated scanning with various authentication mechanisms. Beagle Security supports testing behind login pages, allowing it to conduct comprehensive security assessments of authenticated sections of web applications.
- Integration capabilities for DevSecOps. Beagle Security integrates with popular CI/CD platforms like Jenkins, Bitbucket, Azure Pipelines, and GitHub Actions, enabling organizations to embed security testing directly into their development pipelines.
- Users have the flexibility to trigger penetration tests on demand or schedule them to run periodically (e.g., weekly or semiannually).
Beagle Security Cons
- Pricing is per test (and tests are conducted on individual targets), which might limit extensive use on lower-tier plans. Unlike some solutions that offer unlimited scans per asset, Beagle Security’s pricing structure is based on the number of penetration tests performed.
- The Essential plan lacks API testing, asset discovery, compliance reports, and certain integrations. It is also limited to two tests per month.
- Tests do not run continuously. They require manual triggering or scheduling.
Beagle Security Demo and Pricing
- Free trial: ✅ (10 days and only for the Advanced Plan)
- Demo: ✅
Beagle Security offers a free plan with one very limited test per month, along with three paid plans. The Essential plan is priced at $119 per month and offers two tests per month. The Advanced Plan is priced at $359 per month, with more features and 15 tests per month.
The Enterprise Plan caters to those who need enterprise-grade features, including SSO, a dedicated customer success manager, and priority support. The price is not published on their website, but G2 estimated it at $6,850 per year.
Our Verdict on Beagle Security
Beagle Security is a viable DAST tool and an alternative to other popular vulnerability scanners. It has strong DevSecOps capabilities, powerful vulnerability scanning, and impressive integrations, but like Acunetix, it falls short in asset discovery and continuous monitoring, especially if you’re looking for a platform that provides visibility over your entire external attack surface.
Read a detailed comparison between Beagle Security and Attaxion
10. ProjectDiscovery
ProjectDiscovery is a vulnerability management platform driven by its own open-source scanner, Nuclei, which is a popular vulnerability scanner designed to minimize false positives. Aside from Nuclei, ProjectDiscovery is also the developer of other well-known open-source tools like Subfinder and Naabu, which are part of the platform.
ProjectDiscovery’s Key Features and Differentiators
ProjectDiscovery’s standout features stem from its foundation in open-source tools that are well regarded in the cybersecurity community:
- Advanced asset discovery: The platform goes beyond basic asset discovery. It uses its own tools (i.e., Subfinder, Cloudlist, and Naabu) to discover and catalog an organization’s assets and integrates with the Crunchbase API to automatically find subsidiaries and their related assets.
- Template-based scanning: Nuclei, which ProjectDiscovery uses as its vulnerability scanner, stands out because it is template-based, rather than version-based. This means it doesn’t just assign vulnerabilities by detecting a specific software version. Instead, it uses templates to reproduce an attacker’s steps, validating whether a vulnerability truly exists and is exploitable.
- Internal network scanning capability: The platform also offers the capability for internal network scanning via its TunnelX tool.
ProjectDiscovery Pros
- Good discovery capabilities. The combination of the open-source tools under the hood gives ProjectDiscovery a solid asset discovery engine.
- Popular vulnerability scanner. Nuclei is widely respected as an open-source alternative to commercial vulnerability scanners.
- Internal scanning. ProjectDiscovery can perform both internal and external network scanning.
- Various integration options. The platform offers a wide range of integrations for remediation, notifications, and ticketing, including Slack, MS Teams, Jira, GitHub, and GitLab.
ProjectDiscovery Cons
- False negatives. During internal testing, ProjectDiscovery found zero vulnerabilities for the target domain, even though other platforms detected real vulnerabilities.
- Third-party dependencies add costs. To perform at its best, the platform requires third-party APIs for some of its tools, such as Subfinder, which means users need to pay for their own API keys to get the most out of it.
- Sometimes unstable. Some users have reported bugs and glitches, such as scans failing to start or exports not working correctly.
- No monthly plans. The free tier comes with significant limitations and does not address EASM needs, while the Enterprise tier requires a yearly commitment right away and might be too costly for smaller businesses.
ProjectDiscovery Demo and Pricing
- Free trial: ❌
- Demo: ✅
ProjectDiscovery does not publicly disclose its pricing for the Enterprise plan, and external sources have cited varying pricing. An AWS listing showed a price of $30 per asset per year, whereas on G2, the disclosed price was $2,500 per year. The only tier with publicly available details is the Free plan, which has notable limitations, including a cap of 10 new domains per month and a once-a-month vulnerability scan.
Our Verdict on ProjectDiscovery
ProjectDiscovery is an interesting tool that does a great job with asset discovery, but struggles with false negatives and a dependency on community-driven templates with varying quality when it comes to vulnerability scanning. This means that users must be vigilant in validating results. While Project Discovery’s approach is flexible, it may lack the polished, enterprise-grade reliability of some of its competitors.
Read a detailed comparison between ProjectDiscovery and Attaxion
11. Tenable Nessus Expert
Tenable Nessus Expert is an advanced version of the renowned Nessus Professional vulnerability assessment tool, adding some external attack surface management capabilities to it. Nessus Expert includes asset discovery and web application scanning that identifies vulnerabilities in both custom code and third-party components.
Tenable Nessus Expert’s Key Features and Differentiators
- Cloud or on-premises installation. Nessus Expert requires deployment, whether on a local computer, a server, or a virtual machine in the cloud.
- Internal and external scanning. Nessus Expert can scan both internal and external assets, as well as cloud infrastructure-as-code.
- Compliance standard audits. Nessus Expert can audit and ensure that IT assets are compliant with over 500 different policies and standards.
- Better suited for technical users. The platform is primarily designed for pen testers and cybersecurity consultants, with Tenable making it available even on a Raspberry Pi.
- Additional risk detection. Users can run Active Directory (AD) checks (this feature is available across all Nessus variations and is not specific to Nessus Expert) and scan Infrastructure as Code (IaC) repositories.
Tenable Nessus Expert Pros
- Many users report that Nessus Expert is easy to install and navigate.
- Nessus Expert can identify zero-trust vulnerabilities from the CISA alert list.
- Built-in report templates that are readily available for managerial reports.
- Can detect a wide range of vulnerabilities, weaknesses, misconfigurations, and other security risks.
Tenable Nessus Expert Cons
- Some users report negative experiences with Tenable’s customer support for setup assistance.
- Vulnerability scanning for large environments can take two to three days.
- Past scans take up disk space, and they must be manually deleted to free up space.
- Some users have expressed a desire for more granular control over agent profiles and other settings to better suit their specific environments.
- The scanner can report false positives, according to some reviews.
Tenable Nessus Expert Demo and Pricing
- Free trial: ✅ (7 days)
- Interactive demo: ❌
Nessus Expert is priced at $6,390 per year, with discounts available for multi-year licenses. This includes external attack surface scanning for five domains per quarter, but does not cover advanced customer support and training.
Access to 24/7 phone, email, community, and chat support is offered as an add-on, at $400 per year, while an on-demand video training course for one person is priced at an additional $275 per year.
The pricing above is for the US. It’s region-specific, and, for example, in the EU the price is roughly 20% higher.
Our Verdict on Tenable Nessus Expert
Tenable Nessus Expert is a vulnerability assessment tool with some added EASM capabilities, but not an EASM platform on its own. While its strength is vulnerability scanning, its asset discovery is not very reliable (it sometimes fails to discover anything or identifies false-positive subdomains). It also has very limited continuous monitoring capabilities, which are an EASM must-have. For continuous monitoring and full-scale EASM, Tenable wants users to commit to their ecosystem and use Tenable One or Tenable Vulnerability Management which have Nessus built in, but are more costly and difficult to set up.
However, for organizations with a large budget that need a vulnerability scanner for both internal and external assets — with the added benefit of some EASM capabilities for cloud and IaC environments — Tenable Nessus Expert is a viable option.
Read a detailed comparison between Tenable Nessus Expert and Attaxion
Other Notable External Attack Surface Management Platforms
There are many more EASM solutions on the market. We only covered solutions that we ourselves could test. Other notable mentions include:
- Cycognito, a well-known EASM vendor which blends EASM with exploit intelligence.
- CyberInt Argos Edge, a security platform that combines threat intelligence with EASM capabilities.
- CrowdStrike Falcon Surface, an EASM solution by CrowdStrike with an interesting function of dividing the assets into groups such as managed or unmanaged and belonging to the official or unofficial perimeter.
- Mandiant Attack Surface Management, an ASM platform by Google with functionality very similar to Attaxion, but much more expensive. Mandiant’s strong sides include tight collaboration with Google Project Zero—a team of elite hackers researching 0-day vulnerabilities.
- Halo Security, a company that combines an EASM solution with DAST and some penetration testing services.
- IBM Security Randori, a solution that combines external attack surface management with continuous automated red teaming (CART).
- Edgescan Attack Surface Management, an EASM solution that optionally comes with penetration testing as a service (PTaaS).
- InsightVM by Rapid7, formally a vulnerability management tool that has all the same capabilities as an EASM solution, with a focus on regulation compliance.
Some of them are either very expensive – like Mandiant ASM and CyberInt Argos Edge – or limited – like Tenable Nessus Expert, which relies on a subdomain scanner for asset discovery. Most importantly, we haven’t had the chance to try them yet. As we get to test new external attack surface management tools, we’ll update the article.
Conclusion
Choosing the right external attack surface management solution depends on many aspects of your infrastructure, from its size to where it’s based. It also needs to suit your needs and preferences – from offering the right prioritization framework to being able to integrate with the rest of your cybersecurity tech stack.
Despite having mostly very similar functionality, EASM solutions differ in quality when it comes to asset discovery and vulnerability scanning. Finally, another factor that plays a huge role in the budget. External attack surface management platforms’ pricing can differ by up to 2 orders of magnitude.
From the list above, Attaxion offers the best attack surface discovery capabilities thanks to its numerous reconnaissance techniques at a reasonable price. The other relatively inexpensive solutions are Detectify, Intruder, and Azure-specific Microsoft Defender EASM. All have their pros and cons, but none of them come close to Attaxion when it comes to attack surface coverage.
Censys ASM is a balanced solution, but with a much heftier price tag, and Palo Alto Cortex Xpanse costs significantly more than anything else on the list, effectively making it inaccessible for most companies that don’t have millions of dollars in their cybersecurity budget.